2017-07-10 - RIG EK FROM THE HOOKADS CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-10-HookAds-Rig-EK-traffic-3-pcaps.zip 10.9 MB (10,861,474 bytes)
- 2017-07-10-1st-run-HookAds-Rig-EK.pcap (5,353,889 bytes)
- 2017-07-10-2nd-run-HookAds-Rig-EK.pcap (3,324,185 bytes)
- 2017-07-10-3rd-and-4th-run-HookAds-Rig-EK.pcap (2,823,591 bytes)
- 2017-07-10-HookAds-Rig-EK-malware-and-artifacts.zip 569.2 kB (569,241 bytes)
- 2017-07-10-1st-run-Rig-EK-landing-page.txt (61,281 bytes)
- 2017-07-10-1st-run-homocyte_info-banners-counterhits.txt (6,397 bytes)
- 2017-07-10-1st-run-script-from-HookAds-related-site-popunder.php.txt (1255 bytes)
- 2017-07-10-2nd-run-Rig-EK-landing-page.txt (121,916 bytes)
- 2017-07-10-2nd-run-homocyte_info-banners-counterhits.txt (6,465 bytes)
- 2017-07-10-2nd-run-script-from-HookAds-related-site-popunder.php.txt (1,255 bytes)
- 2017-07-10-3rd-run-Rig-EK-landing-page.txt (121,927 bytes)
- 2017-07-10-3rd-run-homocyte_info-banners-counterhits.txt (6,473 bytes)
- 2017-07-10-3rd-run-script-from-HookAds-related-site-popunder.php.txt (1,255 bytes)
- 2017-07-10-4th-run-Rig-EK-landing-page.txt (121,981 bytes)
- 2017-07-10-4th-run-homocyte_info-banners-counterhits.txt (6,377 bytes)
- 2017-07-10-4th-run-script-from-HookAds-related-site-popunder.php.txt (1,255 bytes)
- 2017-07-10-HookAds-Rig-EK-payload-1st-thru-3rd-runs.exe (291,328 bytes)
- 2017-07-10-HookAds-Rig-EK-payload-4th-run.exe (204,800 bytes)
- 2017-07-10-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-07-10-Rig-EK-flash-exploit.swf (14,732 bytes)
BACKGROUND ON THE HOOKADS CAMPAIGN:
- 2016-11-01 - Malwarebytes Blog: The HookAds malvertising campaign (link)
- 2017-05-14 - Zerophage Malware: Rig EK delivers Chthonic (link)
- 2017-06-14 - Zerophage Malware: Rig EK via malvertising drops Dreambot (link)
- 2017-06-30 - My previous blog on HookAds: Rig EK from HookAds campaign sends Chthonic banking Trojan (link)
NOTES:
- In the 3rd pcap, the browser crashed and restarted, creating another infection chain with a different malware payload.
TRAFFIC
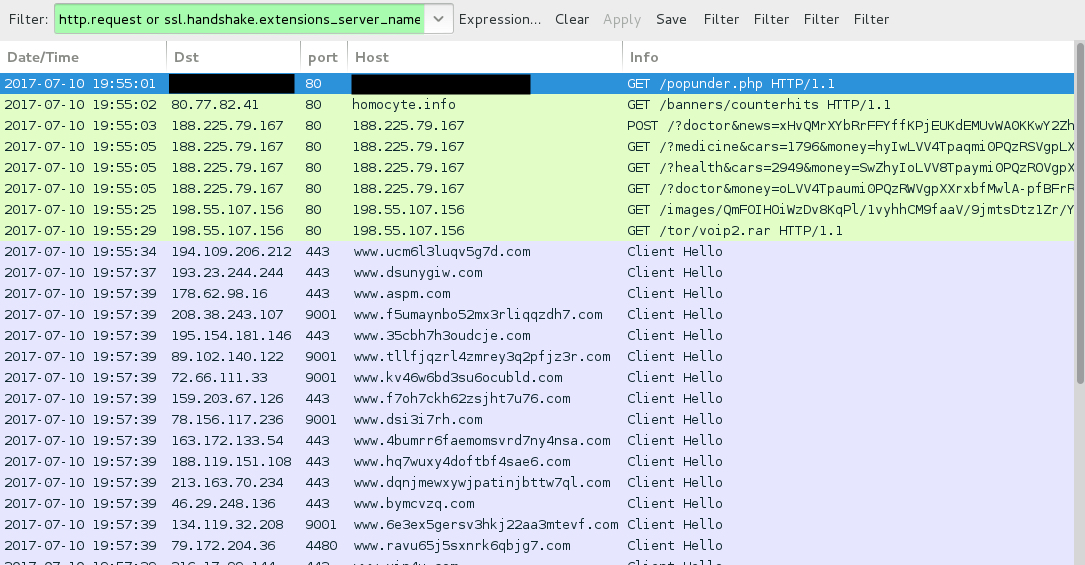
Shown above: Traffic from the 1st pcap filtered in Wireshark.
