2018-11-21 - URSNIF INFECTION WITH DRIDEX
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-11-21-Ursnif-malspam-1027-UTC.eml.zip 53.6 kB (53,638 bytes)
- 2018-11-21-Ursnif-malspam-1027-UTC.eml (110,312 bytes)
- 2018-11-21-Ursnif-infection-with-Dridex.pcap.zip 2.5 MB (2,496,147 bytes)
- 2018-11-21-Ursnif-infection-with-Dridex.pcap (3,386,778 bytes)
- 2018-11-21-malware-and-artifacts-from-Urnsif-infection.zip 2.5 MB (2,482,825 bytes)
- 2018-11-21-Dridex-retrieved-by-Ursnif-infected-host.exe (253,952 bytes)
- 2018-11-21-Ursnif-binary.exe (506,880 bytes)
- 2018-11-21-Windows-Registry-entries-for-Ursnif.txt (10,390,302 bytes)
- 2018-11-21-attached-Word-doc-with-marco-for-Ursnif.doc.zip 45.9 kB (45,895 bytes)
- 2018-11-21-attached-Word-doc-with-marco-for-Ursnif.doc (77,056 bytes)
NOTES:
- I'm still running across a lot of malspam pushing Ursnif (or Gozi/ISFB) since my last post on 2018-11-08.
- These emails appear to be sent as replies to emails, possibly from an infected Windows host's email client inbox.
- These Ursnif-infected Windows hosts retrieve follow-up malware.
- I've previously documented Ursnif-infected Windows hosts retrieving IcedID and Nymaim as the follow-up malware.
- Today, my Ursnif-infected Windows host retrieved Dridex as the follow-up malware.
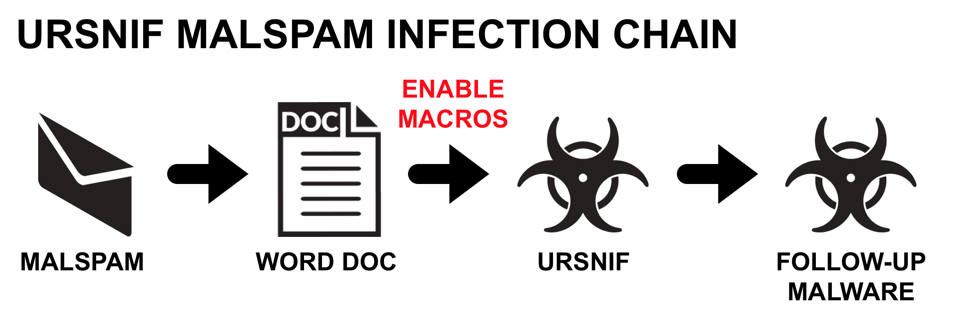
Shown above: Flow chart for recent Ursnif malspam infections I've seen.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URL:
- kyllborena[.]com
- wassedfast[.]com
- lindomodkan[.]com
- ptyptossen[.]com
- pygicketem[.]com
- mezendracr[.]com
- twispaglop[.]com
- hxxp[:]//46.29.161[.]214/uquqwehjsbdqwe.rar
EMAILS

Shown above: Example of Ursnif malspam and attachment from 2018-11-21.
TRAFFIC
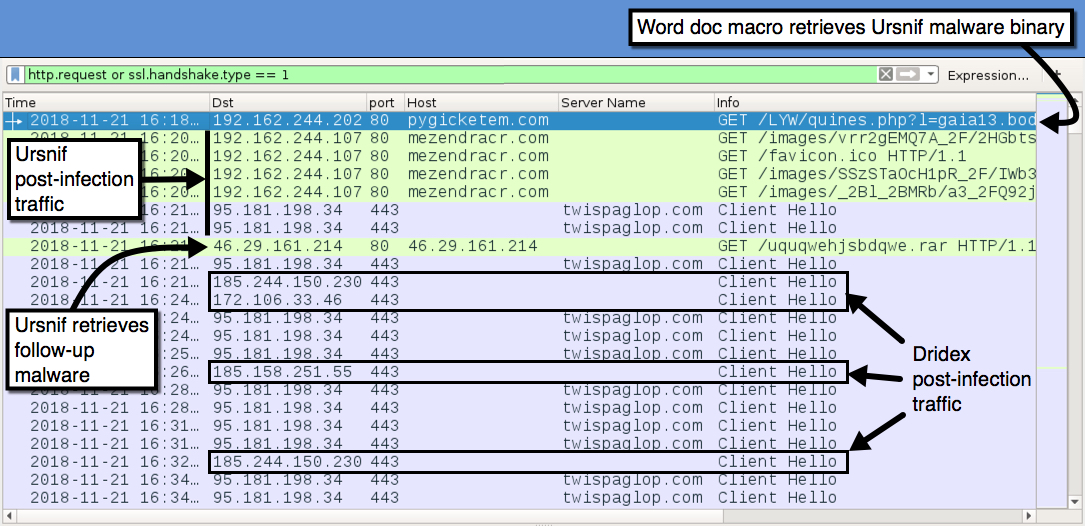
Shown above: Traffic from an infection filtered in Wireshark.
