2018-04-10 - GANDCRAB RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Zip archive of the email: 2018-04-10-GandCrab-malspam-example.eml.zip 116 kB (115,935 bytes)
- 2018-04-10-GandCrab-malspam-example.eml 227 kB (227,109 bytes)
- 2018-04-10-Gandcrab-infection-traffic.pcap 358 kB (357,722 bytes)
- 2018-04-10-CRAB-DECRYPT.txt 4.2 kB (4,218 bytes)
- 2018-04-10-Gandcrab-Decryptor-BTC.html 15.8 kB (15,791 bytes)
- 2018-04-10-Gandcrab-Decryptor-DASH.html 15.7 kB (15,724 bytes)
- 2018-04-10-Gandcrab-Decryptor-Support.html 10.9 kB (10,875 bytes)
- 2018-04-10-Gandcrab-Decryptor-index.html 10.6 kB (10,623 bytes)
- 2018-04-10-Gandcrab-Decryptor-test-decrypt.html 9.9 kB (9,931 bytes)
- 2018-04-10-Gandcrab-binary.exe 301 kB (301,064 bytes)
- DOC3660738334.doc 169 kB (169,472 bytes)
- DOC3660738334.zip 170 kB (169,604 bytes)
NOTES:
- These waves of malspam use [0.0.0[.]0] as a spoofed address in the Received: from line from the email headers.
- I've previously documented this specific campaign on 2018-03-16 (a full post) and 2018-04-03 (a quick post).
- Unlike previous posts, I only have one email sample for today's blog.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- hxxp[:]//185.189.58[.]222/da.exe
- ransomeware[.]bit
- zonealarm[.]bit
- gandcrab2pie73et[.]onion
- gandcrab2pie73et[.]onion[.]rip
- gandcrab2pie73et[.]onion[.]plus
- gandcrab2pie73et[.]onion[.]to
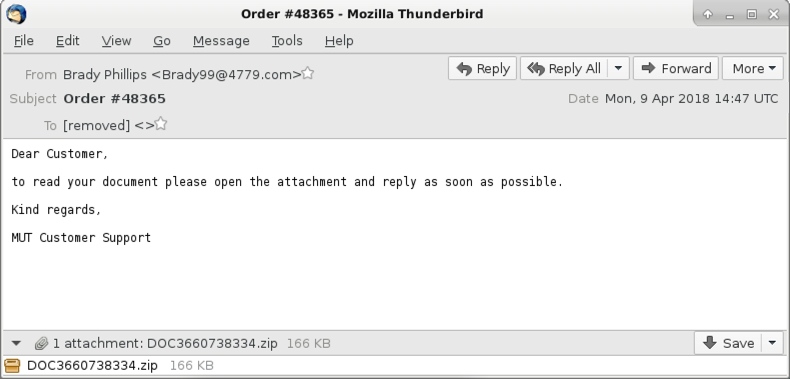
Shown above: Screenshot of the email.
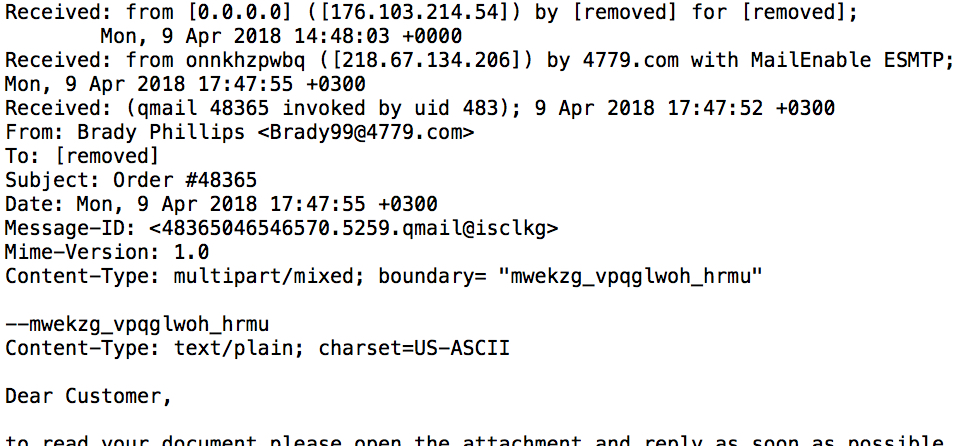
Shown above: Screenshot of the email headers.
