2017-09-22 - INFOSTEALER INFECTION FROM BOLETO MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-09-22-Boleto-themed-infostealer-infection-traffic.pcap.zip 738 kB (737,886 bytes)
- 2017-09-22-Boleto-themed-infostealer-infection-traffic.pcap (865,555 bytes)
- 2017-09-22-Boleto-themed-email-and-associated-malware.zip 1.2 MB (1,224,025 bytes)
- 1508201700016067882247230289631.pdf (9,198 bytes)
- 2017-09-22-Boleto-malspam-1758-UTC.eml (68,488 bytes)
- 250920178234282343294329423.exe (356,352 bytes)
- E-Enviar.txt (21 bytes)
- EQATEC.Analytics.Monitor.dll (160,768 bytes)
- FiddlerCore.dll (430,424 bytes)
- FiddlerRoot.cer (950 bytes)
- chaves3.zip (400,460 bytes)
- idfptray.exe (5,675,008 bytes)
- micos.txt (0 bytes)
NOTES:
- Today I saw different malware than seen in my last post about this malspam on 2017-08-28.
- The PDF attachment has a different link than the email, but they both redirected to the same drive.google[.]com URL to send the same EXE malware.
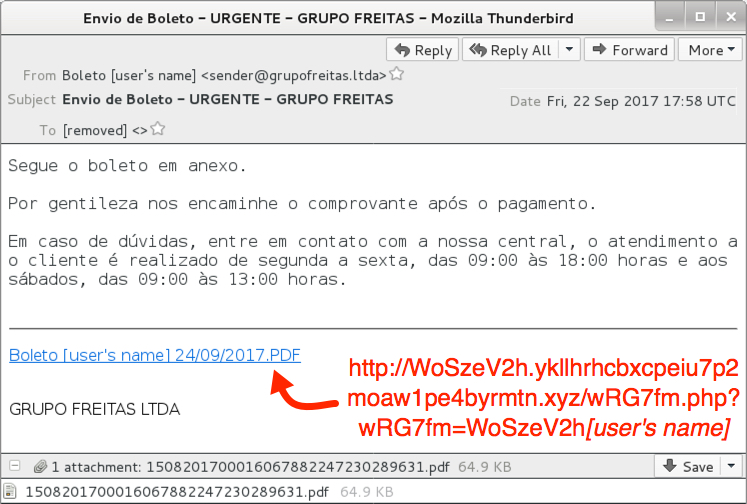
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Sending mail server: grupofreitas[.]ltda
- From: Boleto [recipient's name] <sender@grupofreitas[.]ltda>
- Subject: Envio de Boleto - URGENTE - GRUPO FREITAS
- Date: Friday, 2017-09-22 17:58 UTC
- Attachment name: 1508201700016067882247230289631.pdf
- Link from the message: WoSzeV2h.ykllhrhcbxcpeiu7p2moaw1pe4byrmtn[.]xyz/wRG7fm.php?wRG7fm=WoSzeV2h[recipient's name]
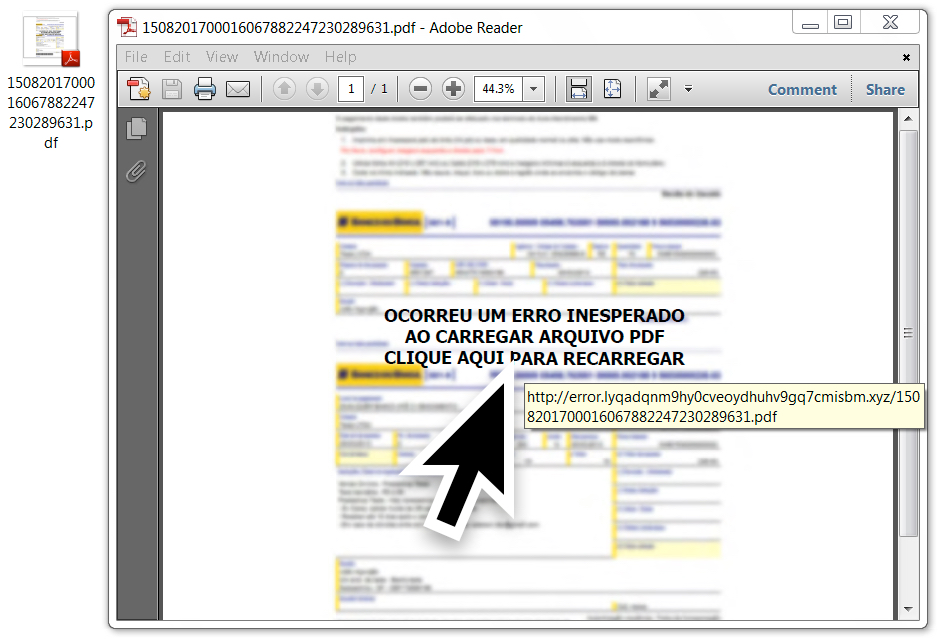
Shown above: Link seen in the PDF attachment.
