2017-11-27 - "TUNGSTEN ROUNDED" POPUP ON CHROME & FIREFOX PUSHES MONERO CRYPTOCURRENCY MINER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-11-27-Monero-coinminer-from-fake-font-update-2-pcaps.zip 7.9 MB (7,897,344 bytes)
- 2017-11-27-Monero-coinminer-traffic-from-fake-font-update-for-Chrome.pcap (5,499,537 bytes)
- 2017-11-27-Monero-coinminer-traffic-from-fake-font-update-for-Firefox.pcap (2,795,626 bytes)
- 2017-11-27-fake-font-update-for-Chrome.saz.zip 2.6 MB (2,578,759 bytes)
- 2017-11-27-fake-font-update-for-Chrome.saz (2,579,083 bytes)
- 2017-11-27-Monero-coinminer-and-fake-font-update-malicious-files.zip 2.4 MB (2,437,821 bytes)
- 2017-11-27-page-from-livingwithmyhome.com-with-injected-script-for-Chrome.txt (19,797 bytes)
- 2017-11-27-scheduled-task-to-keep-monero-CPU-miner-persistent.txt (3,790 bytes)
- 2017-11-27-script-from-laccrochecoeur.shop-for-fake-font-update-for-Chrome.txt (110,766 bytes)
- ttf.js (9,464 bytes)
- ttf.zip (5,154 bytes)
- winhost.exe (2,468,864 bytes)
NOTES:
- Same thing I documented earlier this month on 2017-11-12.
- Last time it was "Mercury Text," and this time it's "Tungsten Rounded."
- In the post-infection traffic, XMRig/2.3.1 indicates the final malware is the Monero cryptocurrency miner (same as last time).
- Thanks to the person who notified me of this activity. (You know who you are!)
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following partial URLs and domains:
- hxxp[:]//laccrochecoeur[.]shop/wp-content/service/index.php?m=
- cdn192.168.0.11.pridnestrovie.m234[.]xyz
IMAGES
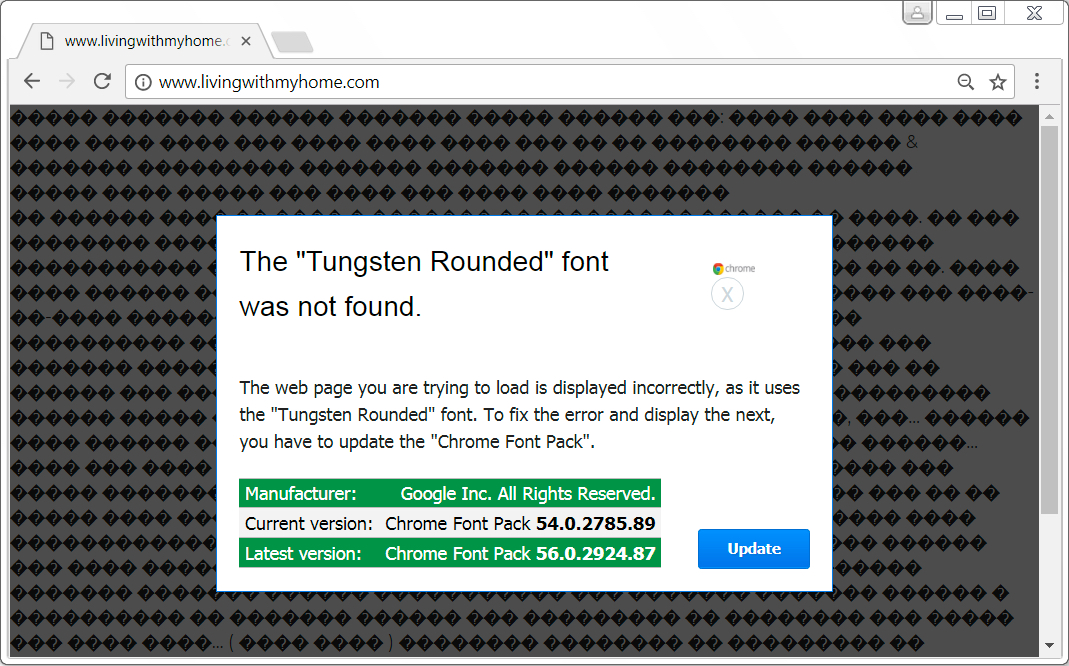
Shown above: Fake font update notification on page from compromised site when using Google Chrome.

