2017-09-15 - BLANK SLATE CAMPAIGN PUSHES LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-15-Blank-Slate-campaign-pushes-Locky-ransomware-4-pcaps.zip 2.2 MB (2,159,739 bytes)
- 2017-09-15-Blank-Slate-malspam-tracker.csv.zip 1.0 kB (1,012 bytes)
- 2017-09-15-Blank-Slate-emails-and-Locky-ransomware-files.zip 2.6 MB (2,623,805 bytes)
SOME BACKGROUND:
- 2017-03-02 - Palo Alto Networks Unit 42 Blog: "Blank Slate" Campaign Takes Advantage of Hosting Providers to Spread Ransomware.
- 2017-03-22 - Internet Storm Center (ISC): "Blank Slate" malspam still pushing Cerber ransomware.
- 2017-06-29 - ISC: Catching up with Blank Slate: a malspam campaign still going strong.
- 2017-07-31 - Bleeping Computer: Crypt GlobeImposter Ransomware Distributed via Blank Slate Malspam.
- 2017-08-02 - Malware-Traffic-Analysis.net: "Blank Slate" malspam pushing Gryphon ransomware (a BTCware variant).
TODAY'S NOTES:
- Others have seen emails from the Blank Slate campaign today. See (this Twitter thread for more info).
- Today's Blank Slate now has one line of message text that reads: Dear [recipient's email address]
- Blank Slate is still pushing "Lukitus" variant Locky ransomware, just like earlier this week.
- And as usual for these Word documents, once I enabled macros, they only infected my lab hosts after I closed the documents.
EMAILS
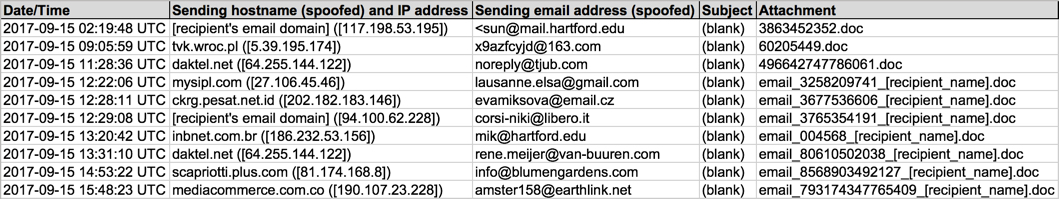
Shown above: Screenshot from the spreadsheet tacker.
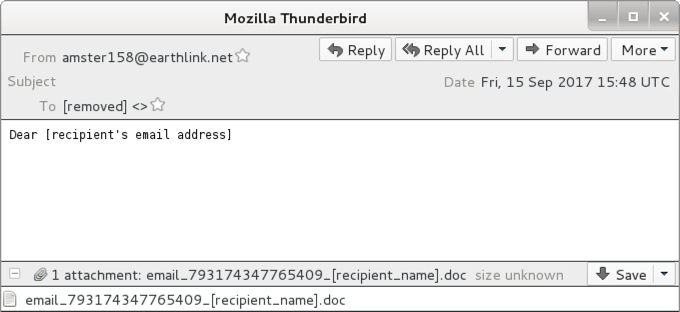
Shown above: Screen shot from one of the emails.
EMAILS COLLECTED:
- 2017-09-15 02:19:48 UTC -- From (spoofed): sun@mail.hartford[.]edu -- Attachment name: 3863452352.doc
- 2017-09-15 09:05:59 UTC -- From (spoofed): x9azfcyjd@163[.]com -- Attachment name: 60205449.doc
- 2017-09-15 11:28:36 UTC -- From (spoofed): noreply@tjub[.]com -- Attachment name: 496642747786061.doc
- 2017-09-15 12:22:06 UTC -- From (spoofed): lausanne.elsa@gmail[.]com -- Attachment name: email_3258209741_[recipient's name].doc
- 2017-09-15 12:28:11 UTC -- From (spoofed): evamiksova@email[.]cz -- Attachment name: email_3677536606_[recipient's name].doc
- 2017-09-15 12:29:08 UTC -- From (spoofed): corsi-niki@libero[.]it -- Attachment name: email_3765354191_[recipient's name].doc
- 2017-09-15 13:20:42 UTC -- From (spoofed): mik@hartford[.]edu -- Attachment name: email_004568_[recipient's name].doc
- 2017-09-15 13:31:10 UTC -- From (spoofed): rene.meijer@van-buuren[.]com -- Attachment name: email_80610502038_[recipient's name].doc
- 2017-09-15 14:53:22 UTC -- From (spoofed): info@blumengardens[.]com -- Attachment name: email_8568903492127_[recipient's name].doc
- 2017-09-15 15:48:23 UTC -- From (spoofed): amster158@earthlink[.]net -- Attachment name: email_793174347765409_[recipient's name].doc
TRAFFIC
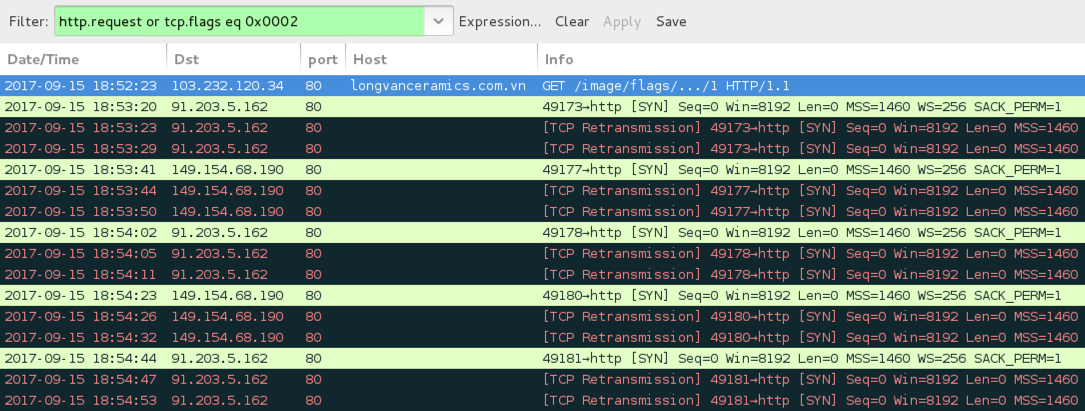
Shown above: Example of the infection traffic filtered in Wireshark.
