2017-08-21 - TRICKBOT INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-08-21-Trickbot-infection-traffic.pcap.zip 934 kB (934,466 bytes)
- 2017-08-21-Trickbot-infection-traffic.pcap (1,246,136 bytes)
- 2017-08-21-Trickbot-malspam-0924-UTC.eml.zip 65.0 kB (64,958 bytes)
- 2017-08-21-Trickbot-malspam-0924-UTC.eml (133,295 bytes)
- 2017-08-21-malware-from-Trickbot-infection.zip 338.6 kB (338,643 bytes)
- 2017-08-21-Trickbot-Vpjnf.bat.txt (332 bytes)
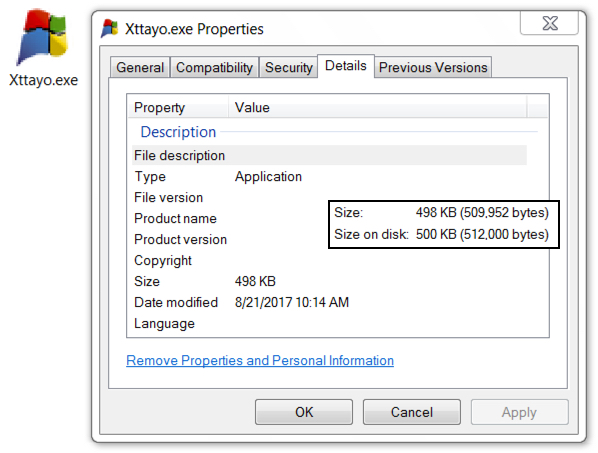
- 2017-08-21-Trickbot-Xttayo.exe (509,952 bytes)
- 2017-08-21-Trickbot-services_update.xml.txt (3,950 bytes)
- NatWest258345907_2243.doc (96,258 bytes)
ASSOCIATED BLOG POSTS:
- My Online Security - Posts for Trickbot
- 2017-08-12 - Malware-Traffic-Analysis.net - Malspam continues to push Trickbot banking Trojan
- 2017-08-15 - Internet Storm Center (ISC) - Malspam pushing Trickbot banking Trojan
HEADER INFORMATION:
- Date: Monday, 2017-08-21 09:24 UTC
- Message-ID: <000001d31a78$7f5d1240$7e1736c0$@ml>
- From: New post NatWest Bank <noreply@natwest78[.]ml>
- Subject: NatWest
- Attachment: NatWest258345907_2243.doc
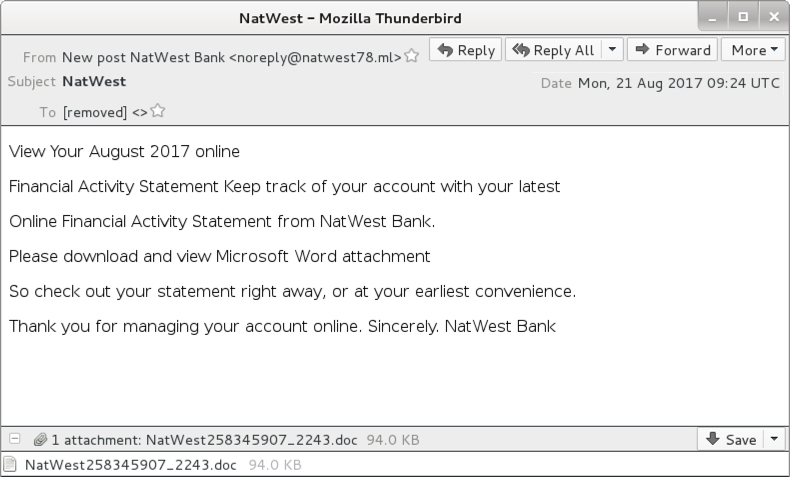
Shown above: Screenshot of the email.