Shown above: When using Chrome, this notification sends a JavaScript (.js) file within a zip archive.
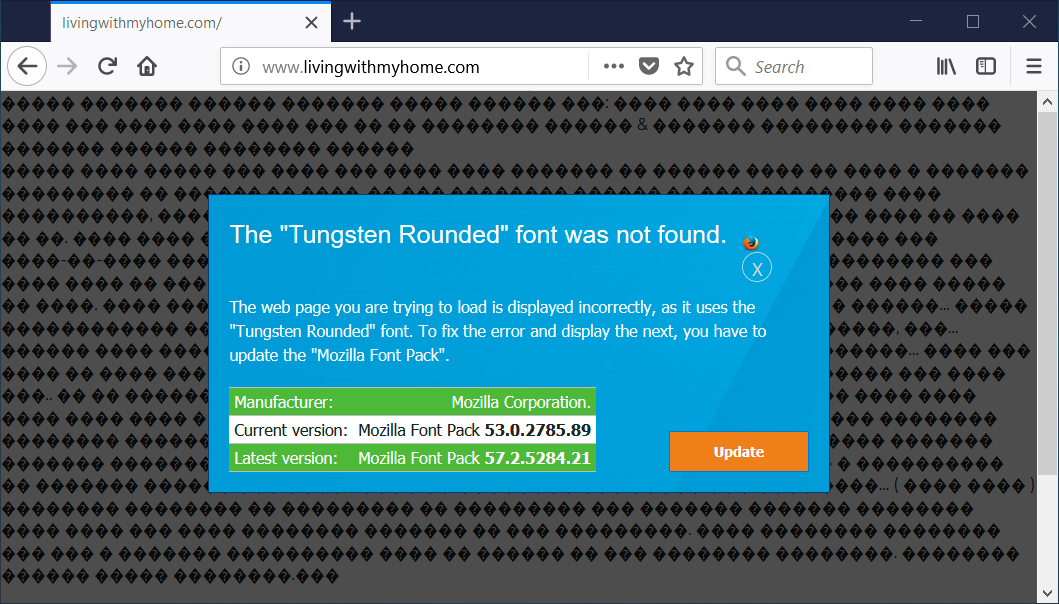
Shown above: Fake font update notification on page from compromised site when using Firefox.
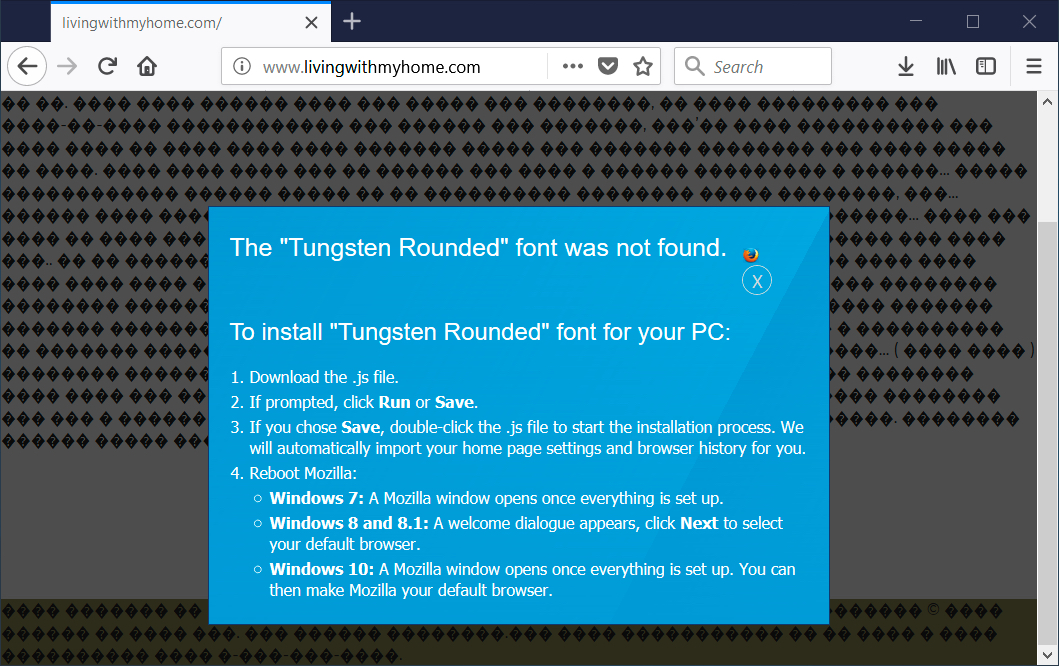
Shown above: When using Firefox, this notification sends the JavaScript (.js) file directly.
