2018-09-05 - EMOTET INFECTION WITH ICEDID BANKING TROJAN AND AZORULT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-09-05-Emotet-malspam-with-PDF-attachments-3-examples.zip 7.9 kB (7,898 bytes)
- 2018-09-05-Emotet-infection-with-IcedID-banking-Trojan-and-AZORult.pcap.zip 5.3 MB (5,328,331 bytes)
- 2018-09-05-malware-and-artifacts-from-Emotet-infection-with-IcedID-and-AZORult.zip 960 kB (960,083 bytes)
NOTES:
- Traffic-wise, it looks like Emotet retrieved IcedID, then IcedID retrieved AZORult.
- As noted yesterday, this week I've seen Emotet malspam with PDF attachments, where there is no link in the message text for an Emotet Word doc.
- Instead, the PDF attachments have a link for the Emotet Word doc.
- Of note, I'm also seeing Word docs directly attached to the emails from Emotet malspam.
- And as usual I'm also finding URLs from the Emotet malspam message text with links to the Word document (these emails have no attachments).
- A final reminder that Emotet malspam currently uses at least 3 methods to infect a vulnerable Windows host:
- Malspam with no attachments and a link to the Word doc in the message text.
- Malspam with no links in the message text, but a PDF attachment with a link to the Word doc in that PDF file.
- Malspam with no links in the message text, but a Word doc attached directly to the email.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxp[:]//treesurveys.infrontdesigns[.]com/payment-09-18
- hxxp[:]//treesurveys.infrontdesigns[.]com/payment-09-18/
- hxxp[:]//aspettaprimavera[.]it/4LmlHpS
- hxxp[:]//aspettaprimavera[.]it/4LmlHpS/
- fillizee[.]com
- aboupir[.]com
- hxxp[:]//kanboard.globalsoftm[.]com/vendor/symfony/console/Tests/Formatter/crypt_AU3_EXE.exe
- hxxp[:]//107.182.230[.]25/index.php
- hxxp[:]//201.170.69[.]112/whoami.php
EMAILS
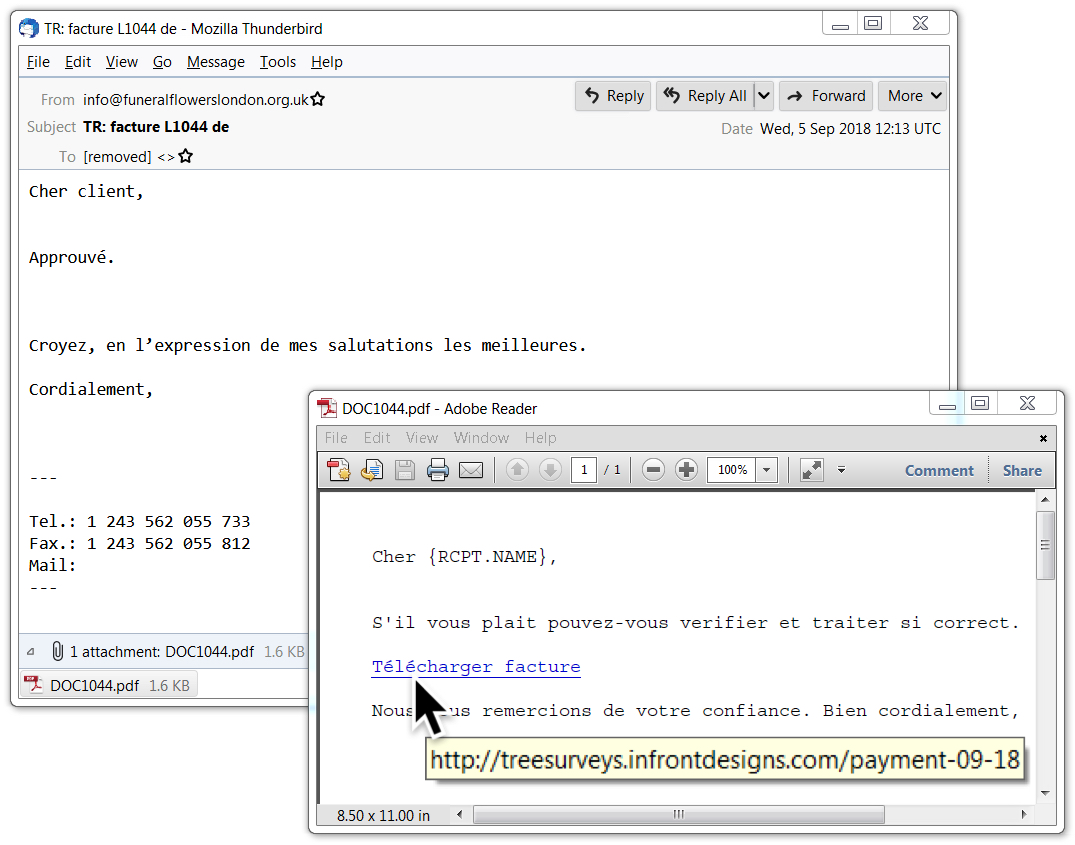
Shown above: Screenshot from a malspam example on Wednesday 2018-09-05.
