2017-10-02 - NECURS BOTNET MALSPAM STILL PUSHING ".YKCOL" VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-02-Locky-ransomware-infection.pcap.zip 552.5 kB (552,514 bytes)
- 2017-10-02-Necurs-Botnet-malspam-tracker.csv.zip 1.5 kB (1,455 bytes)
- 2017-10-02-Necurs-Botnet-emails-and-Locky-ransomware-files.zip 782.9 kB (782,941 bytes)
NOTES:
- Has this been still going on every weekday, since I last documented it on 2017-09-18? So repetitive... So boring.
- Didn't notice any post-infection callback traffic after the initial Locky download.
EMAILS
EMAILS COLLECTED:
Read: Date/Time -- Subject -- Sending email address (spoofed)
- 2017-10-02 09:08 UTC -- Subject: New Doc 2017-10-01 - Page 1 -- From (spoofed): Madge Carlstrom <MadgeCarlstrom@gmail[.]com>
- 2017-10-02 10:00 UTC -- Subject: New Doc 2017-10-02 - Page 3 -- From (spoofed): Hillary Hinman <HillaryHinman@gmail[.]com>
- 2017-10-02 10:24 UTC -- Subject: New Doc 2017-10-01 - Page 3 -- From (spoofed): Meagan Kenyon-slaney <MeaganKenyon-slaney@gmail[.]com>
- 2017-10-02 10:33 UTC -- Subject: New Doc 2017-10-01 - Page 2 -- From (spoofed): Sarah Gilbraith <SarahGilbraith@gmail[.]com>
- 2017-10-02 11:25 UTC -- Subject: New Doc 2017-10-02 - Page 1 -- From (spoofed): Marvin Whotton <MarvinWhotton@gmail[.]com>
- 2017-10-02 12:51 UTC -- Subject: New Doc 2017-10-02 - Page 2 -- From (spoofed): Ingrid Eliza <IngridEliza@gmail[.]com>
- 2017-10-02 15:10 UTC -- Subject: Emailed Invoice - 966554 -- From (spoofed): Rosalinda Hannay <Rosalinda@[recipient's email domain]>
- 2017-10-02 15:56 UTC -- Subject: Emailed Invoice - 842905 -- From (spoofed): Penelope Cotes <Penelope@[recipient's email domain]>
- 2017-10-02 16:22 UTC -- Subject: Emailed Invoice - 336905 -- From (spoofed): Lily Bruckner <Lily@[recipient's email domain]>
- 2017-10-02 17:40 UTC -- Subject: Emailed Invoice - 539014 -- From (spoofed): Milo Mcgowan <Milo@[recipient's email domain]>
- 2017-10-02 23:40 UTC -- Subject: Emailed Invoice - 635418 -- From (spoofed): Herminia Godley <Herminia@[recipient's email domain]>
- 2017-10-02 23:47 UTC -- Subject: Emailed Invoice - 631798 -- From (spoofed): Vince Hollwey <Vince@[recipient's email domain]>
TRAFFIC
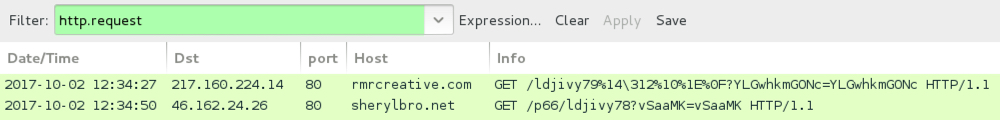
Shown above: Infection traffic filtered in Wireshark (no post-infection traffic noted).
