2017-04-06 - "BLANK SLATE" CAMPAIGN STILL PUSHING CERBER RANSOMWARE, STILL USING FAKE CHROME PAGE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-04-06-Blank-Slate-activity-11-pcaps.zip 4.9 MB (4,933,002 bytes)
- 2017-04-06-Blank-Slate-malspam-tracker.csv.zip 3.0 kB (3,000 bytes)
- 2017-04-06-Blank-Slate-emails-and-Cerber-ransomware.zip 4.2 MB (4,164,053 bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
OTHER NOTES:
- I've collected 52 emails from the Blank Slate campaign during the past few days.
- Of these 52 emails, I found one Microsoft-themed message linking to a fake Chrome install page similar to the one seen on 2017-03-24.
- All the other emails were blank with zip attachments containing .js files.
- This time, the fake Chrome page sent a zip archive instead of an executable.
FAKE CHROME PAGE
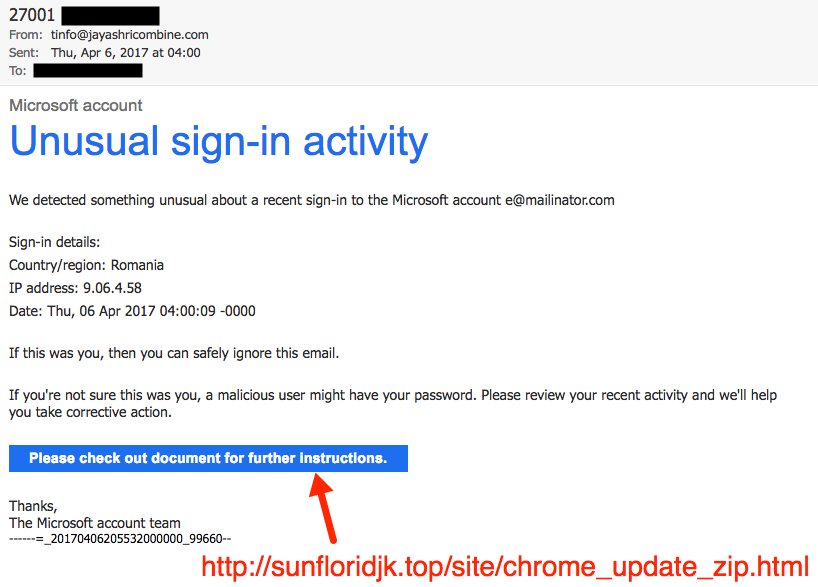
Shown above: Screen shot from the fake Microsoft email.
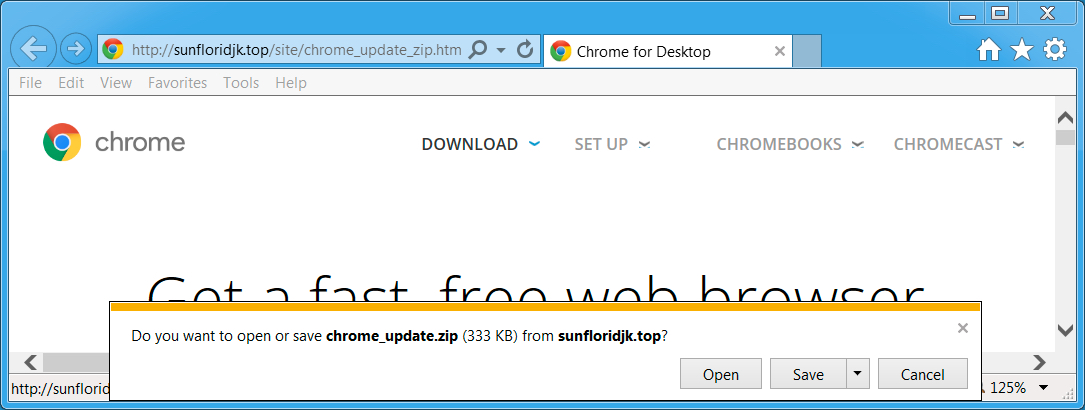
Shown above: Letting the fake Chrome page send a fake Chrome update as a zip archive.
