2018-10-08 - QUICK POST: TRICKBOT SAT75 INFECTION WITH POWERSHELL EMPIRE TRAFFIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Traffic: 2018-10-08-Trickbot-sat75-infection-with-powershell-empire-traffic.pcap.zip 17.7 MB (17,664,234 bytes)
- 2018-10-08-Trickbot-sat75-infection-with-powershell-empire-traffic.pcap (22,206,323 bytes)
- Malware and artifacts: 2018-10-08-Trickbot-malware-and-artifacts.zip 17.5 MB (17,474,784 bytes)
- 2018-10-08-Trickbot-artifact.bat.txt
- 2018-10-08-Trickbot-malware-binary-gtag-sat75.exe
- 2018-10-08-attached-Word-doc-with-macro-for-Trickbot.doc
- 2018-10-08-scheduled-task-to-keep-Trickbot-persistent-Msnetcs.xml.txt
- AIMY/
- AIMY/FAQ
- AIMY/grabber_temp.INTEG.RAW
- AIMY/info.dat
- AIMY/README.md
- AIMY/rrrrrrrrrr74.exe
- AIMY/Modules/
- AIMY/Modules/importDll64
- AIMY/Modules/injectDll64
- AIMY/Modules/injectDll64_configs/
- AIMY/Modules/injectDll64_configs/dinj
- AIMY/Modules/injectDll64_configs/dpost
- AIMY/Modules/injectDll64_configs/sinj
- AIMY/Modules/mailsearcher64
- AIMY/Modules/mailsearcher64_configs/
- AIMY/Modules/mailsearcher64_configs/mailconf
- AIMY/Modules/networkDll64
- AIMY/Modules/networkDll64_configs/
- AIMY/Modules/networkDll64_configs/dpost
- AIMY/Modules/NewBCtestDll64
- AIMY/Modules/NewBCtestDll64_configs/
- AIMY/Modules/NewBCtestDll64_configs/bcconfig
- AIMY/Modules/systeminfo64
- decoded-Trickbot-modules/
- decoded-Trickbot-modules/2018-10-08-importDll64_module_decoded.dll
- decoded-Trickbot-modules/2018-10-08-injectDll64_module_decoded.dll
- decoded-Trickbot-modules/2018-10-08-mailsercher64_module_decoded.dll
- decoded-Trickbot-modules/2018-10-08-networkDll64_module_decoded.dll
- decoded-Trickbot-modules/2018-10-08-NewBCtestDll64_module_decoded.dll
- decoded-Trickbot-modules/2018-10-08-systeminfo64_module_decoded.dll
NOTES:
- I last saw Powershell Empire traffic associated with Trickbot on 2018-07-21 after letting an infected Windows host run overnight (link).
- This is the second time I've documented this.
- Based on the timing of the Powershell Empire traffic, I think it's associated with Trickbot's NewBCtestDll64 module
- Big thanks to @hasherezade for her Python script I used to decode the Trickbot modules (link).
IMAGES
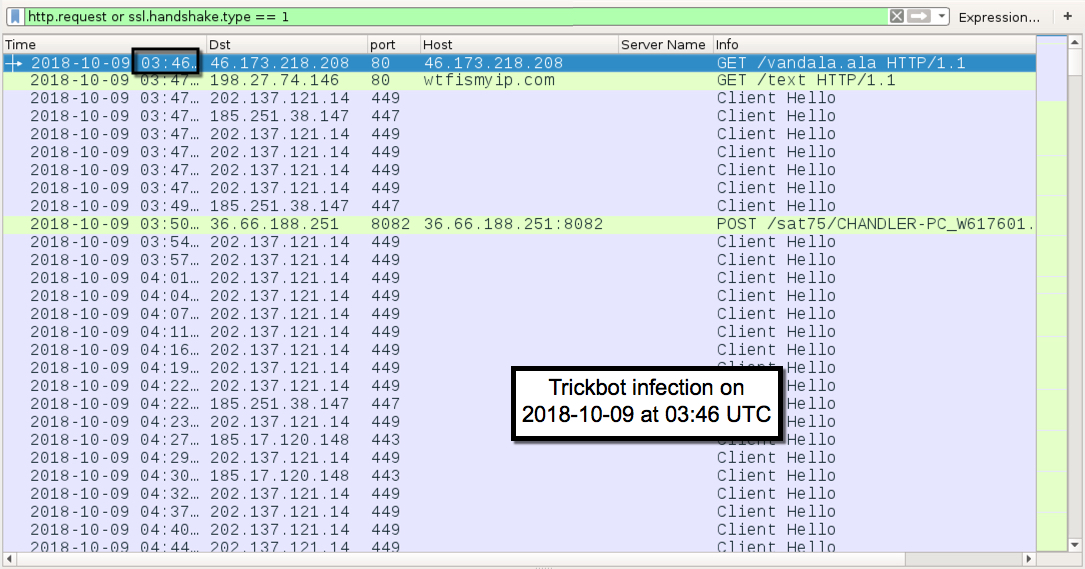
Shown above: Infection traffic filtered in Wireshark (1 of 2).