TRAFFIC
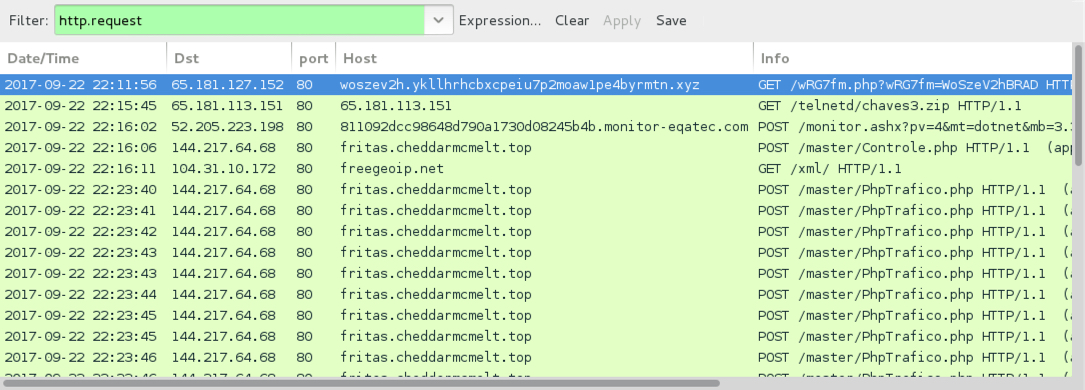
Shown above: Traffic from this infection filtered in Wireshark.
TRAFFIC SEEN USING LINK FROM THE EMAIL:
- 65.181.127[.]152 port 80 - vq7jtrz3.lch8gmmpxpn7dficzttxmpkmngmmgqdr[.]xyz - GET /c4Wzab.php?c4Wzab=VQ7jtrz3[recipient's name]
- drive.google[.]com - GET /uc?authuser=0&id=0B6_FS3bjfLXrYkZXWV9NLTAtRm8&export=download
- doc-0g-60-docs.googleusercontent[.]com - domain that returned the EXE file
TRAFFIC SEEN USING LINK FROM THE ATTACHED PDF FILE:
- 65.181.127[.]152 port 80 - error.lyqadqnm9hy0cveoydhuhv9gq7cmisbm[.]xyz - GET /1508201700016067882247230289631.pdf
- drive.google[.]com - GET /uc?authuser=0&id=0B6_FS3bjfLXrYkZXWV9NLTAtRm8&export=download
- doc-0g-60-docs.googleusercontent[.]com - domain that returned the EXE file
ASSOCIATED DOMAINS AND POST-INFECTION TRAFFIC:
- 65.181.113[.]151 port 80 - 65.181.113[.]151 - GET /telnetd/chaves3.zip
- 52.205.223[.]198 port 80 - 811092dcc98648d790a1730d08245b4b.monitor-eqatec[.]com - POST /monitor.ashx?pv=4&[long list of variables]
- 144.217.64[.]68 port 80 - fritas.cheddarmcmelt[.]top - POST /master/Controle.php
