2017-07-03 - KOVTER INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-03-Kovter-infection-traffic.pcap.zip 3.4 MB (3,371,852 bytes)
- 2017-07-03-Kovter-infection-traffic.pcap (7,316,883 bytes)
- 2017-07-03-Kovter-emails-and-malware.zip 360.2 kB (360,260 bytes)
- 2017-06-30-UPS-themed-Kovter-malspam-1557-UTC.eml (3,825 bytes)
- 2017-07-01-UPS-themed-Kovter-malspam-2003-UTC.eml (3,773 bytes)
- 2017-07-02-UPS-themed-Kovter-malspam-0930-UTC.eml (3,702 bytes)
- 2017-07-03-Kovter-sample-retrieved-by-js-file.exe (485,261 bytes)
- UPS-Label-07584276.doc.js (1,750 bytes)
- UPS-Label-07584276.zip (1,442 bytes)
- UPS-Package-06520201.doc.js (1,648 bytes)
- UPS-Package-06520201.zip (1,439 bytes)
- UPS-Package-07907895.doc.js (1,682 bytes)
- UPS-Package-07907895.zip (1,448 bytes)
RELATED BLOG POSTS:
- malware-traffic-analysis.net (this blog) - 2017-06-29: Kovter infection (link)
OTHERS NOTES:
- Post-infection characteristics from my infected lab host are pretty much the same as I saw last time (see my link above).
EMAILS
EMAIL HEADERS:
- Date: Friday 2017-06-30 at 15:57 UTC
- From: networkc@server.srv2eua[.]com[.]br
- Subject: Courier was not able to deliver your parcel (ID07907895, UPS)
- Attachment: UPS-Package-07907895.zip
- Date: Saturday 2017-07-01 at 20:03 UTC
- From: anonymous@hosting-fabrika[.]ru
- Subject: Please recheck your delivery address (UPS parcel 06520201)
- Attachment: UPS-Package-06520201.zip
- Date: Sunday 2017-07-02 at 09:30 UTC
- From: webmaster@std-simbirsk[.]ru
- Subject: Parcel ID07584276 delivery problems, please review
- Attachment: UPS-Label-07584276.zip
TRAFFIC
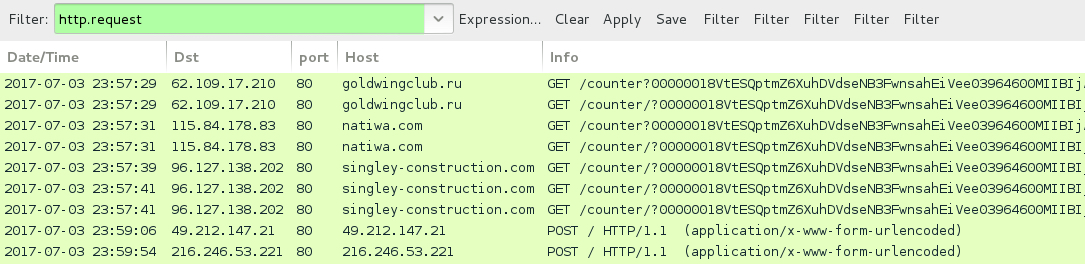
Shown above: Traffic from an infection on 2017-07-03 using one of the extracted .js files, filtered in Wireshark.
PARTIAL URLS RECOVERED FROM THE .JS FILES:
- artdecorfashion[.]com - GET /counter [followed by long string of characters]
- csasesores[.]com[.]ar - GET /counter [followed by long string of characters]
- desinano[.]com[.]ar - GET /counter [followed by long string of characters]
- elita5[.]md - GET /counter [followed by long string of characters]
- goldwingclub[.]ru - GET /counter [followed by long string of characters]
- natiwa[.]com - GET /counter [followed by long string of characters]
- resedaplumbing[.]com - GET /counter [followed by long string of characters]
- singley-construction[.]com - GET /counter [followed by long string of characters]
- uploadmiller.miller-media[.]at - GET /counter [followed by long string of characters]
- vademecsa[.]com[.]ar - GET /counter [followed by long string of characters]
- vindexsa[.]com[.]ar - GET /counter [followed by long string of characters]
- winnicemoldawii[.]pl - GET /counter [followed by long string of characters]
- www.gloszp[.]pl - GET /counter [followed by long string of characters]
POST-INFECTION TRAFFIC:
- Various IP addresses and over TCP ports 80, 443, and 8080.
FILE HASHES
EMAIL ATTACHMENTS:
- SHA256 hash: de65e744295133f3c5c606d84947ce934a7562a941e29e83b675bbb66d78e7de
File name: UPS-Package-07907895.zip
- SHA256 hash: 714609929d73714ce1a45a2c17ecaf4ce94275d635858cbaea5e562e850a2a86
File name: UPS-Package-06520201.zip
- SHA256 hash: ac34b856837a8462952f8f3dcda6aead4e9333be653ae76dd08a69517c533927
File name: UPS-Label-07584276.zip (corrupt zip archive)
EXTRACTED .JS FILES:
- SHA256 hash: f577049733d77cf4abf99374741804257821c20d34f0f2986a83e1815512505f
File name: UPS-Package-07907895.doc.js
- SHA256 hash: 2d8a7a9265096a443a70ad640491d9e7063a76969e0ec7b1aec2ad8ecd4c288a
File name: UPS-Package-06520201.doc.js
- SHA256 hash: f645bed551d4188e84d5ced3239e033cc8869f754081c108de6481c32b962620
File name: UPS-Label-07584276.doc.js
KOVTER SAMPLE DOWNLOADED BY ONE OF THE .JS FILES:
- SHA256 hash: 5addc5c129282e9705b65b7156134e1c752a9ed2379a75471795c5c95e2a2110
File description: Kovter sample retrieved by one of the .js files on 2017-07-03
Click here to return to the main page.
