2018-05-24 - QUICK POST: TRICKBOT MALSPAM (INFECTION FROM CLIENT TO DOMAIN CONTROLLER)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-05-24-Trickbot-malspam-1140-UTC.eml.zip 67 kB (67,214 bytes)
- 2018-05-24-Trickbot-infection-on-single-host.pcap.zip 5.4 MB (5,425,948 bytes)
- 2018-05-24-Trickbot-infection-in-AD-environment.pcap.zip 18.9 MB (18,852,733 bytes)
- 2018-05-24-malware-and-artifacts-from-Trickbot-infection.zip 956 kB (955,622 bytes)
NOTES:
- I did 2 runs for this infection traffic: One for a single Windows host, and one for a Windows client in an Active Directory environment logged in to a domain controller.
- Like I posted last month on 2018-04-30, today's infection went from the Windows client to the domain controller over SMB.
- Unlike last time, there's additional HTTP traffic over port 8082 with information from the infected Windows hosts (something I don't remember seeing before).
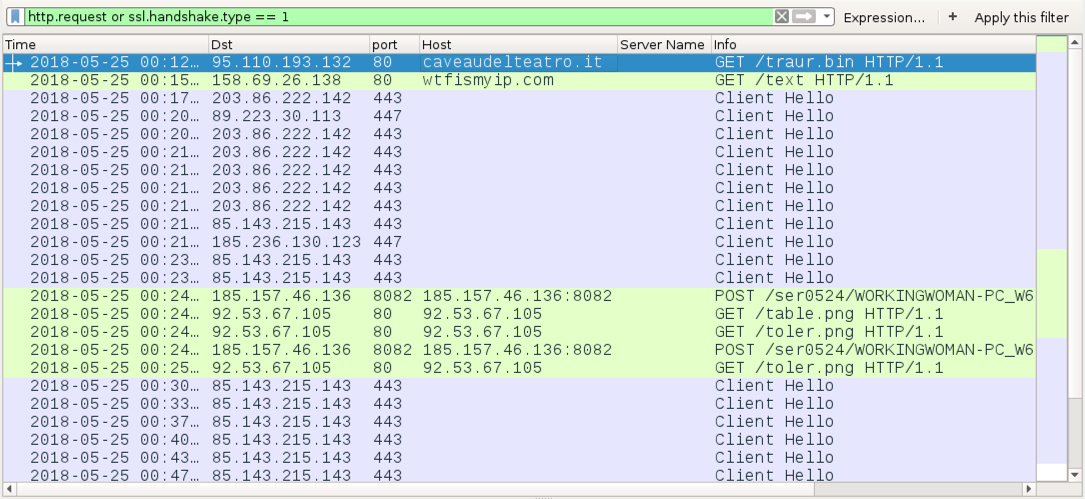
Shown above: Infection traffic from a single Windows host (for example, a home user) filtered in Wireshark.
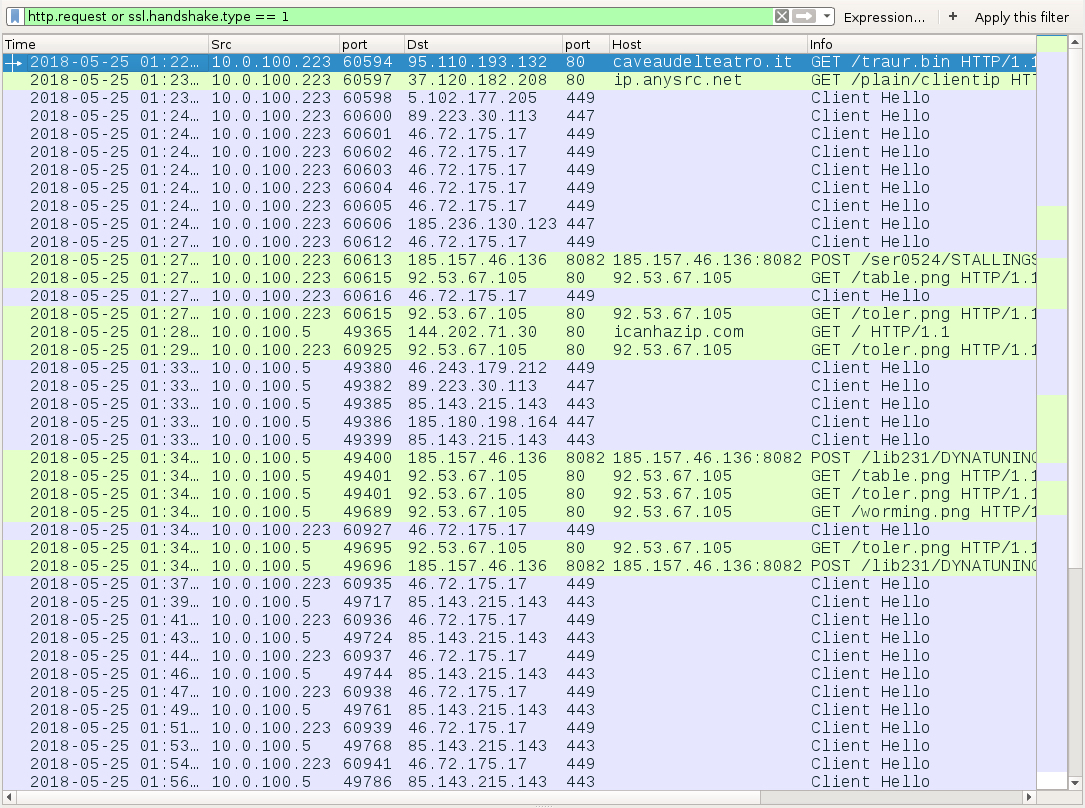
Shown above: Infection traffic from a Windows client (like a work computer) in an AD environment filtered in Wireshark.
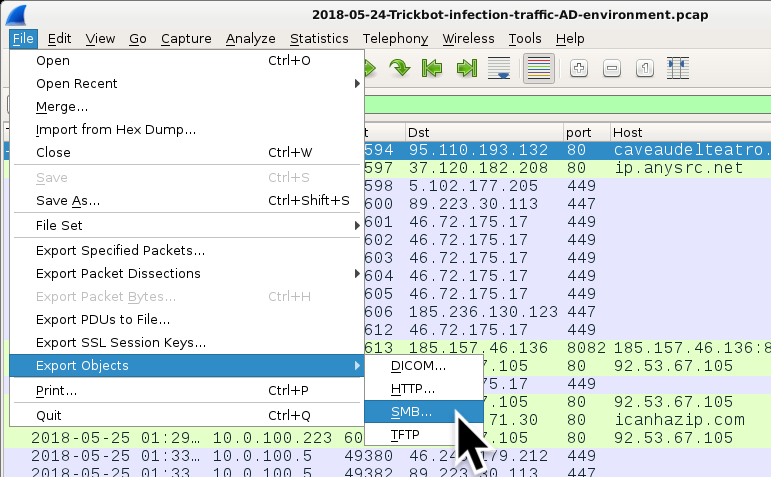
Shown above: You can extract these Trickbot malware samples sent over SMB from the pcap in Wireshark by using File --> Export Objects --> SMB...
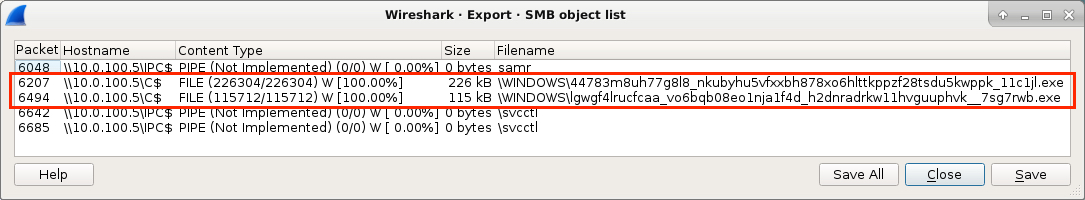
Shown above: The malware binaries ent over SMB (additional file hashes were also found from the HTTP objects).
