2018-10-04 - QUICK POST: TRICKBOT SPREADS FROM CLIENT TO DC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-10-04-Trickbot-malspam-1140-UTC.eml.zip 42.8 kB (42,786 bytes)
- 2018-10-04-Trickbot-spreads-from-client-to-DC.pcap.zip 31.6 MB (31,621,376 bytes)
- 2018-10-04-Trickbot-malware-and-artifacts.zip 24.2 MB (24,221,665 bytes)
- Incoming_CHAPS_Form.doc
- Client/
- Client/2018-10-04-downloaded-trickbot-binary-gtag-ser1004.exe
- Client/2018-10-04-Trickbot-artifact-symbolqtring.bat.txt
- Client/2018-10-04-Trickbot-scheduled-task-on-client-Msnetcs.xml.txt
- Client/AMNI/
- Client/AMNI/FAQ
- Client/AMNI/grabber_temp.INTEG.RAW
- Client/AMNI/Modules/
- Client/AMNI/Modules/importDll64
- Client/AMNI/Modules/injectDll64
- Client/AMNI/Modules/injectDll64_configs/
- Client/AMNI/Modules/injectDll64_configs/dinj
- Client/AMNI/Modules/injectDll64_configs/dpost
- Client/AMNI/Modules/injectDll64_configs/sinj
- Client/AMNI/Modules/mailsearcher64
- Client/AMNI/Modules/mailsearcher64_configs/
- Client/AMNI/Modules/mailsearcher64_configs/mailconf
- Client/AMNI/Modules/networkDll64
- Client/AMNI/Modules/networkDll64_configs/
- Client/AMNI/Modules/networkDll64_configs/dpost
- Client/AMNI/Modules/shareDll64
- Client/AMNI/Modules/systeminfo64
- Client/AMNI/Modules/wormDll64
- Client/AMNI/README.md
- Client/AMNI/rrrrrrrrrrr.exe
- Client/AMNI/tetup.exe
- DC/
- DC/2018-10-04-Trickbot-binary-C-Windows-System32-setup.exe
- DC/2018-10-04-Trickbot-scheduled-task-on-DC-Msnetcs.xml.txt
- DC/AMNI/
- DC/AMNI/FAQ
- DC/AMNI/Modules/
- DC/AMNI/Modules/importDll64
- DC/AMNI/Modules/injectDll64
- DC/AMNI/Modules/injectDll64_configs/
- DC/AMNI/Modules/injectDll64_configs/dinj
- DC/AMNI/Modules/injectDll64_configs/dpost
- DC/AMNI/Modules/injectDll64_configs/sinj
- DC/AMNI/Modules/mailsearcher64
- DC/AMNI/Modules/mailsearcher64_configs/
- DC/AMNI/Modules/mailsearcher64_configs/mailconf
- DC/AMNI/Modules/networkDll64
- DC/AMNI/Modules/networkDll64_configs/
- DC/AMNI/Modules/networkDll64_configs/dpost
- DC/AMNI/Modules/shareDll64
- DC/AMNI/Modules/systeminfo64
- DC/AMNI/README.md
- DC/AMNI/tetup.exe
NOTES:
- I usually see Trickbot send a Trickbot malware binary through SMB when spreading from client to DC.
- With the above method, you can export the two associated malware binaries from SMB in Wireshark as seen in this example posted on 2018-08-07.
- But today Trickbot used a "URL through SMB" propagation method to spread from client to DC, which I've only seen one time prior to this on 2018-08-17 (link).
- With the second method, there are no malware binaries in the SMB traffic.
IMAGES
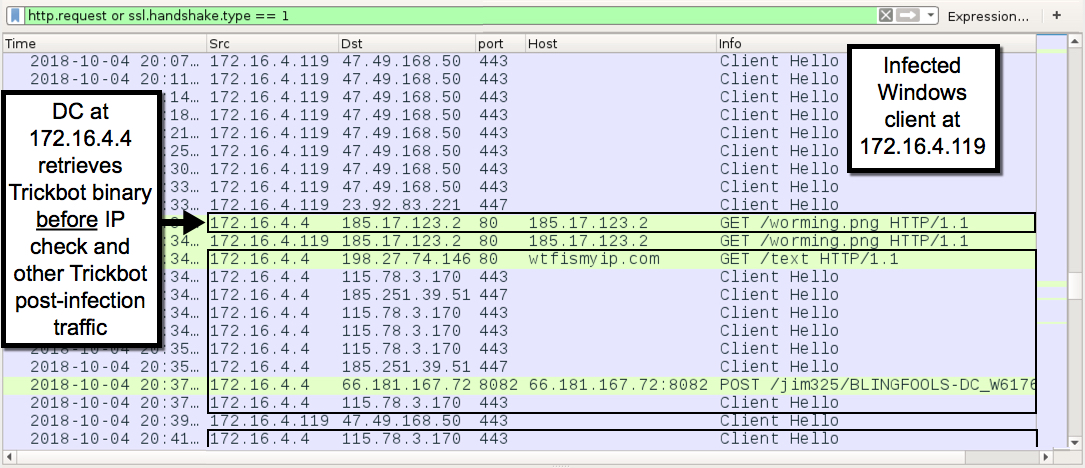
Shown above: Traffic from the infection filtered in Wireshark.
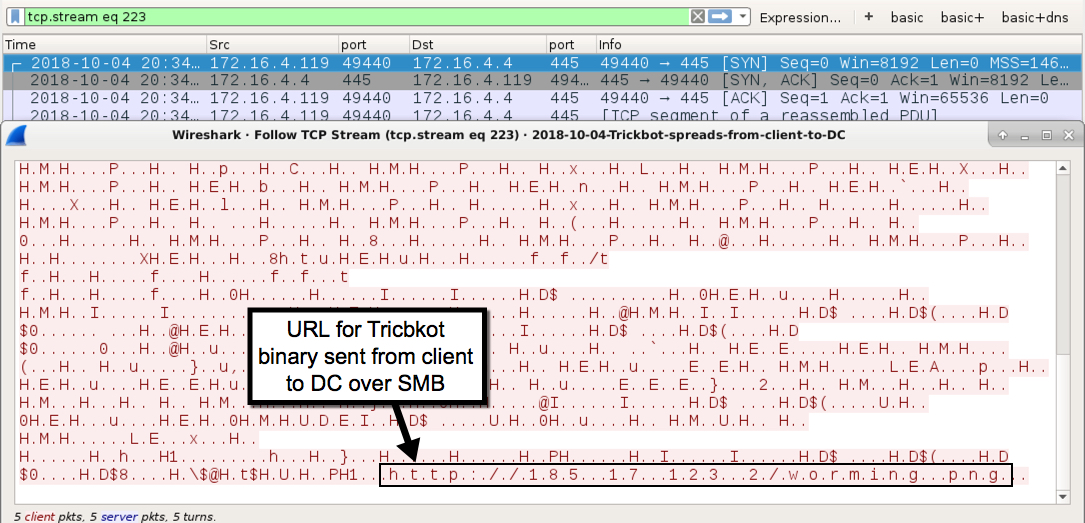
Shown above: URL for the Trickbot binary to infect the DC sent over SMB from the client to the DC.
Click here to return to the main page.
