2017-10-11 - BANLOAD INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-11-Banload-infection-traffic-2-pcaps.zip 6.8 MB (6,830,494 bytes)
- 2017-10-11-Banload-infection-1st-run.pcap (3,528,066 bytes)
- 2017-10-11-Banload-infection-2nd-run.pcap (3,647,909 bytes)
- 2017-10-11-Banload-emails-and-malware.zip 2.3 MB (2,348,172 bytes)
- 01.zip (1,586,625 bytes)
- 2017-10-11-WhatsApp-malspam-0501-UTC.eml (5,364 bytes)
- 2017-10-11-WhatsApp-malspam-1216-UTC.eml (17,682 bytes)
- WhatsAppImage2017-10-11at17.59.08.exe (1,816,064 bytes)
NOTES:
- Banload is a generic term given to downloaders that install banking Trojans. I most often see Banload associated with Brazil-based malspam.
- This post is very similar to malspam I documented earlier this month on 2017-10-03.
EMAIL INFORMATION:

Shown above: Screenshot from the 1st email.
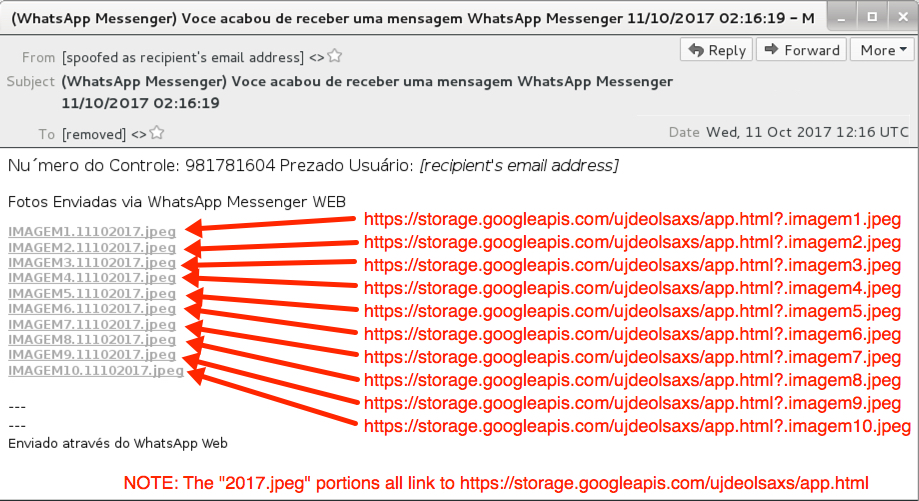
Shown above: Screenshot from the 2nd email.
1ST EMAIL:
- Date: Wednesday, 2017-10-11 05:01 UTC
- From: [spoofed as recipient's email address]
- Subject: Recebemos varias Denuncias que seu WhatsApp esta postando Videos que estao Violando 11/10/2017 07:01:17
- Received: from web19.webwhats[.]ga ([80.211.135[.]104])
- X-PHP-Originating-Script: 0:cofjopovdstjveopxdwd.php
- Message-ID: <20171011050117.CAB1D8C4AF@web19.webwhats[.]ga>
- Link in the email: hxxps[:]//storage.googleapis[.]com/improprio/Whatsapp.html
2ND EMAIL:
- Date: Wednesday, 2017-10-11 12:16 UTC
- From: [spoofed as recipient's email address]
- Subject: (WhatsApp Messenger) Voce acabou de receber uma mensagem WhatsApp Messenger 11/10/2017 02:16:19
- Received: from web5.mensagemwebwhatsapp[.]ml ([195.181.216[.]53])
- X-PHP-Originating-Script: 0:cofjopovdstjveopxdwd.php
- Message-ID: <20171011121619.5821B85399@web5.mensagemwebwhatsapp[.]ml>
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem1.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem2.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem3.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem4.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem5.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem6.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem7.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem8.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem9.jpeg
- Link in the email: hxxps[:]//storage.googleapis[.]com/ujdeolsaxs/app.html?.imagem10.jpeg
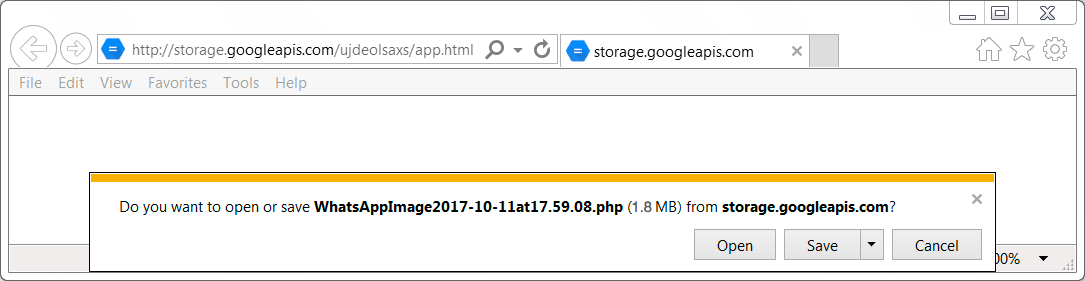
Shown above: Clicking on an email link returns an EXE file (file extension showed as .php when I used Internet Explorer).
