2017-07-21 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-21-Infostealer-infection-from-Brazil-malspam.pcap.zip 3.0 MB (2,950,452 bytes)
- 2017-07-21-Infostealer-infection-from-Brazil-malspam.pcap (3,391,724 bytes)
- 2017-07-21-Boleto-email-and-malware-from-an-infection.zip 4.9 MB (4,898,326 bytes)
- 20072017008184910142830132981348292017.pdf (46,878 bytes)
- 20072017008184910142830132981348292017.vbs (2,678 bytes)
- 2017-07-21-0830-UTC-Boleto-malspam.eml (64,604 bytes)
- 2017-07-21-Boleto-malspam-artifacts-information.csv (2,127 bytes)
- ANDRELLY-PC.aes (16 bytes)
- ANDRELLY-PC.zip (3,283,290 bytes)
- ANDRELLY-PCx.ocx (384 bytes)
- Ionic.Zip.Reduced.dll (253,440 bytes)
- SYSANDRELLYPC55.xml (3,380 bytes)
- c.cer (905 bytes)
- crov.exe (1,690,096 bytes)
- dll.dll.exe (396,480 bytes)
- niljxqjz.g3t.vbs (118 bytes)
- ps.exe (452,608 bytes)
- rff5waw2.4w2.vbs (136 bytes)
- taskmgrs.exe (2 bytes)
NOTES:
- As noted in a previous post about this activity (link), since mid-June 2017 there's been a PDF attachment included with these emails.
