2017-05-03 - "BLANK SLATE" CAMPAIGN PUSHES GLOBEIMPOSTER RANSOMWARE VARIANT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
2017-05-03 update: This is actually a GlobeImposter ransomware variant instead of Globe ransomware as I originally thought. Updated the writeup.
ASSOCIATED FILES:
- 2017-05-03-GlobeImposter-ransomware-variant-from-newfornz_top.pcap.zip 153 kB (153,167 bytes)
- 2017-05-03-Blank-Slate-malspam-tracker.csv.zip 1.1 kB (1,104 bytes)
- 2017-05-03-Blank-Slate-emails-and-GlobeImposter-ransomware-variant.zip 269.8 kB (269,783 bytes)
BACKGROUND:
- For background on this campaign, see the Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- I wrote a follow-up for the Internet Storm Center (ISC) titled: "Blank Slate" malspam still pushing Cerber ransomware.
TODAY'S NOTES:
- Still seeing zip attachments containing .js files from the Blank Slate campaign.
- Yesterday, Blank Slate was pushing Mordor ransomware, but today it's pushing a different type ransomware.
- Based on the visual style of the decryption instructions, I thought this was a variant of Globe ransomware (link).
- After checking with @BleepinComputer, I found this is probably a GlobeImposter variant (different from the Globe ransomware family).
- No post-infection traffic was noted for this infection.
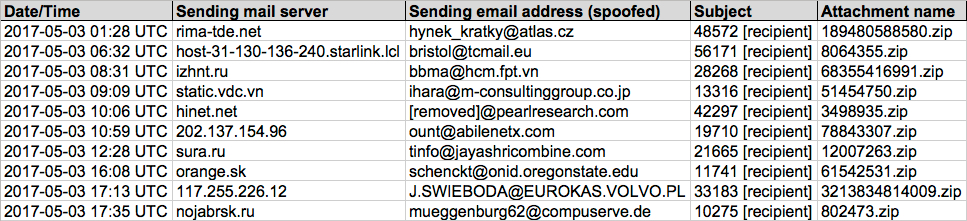
Shown above: Screenshot of spreadsheet tracker (1 of 2).
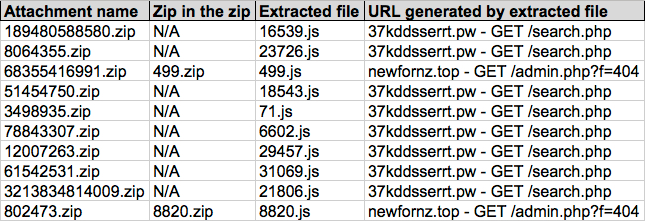
Shown above: Screenshot of spreadsheet tracker (1 of 2).
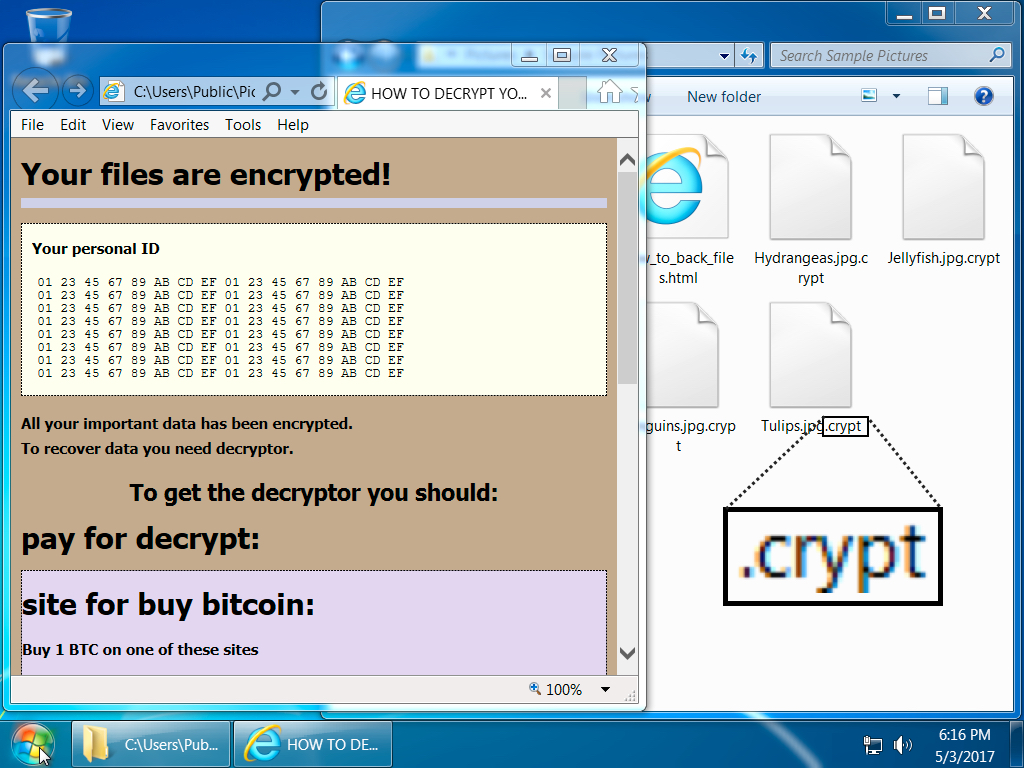
Shown above: Desktop of an infected Windows host.
