2017-05-26 - COREBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-05-26-Corebot-infection-from-fake-DHL-site.pcap.zip 932.6 kB (932,590 bytes)
- 2017-05-26-Corebot-infection-from-fake-DHL-site.pcap (1,495,969 bytes)
- 2017-05-26-Corebot-emails-and-malware.zip 425.1 kB (425,102 bytes)
- 2017-05-25-DHL-themed-Corebot-malspam-024959-UTC.eml (1,255 bytes)
- 2017-05-25-DHL-themed-Corebot-malspam-225407-UTC.eml (1,237 bytes)
- 34cf4593-e97c-459b-b49d-bf21da142526.exe (284,514 bytes)
- invoice-0063827410370260857-000001870346531780753154078347.pdf.js (21,338 bytes)
- invoice-0063827410370260857-000001870346531780753154078347.zip (5985 bytes)
- jebfc.exe (272,226 bytes)
NOTES:
- Thanks to @mesa_matt who recently identified this as Corebot (link).
- I previously saw similar malspam pushing the same type of malware (without the fake DHL site) on 2017-04-28.
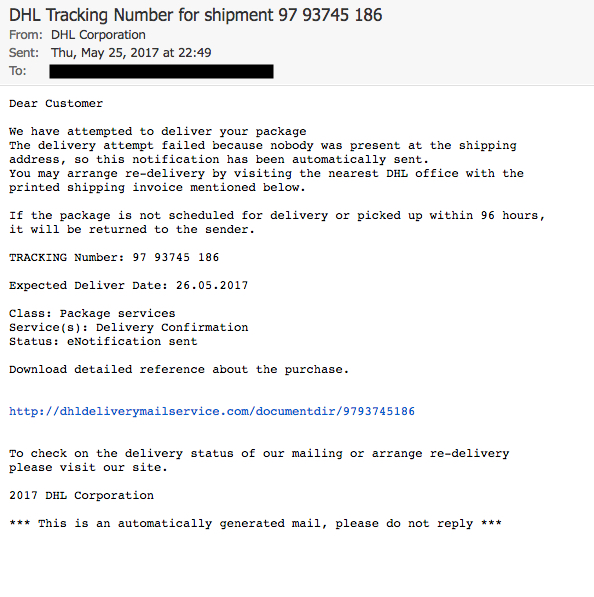
Shown above: Screenshot of one of the emails.
EMAIL HEADERS:
- Date/Time: Thursday 2017-05-25 at 22:49 UTC
- From: (spoofed) "DHL Corporation" <dhl@bulletproofmedia[.]biz>
- Subject: DHL Tracking Number for shipment 97 93745 186
- Date/Time: Thursday 2017-05-25 at 22:54 UTC
- From: (spoofed) "DHL Corporation" <dhl@digialbums[.]net>
- Subject: DHL Tracking Number for shipment 97 93745 186
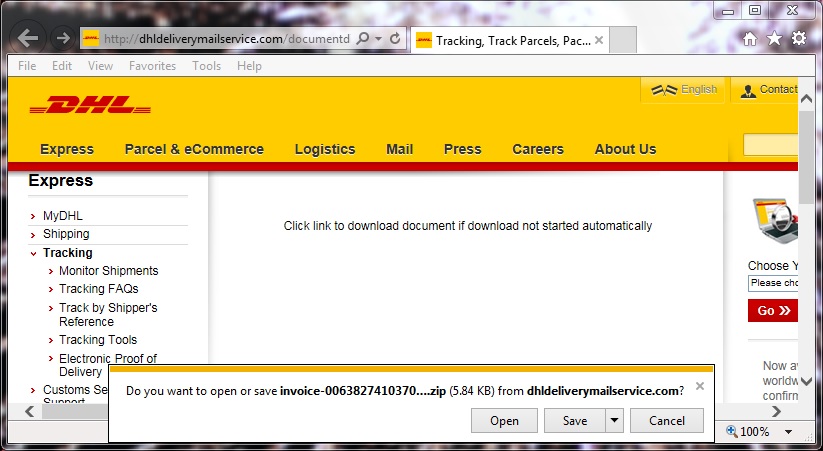
Shown above: Link from the email goes to a fake DHL page that sends a zip archive.