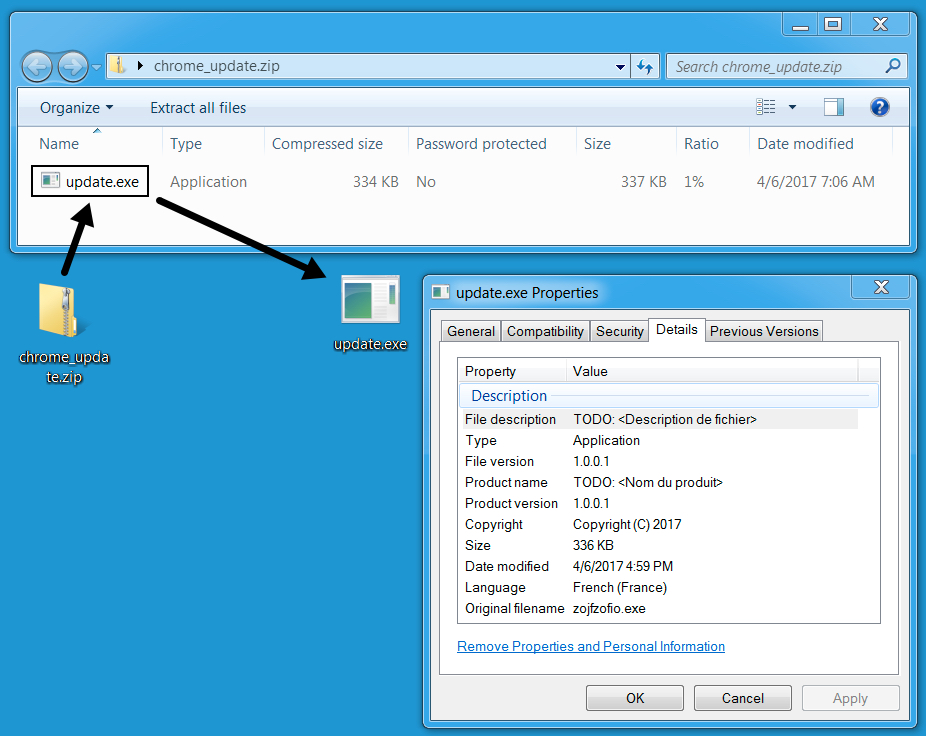
Shown above: Zip acrhive sent by the fake Chrome page contains (Cerber) ransomware.
TRAFFIC
HTTP TRAFFIC FOR THE RANSOMWARE FOR THE PAST FEW DAYS:
- 47.91.76[.]28 port 80 - www.gerbnopesa[.]top - GET /user.php?f=2.gif
- 47.91.76[.]28 port 80 - www.opennewsnz[.]top - GET /user.php?f=2.gif
- 52.37.58[.]18 port 80 - jhdgh[.]club - GET /search.php
- 52.37.58[.]18 port 80 - jhdgh[.]download - GET /search.php
- 52.37.58[.]18 port 80 - resettinfgd1991[.]gdn - GET /search.php
- 52.37.58[.]18 port 80 - resettinfgd1991[.]trade - GET /search.php
- 54.149.101[.]37 port 80 - jhdgh[.]online - GET /search.php
- 185.195.24[.]180 port 80 - www.bkasioqpz[.]top - GET /user.php?f=2.gif
- 185.195.24[.]180 port 80 - www.nowsunnygk[.]top - GET /user.php?f=2.gif
RANSOMWARE DOWNLOAD FROM FAKE CHROME INSTALL PAGE ON THURSDAY 2017-04-06:
- 47.91.76[.]28 port 80 - sunfloridjk[.]top - GET /site/chrome_update_zip.html
- 47.91.76[.]28 port 80 - sunfloridjk[.]top - GET /site/download_zip.php
MALWARE
SHA256 HASHES FOR CERBER RANSOMWARE SAMPLES:
- fb46fcb91063ce81a904bbf344cd96edb9f2a4858bec25970a7eb7cdfd962ed0 - from from-bkasioqpz[.]top