EMAIL HEADERS:
Received: from [0.0.0[.]0] ([176.103.214[.]54]) by [removed] for [removed];
Mon, 9 Apr 2018 14:48:03 +0000
Received: from onnkhzpwbq ([218.67.134[.]206]) by 4779[.]com with MailEnable ESMTP;
Mon, 9 Apr 2018 17:47:55 +0300
Received: (qmail 48365 invoked by uid 483); 9 Apr 2018 17:47:52 +0300
From: Brady Phillips <Brady99@4779[.]com>
Subject: Order #48365
Date: Mon, 9 Apr 2018 17:47:55 +0300
Message-ID: <48365046546570.5259.qmail@isclkg>

Shown above: Extracting the Word document from the attached zip file.
TRAFFIC
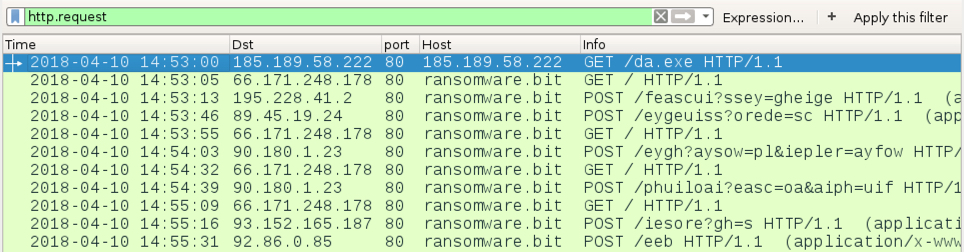
Shown above: Infection traffic filtered in Wireshark.
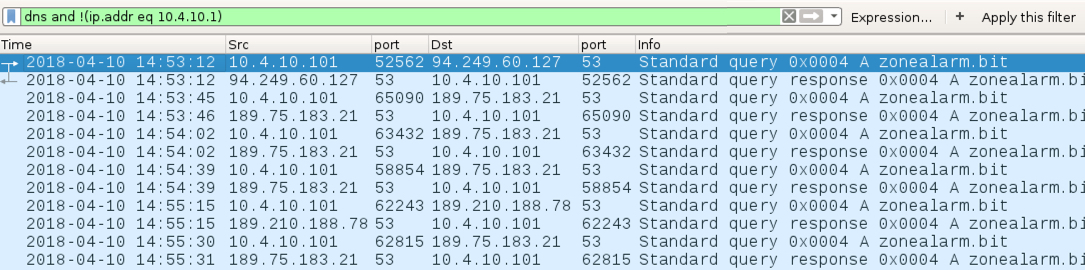
Shown above: DNS traffic to unusual hosts that returned IP addresses for HTTP traffic to ransomware[.]bit.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 185.189.58[.]222 port 80 - 185.189.58[.]222 - GET /da.exe
- DNS query for ipv4bot.whatismyipaddress[.]com - returned IP address used for HTTP GET requests to ransomware[.]bit
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET / (IP address check)