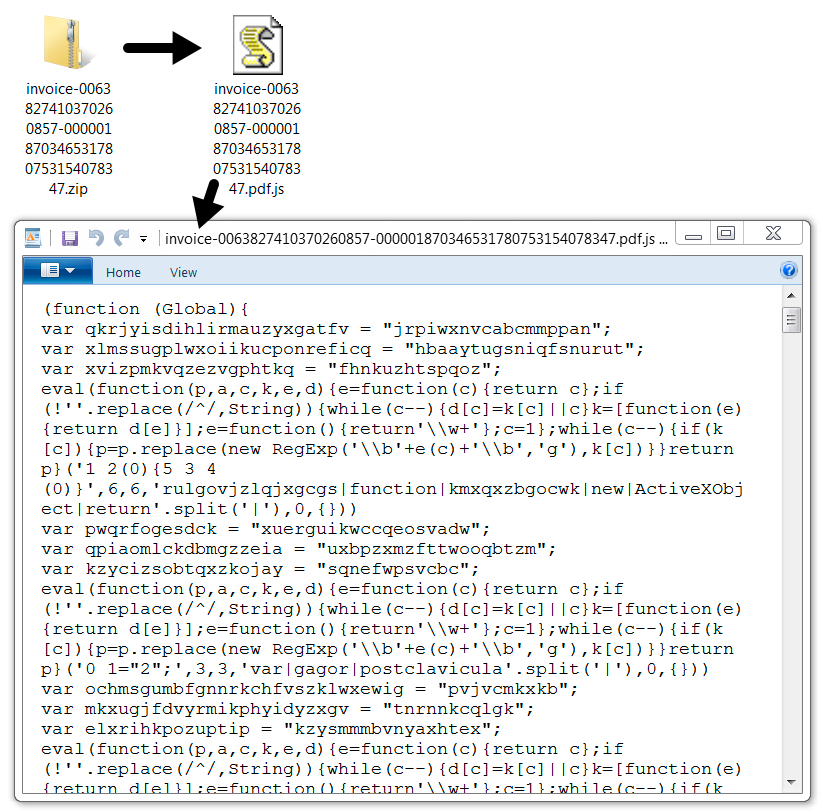
Shown above: Zip archive from the fake DHL page contains a .js downloader.
TRAFFIC
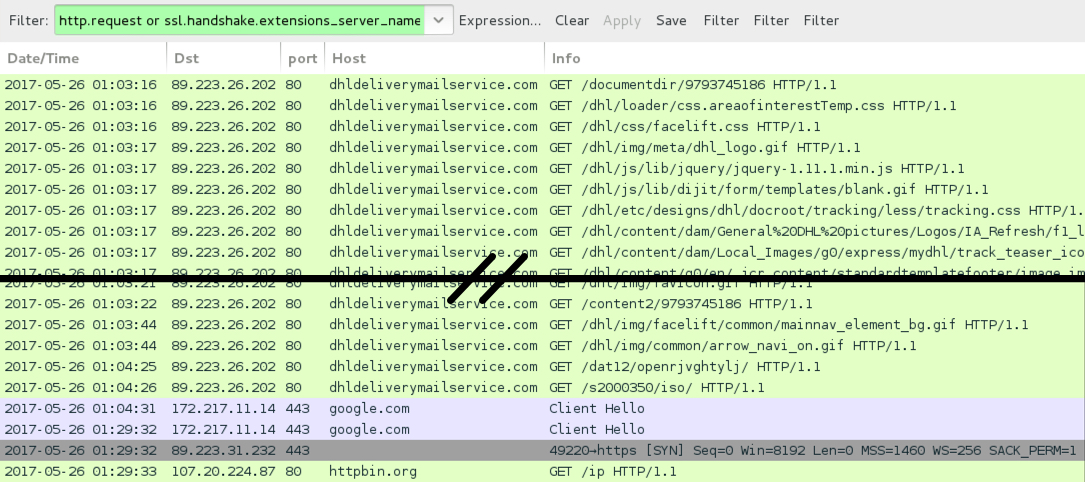
Shown above: Traffic from the infection filtered in Wireshark.
