2016-12-01 - GOZI (ISFB) INFECTION FROM ITALIAN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-01-Gozi-ISFB-infection-traffic.pcap.zip 386.1 kB (386,140 bytes)
- 2016-12-01-Gozi-ISFB-infection-traffic.pcap (1,024,404 bytes)
- 2016-12-01-email-and-malware-from-Gozi-ISFB-infection.zip 300.9 kB (300,874 bytes)
- 2016-12-01-Gozi-ISFB-malspam-1335-UTC.eml (2,053 bytes)
- DOC69483.zip (1,404 bytes)
- 738928.exe (793,600 bytes)
NOTES:
- This is the same type of malspam and payload as yesterday's blog post (link)
- However, today the files and some of domains/URLs have been updated.
- @suspectnetworks informed me this is Gozi ISBF instead of Ursnif/Dreambot like I originally thought based on the alerts from yesterday.
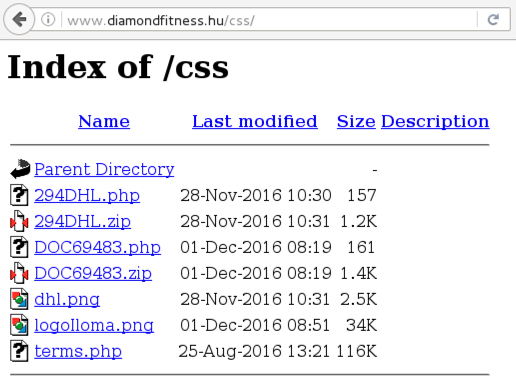
- It looks like that css directory on www.diamondfitness[.]hu is an open book.
THE EMAIL

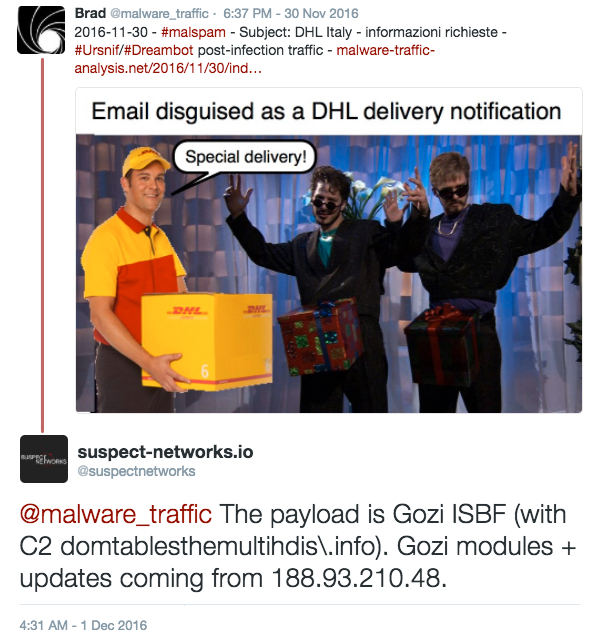
Shown above: Screenshot of the email.
EMAIL HEADER INFO:
- Date/time: Thursday 2016-12-01 13:35:07 UTC
- From: Info1 <dhl.info1.italy@dhl[.]com>
- Subject: DHL Italy - Notifica spedizione
- Message-ID: <156B9E3F127E310973760021EB5E15BC@PCPC>
- Received from: lala.univ-perp[.]fr (194.167.137[.]26)
LINK FROM THE MESSAGE TEXT:
- 84.2.35[.]141 port 80 - www.diamondfitness[.]hu - GET /css/DOC69483.php
THE MALICIOUS ZIP ARCHIVE
ZIP ARCHIVE:
- SHA256 hash: 6e4ea69ad4c50624a59637efe6d612267c599cb9575fac25ea4544de46e12972
File name: DOC69483.zip (1,404 bytes)
EXTRACTED .JS FILE:
- SHA256 hash: a10cd296e3f58fe329bbff6edaf0bdbb1f9099a088b7a5cede583dda09dd7cf2
File name: DOC69483.js (3,482 bytes)
TRAFFIC
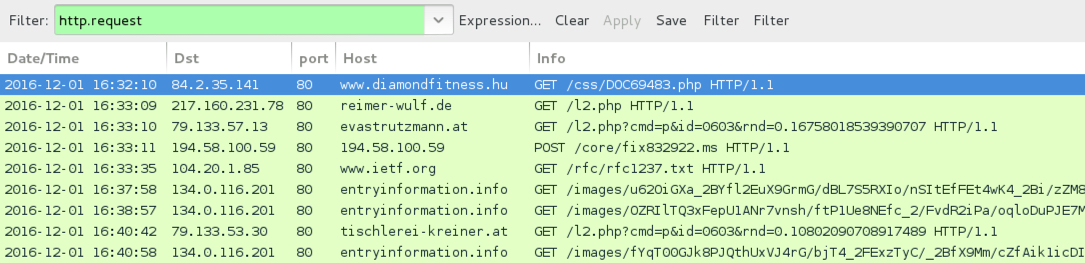
Shown above: Infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- 84.2.35[.]141 port 80 - www.diamondfitness[.]hu - GET /css/DOC69483.php
- 217.160.231[.]78 port 80 - reimer-wulf[.]de - GET /l2.php
- 79.133.57[.]13 port 80 - evastrutzmann[.]at - GET /l2.php?cmd=p&id=0603&rnd=0.16758018539390707
- 194.58.100[.]59 port 80 - 194.58.100[.]59 - POST /core/fix832922.ms
- www.ietf[.]org - GET /rfc/rfc1237.txt
- 134.0.116[.]201 port 80 - entryinformation[.]info - Post-infection callback traffic
- 79.133.53[.]30 port 80 - tischlerei-kreiner[.]at - GET /l2.php?cmd=p&id=0603&rnd=0.10802090708917489
POST-INFECTION FILE HASHES
DOWNLOADED .EXE FILE:
- SHA256 hash: 885393f832f0eb5c97e470419e0858e858f7b00545f66668c33a9846788b1d18 (793,600 bytes)
File name: C:\Users\[username]\AppData\Local\Temp\738928.exe
File name: C:\Users\[username]\AppData\Roaming\clbcbact\crypvobj.exe
Click here to return to the main page.