2017-08-28 - INFOSTEALER INFECTION FROM BRAZIL MALSPAM
ASSOCIATED FILES:
- 2017-08-28-infostealer-infection-traffic.pcap.zip 3.2 MB (3,186,114 bytes)
- 2017-08-28-infostealer-infection-traffic.pcap (3,645,873 bytes)
- 2017-08-28-Brazil-email-and-malware-files.zip 94.0 kB (93,961 bytes)
- 1508201700016067882247230289631.pdf (49,198 bytes)
- 2017-08-28-Boleto-malspam-0629-UTC.eml (68,408 bytes)
- 2017-08-28-sched-task-for-persistence.txt (3,376 bytes)
- 2308201700026174031337009631980.vbs (4,912 bytes)
NOTES:
- As noted in previous posts about malspam from this actor (2017-06-16 and 2017-07-21), since mid-June 2017 there's been a PDF attachment included with these emails.
- Like last time, the PDF attachment has a different link than the email, but they both redirected to the same sendspace[.]com URL to send the same VBS malware.
- I forgot to get copies for all of the artifacts from the infected host before I wiped it.
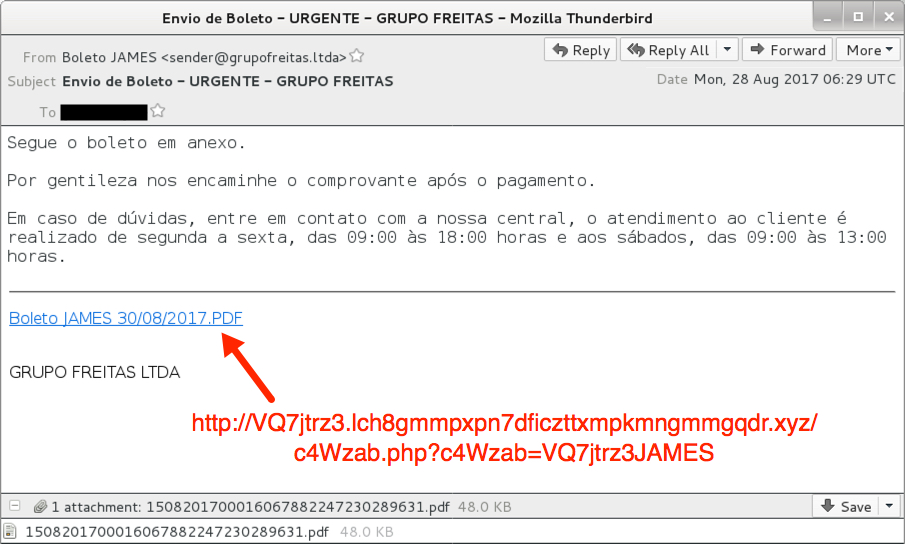
Shown above: Screenshot of the email.
EMAIL HEADERS:
- Sending mail server: grupofreitas[.]ltda
- From: Boleto [recipient's name] <sender@grupofreitas[.]ltda>
- Subject: Envio de Boleto - URGENTE - GRUPO FREITAS
- Date: Monday, 2017-08-28 06:29 UTC
- Attachment name: 1508201700016067882247230289631.pdf
- Link from the message: VQ7jtrz3.lch8gmmpxpn7dficzttxmpkmngmmgqdr[.]xyz/c4Wzab.php?c4Wzab=VQ7jtrz3[recipient's name]
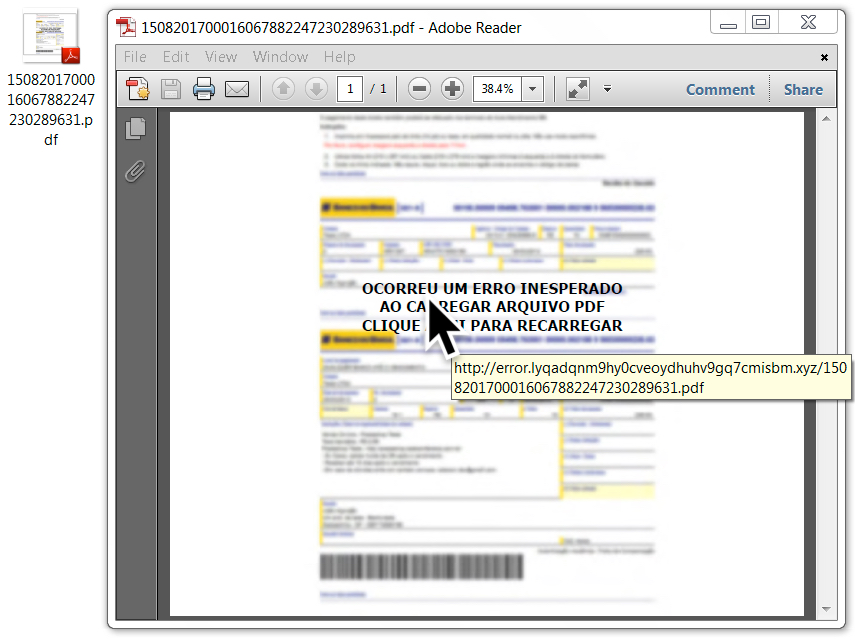
Shown above: Link seen in the PDF attachment.
