2017-12-08 - FOBOS CAMPAIGN RIG EK SENDS BUNITU
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-12-08-Fobos-campaign-Rig-EK-sends-Bunitu.pcap.zip 272 kB (271,874 bytes)
- 2017-12-08-Fobos-campaign-Rig-EK-sends-Bunitu.pcap (317,090 bytes)
- 2017-12-08-Fobos-campaign-Rig-EK-malware-and-artifacts.zip 212.4 kB (212,431 bytes)
- 2017-12-08-Bunitu-post-infection-artifact-liaogiu.dll (30,208 bytes)
- 2017-12-08-Fobos-campaign-Rig-EK-payload-Bunitu.exe (174,080 bytes)
- 2017-12-08-Rig-EK-flash-exploit.swf (14,197 bytes)
- 2017-12-08-Rig-EK-landing-page.txt (132,707 bytes)
- 2017-12-08-page-from-krai-soft.net_txt (39,071 bytes)
- 2017-12-08-script-returned-from-103jdhhfff99500910_info.txt (921 bytes)
NOTES:
- 2017-03-15 - Mandiant: Still Getting Served: A Look at Recent Malvertising Campaigns Involving Exploit Kits
- 2017-08-16 - MalwareBreakdown.com: Fobos Campaign Using RIG EK to Drop Bunitu Trojan
- 2017-08-28 - Malware-traffic-analysis.net: Fobos campaign Rig EK sends Bunitu
- krai-soft[.]net is a decoy site set up specifically for the Fobos campaign.
TRAFFIC
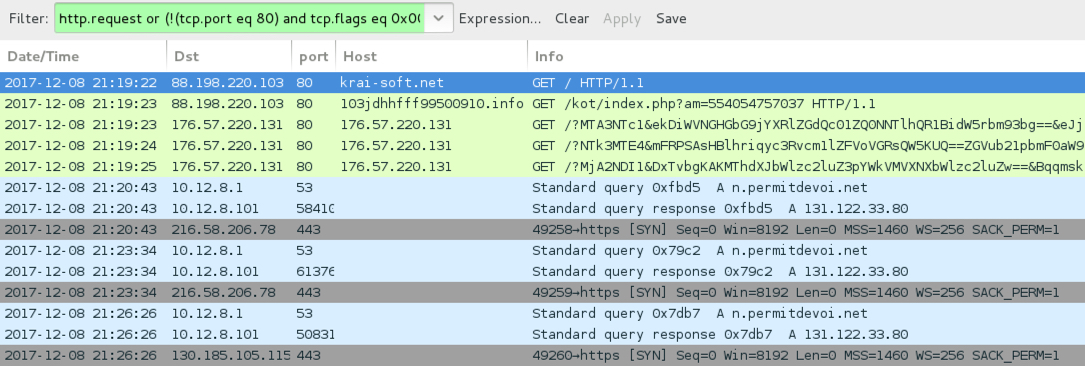
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 88.198.220[.]103 port 80 - krai-soft[.]net - Domain used by Fobos campaign
- 88.198.220[.]103 port 80 - 103jdhhfff99500910[.]info - GET /kot/index.php?am=554054757037 [redirect/gate]
- 176.57.220[.]131 port 80 - 176.57.220[.]131 - Rig EK
- 216.58.206[.]78 port 443 - 216.58.206[.]78 - Bunitu post-infection traffic
- 130.185.105[.]115 port 443 - 130.185.105[.]115 - Bunitu post-infection traffic
- DNS queries for n.permitdevoi[.]net - resolved to 131.122.33[.]80 but no follow-up traffic
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: 0fb10ab2787966d827e6e7b5947d2bc8cd364f3f98025f155f7f8352405703d1
File size: 14,197 bytes
File description: Rig EK flash exploit seen on 2017-12-08
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: efaaa9630107def091c25d4f50fff7ed3d30d27163d552b5034659a9991c1437
File location: C:\Users\[username]\AppData\Local\Temp\bilo542.exe
File size: 174,080 bytes
File description: Windows EXE file to install Bunitu
- SHA256 hash: bf83ff6b7c5bd5879e98c5a1dc9971bb80f2ce99e325a81c8448c140055e6034
File location: C:\Users\[username]\AppData\Local\liaogui.dll
File size: 30,208 bytes
File description: Bunitu DLL persistent on the infected Windows hostn
Run method: rundll32.exe [filename],liaogiu
IMAGES
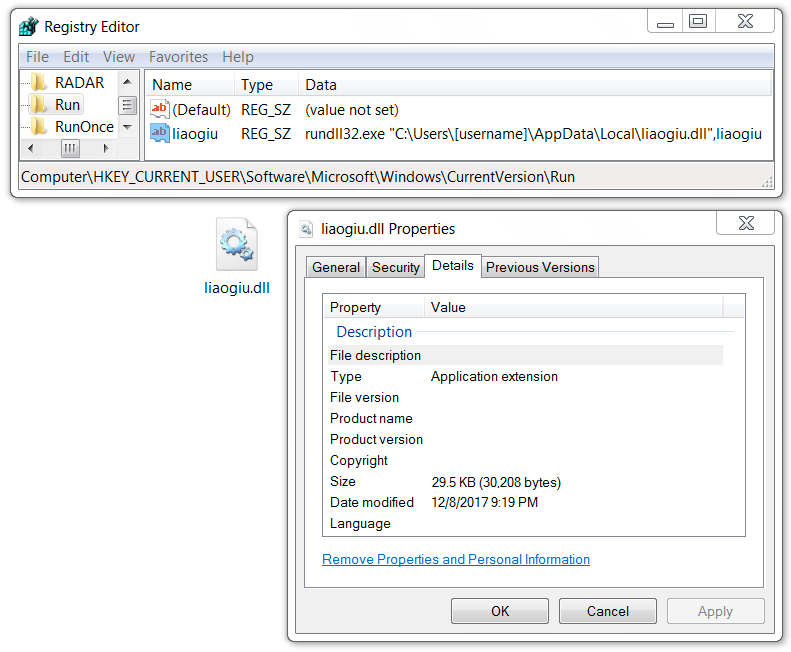
Shown above: Malware persistent on the infected Windows host.
Click here to return to the main page.
