2016-09-26 - NEW HOST PROFILING TRAFFIC SEEN FROM DOWNLOADER FOR LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-26-Afraidgate-Neutrino-EK-sends-Locky-ransomware.pcap.zip 508.8 kB (508,840 bytes)
- 2016-09-26-Afraidgate-Neutrino-EK-sends-Locky-ransomware.pcap (550,217 bytes)
- 2016-09-26-Afraidgate-Neutrino-EK-and-Locky-ransomware-files.zip 424.2 kB (424,205 bytes)
- 2016-09-26-Afraidgate-Locky-ransomware-decrypt-instructions.bmp (3,721,466 bytes)
- 2016-09-26-Afraidgate-Locky-ransomware-decrypt-instructions.html (10,085 bytes)
- 2016-09-26-Afraidgate-Neutrino-EK-flash-exploit.swf (76,691 bytes)
- 2016-09-26-Afraidgate-Neutrino-EK-landing-page.txt (2,472 bytes)
- 2016-09-26-Afraidgate-Neutrino-EK-payload-Locky-ransomware-downloader.exe (47,104 bytes)
- 2016-09-26-Locky-decryptor-page-style.css (3,422 bytes)
- 2016-09-26-Locky-decryptor-page.html (6,008 bytes)
- 2016-09-26-another-Locky-ransomware-binary-found-on-the-infected-host.exe (173,568 bytes)
- 2016-09-26-follow-up-download-Locky-ransomware.exe (173,568 bytes)
- 2016-09-26-lesley.portcoquitlamweather_ca-modules-tmpl-js-hammer.js.txt (227 bytes)
NOTES:
- Traffic from this Locky ransomware infection shows host profiling activity I haven't noticed before.
- For details, see the last image in the images section of this blog post.
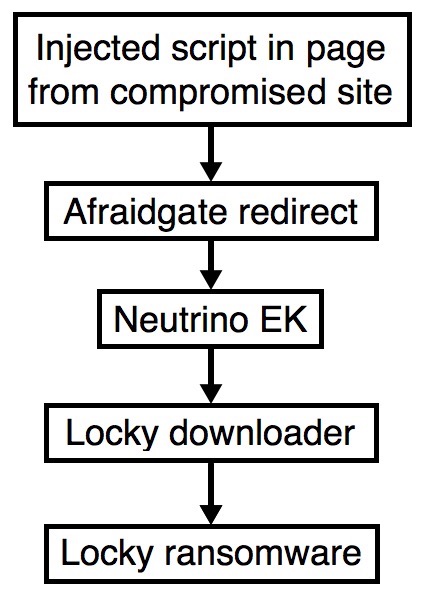
- Otherwise, the Afraidgate Neutrino exploit kit (EK) traffic that sent today's Locky ransomware is the same as seen last week on 2016-09-22.
- Recent developments on the Afraidgate campaign can be found here.
UPDATES:
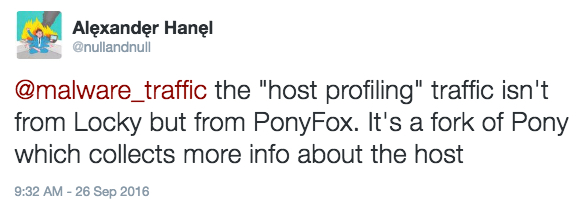
- Thanks to @nullandnull, who tweeted this host profiling traffic was caused by PonyFox, a fork of Pony that collects more info about the infected host.
- Looks like @Kafeine has a post about this new Pony fork (calling it Fox Stealer) at: https://malware.dontneedcoffee.com/2016/09/fox-stealer-another-pony-fork.html
Shown above: Tweet from @nullandnull about the profiling traffic.
Shown above: Flowchart for this infection traffic.
TRAFFIC
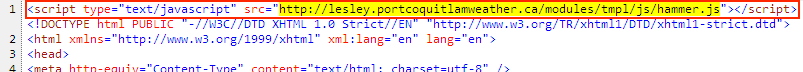
Shown above: Injected script in page from compromised site pointing to the Afraidgate URL.

Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 188.166.66[.]191 port 80 - lesley.portcoquitlamweather[.]ca - GET /modules/tmpl/js/hammer.js - Afraidgate redirect
- 78.46.167[.]130 port 80 - oxraa.blackfinish[.]top - Neutrino EK
- 45.32.144[.]151 port 80 - crocotan[.]com - Follow-up download of Locky ransomware
- 104.36.83[.]52 port 80 - blognetoo[.]com - POST /find.php/hello - Host profiling traffic
- 104.36.83[.]52 port 80 - blognetoo[.]com - POST /find.php/data - Host profiling traffic
- 62.173.154[.]240 port 80 - 62.173.154[.]240 - POST /data/info.php - Locky ransomware post-infection callback
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- f5xraa2y2ybtrefz[.]tor2web[.]org
- f5xraa2y2ybtrefz[.]onion[.]to
FILE HASHES
NEUTRINO EK FLASH EXPLOIT:
- SHA256 hash: 05db6236bed2620b0649ee207e6b9cb6028cd442acbee4fae1fbbd62c4c1c1f1
File name: 2016-09-26-Afraidgate-Neutrino-EK-flash-exploit.swf
NEUTRINO EK PAYLOAD (PONYFOX):
- SHA256 hash: da8de46603bba7ec820616e7706cacfc86cd405820c0ec32e75448c2f01c42cd
File name: 2016-09-26-Afraidgate-Neutrino-EK-payload-Locky-ransomware-downloader.exe
FOLLOW-UP MALWARE (LOCKY):
- SHA256 hash: f2366cab8fd2169259a54aed23514c3f9993427e325939df16c2365b7b4ca8a6
File name: 2016-09-26-follow-up-download-Locky-ransomware.exe
- SHA256 hash: 7cf005fad833d696bd859778235285661c11d5f73290d0d7ed1ad5ac8dbb9a14
File name: 2016-09-26-another-Locky-binary-found-on-the-infected-host.exe
IMAGES
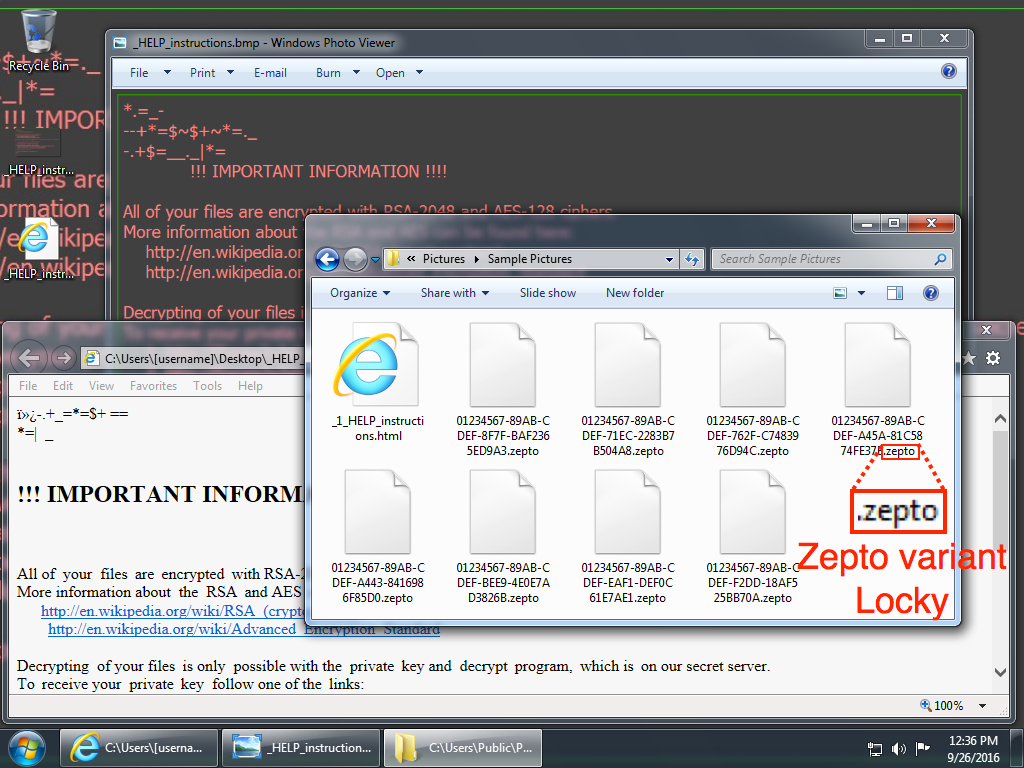
Shown above: Desktop of the infected Windows host.