- DNS queries for ns1.corp-servers[.]ru - returned IP addresses used for DNS queries on zonealarm[.]bit
- DNS queries for zonealarm[.]bit - returned IP addresses used in HTTP POST requests to ransomware[.]bit
- 195.228.41[.]2 port 80 - ransomware[.]bit - POST /feascui?ssey=gheige
- 89.45.19[.]24 port 80 - ransomware[.]bit - POST /eygeuiss?orede=sc
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET / (IP address check)
- 90.180.1[.]23 port 80 - ransomware[.]bit - POST /eygh?aysow=pl&iepler=ayfow
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET / (IP address check)
- 90.180.1[.]23 port 80 - ransomware[.]bit - POST /phuiloai?easc=oa&aiph=uif
- 66.171.248[.]178 port 80 - ransomware[.]bit - GET / (IP address check)
- 93.152.165[.]187 port 80 - ransomware[.]bit - POST /iesore?gh=s
- 92.86.0[.]85 port 80 - ransomware[.]bit - POST /eeb
DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- gandcrab2pie73et[.]onion
- gandcrab2pie73et[.]onion[.]rip
- gandcrab2pie73et[.]onion[.]plus
- gandcrab2pie73et[.]onion[.]to
FILE HASHES
ZIP ARCHIVE FROM THE EMAIL:
- SHA256 hash: 491c45a3326709e23e31d57f19baf1ffc6b394320a4e9dc6c38b177019d4f024
File size: 169,604 bytes
File description: Zip archive from malspam pushing Gandcrab on Monday 2018-04-09
WORD DOCUMENT EXTRACTED FROM THE ABOVE ARCHIVE:
- SHA256 hash: bcff17a1885a330497594ca80b29257313195e3b065f674ad2d205b7c63b919d
File size: 169,472 bytes
File description: Word document with macro to retrieve and execute the malware binary
MALWARE BINARY RETRIEVED AFTER ENABLING MACROS:
- SHA256 hash: a8c4a89f2dd8c43f29f336cbd9af2a1cee3f9309c54de20ac86730feb127f667
File size: 301,064 bytes
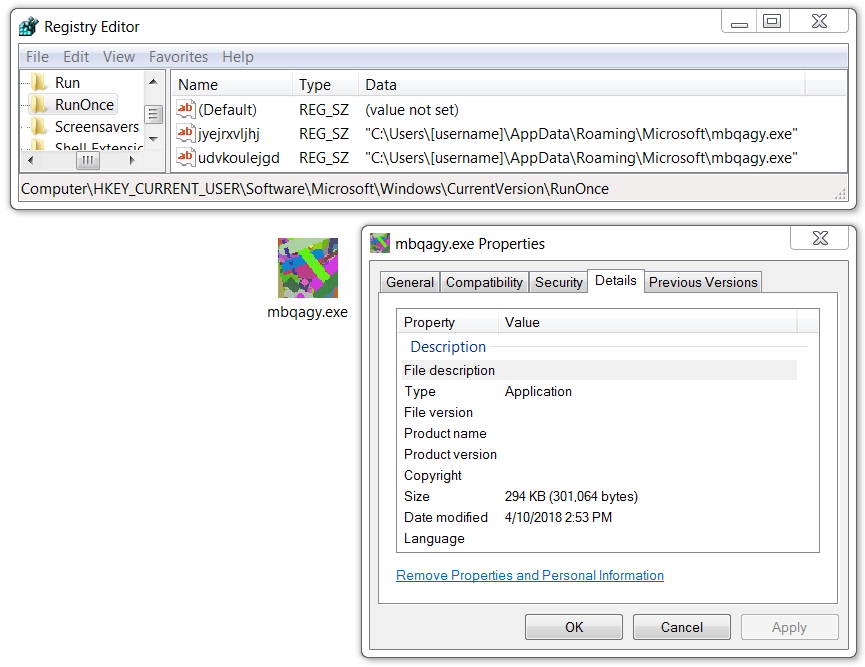
File location: C:\Users\[username]\AppData\Local\Temp\bKKc.exe
File location: C:\Users\[username]\AppData\Roaming\Microsoft\mbqagy.exe
File description: Gandcrab ransomware
Shown above: Gandcrab ransomware persistent on an infected Windows host.
IMAGES FROM AN INFECTION
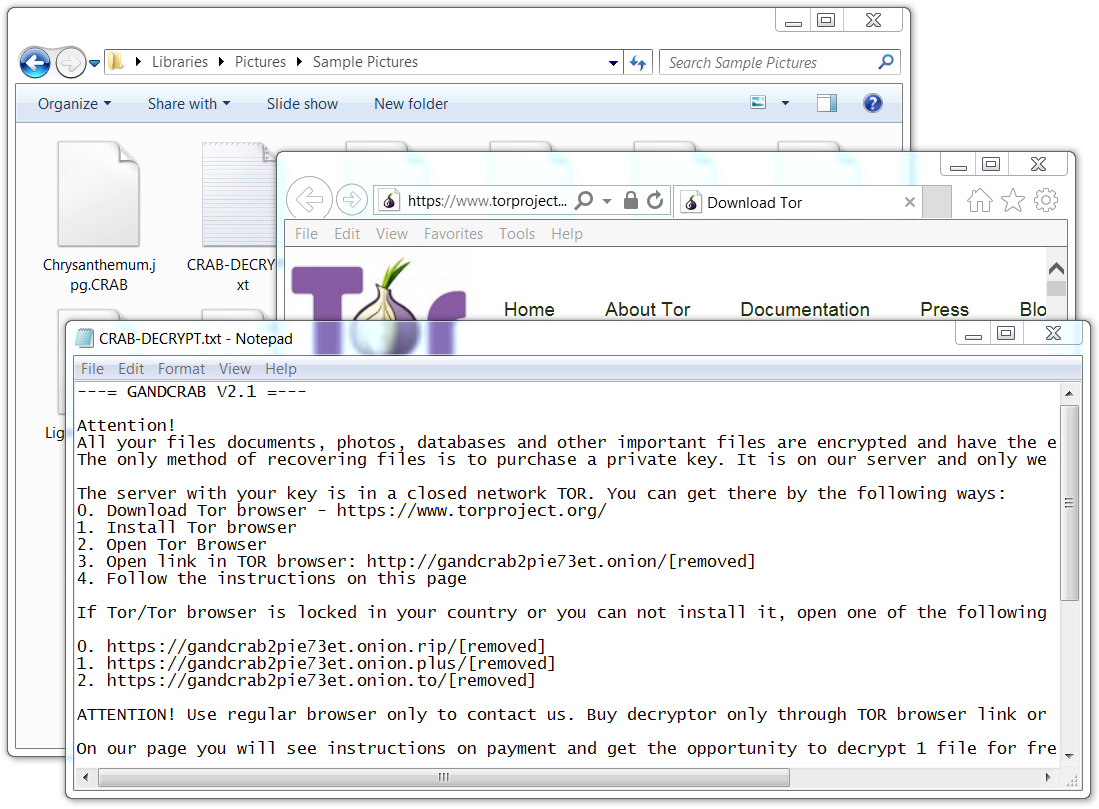
Shown above: Partial screenshot from the desktop of an infected Windows host.
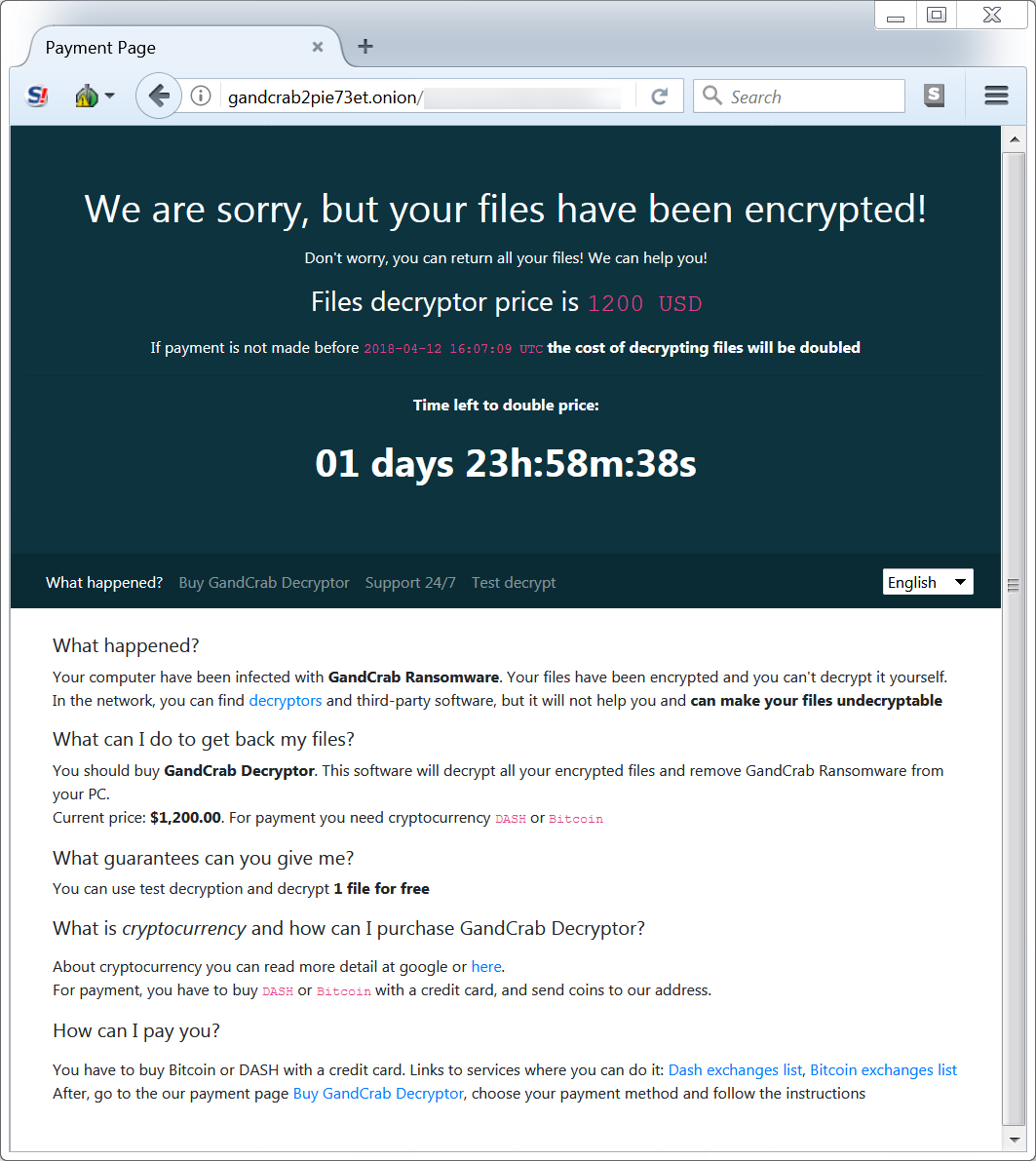
Shown above: A screenshot of today's Gandcrab ransomware decryptor.