PARTIAL URLS FROM THE .JS FILES TO DOWNLOAD LOCKY:
- hxxp[:]//demeter[.]py/ldjivy78
- hxxp[:]//globoart[.]es/ldjivy78
- hxxp[:]//lacosturera[.]es/ldjivy78
- hxxp[:]//ma-patents[.]com/ldjivy78
- hxxp[:]//malvapraha[.]cz/ldjivy78
- hxxp[:]//maurocesari.it/ldjivy78
- hxxp[:]//miguelangeltrabado[.]com/ldjivy78
- hxxp[:]//rmrcreative[.]com/ldjivy78
- hxxp[:]//ryanbaptistchurch[.]com/ldjivy78
- hxxp[:]//sherylbro[.]net/p66/ldjivy78
- hxxp[:]//themaninroom306[.]com/ldjivy78
- hxxp[:]//goliathstoneindustries[.]com/873gfhi3f3r
- hxxp[:]//honeypot.egdevcenter[.]com/873gfhi3f3r
- hxxp[:]//jeangurunlian[.]com/873gfhi3f3r
- hxxp[:]//kartprinterleri[.]com/873gfhi3f3r
- hxxp[:]//leightonbrothers[.]co[.]uk/873gfhi3f3r
- hxxp[:]//motifahsap[.]com/873gfhi3f3r
- hxxp[:]//pacalik[.]net/873gfhi3f3r
- hxxp[:]//robsacks[.]com/873gfhi3f3r
- hxxp[:]//schwellenwertdaten.de/873gfhi3f3r
- hxxp[:]//sherylbro[.]net/p66/873gfhi3f3r
- hxxp[:]//wallstproperties[.]com/873gfhi3f3r
ASSOCIATED FILES
SHA256 HASHES FOR ATTACHMENTS:
- 7d8c29758c00b082d1c15f65df4ad0a83ad4f46ba357f90061ded076c355bb61 - New Doc 2017-10-01 - Page 1.7z
- 8ca1cc3b21a80d807c4deb66f3ca04be938f19f06aa5184833f4f7eb6f10e0ee - New Doc 2017-10-01 - Page 2.7z
- 97b5ebe742deb72bf6abcd5a404cca67e7359b2e668efbe21211367343fcfbe8 - New Doc 2017-10-01 - Page 3.7z
- 9aea2ea41590b1aa267cd32c0d5d680c97379e8183c42768f403c93e522548ed - New Doc 2017-10-02 - Page 1.7z
- 3ab2eaed5e71714cf3e0f8e4c93403d723c2105d5138d3246cb1c2bddae276f7 - New Doc 2017-10-02 - Page 2.7z
- 4bd59eb178a48f4c035b60274335779be1e342cc61cecb20ffe932c11b1849d1 - New Doc 2017-10-02 - Page 3.7z
- d9abd77843072dcf1985d4d6f5c17269fa1a6ff5beefce1409f69f45d4dff38c - i_336905.7z
- 903d006620cadd64c84062a348ae371822f887c64ab3813978a3cc4b7ef9f852 - i_539014.7z