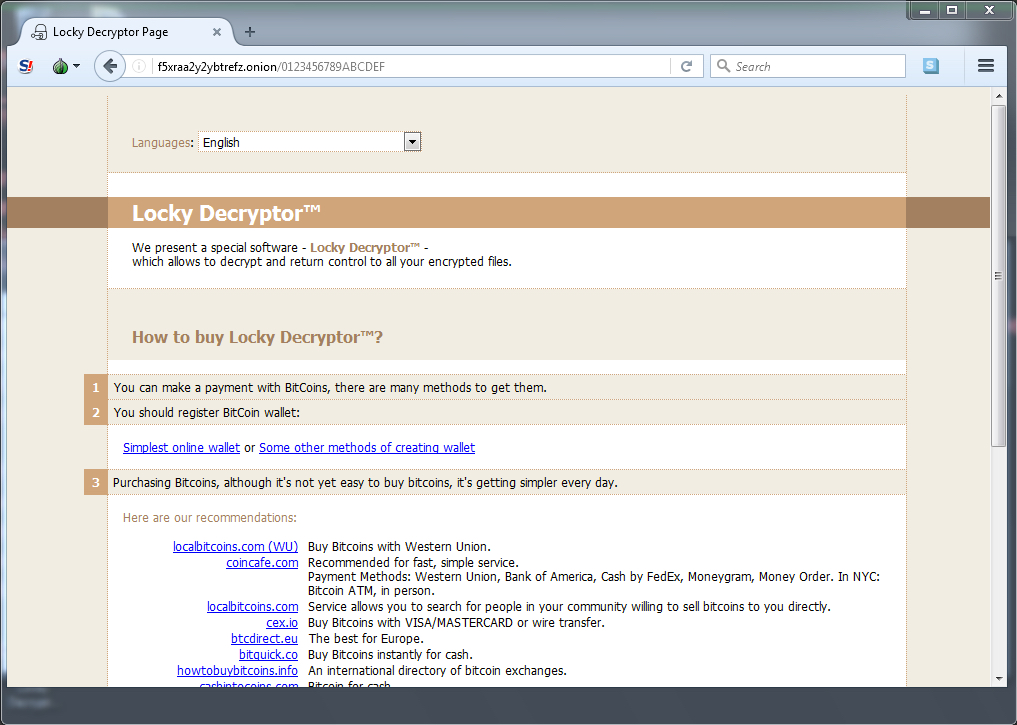
Shown above: Checking the decryption instructions link using a Tor browser.
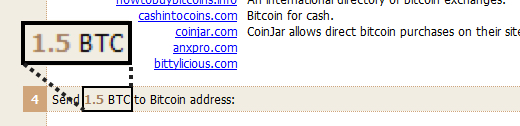
Shown above: 1.5 bitcoins is the ransom for this Locky ransomware infection.
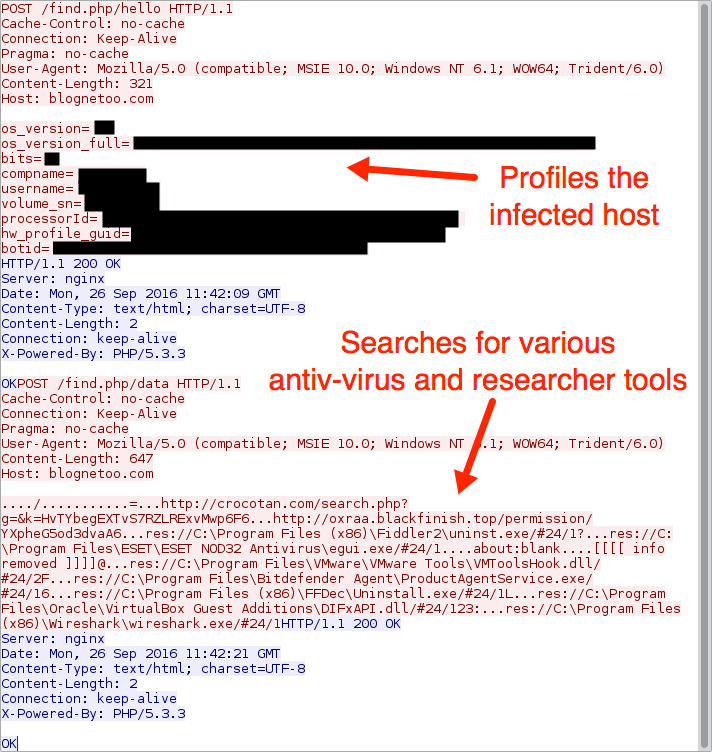
Shown above: Traffic profiling the infected host.
Click here to return to the main page.