2018-07-13 - MALSPAM USES .IQY FILE TO PUSH FLAWED AMMYY RAT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-07-13-Flawed-Ammyy-malspam-tracker.csv.zip 0.8 kB (765 bytes)
- 2018-07-13-Flawed-Ammyy-malspam-tracker.csv (1,041 bytes)
- 2018-07-13-Flawed-Ammyy-malspam-6-examples.txt.zip 3.0 kB (3,046 bytes)
- 2018-07-13-Flawed-Ammyy-malspam-6-email-examples.txt (25,291 bytes)
- 2018-07-13-Flawed-Ammyy-infection-traffic.pcap.zip 809.7 kB (809,731 bytes)
- 2018-07-13-Flawed-Ammyy-infection-traffic.pcap (914,768 bytes)
- 2018-07-13-malware-from-Flawed-Ammyy-infection.zip 437.9 kB (437,877 bytes)
- PDF_060975187_13072018.iqy (33 bytes)
- winmedia2.exe (160,256 bytes)
- wsus.exe (669,472 bytes)
NOTES:
- More malspam using .iqy files to spread Flawed Ammyy RAT.
- My previous documentation on this activity was 2018-06-13.
- As noted before, IQY is a file extension for an "internet query" used by Microsoft Excel. You have to click through some warnings to infect a vulnerable Windows host.
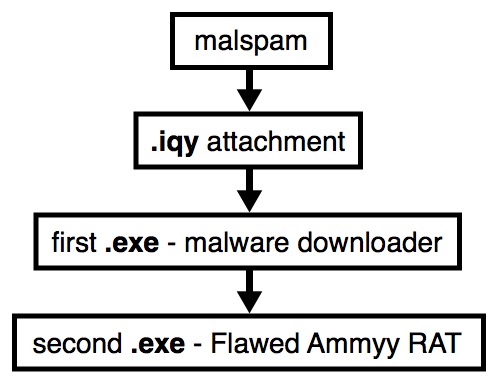
Shown above: Flow chart for this activity.
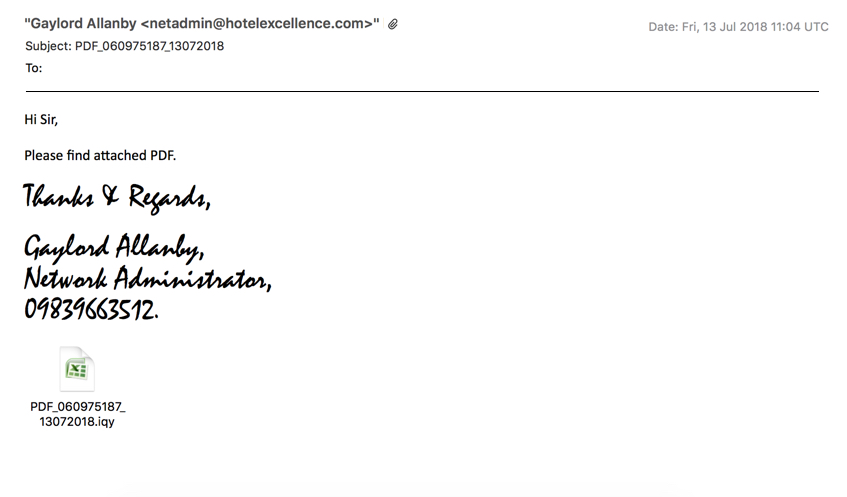
Shown above: Screenshot from an example of the malspam.