TRAFFIC FROM AN INFECTION:
- 89.223.26[.]202 port 80 - dhldeliverymailservice[.]com - GET /documentdir/9793745186 [URL for fake DHL page]
- 89.223.26[.]202 port 80 - dhldeliverymailservice[.]com - GET /content2/9793745186 [returned zip archive]
- 89.223.26[.]202 port 80 - dhldeliverymailservice[.]com - GET /s2000350/iso/ [returned Corebot EXE]
- 89.223.31[.]232 port 443 - 89.223.31[.]232 - HTTPS Corebot C2 traffic
- 107.20.224[.]87 port 80 - httpbin[.]org - GET /ip
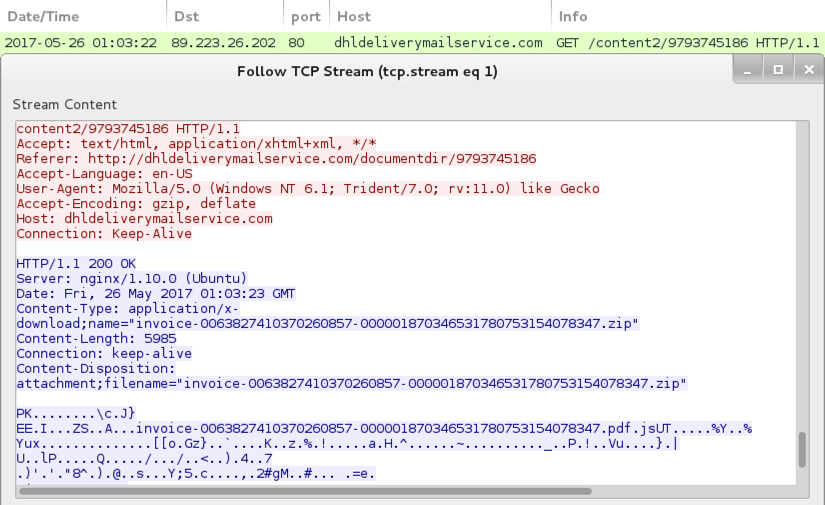
Shown above: TCP stream of fake DHL site sending the malicious zip archive.
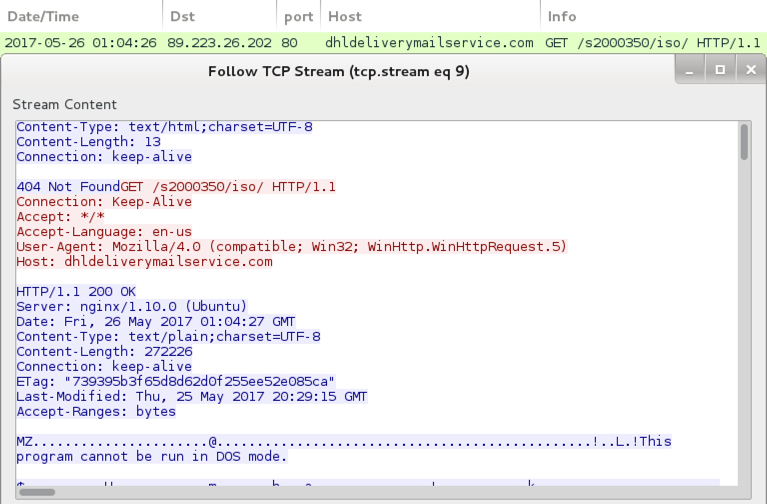
Shown above: TCP stream of HTTP request of the Windows executable for Corebot.
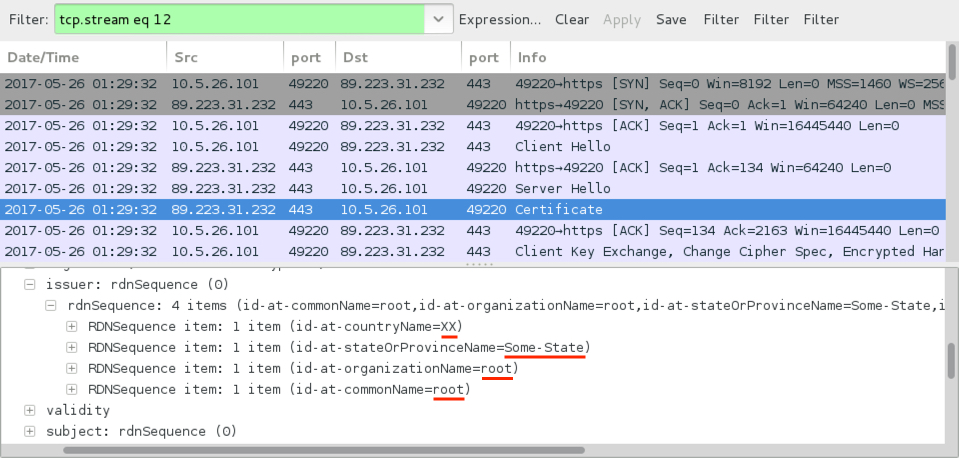
Shown above: Certificate data from the Corebot C2 traffic shown in Wireshark.