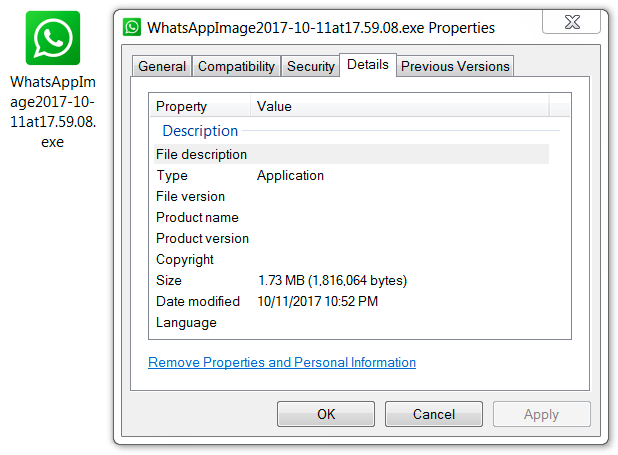
Shown above: Downloaded EXE (same file downloaded from both emails).
TRAFFIC
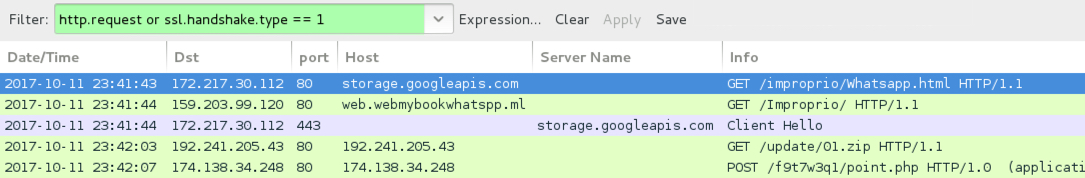
Shown above: Infection traffic filtered in Wireshark (1st run from link in 1st email).
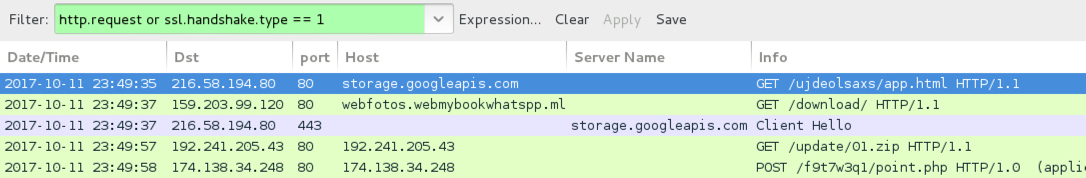
Shown above: Infection traffic filtered in Wireshark (2nd run from link in 2nd email).
