2016-09-14 - EITEST GATE URL PATTERNS CHANGED
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-14-EITest-Rig-EK-sends-Bart-ransomware.pcap.zip 176.8 kB (176,775 bytes)
- 2016-09-14-EITest-Rig-EK-sends-Bart-ransomware.pcap (241,384 bytes)
- 2016-09-14-EITest-Rig-EK-and-Bart-ransomware-files.zip 206.1 kB (206,086 bytes)
- 2016-09-14-Bart-ransomware-decryptor-page.css (3,049 bytes)
- 2016-09-14-Bart-ransomware-decryptor-page.html (6,439 bytes)
- 2016-09-14-Bart-ransomware-recovery-instructions.bmp (3,686,454 bytes)
- 2016-09-14-Bart-ransomware-recovery-instructions.txt (1,696 bytes)
- 2016-09-14-EITest-Rig-EK-flash-exploit.swf (49,000 bytes)
- 2016-09-14-EITest-Rig-EK-landing-page.txt (3,422 bytes)
- 2016-09-14-EITest-Rig-EK-payload-Bart-ransomware.exe (123,904 bytes)
- 2016-09-14-EITest-flash-redirect-from-freekidscrafts_xyz.swf (4,032 bytes)
- 2016-09-14-page-from-hydrogengroup_com-with-injected-EITest-script.txt (52,446 bytes)
NOTES:
- Thanks to Peter for emailing me about this compromised site.
- URL patterns for the EITest gate have changed (see below image of the traffic filtered in Wireshark for details).
- I last documented EITest Rig EK sending Bart ransomware on 2016-09-01.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
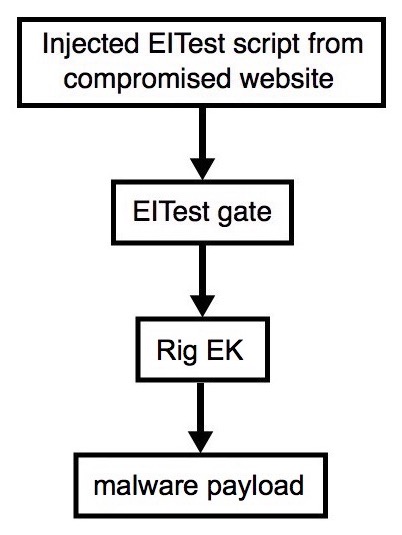
Shown above: Flowchart for this infection traffic.
TRAFFIC
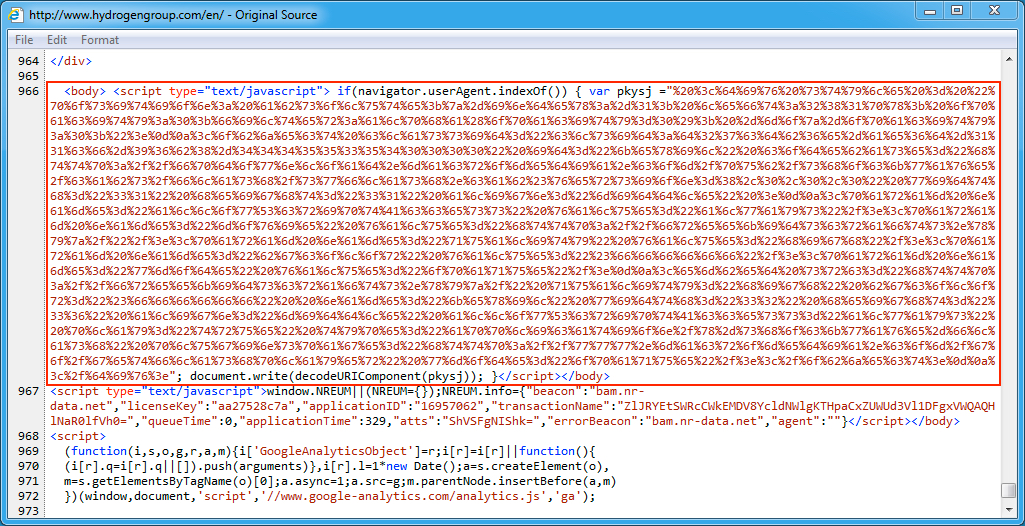
Shown above: Injected script in page from the compromised site pointing to the EITest gate.

Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.hydrogengroup[.]com - Compromised site
- 31.184.193[.]168 port 80 - freekidscrafts[.]xyz - EITest gate
- 185.117.73[.]165 port 80 - tbcd5.gncc15s[.]top - Rig EK
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- s3clm4lufbmfhmeb[.tor2web[.]org
- s3clm4lufbmfhmeb[.]onion[.]to
- s3clm4lufbmfhmeb[.]onion[.]cab
- s3clm4lufbmfhmeb[.]onion[.]link
FILE HASHES
FLASH FILES:
- SHA256 hash: 5e9f03a083aed555fb3dbf20fd4121b92f9ba5e5b2a4edd851f210536abbb853
File name: 2016-09-14-EITest-flash-redirect-from-freekidscrafts_xyz.swf
- SHA256 hash: e20fc49d11d8232b51ec3ce2fa24d3081c3d48db4cb66a31e2bc2c07b43e27b8
File name: 2016-09-14-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 45fcdd90b1268f6d5dd2a99a78c3df1a95b7809cbe13b68d9f164edd2264005e
File name: 2016-09-14-EITest-Rig-EK-payload-Bart-ransomware.exe
IMAGES
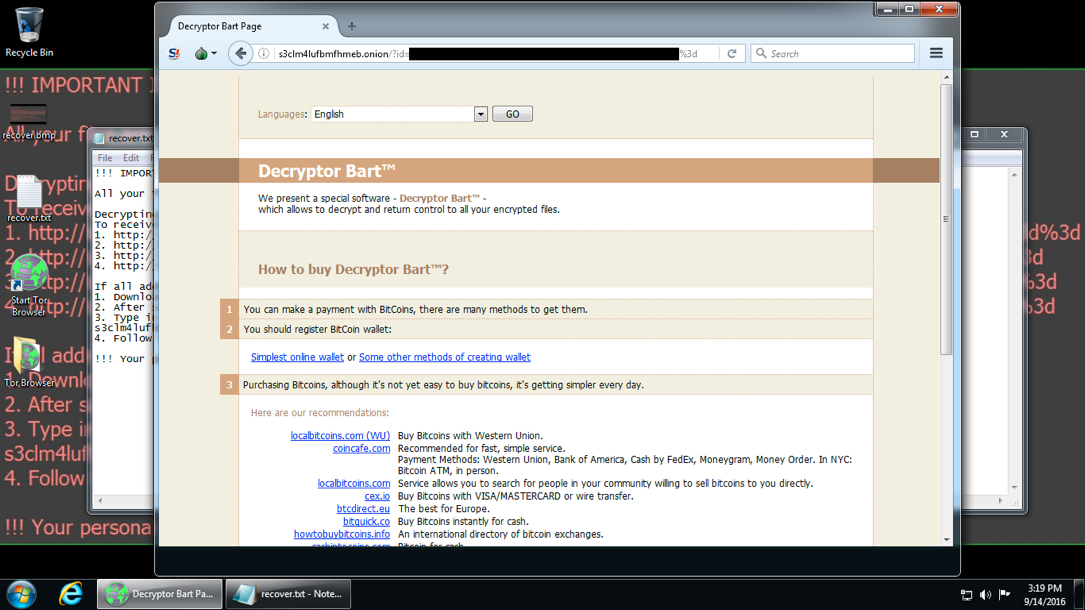
Shown above: The infected Windows host.
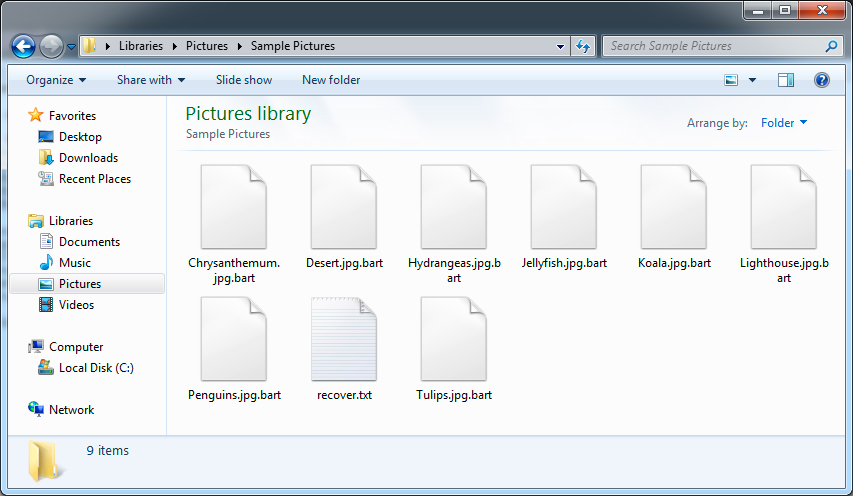
Shown above: File extension .bart appended to the encrypted files.
Click here to return to the main page.