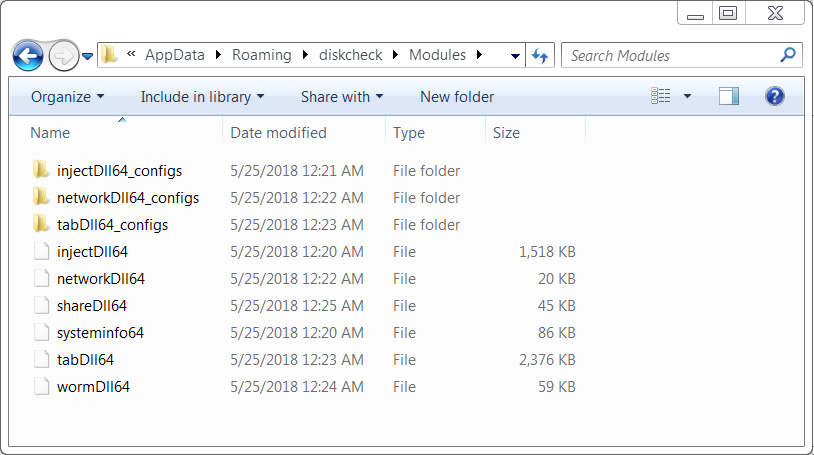
Shown above: Malware objects from a folder in the infected user's AppData\Roaming directory.
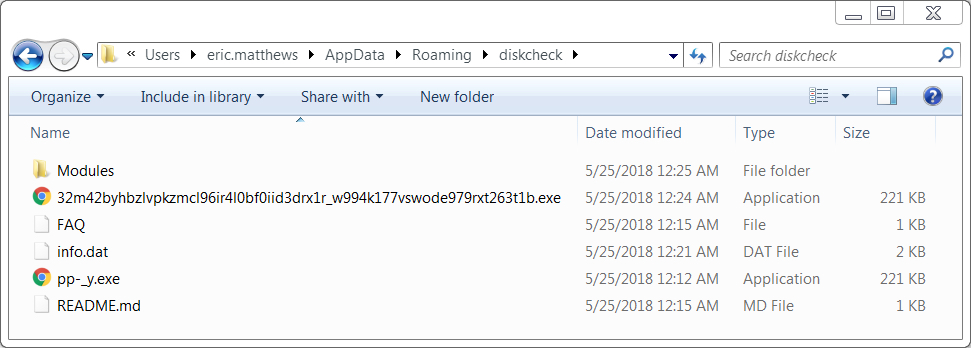
Shown above: An additional file, the same size as the downloaded Trickbot binary, but with a different file hash.
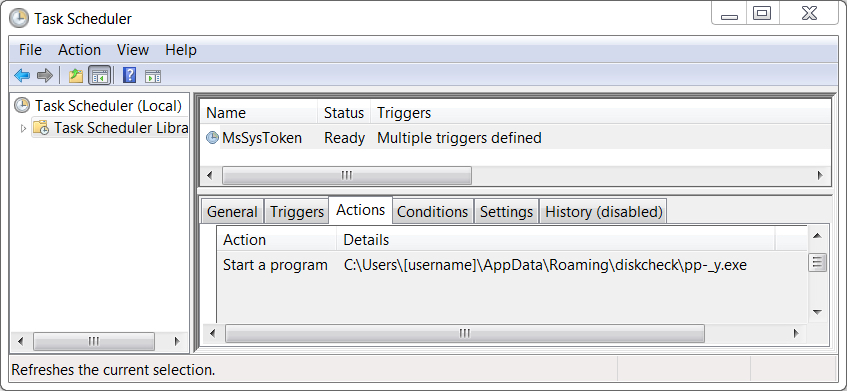
Shown above: Scheduled task to keep the Trickbot infection persistent.
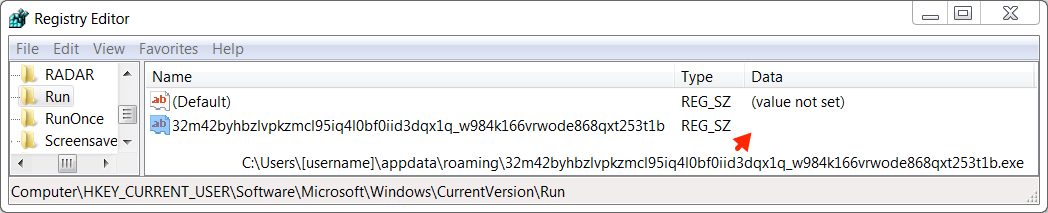
Shown above: Windows registry update for the additional malware binary.
Click here to return to the main page.
