2017-09-08 - EITEST CAMPAIGN FAKE AV ALERTS / HOEFLERTEXT POPUPS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-08-EITest-campaign-2-pcaps.zip 4.1 MB (4,083,816 bytes)
- 2017-09-08-EITest-HoeflerText-popup-and-NetSupport-Manager-RAT-infection.pcap (5,472,748 bytes)
- 2017-09-08-EITest-fake-AV-page-for-tech-support-scam.pcap (416,367 bytes)
- 2017-09-08-EITest-campaign-malware-and-artifacts.zip 7.9 MB (7,905,077 bytes)
- 2017-09-08-DSAdaDSDA.js.txt (4,630 bytes)
- 2017-09-08-Font_Chrome.exe (287,988 bytes)
- 2017-09-08-NetSupport-Manager-RAT-installer-8vpv5aazn.jpg.exe (3,804,458 bytes)
- 2017-09-08-base62-string-for-NetSupport-Manager-RAT-installer.txt (5,072,612 bytes)
- 2017-09-08-client32.ini.txt (969 bytes)
- 2017-09-08-fake-AV-page-audio.mp3 (262,144 bytes)
- 2017-09-08-fake-AV-page-from-angel07091.tk.txt (4,374 bytes)
- 2017-09-08-page-from-mintdentistryplano_com-with-injected-EITest-script-for-HoelferText-popup.txt (179,923 bytes)
- 2017-09-08-page-from-mintdentistryplano_com-with-injected-EITest-script-for-fake-AV-alert.txt (134,848 bytes)
NOTES:
- Mostly the same indicators as yesterday, but a different compromised site to kick off the infection chain. See my previous blog post for indicators and more information.
- Related tweet on 2017-09-08 from @killamjr: https://twitter.com/killamjr/status/906149309476888576
Shown above: @killamjr's tweet.
SOME IMAGES
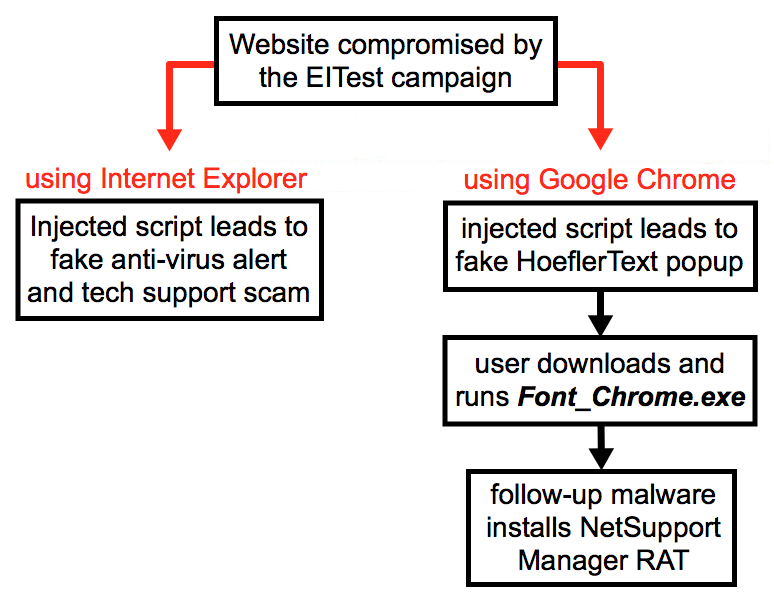
Shown above: Current flow chart for activity caused by the EITest campaign.
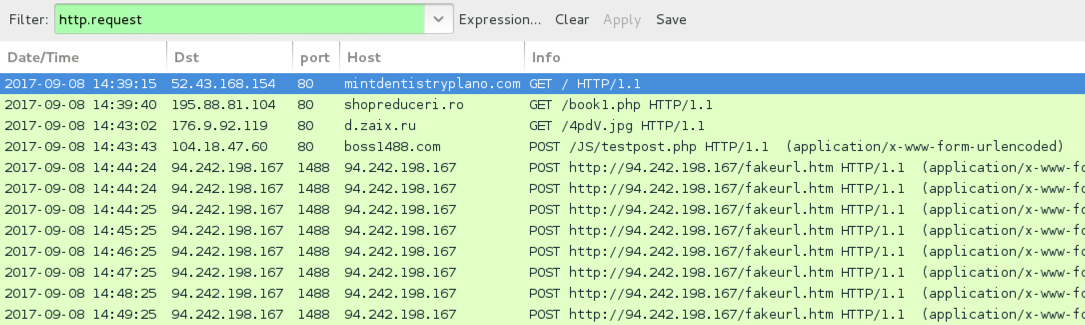
Shown above: Traffic for HoeflerText popup and NetSupport Manager RAT infection.
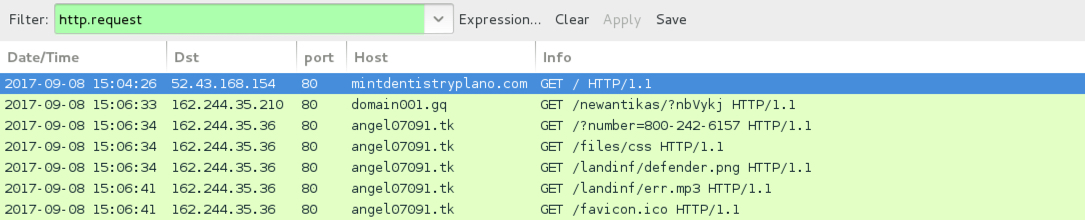
Shown above: Traffic for fake anti-virus page and tech support scam.
Click here to return to the main page.