- The PDF attachment has a different link than the email, but they both redirect to the same bit[.]ly URL to send the same VBS malware.
- As usual, most of the artifacts found on the infected host are not inherently malicious. It's just the way they're being used.
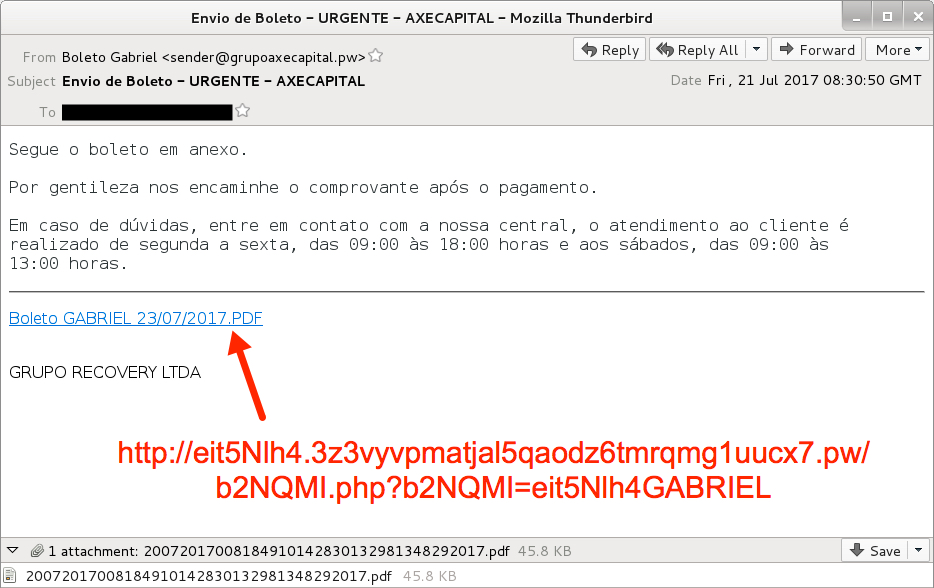
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Sending mail server: grupoaxecapital[.]pw
- From: Boleto [recipient's name] <sender@grupoaxecapital[.]pw>
- Subject: Envio de Boleto - URGENTE - AXECAPITAL
- Date: Friday, 2017-07-21 08:30 UTC
- Attachment name: 20072017008184910142830132981348292017.pdf
- Link from the message: eit5Nlh4.3z3vyvpmatjal5qaodz6tmrqmg1uucx7[.]pw/b2NQMI.php?b2NQMI=eit5Nlh4[recipient's name]
ATTACHMENT
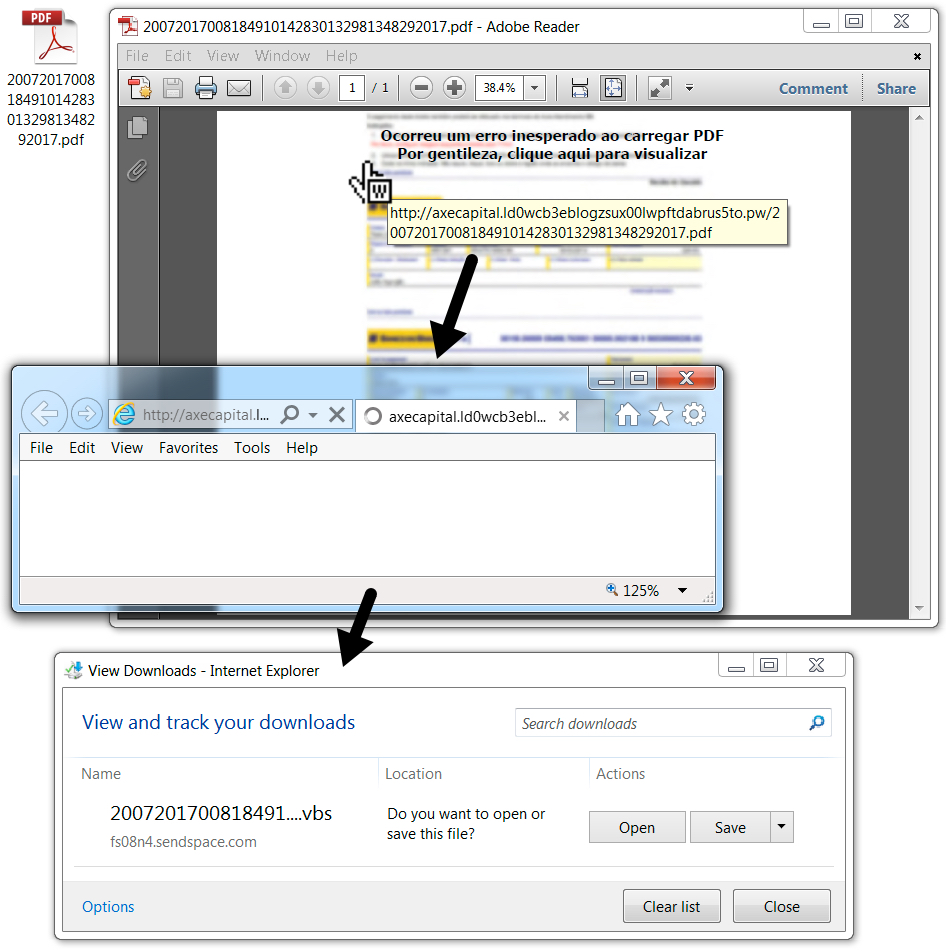
Shown above: Link from the PDF attachment downloads a VBS file.
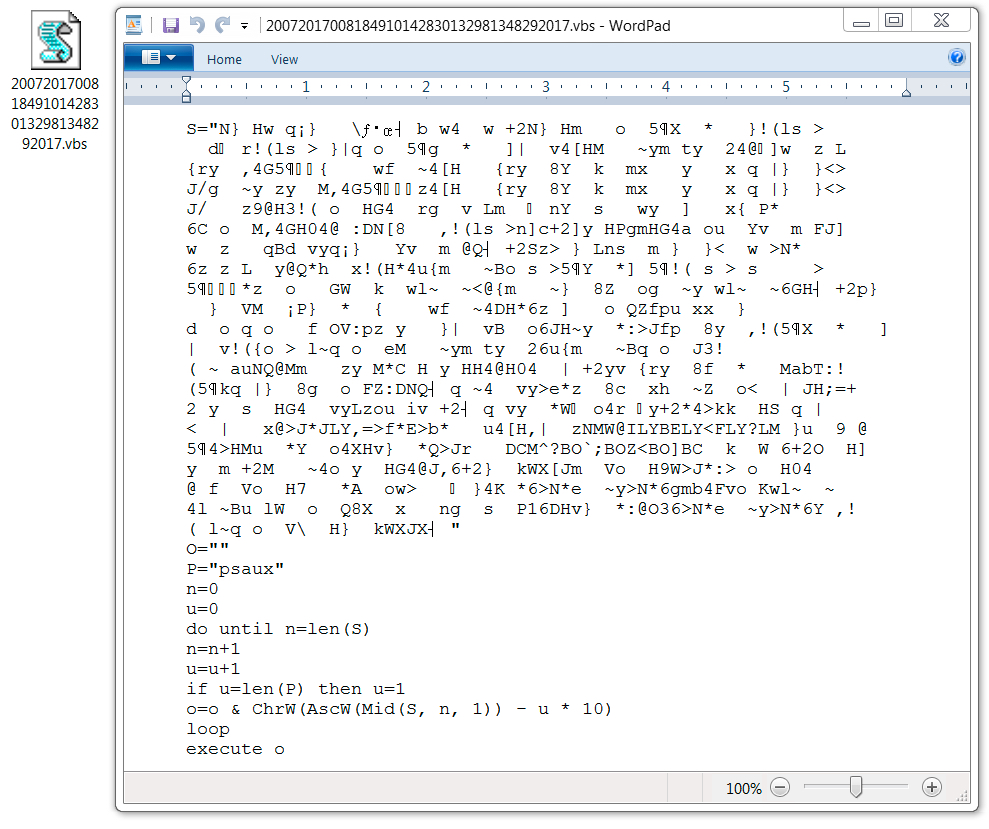
Shown above: The downloaded VBS file.