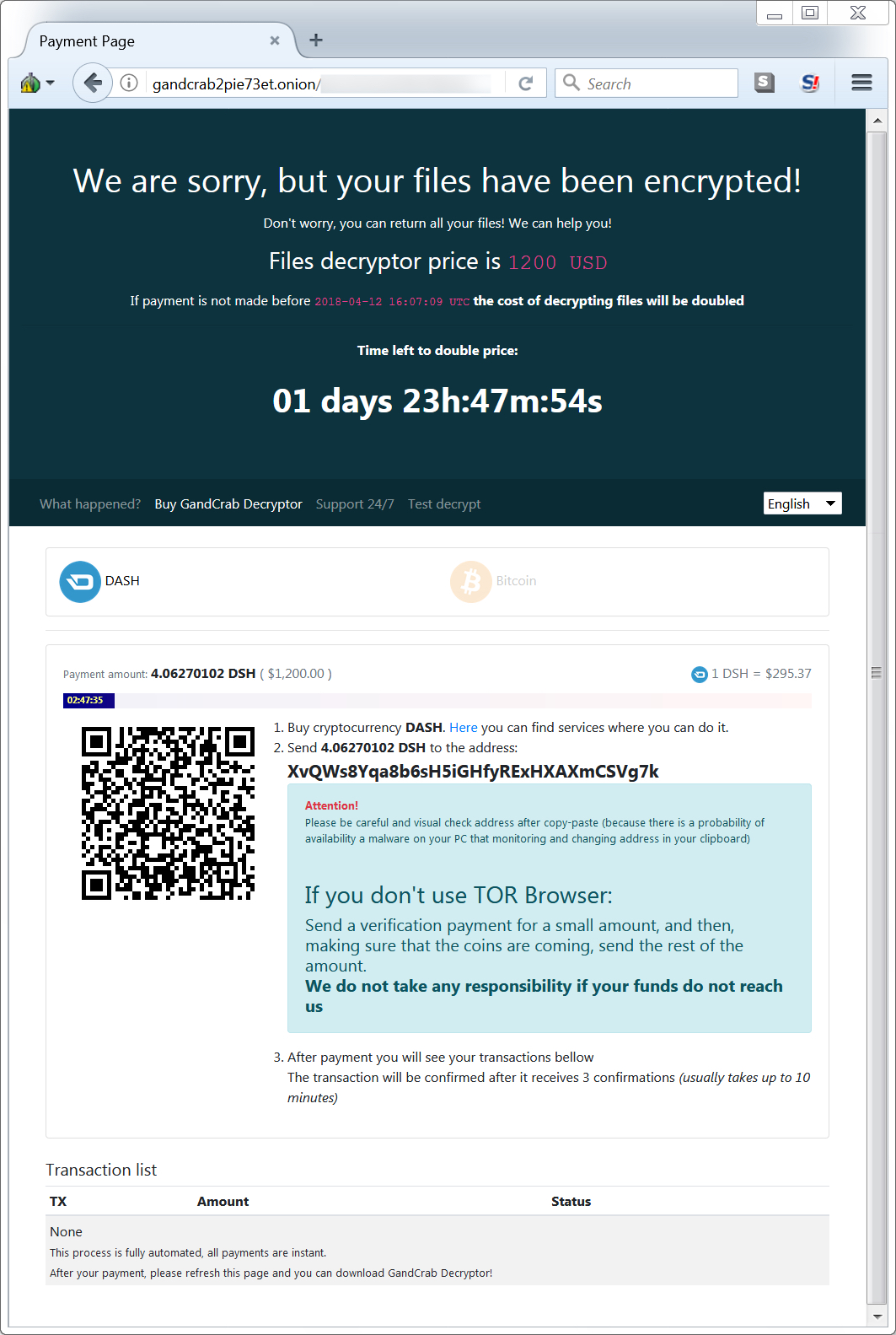
Shown above: Decryptor instructions for paying the ransom with Dash cryptocurrency.