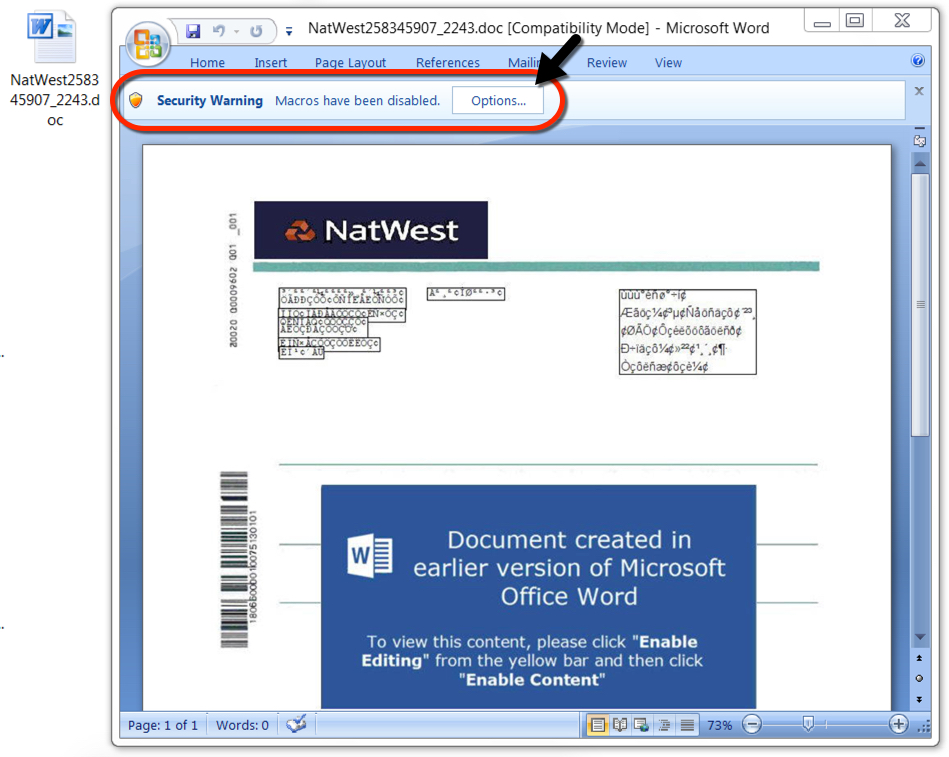
Shown above: Attachment from the email.
TRAFFIC
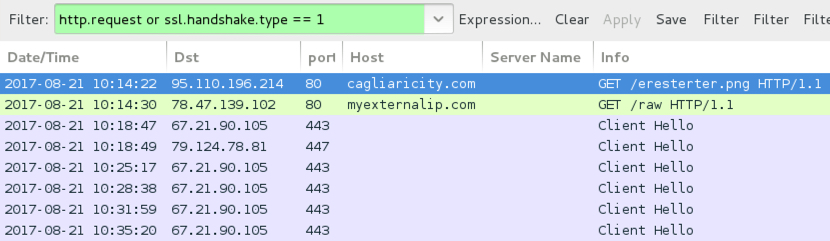
Shown above: Traffic from an infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 95.110.196[.]214 port 80 - cagliaricity[.]com - GET /eresterter.png [URL generated by Word macro to retrieve Trickbot binary]
- 69.64.57[.]170 port 80 - cepsanny[.]com[.]br - GET /Laudos/eresterter.png [URL generated by Word macro to retrieve Trickbot binary]
- 67.21.90[.]105 port 443 - post-infection HTTPS/SSL/TLS traffic from Trickbot-infected host
- 79.124.78[.]81 port 447 - post-infection HTTPS/SSL/TLS traffic from Trickbot-infected host
- 72.211.215[.]68 port 449 - post-infection connection attempts from Trickbot-infected host
MALWARE
EMAIL ATTACHMENT (WORD DOCUMENT):
- SHA256 hash: b895c34ecf45d111049a34fe69fdc4dce634de42d93fd1438b8e0c2e582217d8
File name: NatWest258345907_2243.doc
File size: 96,258 bytes
TRICKBOT BINARY:
- SHA256 hash: >a573c781543b04747f259278de09908b1a76b2afc6c00cc6bb1eeefa4df43756
File location: C:\Users\[username]\AppData\Local\Temp\Xttayo.exe
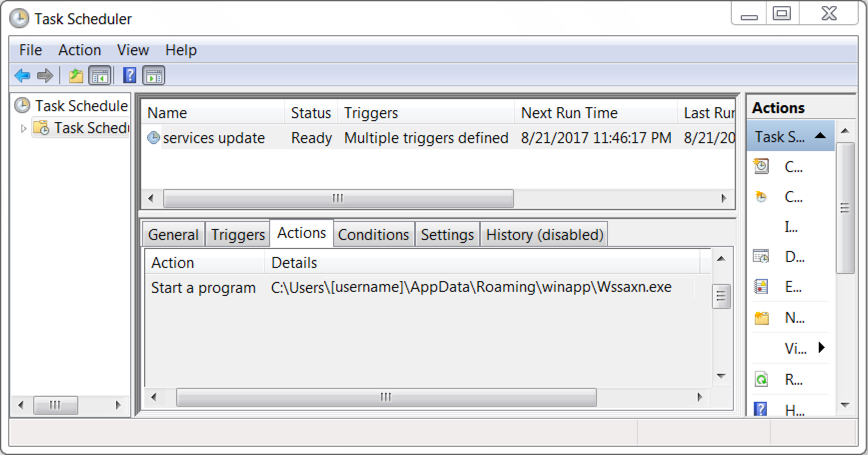
File location: C:\Users\[username]\AppData\Roaming\winapp\Wssaxn.exe
File size: 509,952 bytes
Shown above: Today's Trickbot binary.
Shown above: Scheduled task to keep Trickbot malware persistent after a reboot.
Click here to return to the main page.