URLS FROM THE WORD MACROS TO DOWNLOAD FOLLOW-UP MALWARE (LOCKY RANSOMWARE):
- hxxp[:]//ekolapsm[.]top/admin.php?f=1
- hxxp[:]//rockjonadd[.]top/admin.php?f=1
- hxxp[:]//longvanceramics[.]com[.]vn/image/flags/.../1
- hxxp[:]//tsivn[.]com[.]vn/system/logs/.../1
POST-INFECTION IP ADDRESSES (SAW ATTEMPTED TCP CONNECTIONS BUT NO HTTP TRAFFIC):
- 91.203.5[.]162
- 149.154.68[.]190
USUAL TOR DOMAIN FOR THE LOCKY DECRYPTOR:
- g46mbrrzpfszonuk[.]onion
ASSOCIATED FILES
Shown above: Example of an attachment from one of the emails.
ATTACHED WORD DOCUMENTS:
- 2fa25ea384f8efde34dbe3cdee16c6fdfbd62ce55961df284d091f997081dce3 - 60205449.doc
- 5b964c0a583a01250f25e1e09e46e6ac7befe68ddf92a3ffd4ab268880c41dc8 - 496642747786061.doc
- 6242181dd9b4f06513e9b8f02ba4bae8cb4191c2a9d14e37b21f51262eca647c - email_004568_[recipient_name].doc
- 3547d4ac076df971793aefb96725707a2210ef4865d78071f673cffdb91c3e53 - email_3258209741_[recipient_name].doc
- d0f4d65d71f46638cb4b303c8d7a8df9a91fecbea0b1b11ff5795333f8391868 - email_3677536606_[recipient_name].doc