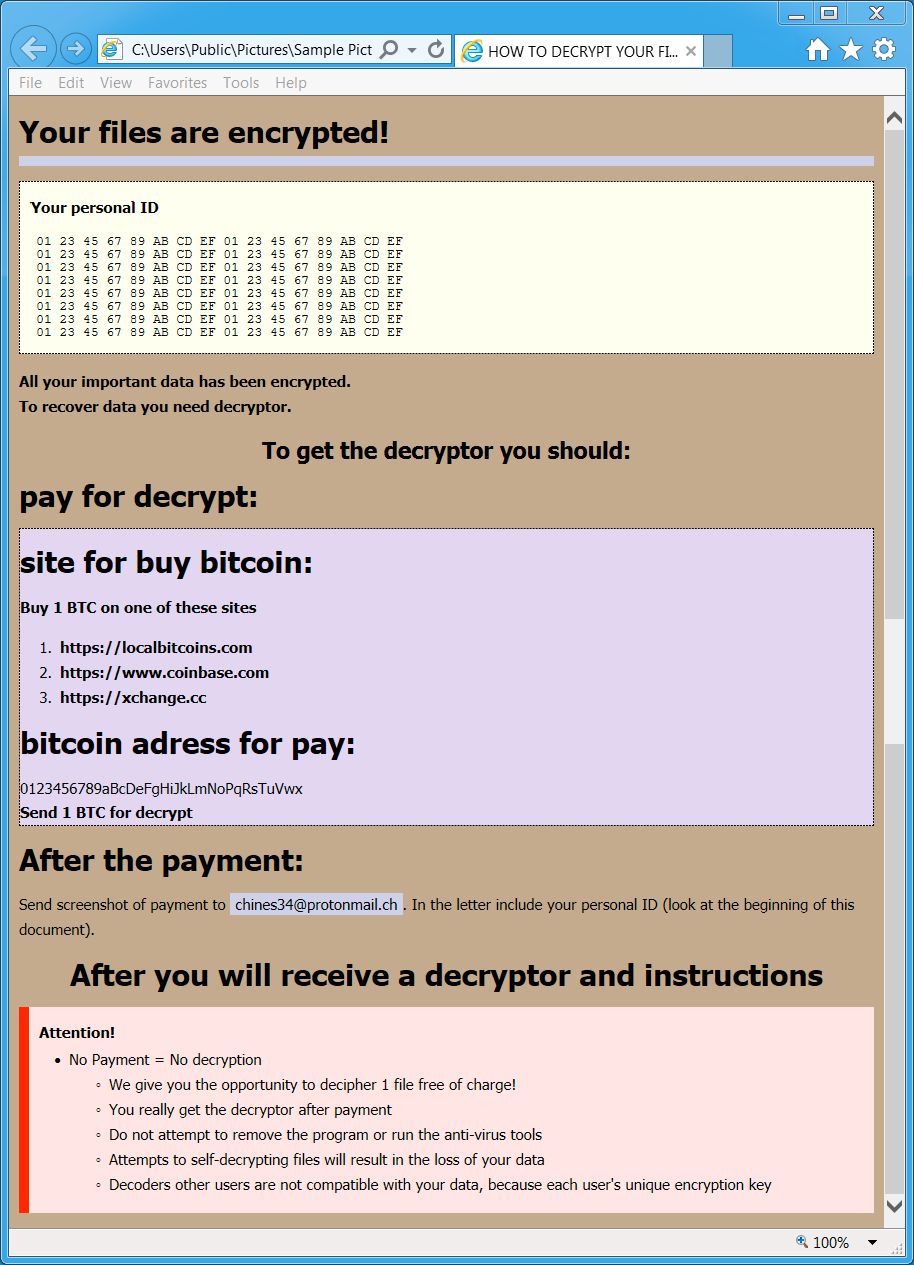
Shown above: Screenshot of the decryption instructions
TRAFFIC
URLS GENERATED BY THE EXTRACTED FILES:
- no IP address (domain didn't resolve) - 37kddsserrt[.]pw - GET /search.php
- 47.91.76[.]69 port 80 - newfornz[.]top - GET /admin.php?f=404
EMAIL FROM THE DECRYPTION INSTRUCTIONS:
- chines34@protonmail[.]ch
SHA256 HASHES
RANSOMWARE SAMPLE:
- SHA256 hash: 435dd2562e6423a2c9a0d4ca12fae43624cf13f71682fd1028b357e5540158db
File description: GlobeImposter ransomware variant from newfornz[.]top on 2017-05-03
Click here to return to the main page.
