2017-12-14 - NGAY CAMPAIGN RIG EK PUSHES QUANT LOADER & MONERO (XMR) COIN MINER
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the pcap: 2017-12-14-Ngay-campaign-Rig-EK-sends-Quant-Loader-and-Monero-coin-miner.pcap.zip 1.0 MB (1,012,916 bytes)
- 2017-12-14-Ngay-campaign-Rig-EK-sends-Quant-Loader-and-Monero-coin-miner.pcap (1,093,405 bytes)
- Zip archive of the malware and artifacts: 2017-12-14-Ngay-campaign-Rig-EK-malware-and-artifacts.zip 1.0 MB (1,016,572 bytes)
- 2017-12-14-HTML-from-192.241.150_92.txt (2,483 bytes)
- 2017-12-14-Ngay-campaign-Rig-EK-payload-Quant-Loader.exe (128,969 bytes)
- 2017-12-14-Rig-EK-artifact-o32.tmp.txt (1,141 bytes)
- 2017-12-14-Rig-EK-flash-exploit.swf (13,940 bytes)
- 2017-12-14-Rig-EK-landing-page.txt (132,729 bytes)
- 2017-12-14-follow-up-malware-Monero-coin-miner.exe (833,487 bytes)
NOTES:
- This is Rig EK used by the Ngay campaign, first documented by @nao_sec at: http://www.nao-sec.org/2017/12/survey-of-ngay-campaign.html
- I posted a previous traffic example on 2017-12-12.
- As before, today's payload was Quant Loader which then grabbed Monero CPU miner.
Shown above: Flow chart for today's infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following URLs:
- coccoc[.]accountant
- hxxp[:]//67.205.189[.]141/mprocess.exe
- thang12[.]ru
- thang1217[.]ru
TRAFFIC
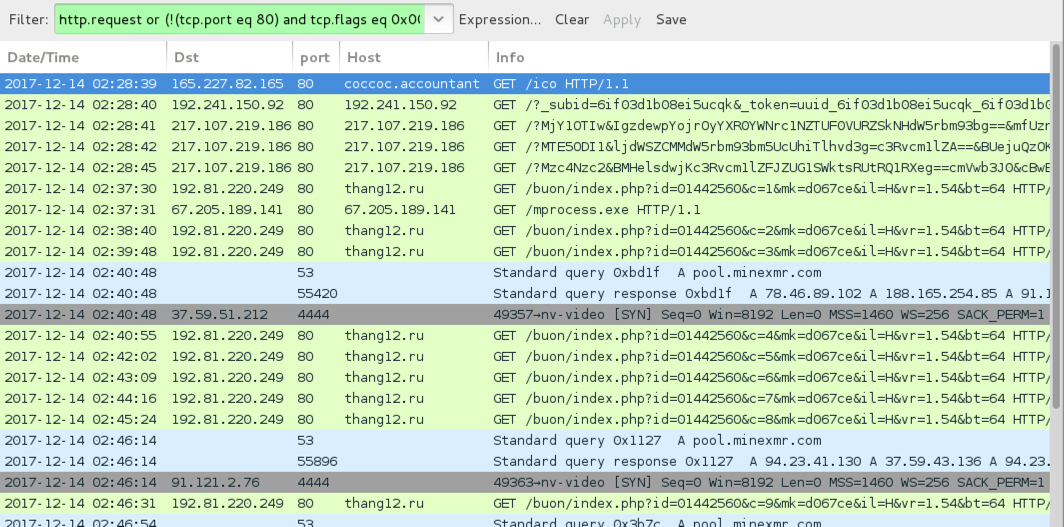
Shown above: Traffic from an infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 165.227.82[.]165 port 80 - coccoc[.]accountant - GET /ico
- 192.241.150[.]92 port 80 - 192.241.150[.]92 - GET /?_subid=[long string of chracters]
- 217.107.219[.]186 port 80 - 217.107.219[.]186 - Rig EK
- 192.81.220[.]249 port 80 - thang12[.]ru - GET /buon/index.php?id=[long string of characters]
- 67.205.189[.]141 port 80 - 67.205.189[.]141 - GET /mprocess.exe
- DNS query for thang1217[.]ru - response: No such name
- 37.59.51[.]212 port 4444 - pool.minexmr[.]com - TCP traffic associated with Monero CPU miner
- 91.121.220[.]249 port 4444 - pool.minexmr[.]com - TCP traffic associated with Monero CPU miner
MALWARE AND ARTIFACTS
ARTIFACTS FROM AN INFECTED WINDOWS HOST:
- SHA256 hash: 5599d248433d40f7b7c4b2e1cbab7d5cb0853e0b8e6c3361c480df2226dc3980
- File size: 13,940 bytes
- File description: Rig EK flash exploit seen on 2017-12-14
- SHA256 hash: a36c8a1d29cb67f877b46c972a8587d07edcbc94173c1d832fb3e2c66b823360
- File size: 128,969 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\bilo264.exe
- File location: C:\Users\[username]\AppData\Roaming\01442560\csrss.exe
- File description: Ngay campaign payload from Rig EK - Quant Loader
- SHA256 hash: 4e7ee8a771ad379abd8efa8321aacdd1ee3c2dfab7acb318e2b76ba03cbdc072
- File size: 833,487 bytes
- File location: hxxp[:]//67.205.189[.]141/mprocess.exe
- File location: C:\Users\[username]\AppData\Local\Temp\23731.exe
- File location: C:\Users\[username]\AppData\Roaming\senior.exe
- File description: Follow-up malware - Monero CPU miner
IMAGES
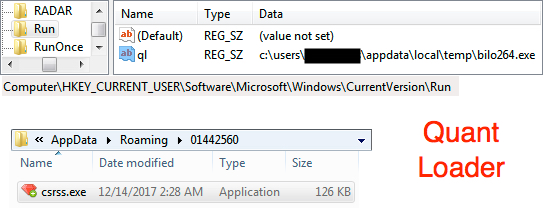
Shown above: Quant Loader persistent on the infected Windows host.
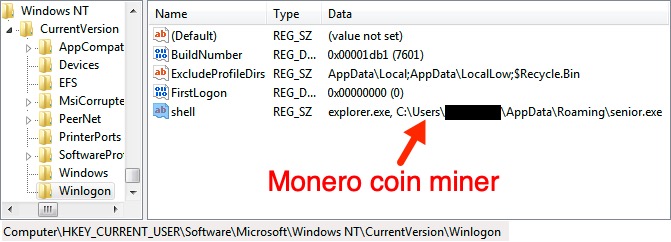
Shown above: Monero (XMR) coin miner persistent on the infected Windows host.
Click here to return to the main page.

