2017-06-30 - RIG EK FROM HOOKADS CAMPAIGN SENDS CHTHONIC BANKING TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-30-HookAds-Rig-EK-sends-Chthonic.pcap.zip 2.4 MB (2,433,334 bytes)
- 2017-06-30-HookAds-Rig-EK-sends-Chthonic.pcap (2,946,243 bytes)
- 2017-06-30-HookAds-Rig-EK-artifacts-and-malware.zip 230 kB (230,173 bytes)
- 2017-06-30-HookAds-Rig-EK-payload-Chthonic.exe (256,512 bytes)
- 2017-06-30-HookAds-script-from-original-site-popunder.php.txt (1,247 bytes)
- 2017-06-30-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-06-30-Rig-EK-flash-exploit.swf (16,451 bytes)
- 2017-06-30-Rig-EK-landing-page.txt (61,294 bytes)
- 2017-06-30-operty.info-banners-bbwjobs.txt (6,397 bytes)
BACKGROUND ON THE HOOKADS CAMPAIGN:
- 2016-11-01 - Malwarebytes Blog: The HookAds malvertising campaign (link)
- 2017-05-14 - Zerophage Malware: Rig EK delivers Chthonic (link)
- 2017-06-14 - Zerophage Malware: Rig EK via malvertising drops Dreambot (link)
- 2017-06-20 - My previous blog on HookAds: Rig EK from HookAds campaign sends Dreambot and Chthonic (link)
BACKGROUND ON THE CHTHONIC BANKING TROJAN:
- 2014-12-18 - SecureList (run by Kaspserky Lab): Chthonic: a new modification of ZeuS (link)
TRAFFIC
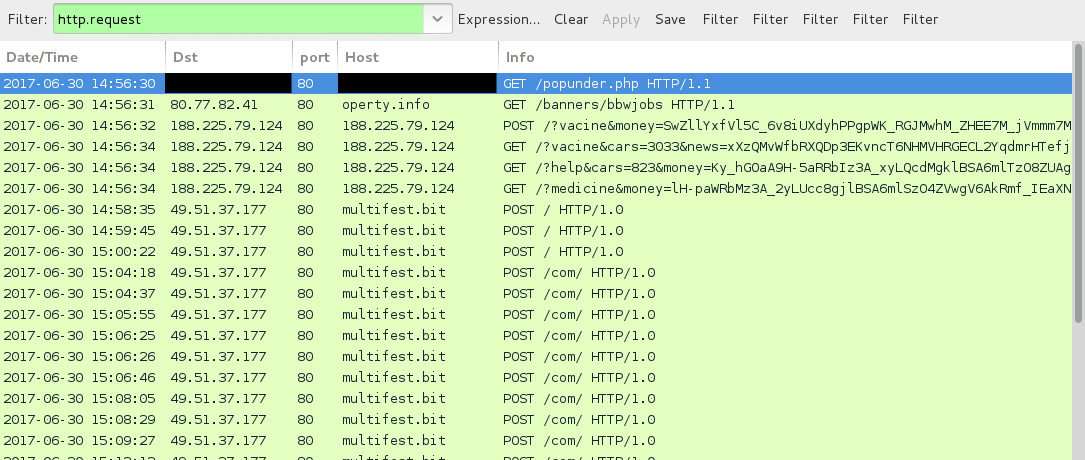
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- [ip address redacted] port 80 - [domain redacted] - GET /popunder.php - Injected code from original site
- 80.77.82[.]41 port 80 - operty.info - GET /banners/bbwjobs - HookAds redirect
- 188.225.79[.]124 port 80 - 188.225.79[.]124 - Rig EK
- Various IP addresses over TCP port 53 - DNS queries for multifest.bit
- 49.51.37[.]177 port 80 - multifest[.]bit - POST / - Chthonic post-infection traffic
- 49.51.37[].177 port 80 - multifest[.]bit - POST /com/ - Chthonic post-infection traffic
- 46.173.218[.]100 port 80 - multifest[].bit - attempted TCP connections, but no response from the server
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: aaec3850f24c100d0780145fcfb2fd982868f552dd102144c5c933b3b62c406f
File size: 16,451 bytes
File description: Rig EK flash exploit seen on 2017-06-30
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 61d8a0ed328566e570b00d224e29994c3f8d70e93e848f98b391d2d9e048c8b8
File size: 256,512 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File location: C:\Users\[username]\AppData\Roaming\Windows Mail\WeindowsMailU.exe
File description: HookAds campaign Rig EK payload seen on 2017-06-30 - Chthonic
IMAGES
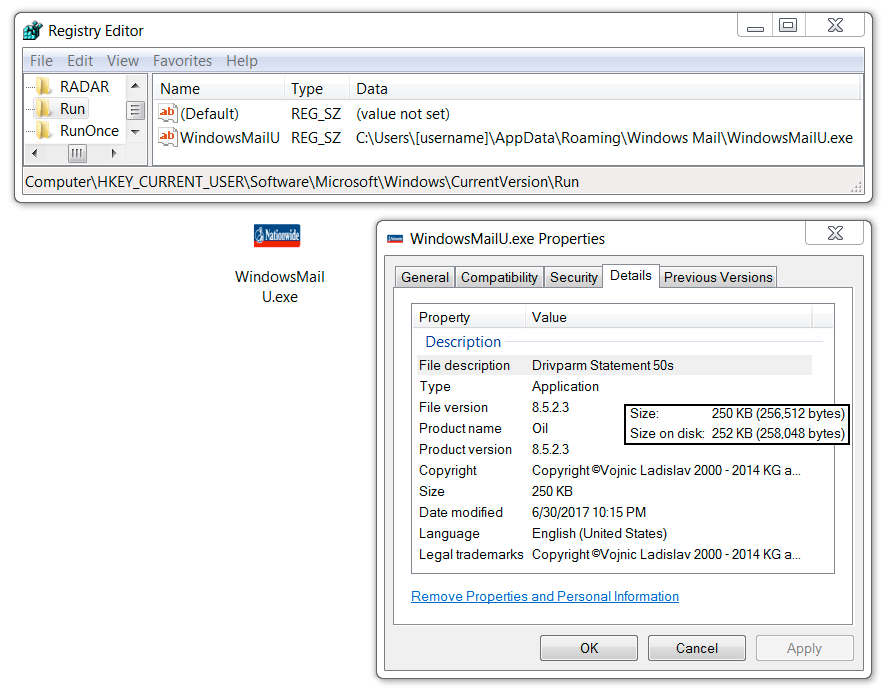
Shown above: Chthonic banking Trojan made persistent on the infected Windows host.
Click here to return to the main page.