3 EXAMPLES OF EMOTET MALSPAM WITH PDF ATTACHMENTS:
- 2018-09-05 at 09:03 UTC -- From: admin.maraisdal@barvallei[.]co[.]za -- Subject: Payment Reminder
- 2018-09-05 at 12:13 UTC -- From: info@funeralflowerslondon[.]org[.]uk -- Subject: TR: facture L1044 de
- 2018-09-05 at 16:20 UTC -- From: hector@almadisa[.]com -- Subject: Paiements
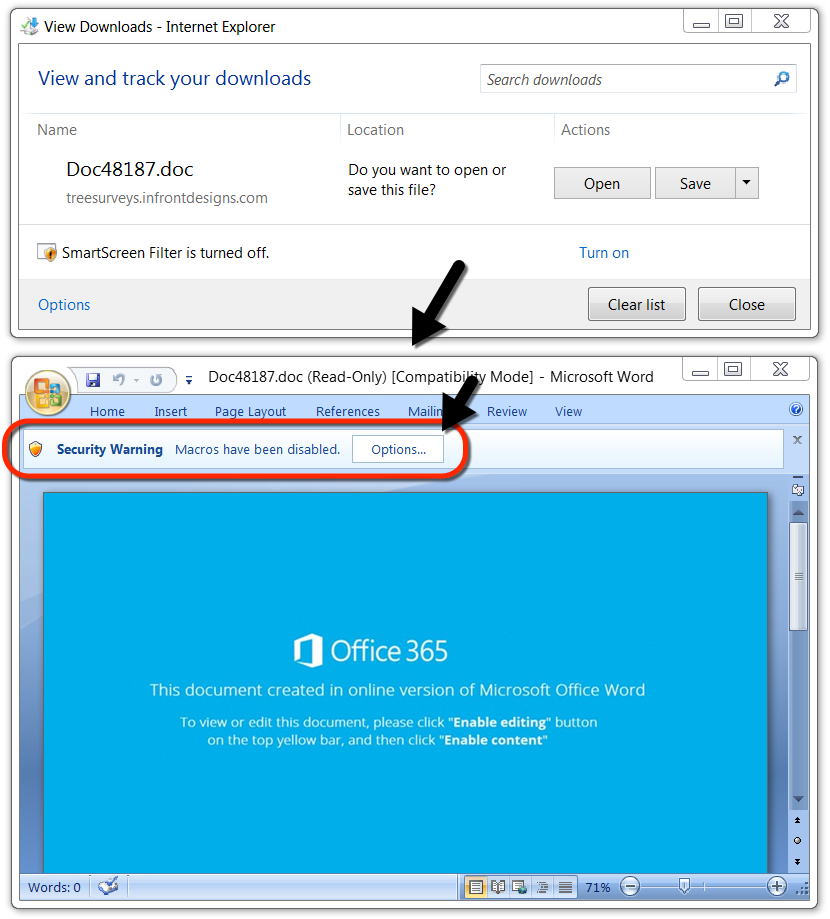
Shown above: Clicking on the link in the PDF document downloads the Word document used to infect a vulnerable Windows host.