- 1a3c2718dadea11348ea5261537283c04bafec8edf7731019e207fe067540aee - email_3765354191_[recipient_name].doc
- b4f4348646d549f9ad8fb27d7e353754cf7a66aa455dd71f0cf16479bb5117c7 - email_80610502038_[recipient_name].doc
- 3acb44fc695152116307bf0bb7f993bcda70b4c356f8b65d0c2f022724319d91 - email_8568903492127_[recipient_name].doc
- de667ee7ed36a884e45d575e1dd9cc98031d1989be6821fae88bb1e59b267a50 - email_793174347765409_[recipient_name].doc
FOLLOW-UP MALWARE (LOCKY RANSOMWARE):
- SHA256 hash: 0899e1d9edfde06e1d21969909a0c06599913fdfc3e45e70548f4935e8cd443b
File size: 649,216 bytes
File description: Locky binary from ekolapsm.top or rockjonadd.top
- SHA256 hash: a22f3b70bef87484d70aaf5f2952dc7cf92aa4bbd55ad90d81989ada54f33279
File size: 676,352 bytes
File description: Locky ransomware binary from longvanceramics[.]com[.]vn or tsivn[.]com[.]vn
IMAGES
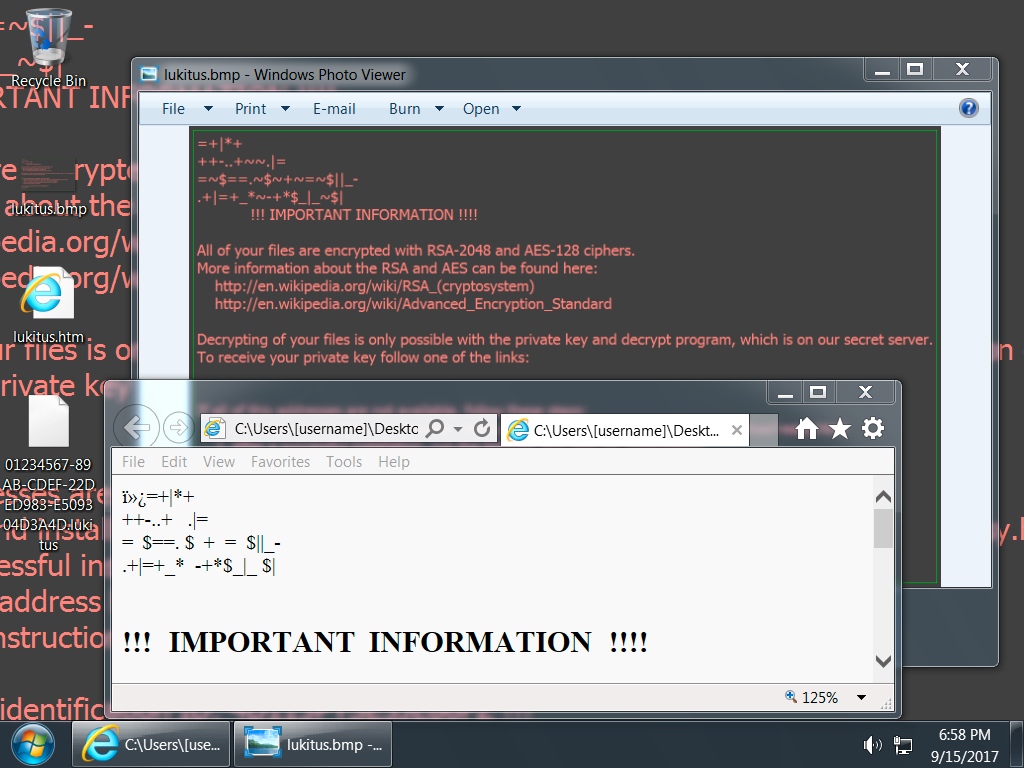
Shown above: Desktop of an infected Windows host.
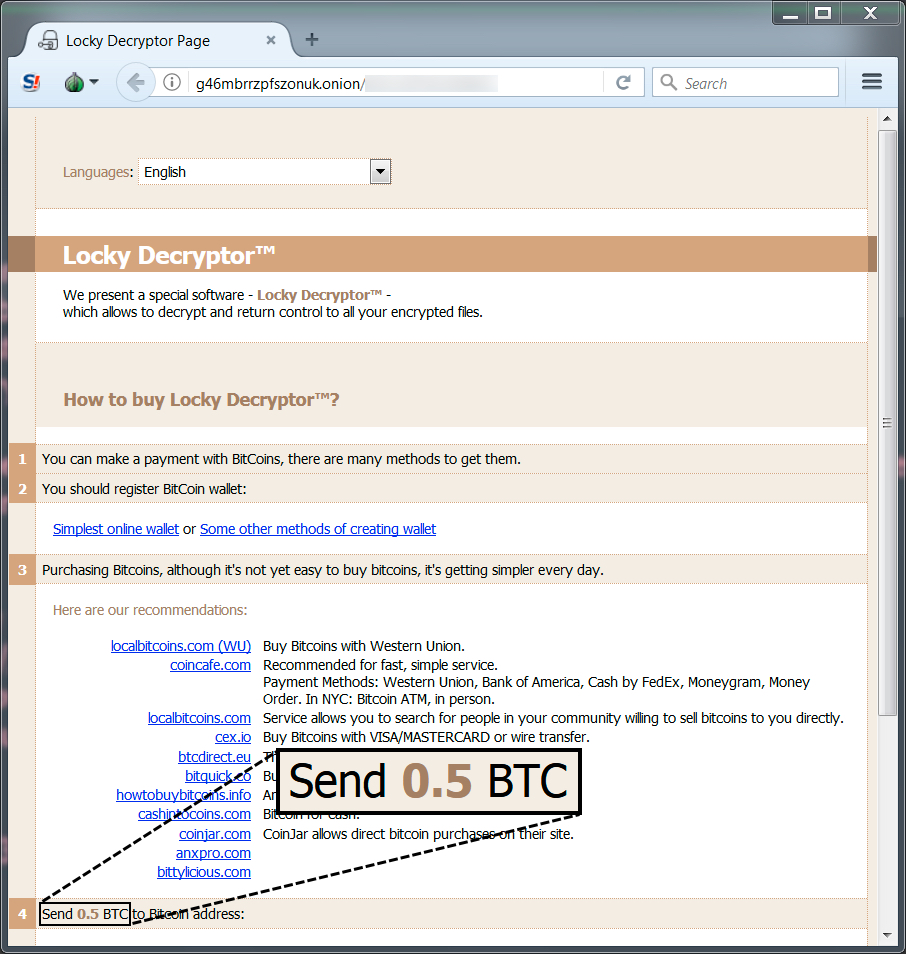
Shown above: The Locky decryptor showing today's ransom cost.
Click here to return to the main page.