TRAFFIC
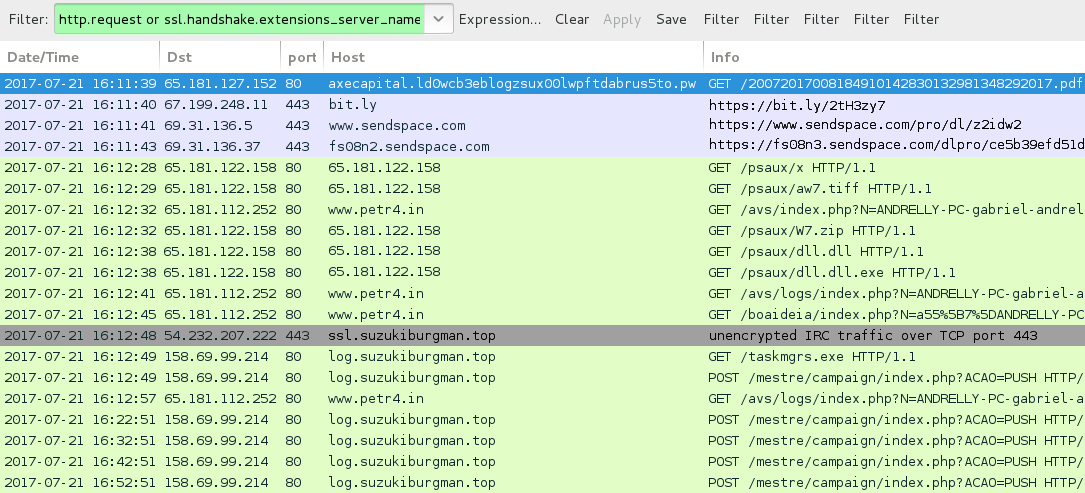
Shown above: Traffic from an infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 65.181.127[.]152 port 80 - eit5Nlh4.3z3vyvpmatjal5qaodz6tmrqmg1uucx7[.]pw - GET /b2NQMI.php?b2NQMI=eit5Nlh4[recipient's name] [link from email]
- 65.181.127[.]152 port 80 - axecapital.ld0wcb3eblogzsux00lwpftdabrus5to[.]pw - GET /20072017008184910142830132981348292017.pdf [link from PDF attchment]
- bit[.]ly - GET /2tH3zy7 [HTTPS]
- www.sendspace[.]com - GET /pro/dl/z2idw2 [HTTPS]
- fs08n3.sendspace[.]com - GET /dlpro/ce5b39efd51d32fcae48ea48c4d444ad/59723a93/z2idw2/20072017008184910142830132981348292017.vbs [HTTPS]
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /psaux/x
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /psaux/aw7.tiff
- 65.181.112[.]252 port 80 - www.petr4[.]in - GET /avs/index.php?[string of characters]
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /psaux/W7.zip
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /psaux/dll.dll
- 65.181.122[.]158 port 80 - 65.181.122[.]158 - GET /psaux/dll.dll.exe
- 65.181.112[.]252 port 80 - www.petr4[.]in - GET /avs/logs/index.php?[string of characters]
- 65.181.112[.]252 port 80 - www.petr4[.]in - GET /boaideia/index.php?[string of characters]
- 54.232.207[.]222 port 443 - ssl.suzukiburgman[.]top - unencrypted IRC traffic
- 158.69.99[.]214 port 80 - log.suzukiburgman[.]top - POST /mestre/admin/x.php
- 158.69.99[.]214 port 80 - log.suzukiburgman[.]top - GET /askmgrs.exe