TRAFFIC
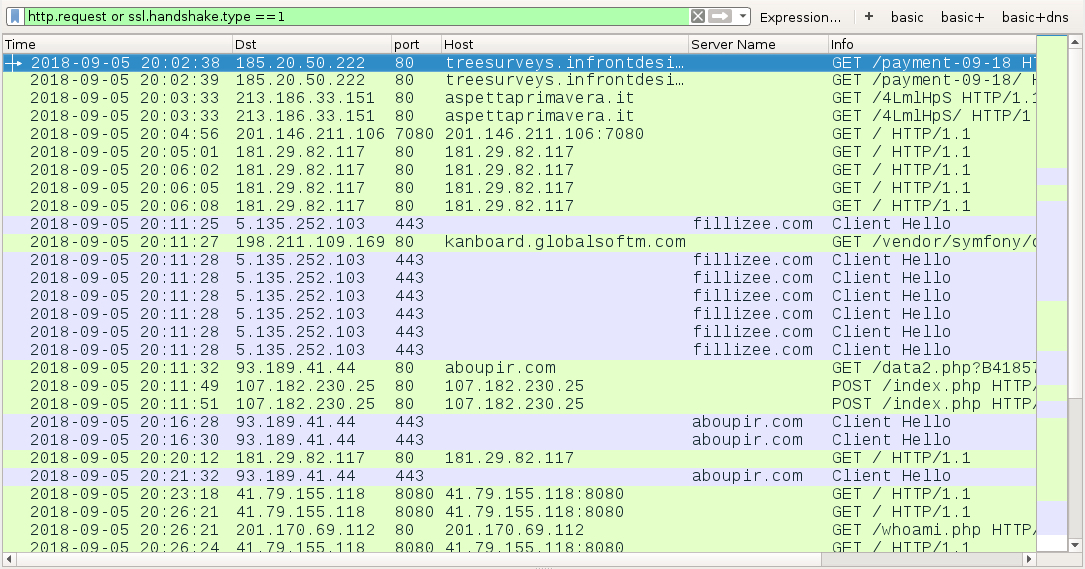
Shown above: Infection traffic filtered in Wireshark.
INITIAL INFECTION TRAFFIC (EMOTET WORD DOC AND EXECUTABLE):
- 185.20.50[.]222 port 80 - treesurveys.infrontdesigns[.]com - GET /payment-09-18
- 185.20.50[.]222 port 80 - treesurveys.infrontdesigns[.]com - GET /payment-09-18/
- 213.186.33[.]151 port 80 - aspettaprimavera[.]it - GET /4LmlHpS
- 213.186.33[.]151 port 80 - aspettaprimavera[.]it - GET /4LmlHpS/
EMOTET POST-INFECTION TRAFFIC:
- 201.146.211[.]106 port 7080 - 201.146.211[.]106:7080 - GET /
- 181.29.82[.]117 port 80 - 181.29.82[.]117 - GET /
- 41.79.155[.]118 port 8080 - 41.79.155[.]118:8080 - GET /
- 41.79.155[.]118 port 8080 - 41.79.155[.]118:8080 - GET /
- 201.170.69[.]112 port 80 - 201.170.69[.]112 - GET /whoami.php
ICEDID BANKING TROJAN POST-INFECTION TRAFFIC:
- 5.135.252[.]103 port 443 - fillizee[.]com - SSL/TLS traffic caused by IcedID banking Trojan
- 93.189.41[.]44 port 80 - aboupir[.]com - GET /data2.php?B41857922C8EBEE9
- 93.189.41[.]44 port 443 - aboupir[.]com - SSL/TLS traffic caused by IcedID banking Trojan
POST-INFECTION TRAFFIC ASSOCIATED WITH AZORULT:
- 198.211.109[.]169 port 80 - kanboard.globalsoftm[.]com - GET /vendor/symfony/console/Tests/Formatter/crypt_AU3_EXE.exe
- 107.182.230[.]25 port 80 - 107.182.230[.]25 - POST /index.php
FILE HASHES
PDF ATTACHMENTS FROM THOSE 3 EXAMPLES:
- 3a0f7fcf42df97c0dba446eade1ac1928d04c97ae97774779b46e87193741ca4 - 1,668 bytes - DOC-3746.pdf
- 28c06c2911c41a1027def891ab5b60b6ee8db221bafb38cb7cf742ac6f1a2800 - 1,593 bytes - DOC1044.pdf