- 104.31.10[.]172 port 80 - freegeoip[.]net - GET /xml/
- 144.217.64[.]68 port 80 - fritas.cheddarmcmelt[.]top - POST /master/PhpTrafico.php [repeats several times]
FILE HASHES
PDF ATTACHMENT:
- SHA256 hash: bd194a81bfed3d57744183dd700e9e4a68f7b05b0f4c94a4eacac5ef6f9c3e49
File size: 49,198 bytes
File name: 1508201700016067882247230289631.pdf
DOWNLOADED EXE FILE (SAME FROM EMAIL LINK OR PDF):
- SHA256 hash: 8332c91467f480e47eb1b02a5a2a06b97af309579dbfce35b9578ff259cfcd8d
File size: 356,352 bytes
File name: 250920178234282343294329423.exe
File description: File downloader for follow-up malware
FOLLOW-UP EXE MADE PERSISTENT ON THE INFECTED HOST:
- SHA256 hash: d8309bc9317c96f1cf9d9cce9562c8c639556a13b28085bd3d3e0e487190f670
File size: 5,675,008 bytes
File location: C:\Users\\AppData\Roaming\Micro07652\idfptray.exe
File description: possible Banking Trojan
IMAGES
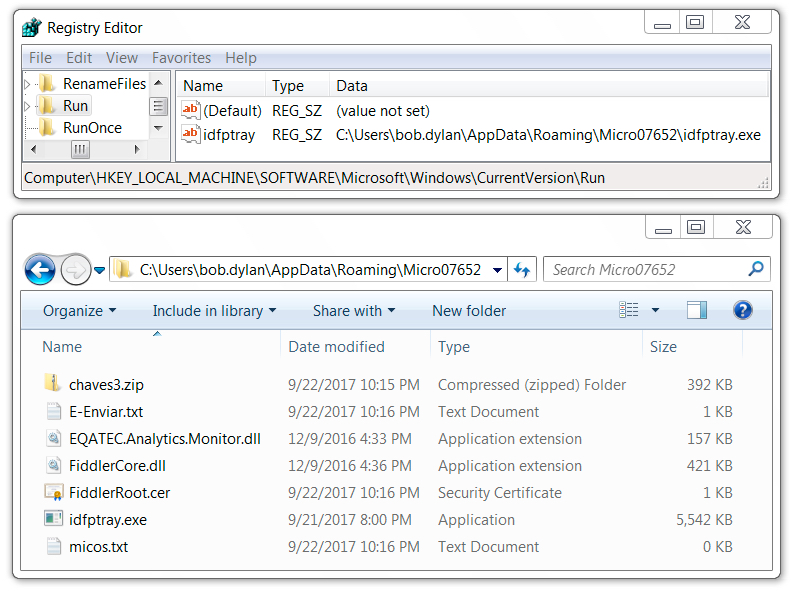
Shown above: Artifacts and the associated Windows registry from the infected host.
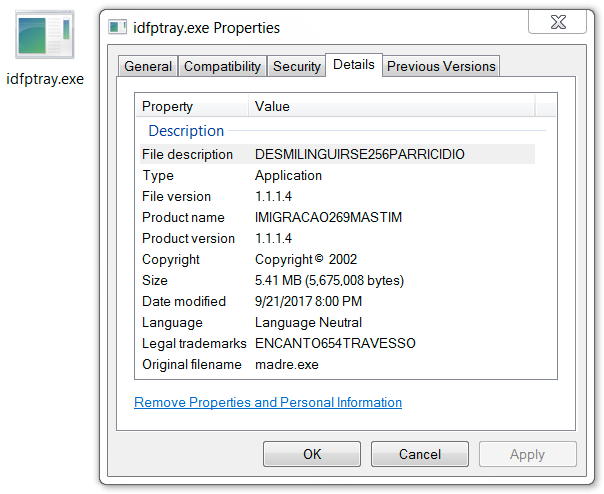
Shown above: More info on the EXE file made persistent from the Windows registry.
Click here to return to the main page.