- d204d9b20ccac6f0345d60dffaa69f0e0f9aabf3e308c762a72771c1c1a828fc - from jhdgh[.]online
- fb46fcb91063ce81a904bbf344cd96edb9f2a4858bec25970a7eb7cdfd962ed0 - from nowsunnygk[.]top
- 7c8889178b79d5622179d20ac6b139ebbab2faa0b2a5577b6b4795b3091275c4 - from gerbnopesa[.]top
- feb092e7a07320c9a68d3a3c533dea8bc5a31dfea287c693efe88ac093e8005b - from jhdgh[.]club
- bc3a50dad8fcb284cdcaa8a2390a82718b98736fbcece22fcb17a83fc6de192d - from jhdgh[.]download
- 4ece34e4bdea5fa3013dbc98783c6814216b8b4b0d02f4a7ecb9177147878de7 - from opennewsnz[.]top
- cfedf50077efbe8ea47a9feb13ef6b35f491f0ecc17755f94bc407b415d10f78 - from resettinfgd1991[.]gdn
- ec34f6c58ad5788dd4b26d7d51bd5818144ea2774a188310da8ccb3bbc20e46c - from resettinfgd1991[.]trade
- bea332be44718de8640c5bee195704e5f713102f89e9fbc8fcb115770c5627bb - chrome_update.zip from sunfloridjk[.]top
- 9e78cbd01966ae356ccfafb9c753a08fce648b6e157b017d43ce6497c9d761f6 - extracted file from chrome_update.zip
IMAGES
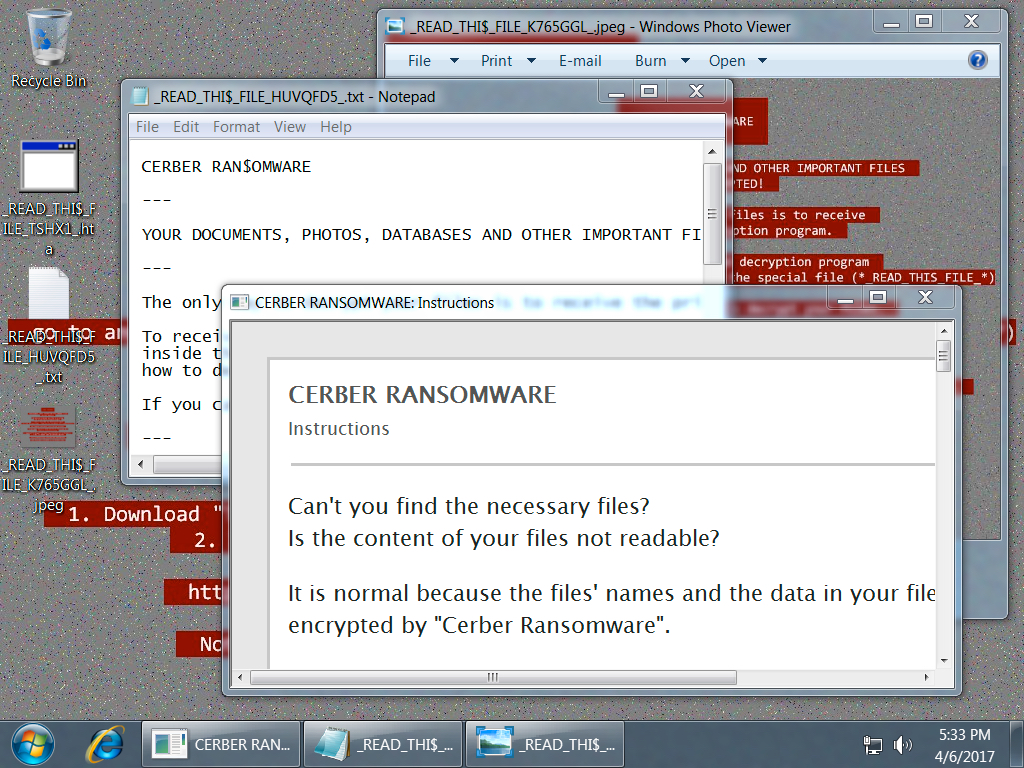
Shown above: Desktop of an infected Windows host. Note the dollar signs used for the letter S.
Click here to return to the main page.