- bda2d2488d1f2d611f9ec792ef7026a461bff753ff156f75da3b1fdf375097ef - 1,619 bytes - DOC154122.pdf
MALWARE RETRIEVED FROM MY INFECTED WINDOWS HOST:
- SHA256 hash: 2106af69195037522d4458574a6734b6156e3d6a181c01d55e72051c22471258
File size: 78,720 bytes
File description: Downloaded Word doc with macro for Emotet
- SHA256 hash: 6556cc4b93b46cc22a7bcdd07f5e0af6aa1b4bec96831232f118fb64158efc45
File size: 510,464 bytes
File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random name].exe
File description: Emotet malware binary retreived from the infected Windows host
- SHA256 hash: 24503419c21a345173822bd36297c8815e8f91c78c0d46211f33a1738479238a
File size: 475,648 bytes
File location: C:\ProgramData\QLUwn7PzPqFo72.exe
File location: C:\ProgramData\tx9r.exe
File description: IcedID malware retreived from the infected Windows host
- SHA256 hash: 3c84bfb7377d0e47c1eaa12fdbee6f5fcd19d482cc9aa3790507f4445d719290
File size: 475,648 bytes
File location: C:\ProgramData\{5A0BA599-0B99-4344-A7E9-AEAFDACF4896}\ayxuiczipqtf
File description: IcedID malware persistent on the infected Windows host
- SHA256 hash: 3a65b5735981f636fbaf9cff05e78f933d10b5191209eb077d4a29210c23e739
File size: 514,560 bytes
File location: hxxp[:]//kanboard.globalsoftm[.]com/vendor/symfony/console/Tests/Formatter/crypt_AU3_EXE.exe
File description: AZORult malware retreived from kanboard.globalsoftm.com
MORE IMAGES
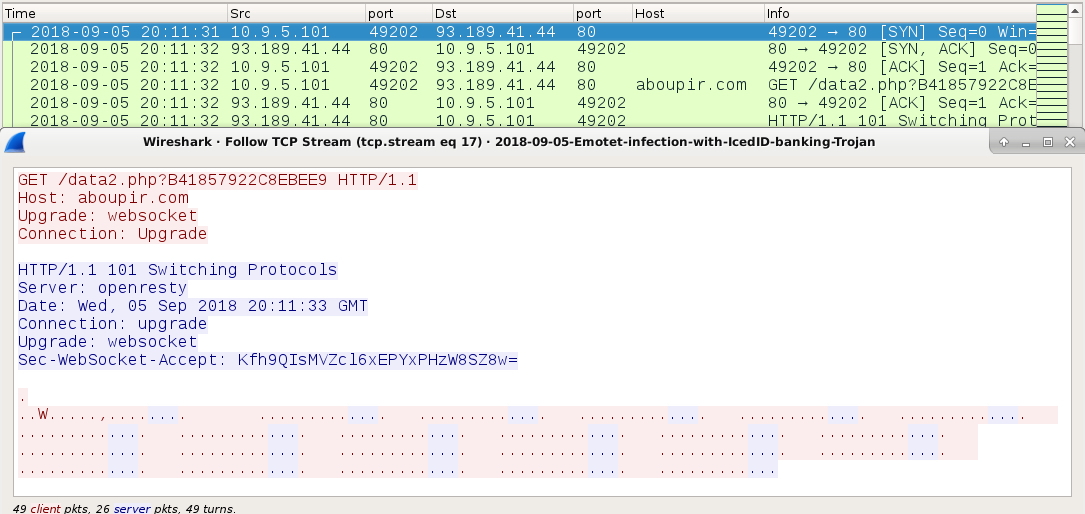
Shown above: Websocket traffic caused by IcedID on the infected Windows host.