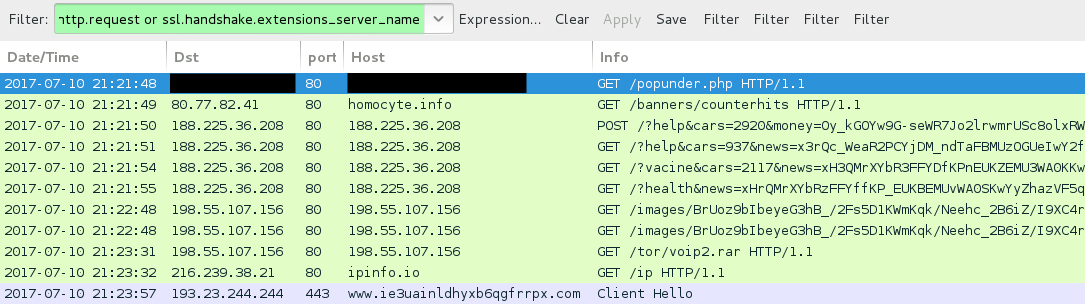
Shown above: Traffic from the 2nd pcap filtered in Wireshark.
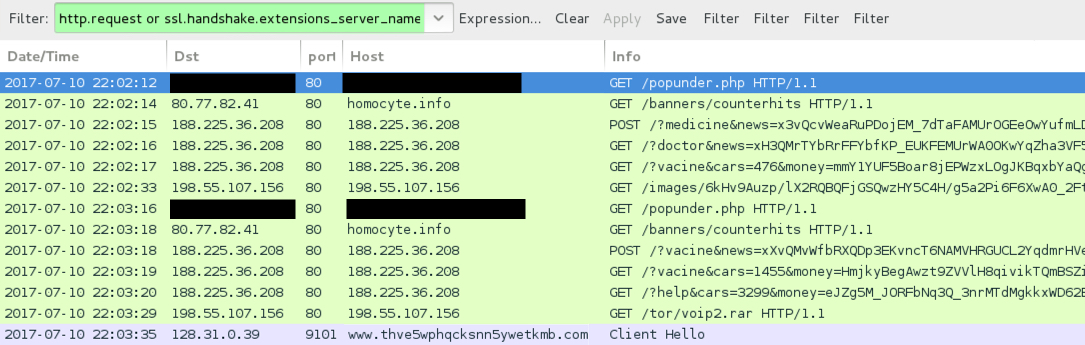
Shown above: Traffic from the 3rd pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- [information removed] port 80 - [information removed] - GET /popunder.php [injected script from HookAds-related site]
- 80.77.82[.]41 port 80 - homocyte[.]info - GET /banners/counterhits [gate/redirect]
- 188.225.79[.]167 port 80 - 188.225.79[.]167 - Rig EK - 1st run
- 188.225.36[.]208 port 80 - 188.225.36[.]208 - Rig EK - 2nd through 4th runs
- 198.55.107[.]156 port 80 - 198.55.107[.]156 - post-infection HTTP traffic
- port 80 - ipinfo[.]io - GET /ip [post-infection HTTP traffic]
- Various IP addresses and over various ports - Tor traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 2b9588b100426be65a1805ba825385aa708bc27cabbf07b3a8e9262c760a69ab
File size: 14,732 bytes
File description: Rig EK flash exploit seen on 2017-07-10
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 5e09e3f7e8e1f94f1556969a89715f555cff5ff999b2e4402e044d4fb5d60ffc
File size: 291,328 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File description: HookAds Rig EK payload, 1st through 3rd runs on 2017-07-10
- SHA256 hash: d3a7e88986498cae0482f1f44d649a3caa8a84eec7721c3f812cc42e4b62f076
File size: 204,800 bytes
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].exe
File description: HookAds Rig EK payload, 4th run on 2017-07-10
Click here to return to the main page.