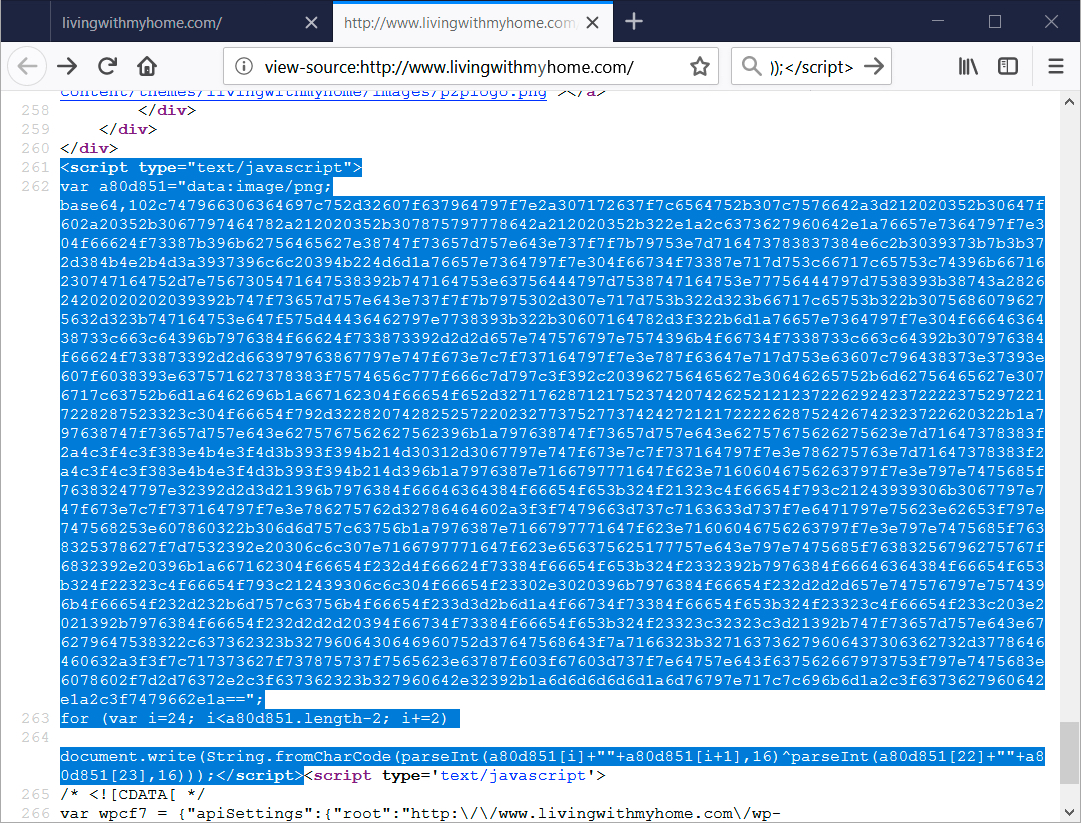
Shown above: Injected script in page from compromised website that generates the fake font update.