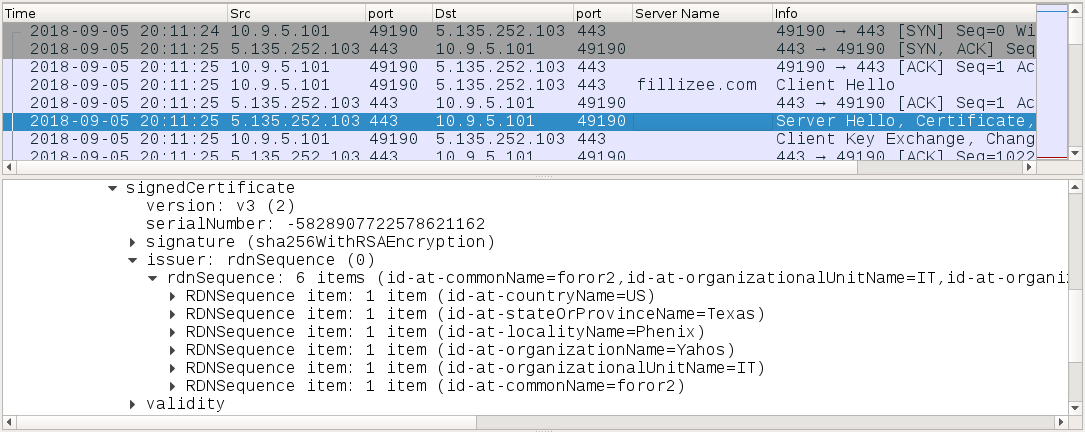
Shown above: SSL/TLS certificate data consistent with previous samples of IcedID banking Trojan (1 of 2).
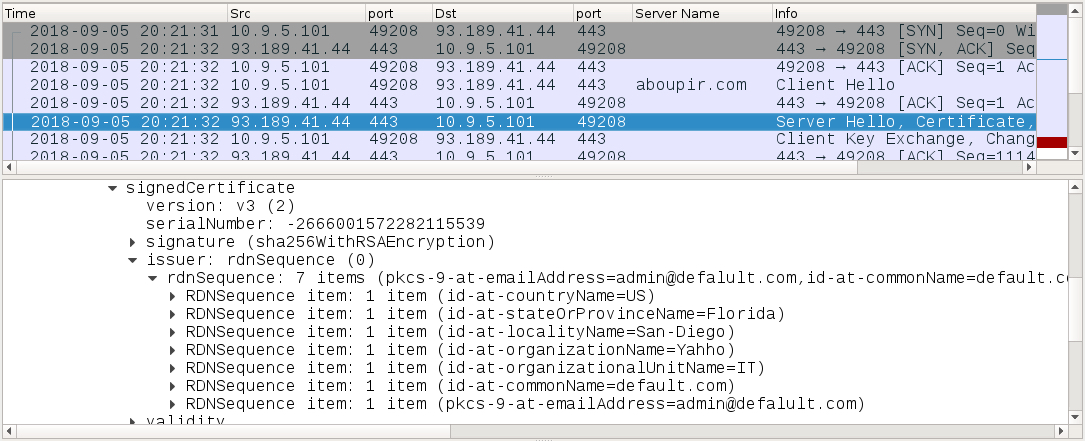
Shown above: SSL/TLS certificate data consistent with previous samples of IcedID banking Trojan (2 of 2).