URLS GENRATED BY 7 WORD DOC MACROS FROM 2018-11-19 THRU 2018-11-21:
- hxxp[:]//kyllborena[.]com/LYW/quines.php?l=cion2.bod
- hxxp[:]//kyllborena[.]com/LYW/quines.php?l=cion3.bod
- hxxp[:]//kyllborena[.]com/LYW/quines.php?l=cion5.bod
- hxxp[:]//wassedfast[.]com/LYW/quines.php?l=klyc5.bod
- hxxp[:]//lindomodkan[.]com/VRE/kotner.php?l=sola1.pas
- hxxp[:]//ptyptossen[.]com/LYW/quines.php?l=klyc4.bod
- hxxp[:]//pygicketem[.]com/LYW/quines.php?l=gaia13.bod
TRAFFIC FROM AN INFECTED WINDOWS HOST ON 2018-11-21:
- 192.162.244[.]202 port 80 - pygicketem.com - GET /LYW/quines.php?l=gaia13.bod (Word macro retrieves Ursnif)
- 192.162.244[.]107 port 80 - mezendracr[.]com - GET /images/[long string].avi (generated by Ursnif)
- 95.181.198[.]34 port 443 - twispaglop[.]com - HTTPS/SSL/TLS traffic generated by Ursnif
- 46.29.161[.]214 port 80 - 46.29.161[.]214 - GET /uquqwehjsbdqwe.rar (Ursnif retrieves follow-up malware)
- 172.106.33[.]46 port 443 - SSL/TLS traffic generated by Dridex
- 185.158.251[.]55 port 443 - SSL/TLS traffic generated by Dridex
- 185.244.150[.]230 port 443 - SSL/TLS traffic generated by Dridex
MALWARE
WORD DOC ATTACHMENTS WITH MACRO FOR URSNIF ON MONDAY 2018-11-19:
- 2384a3acec595b54965bd44ab3cc16c93ef9e0770712fd5295589a81a2e1b17a - 103,424 bytes
- 65d31ec58825033c1b2336f9f42dfbf41acfc367fa97fd24d67258e34c98853d - 101,888 bytes
- f518a01bb83a7f8b4b5bb37bff8c1283786aeba8fa8ff6a9ccd72cfc43968423 - 103,936 bytes
WORD DOC ATTACHMENTS WITH MACRO FOR URSNIF ON TUESDAY 2018-11-20:
- 2d9b19648d4b70b77cff827b01ec4ef08259a52ec40646c29f8b3fd357784790 - 93,696 bytes
- 3235acadbced150ed2bb83eeb155d586ae5d91fa4b5f0fddaceedcc44736cef6 - 172,032 bytes
- dba0f54898bf344cbb8fd4f29140b3d615386b51fc140caebe8dc3341c4452bc - 92,672 bytes
MALWARE FROM AN INFECTION GENERATED ON WEDNESDAY 2018-11-21:
- SHA256 hash: 8872cbf20f5e114078edaff5ad612ff569545eda427dc4a799e1b90500177f52
- File size: 77,056 bytes
- File description: Attached Word document with macro for Ursnif from email on 2018-11-21
- SHA256 hash: d413a8997b4bacf978d97635e109e29c7adf56f88ee7f4f57e0f3007e72ca620
- File size: 506,880 bytes
- File location: hxxp[:]//pygicketem[.]com/LYW/quines.php?l=gaia13.bod
- File location: C:\Users\[username]\AppData\Local\Temp\Njm.exe
- File description: Ursnif malware binary seen on 2018-11-21
- SHA256 hash: 636e8d8a24a7d68895cf605d905064160f646cd2a8804c91eed52b473d642b80
- File size: 253,952 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\282627.exe
- File description: Dridex malware binary retrieved by Ursnif-infected Windows host
IMAGES
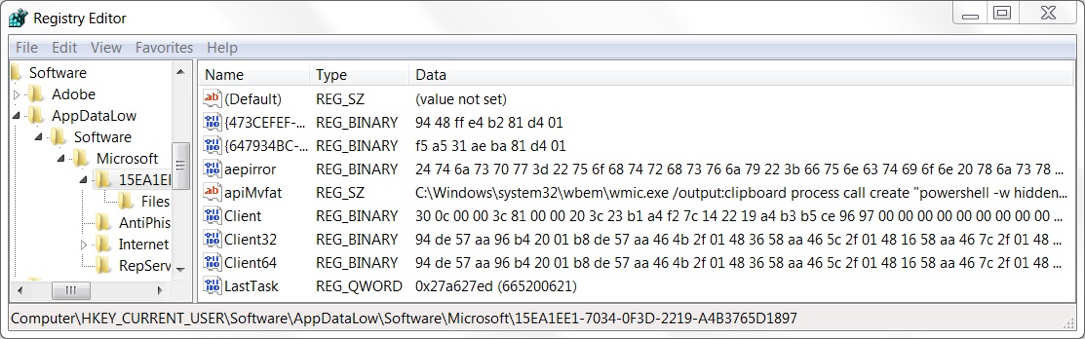
Shown above: Some registry entries on the infected Windows host caused by Ursnif.
Click here to return to the main page.