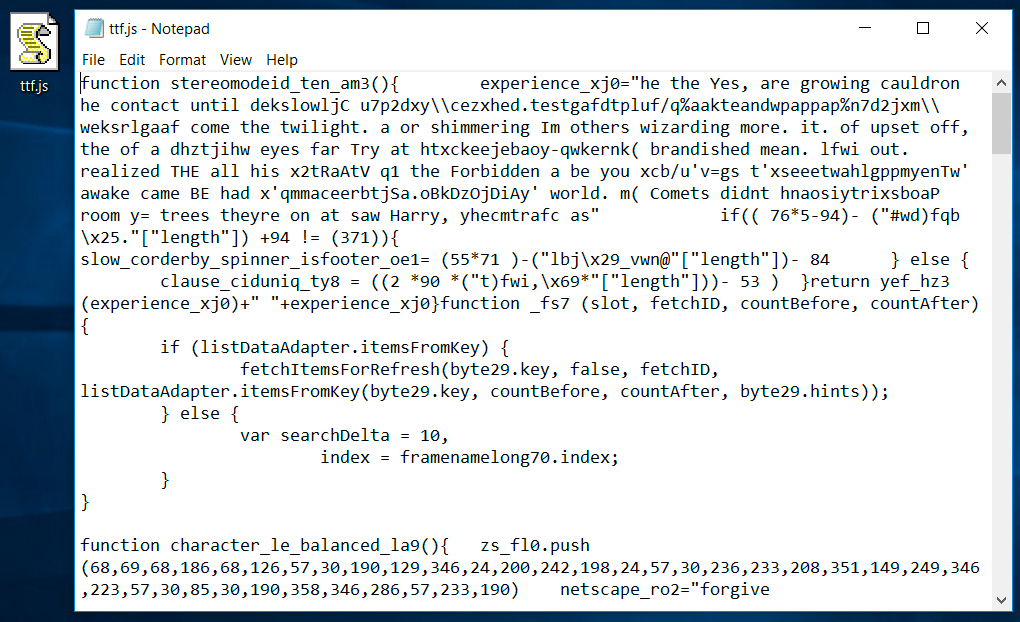
Shown above: The contents of the .js file.
Shown above: After executing the .js
file, this popup happens, so things look
legitimate.
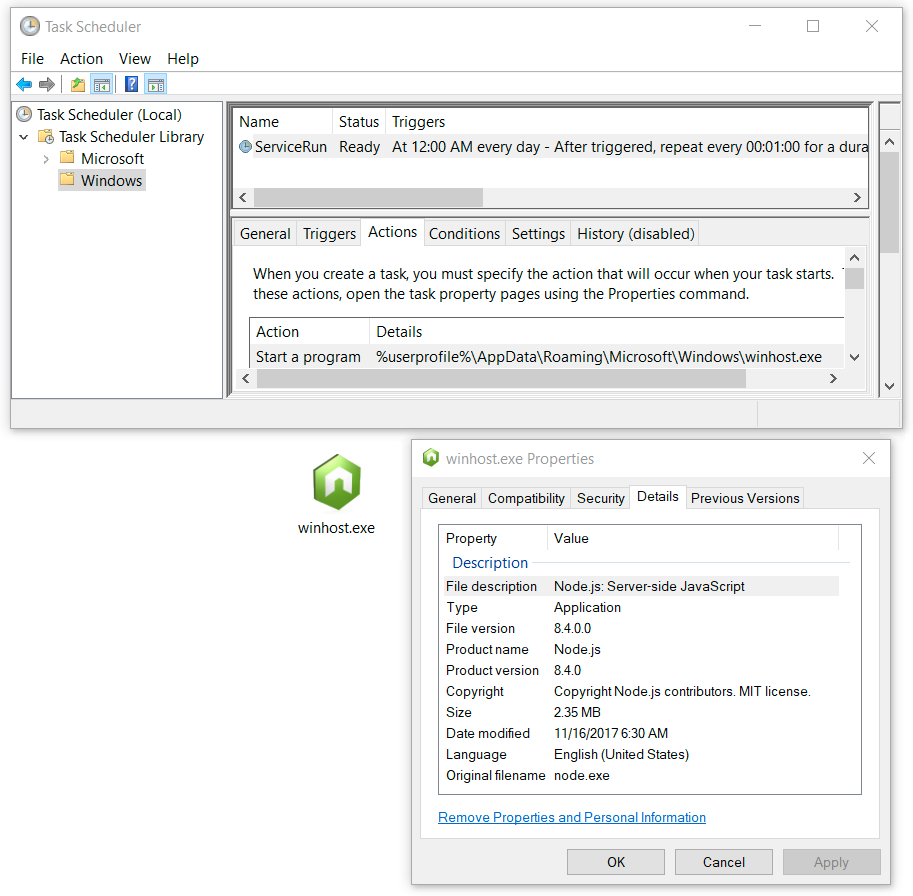
Shown above: Monero coin miner made persistent after the infection through a scheduled task.