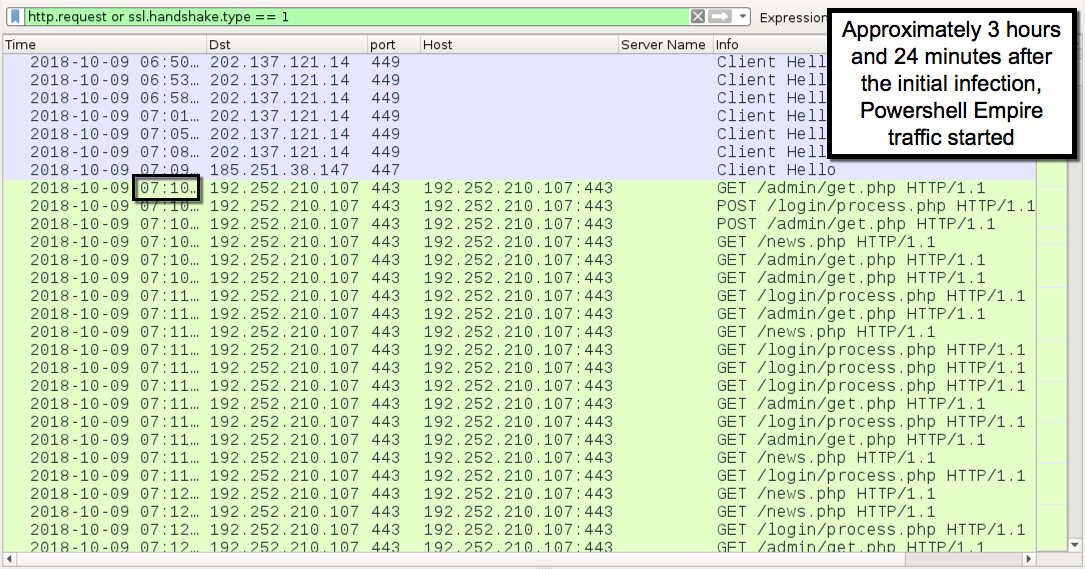
Shown above: Infection traffic filtered in Wireshark (2 of 2).
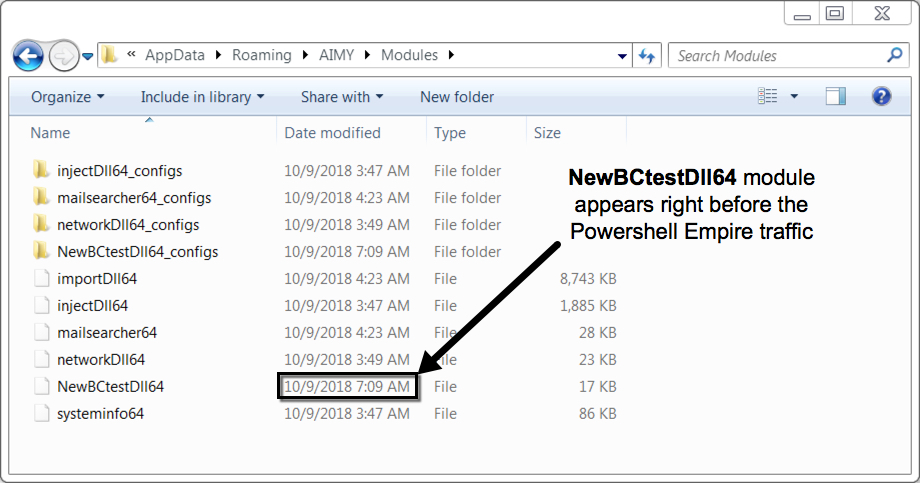
Shown above: Trickbot modules on the infected Windows host.
Click here to return to the main page.