DATA FROM 6 EMAIL EXAMPLES:
- Date/Time: Friday 2018-07-13 as early as 11:04 UTC through at least 12:42 UTC
- Received: from [1.55.134[.]151] ([1.55.134[.]151])
- Received: from [87.116.190[.]155] ([87.116.191[.]37])
- Received: from [116.109.153[.]129] ([116.109.153[.]129])
- Received: from [182.176.108[.]95] ([182.176.108[.]95])
- Received: from nobody[.]invalid ([5.237.22[.]89])
- Received: from static-181-143-64-10.une[.]net[.]co ([181.143.64[.]10])
- From: "Aurelia Winter" <netadmin@casatahoe[.]com>
- From: "Cesar Gonzalez" <netadmin@fabricius-polstring[.]dk>
- From: "Gaylord Allanby" <netadmin@hotelexcellence[.]com>
- From: "Kurt Meechan" <netadmin@6figureoutsourcingsecrets[.]com>
- From: "Leo Lawler" <netadmin@club-in[.]com>
- From: "Renee Stockdall" <netadmin@lpgcpas[.]com>
- Subject: DOC_2348734937_13072018
- Subject: PDF_33975632_13072018
- Subject: PDF_060975187_13072018
- Subject: PDFFILE_831835141665_13072018
- Subject: SCN_023644328_13072018
- Subject: SCN_718592162_13072018
ATTACHMENT NAMES:
- DOC_2348734937_13072018.iqy
- PDF_33975632_13072018.iqy
- PDF_060975187_13072018.iqy
- PDFFILE_831835141665_13072018.iqy
- SCN_023644328_13072018.iqy
- SCN_718592162_13072018.iqy
TRAFFIC
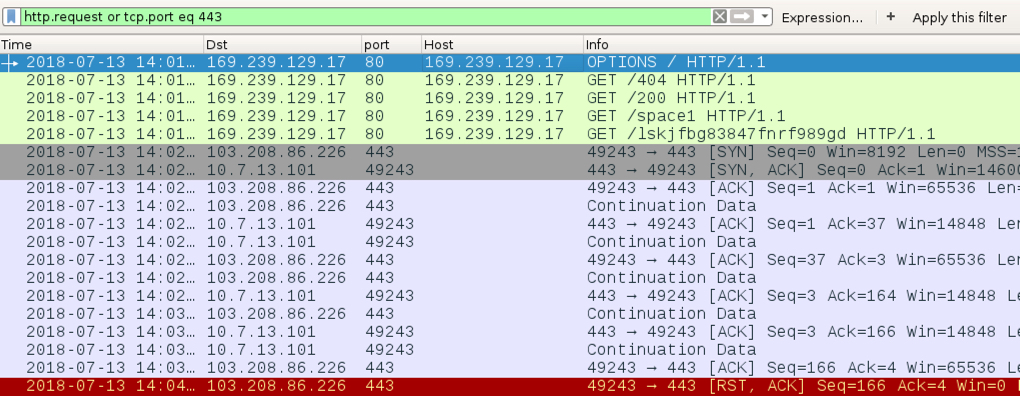
Shown above: Traffic from an infection filtered in Wireshark.
NETWORK TRAFFIC FROM AN INFECTED LAB HOST:
- 169.239.129[.]17 port 80 - 169.239.129[.]17 - OPTIONS /
- 169.239.129[.]17 port 80 - 169.239.129[.]17 - GET /404
- 169.239.129[.]17 port 80 - 169.239.129[.]17 - GET /200
- 169.239.129[.]17 port 80 - 169.239.129[.]17 - GET /space1
- 169.239.129[.]17 port 80 - 169.239.129[.]17 - GET /lskjfbg83847fnrf989gd
- 103.208.86[.]226 port 443 - Flawed Ammyy post-infection traffic (not HTTPS/SSL/TLS)
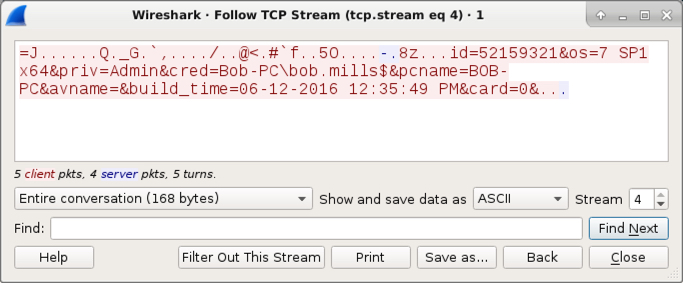
Shown above: Callback traffic caused by the Flawed Ammyy executable.
FILE HASHES
MALSPAM ATTACHMENTS:
- SHA256 hash: 15c074ab2c3c57e199a9a123bd41a17eca61e5c475f161ee2cc8242d41649bf1
File size: 33 bytes
File name: [various names, all ending with .iqy]
File description: Malspam attachment, Excel-based Internet Query (.iqy) file
INITIAL EXECUTABLE:
- SHA256 hash: 5f251ed33fb1b6960b4d5641b44b44f67277765aa69649977a27ec79cb6153da
File size: 160,256 bytes
File location: C:\Users\[username]\AppData\Local\temp\winmedia2.exe
File description: File downloader that grabbed Flawed Ammyy binary
FOLLOW-UP EXECUTABLE:
- SHA256 hash: 73e149adb7cc2a09a7af59aecd441fd4469fc0342b687097cadfbce10896c629
File size: 669,472 bytes
File location: C:\ProgramData\Microsoft Help\wsus.exe
File description: Flawed Ammyy binary
Click here to return to the main page.