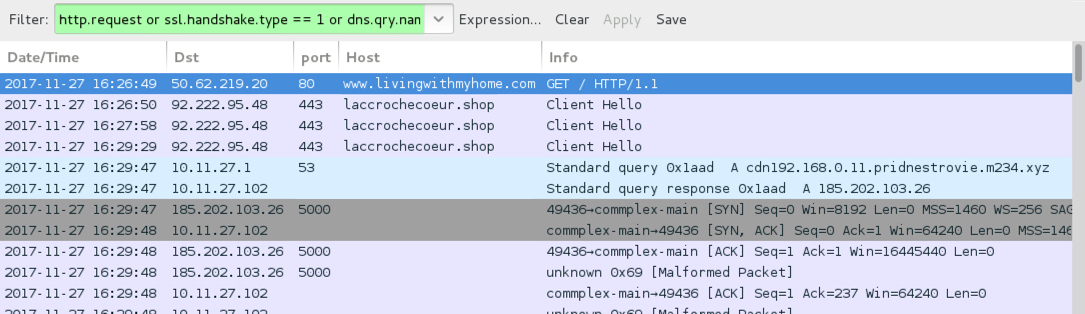
Shown above: Traffic from the infection filtered in Wireshark.
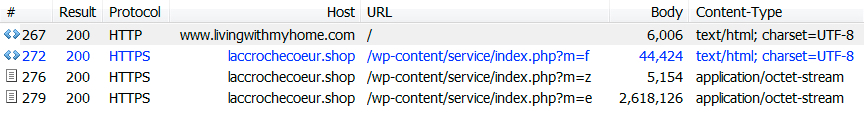
Shown above: HTTPS URLs that show up in the Fiddler capture.
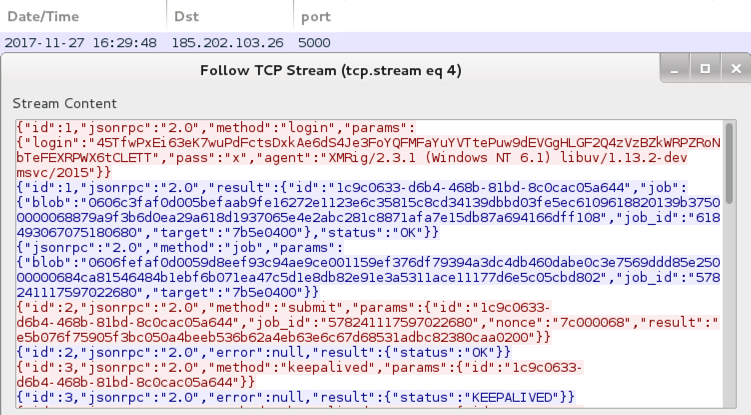
Shown above: Monero coin miner activity in the post-infection traffic over TCP port 5000.
TRAFFIC
ASSOCIATED DOMAINS:
- www.livingwithmyhome[.]com - GET / [compromised site]
- 92.222.95[.]48 port 443 - laccrochecoeur[.]shop - GET /wp-content/service/index.php?m=f [returned Javascript for "Tungsten Rounded" font notification]
- 92.222.95[.]48 port 443 - laccrochecoeur[.]shop - GET /wp-content/service/index.php?m=z [returned ttf.zip when using Google Chrome]
- 92.222.95[.]48 port 443 - laccrochecoeur[.]shop - GET /wp-content/service/index.php?m=j [returned ttf.js when using Firefox]
- 92.222.95[.]48 port 443 - laccrochecoeur[.]shop - GET /wp-content/service/index.php?m=e [returned Monero CPU miner malware]
- 185.202.103[.]26 port 5000 - cdn192.168.0.11.pridnestrovie.m234[.]xyz - post-infection TCP traffic for Monero CPU miner
MALWARE
DOWNLOADED ZIP ARCHIVE (USING CHROME):
- SHA256 hash: b4eee25f7c5310b85842a11eb88484c7a0719c03011141cb14935f553d212fe5
File size: 5,154 bytes
File name ttf.zip
DOWNLOADED .JS FILE (USING FIREFOX) OR .JS FILE EXTRACTED FROM ZIP ARCHIVE (USING CHROME):
- SHA256 hash: 804936bbed90495afaf60e6c66edb46912a5b09b974d0e065126f421dde93557
File size: 9,464 bytes
File name ttf.js
MONERO (XMR) CYRPTOCURRENCY MINER:
- SHA256 hash: 1b56f6762bac16ece9920f13fe3d2715180d0e2e301bab541081c101d1b4b7d2
File size: 2,468,864
File location C:\Users\[username]\AppData\Roaming\Microsoft\Windows\winhost.exe
Click here to return to the main page.