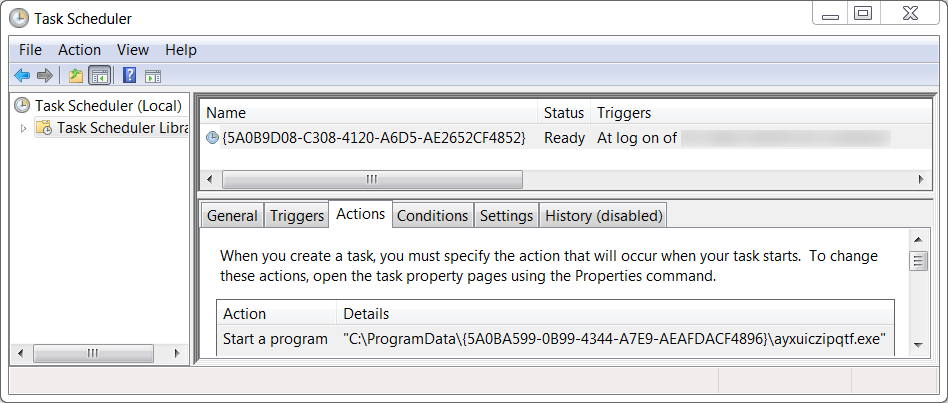
Shown above: Scheduled task to keep IcedID persistent on the infected Windows host.
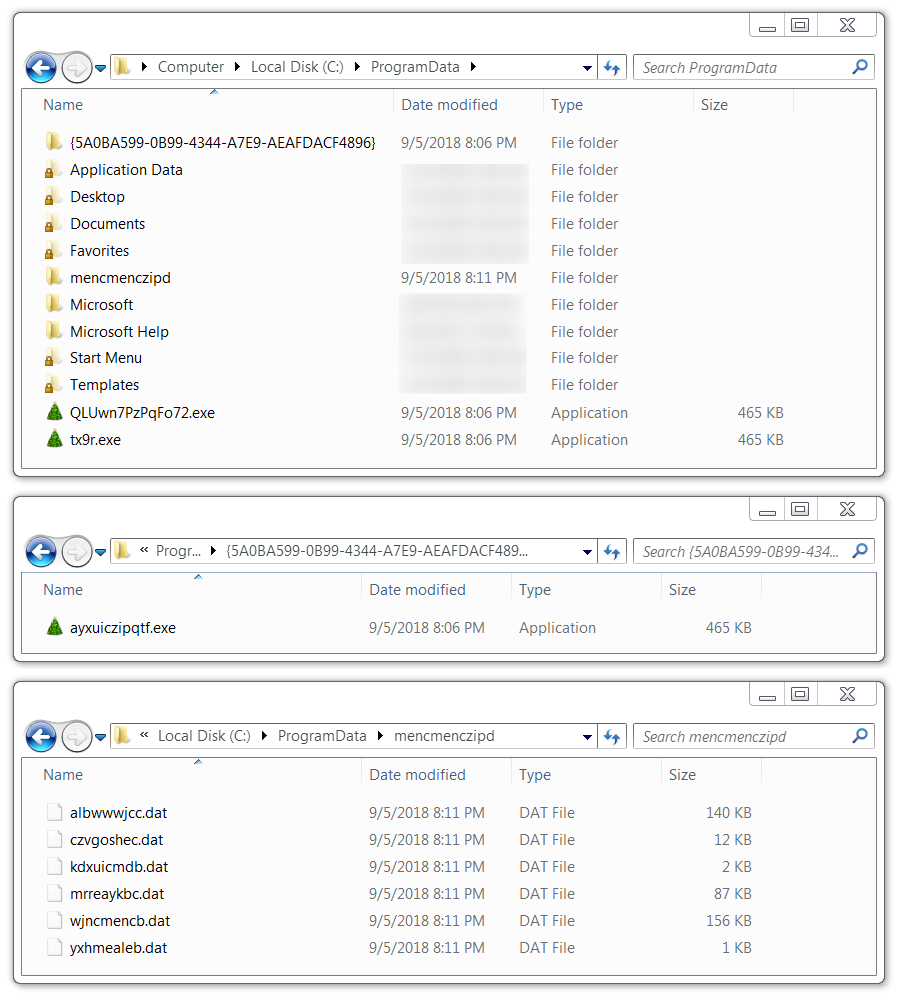
Shown above: Locations of IcedID malware and artifacts on the infected Windows host.
Click here to return to the main page.