1ST RUN:
- port 443 (HTTPS) - storage.googleapis[.]com - GET /improprio/Whatsapp.html
- 159.203.99[.]120 port 80 - web.webmybookwhatspp[.]ml - GET /Improprio/
- port 443 (HTTPS) - storage.googleapis[.]com - GET /mywebs/WhatsAppImage2017-10-11at17.59.08.exe?cli=WhatsApp&/[random string]/[random string].php
- 192.241.205[.]43 port 80 - 192.241.205[.]43 - GET /update/01.zip/
- 174.138.34[.]248 port 80 - 174.138.34[.]248 - POST /f9t7w3q1/point.php
2ND RUN:
- port 443 (HTTPS) - storage.googleapis[.]com - GET /ujdeolsaxs/app.html
- 159.203.99[.]120 port 80 - webfotos.webmybookwhatspp[.]ml - GET /download/
- port 443 (HTTPS) - storage.googleapis[.]com - GET /mywebs/WhatsAppImage2017-10-11at17.59.08.exe?cli=WhatsApp&/[random string]/[random string].php
- 192.241.205[.]43 port 80 - 192.241.205[.]43 - GET /update/01.zip
- 174.138.34[.]248 port 80 - 174.138.34[.]248 - POST /f9t7w3q1/point.php
MALWARE
EXE DOWNLOADED CLICKING A LINK FROM THE EMAILS:
- SHA256 hash: ff536f061ad0348ffd4baa704ce14912d5a65a531575a60b4591aa6f3172c1a3
File name: WhatsAppImage2017-10-11at17.59.08.exe
File size: 1,816,064 bytes
FOLLOW-UP MALWARE (ZIP ARCHIVE) DOWNLOADED BY THE ABOVE FILE:
- SHA256 hash: a9d6bd61517aa2eb4b535d32ef04c0ee7c5254172837dd95ae0a63106497154c
File name: hxxp[:]//192.241.205[.]43/update/01.zip
File size: 1,586,625 bytes
MALWARE RETRIEVED FROM INFECTED WINDOWS HOST (1 OF 2):
- SHA256 hash: b1151d1cc7d90149bafd5d8f099fe21c23f88a9dc4fbd56d9cda959e4858eb80
File location: C:\Users\[username]\AppData\Roaming\[random characters]\jli.dll
File size: 3,177,984 bytes
File description: Malicious DLL file (Banload) from the downloaded malware archive.
MALWARE RETRIEVED FROM INFECTED WINDOWS HOST (2 OF 2):
- SHA256 hash: 7cc34a5423bd3fc9fa63d20ebece4103e22e4360df5b9caa2b461069dac77f4d
File location: C:\Users\[username]\AppData\Roaming\[random characters]\[random characters].exe
File size: 15,936 bytes
File description: EXE from the downloaded malware archive, loads the above DLL (jli.dll).
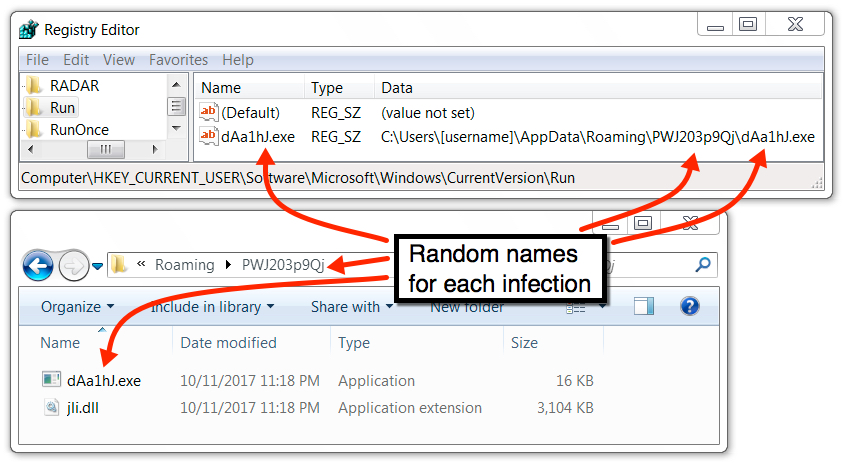
WINDOWS REGISTRY UPDATE:
- Key name: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: [random characters].exe
- Value type: REG_SZ
- Value data: C:\Users\[username]\AppData\Roaming\[random characters]\[random characters].exe
Shown above: Malware persistent on the infected Windows host.
Click here to return to the main page.