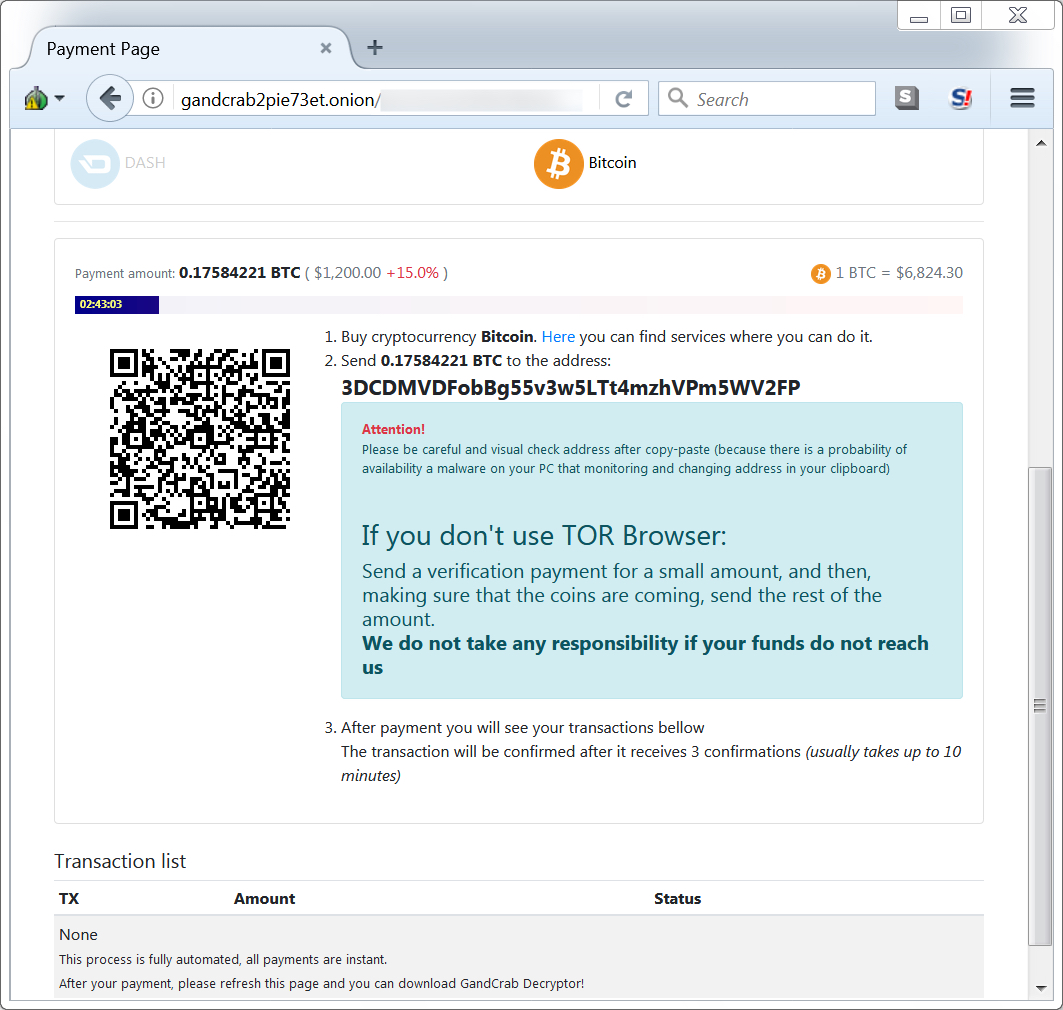
Shown above: Decryptor instructions for paying the ransom with Bitcoin cryptocurrency.
Click here to return to the main page.