TRAFFIC
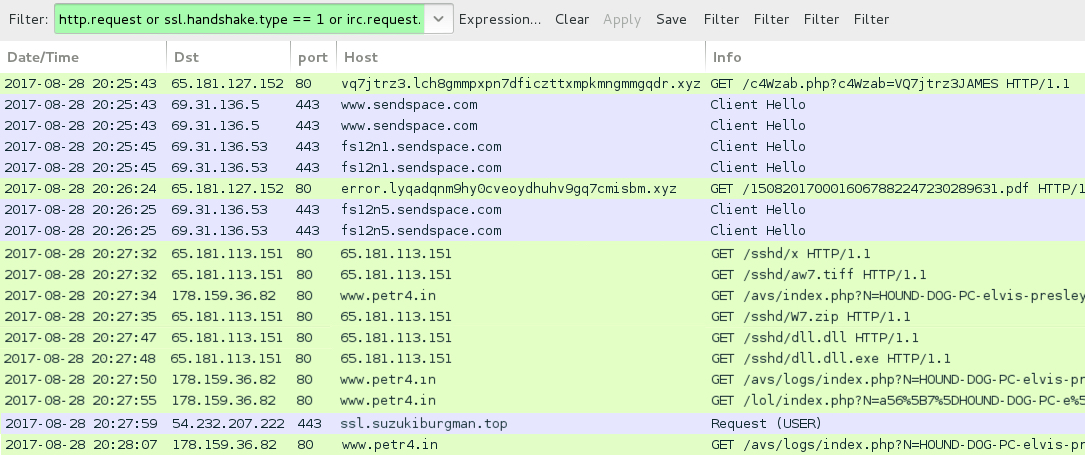
Shown above: Traffic from this infection filtered in Wireshark.
TRAFFIC SEEN USING LINK FROM THE EMAIL:
- 65.181.127[.]152 port 80 - vq7jtrz3.lch8gmmpxpn7dficzttxmpkmngmmgqdr[.]xyz - GET /c4Wzab.php?c4Wzab=VQ7jtrz3[recipient's name]
- www.sendspace[.]com - GET /pro/dl/6ma73i
- fs12n1.sendspace[.]com - domain that returned the VBS file
TRAFFIC SEEN USING LINK FROM THE ATTACHED PDF FILE:
- 65.181.127[.]152 port 80 - error.lyqadqnm9hy0cveoydhuhv9gq7cmisbm[.]xyz - GET /1508201700016067882247230289631.pdf
- www.sendspace[.]com - GET /pro/dl/6ma73i
- fs12n1.sendspace[.]com - domain that returned the VBS file
ASSOCIATED DOMAINS AND POST-INFECTION TRAFFIC:
- 65.181.113[.]151 port 80 - 65.181.113[.]151 - GET /sshd/x
- 65.181.113[.]151 port 80 - 65.181.113[.]151 - GET /sshd/aw7.tiff
- 65.181.113[.]151 port 80 - 65.181.113[.]151 - GET /sshd/W7.zip
- 65.181.113[.]151 port 80 - 65.181.113[.]151 - GET /sshd/dll.dll
- 65.181.113[.]151 port 80 - 65.181.113[.]151 - GET /sshd/dll.dll.exe
- 178.159.36[.]82 port 80 - www.petr4[.]in - GET /avs/index.php?[long string of characters]
- 178.159.36[.]82 port 80 - www.petr4[.]in - GET /avs/logs/index.php?[long string of characters]
- 178.159.36[.]82 port 80 - www.petr4[.]in - GET /lol/index.php?[long string of characters]
- 54.232.207[.]222 port 443 - ssl.suzukiburgman[.]top - IRC traffic using clear text (not encrypted)
FILE HASHES
PDF ATTACHMENT:
- SHA256 hash: bd194a81bfed3d57744183dd700e9e4a68f7b05b0f4c94a4eacac5ef6f9c3e49
File size: 49,198 bytes
File name: 1508201700016067882247230289631.pdf
DOWNLOADED VBS FILE:
- SHA256 hash: a6fe97fbe7582a88a53a6fd102e6b0bf9e5673ba22609b81c5bb0d3c80fda148
File size: 4,912 bytes
File name: 2308201700026174031337009631980.vbs
IMAGES
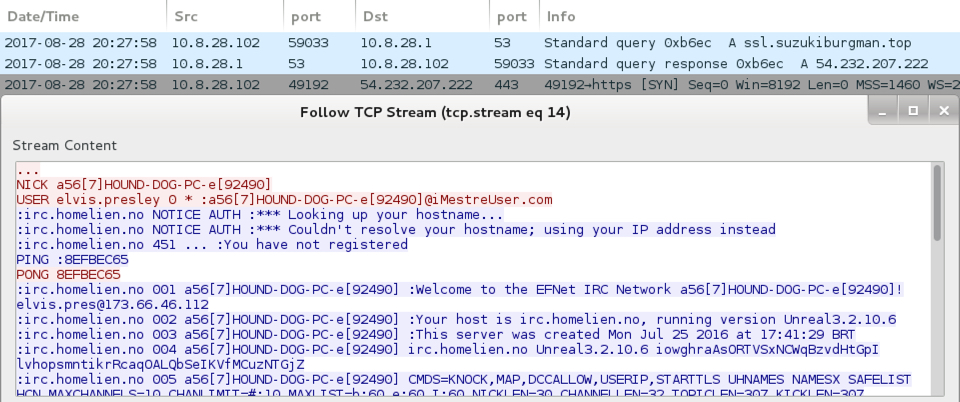
Shown above: Some of the unencrypted IRC traffic noted over TCP port 443.
Click here to return to the main page.