- 158.69.99[.]214 port 80 - log.suzukiburgman[.]top - POST /mestre/campaign/index.php?ACAO=PUSH
- DNS query for imestre.suzukiburgman[.]top - Response: 127.0.0.1
MALWARE
PDF ATTACHMENT:
- SHA256 hash: 441cdbedbd900c5be9bd75d92cea85b08175e54e2a9bcc6b928a2844bccee0ff
File size: 46,878 bytes
File name: 20072017008184910142830132981348292017.pdf
DOWNLOADED VBS FILE:
- SHA256 hash: 0cc5c6082894c31ee1ff769e9bb1902183c8d4383e4046888687464846aa58c0
File size: 2,678 bytes
File name: 20072017008184910142830132981348292017.vbs
ARTIFACTS
SOME ARTIFACTS FOUND ON THE INFECTED (WINDOWS 7) HOST:
- C:\Users\[username]\AppData\Local\Temp\Java\Ionic.Zip.Reduced.dll
- C:\Users\[username]\AppData\Local\Temp\Java\[HOSTNAME].aes
- C:\Users\[username]\AppData\Local\Temp\Java\[HOSTNAME].zip
- C:\Users\[username]\AppData\Local\Temp\Java\dll.dll.exe
- C:\Users\[username]\AppData\Local\Temp\Java\[8 alpha-numeric characters].[3 alpha-numeric characters].vbs
- C:\Users\[username]\AppData\Local\Temp\0003.txt
- C:\Users\[username]\AppData\Local\Temp\ps.exe
- C:\Windows\System32\Java\Ionic.Zip.Reduced.dll
- C:\Windows\System32\Java\[HOSTNAME].aes
- C:\Windows\System32\Java\[HOSTNAME].zip
- C:\Windows\System32\[HOSTNAME]x.ocx
- C:\Windows\System32\c.cer
- C:\Windows\System32\crov.exe
- C:\Windows\System32\[8 alpha-numeric characters].[3 alpha-numeric characters].vbs
- C:\Windows\System32\taskmgrs.exe
IMAGES
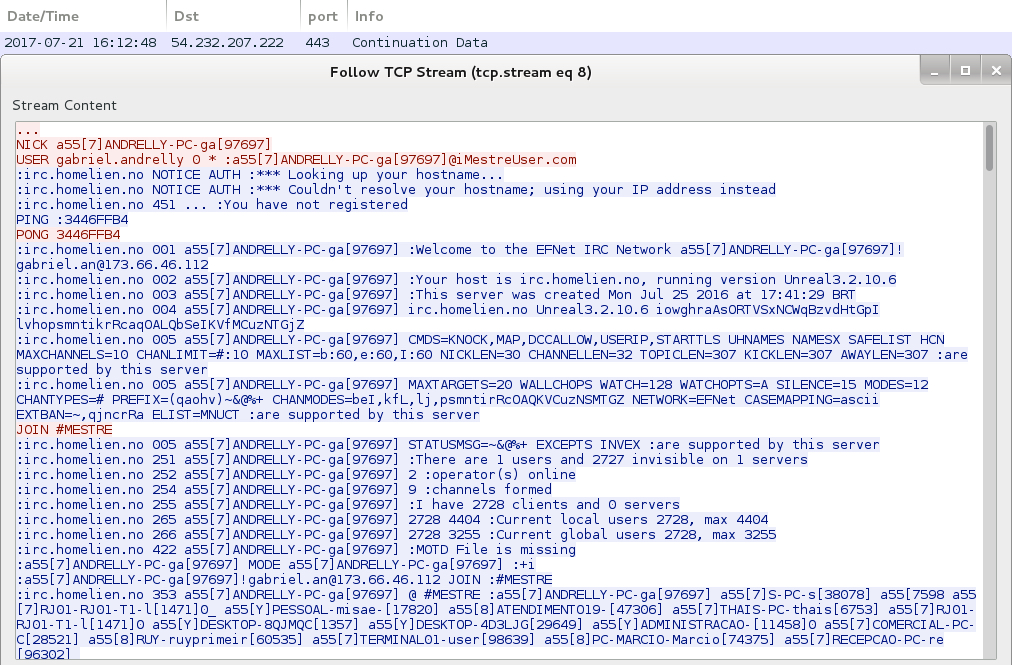
Shown above: Some of the unencrypted IRC traffic noted over TCP port 443.
Click here to return to the main page.