- 68e61274439c7749a354f4e233de2a62b615d3fb9109ceeb328d8f0d539f9127 - i_631798.7z
- 743479068e187dc65ce3e4d8ac5018202cee1e70ca40bc4017bd082aa8ccddf2 - i_842905.7z
- 81dbf49b1ef5d36cc9bb472b4ec37dd988062e467e304ab607383f3feffc16c7 - i_966554.7z
SHA256 HASHES FOR EXTRACTED FILES:
- 772ecf3e5880b496bf27d57cc849b404c459aa942e95844687ee1c19b4923393 - New Doc 2017-10-01 - Page 1 -180.js
- 7e6df97645b419b3710ada9dee378e319c7053cdb02464957f2e639d50aa1abb - New Doc 2017-10-01 - Page 1 -5724.js
- 903fe2ae91601daa94ec3eaea5ee4d93cfd18d9721c89d67645660d5c74ae4ca - New Doc 2017-10-02 - Page 2 -5759.js
- 533e1b48f1410d08e263748c5e659a693e3a562fd720ac02bf8eb52f3e805d26 - New Doc 2017-10-02 - Page 2 -5918.js
- d98ccdaca0420873748ba217b4eb023b34a8e9ff49b34dd89de0db9871ba46af - New Doc 2017-10-02 - Page 2 -8300.js
- 8b0b213100694027fa8946507a240bae450aef077d715254a16e0aa840551b76 - New Doc 2017-10-02 - Page 2 -8415.js
- 7ce44af7b3e132d2d9bdbd7d46909df06e1659345a319d52ae1ccba238782793 - I_309411.js
- 8bce9340c1e3b1896ff1ac4f3f9df4b3dfc8f3e847f6e4c6787fa532d808013c - I_362789.js
- 04ee13a4ae9d340cf6389e59903f29dee575c1fef4a92a6ab06fe342ae27a406 - I_441706.js
- 735606227130600c12273627bc64082e0dcafd2a69bbe53a212fdd6f32d283c2 - I_772198.js
- b3a612700da1372f639ec80420a36b07cf94a2d7cfb79ebc4de7158183480414 - I_843058.js
SHA256 HASH FOR THE ONE LOCKY BINARY SAMPLE I PULLED TODAY:
- 5679535c188131500205cc7c9b28f442eaeb7ed28698d0b69293d434208d24ba - 2017-10-02-Locky-binary-sample.exe
IMAGES
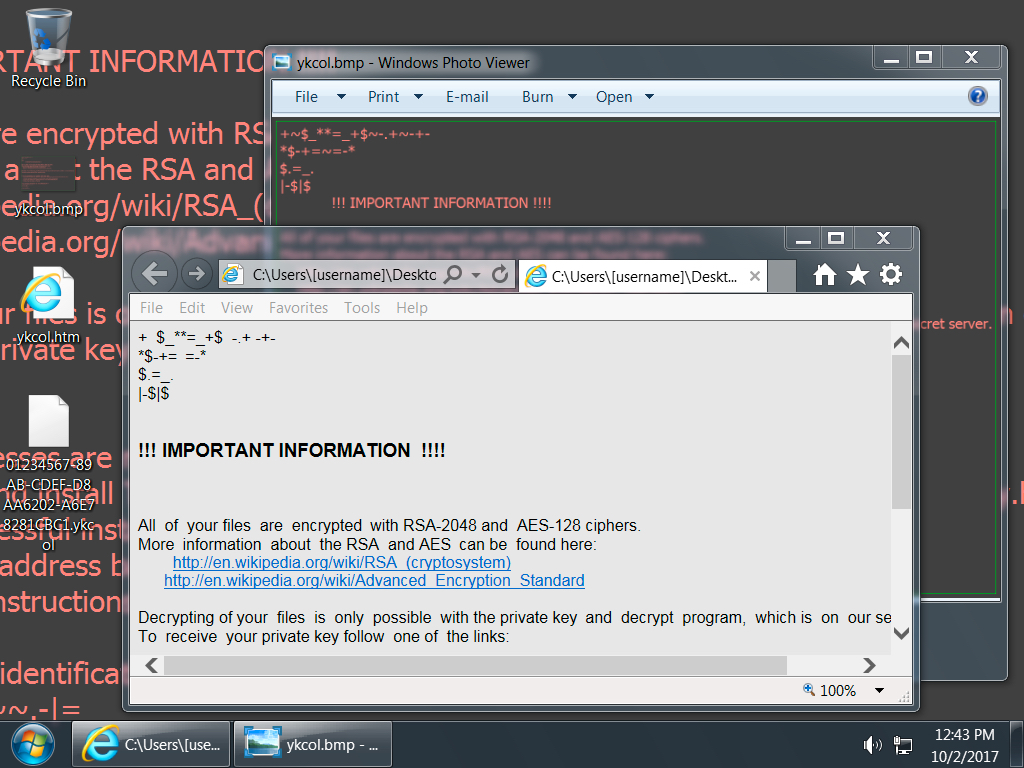
Shown above: Screenshot from an infected Windows desktop--Encrypted files all have a .ykcol file extension.
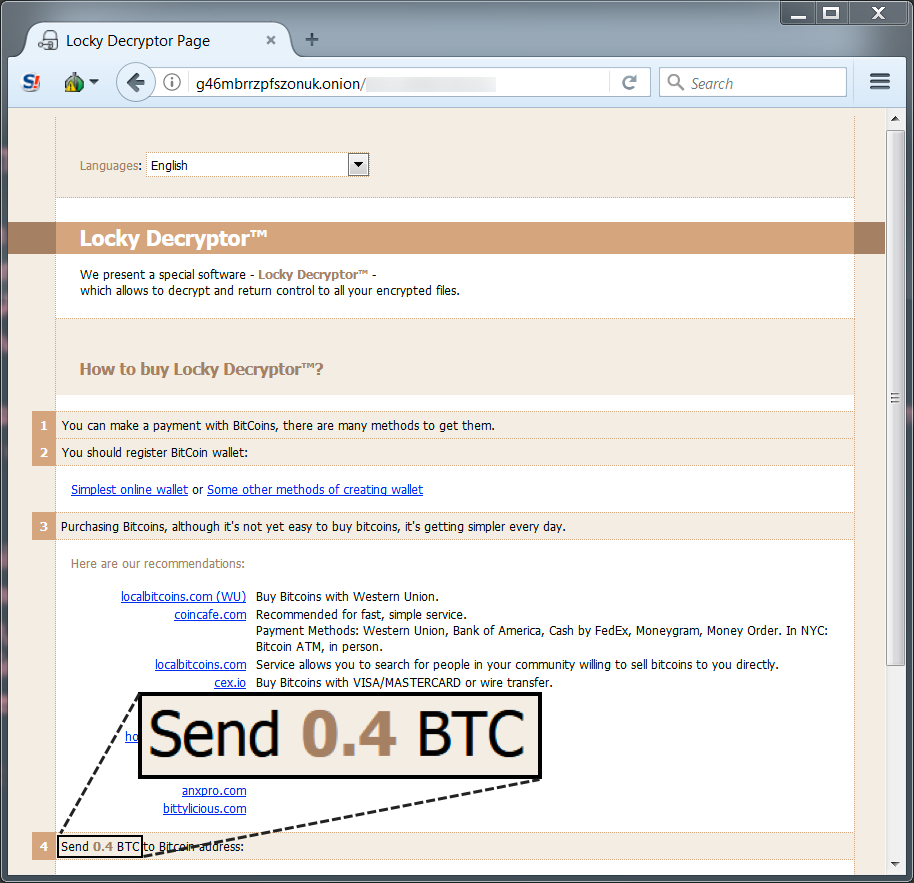
Shown above: Locky Decryptor, where is looks like the ransom cost is .4 Bitcoin now.
Click here to return to the main page.