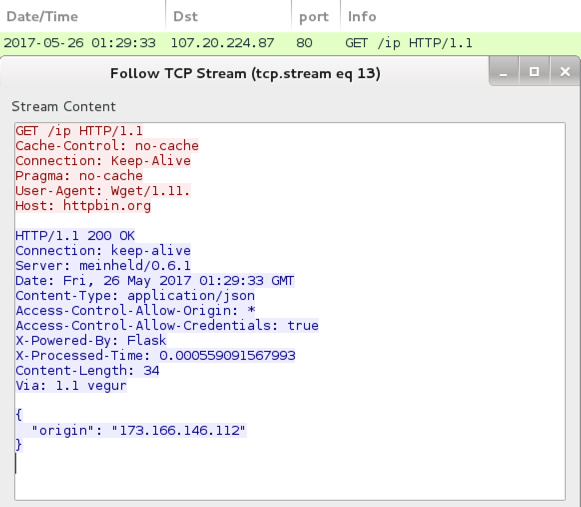
Shown above: TCP stream of an IP address check by the infected host.
FILE HASHES
ZIP ARCHIVE SENT BY FAKE DHL SITE:
- SHA256 hash: 387eeb5f35fc2b61d0c94c638f3eae78637441def39e77c81bf09d2653abe9d5
File name: invoice-0063827410370260857-000001870346531780753154078347.zip
File size: 5,985 bytes
File description: Malicious zip archive
- SHA256 hash: 7ad1e498d4a11d4dc221064525dd50b370a05e8dcfb481da4edf9a353e9322e5
File name: invoice-0063827410370260857-000001870346531780753154078347.pdf.js
File size: 21,338 bytes
File description: Extracted .js file
COREBOT MALWARE FROM THE INFECTED WINDOWS HOST:
- SHA256 hash: 3c74fe8c148812a0b5606aa19a81c98f30ec761f12924115ed8e02eb2f2e3213
File location: C:\Users\[username]\AppData\Local\Temp\jebfc.exe
File size: 272,226 bytes
File description: Windows EXE for Corebot downloaded by the extracted .js file
- SHA256 hash: 921e596509aeddde19888e76fa9b08df248950c8cb479920f5252b10aa25d0ae
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\66372fd0-8d07-4cab-9690-54a63e36d082\34cf4593-e97c-459b-b49d-bf21da142526.exe
File size: 284,514 bytes
File description: Windows EXE for Corebot persistent on the infected host
WINDOWS REGISTRY UPDATE:
- Registry key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Value name: bba00065-1351-41f5-b7a5-6d148cabed17
Value type: REG_SZ
Value data: rundll32 shell32.dll,ShellExec_RunDLL "C:\Users\[username]\AppData\Local\Microsoft\Windows\66372fd0-8d07-4cab-9690-54a63e36d082\34cf4593-e97c-459b-b49d-bf21da142526.exe"
IMAGES
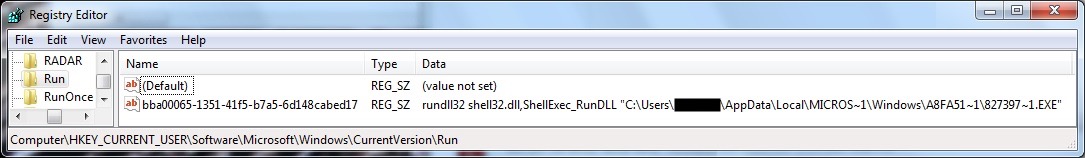
Shown above: Corebot malware persistent on the infected Windows host through a registry update.
Click here to return to the main page.
