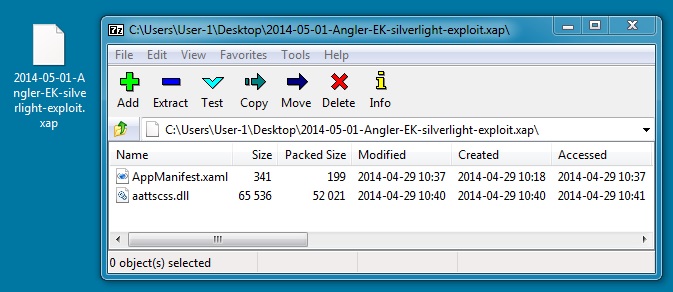
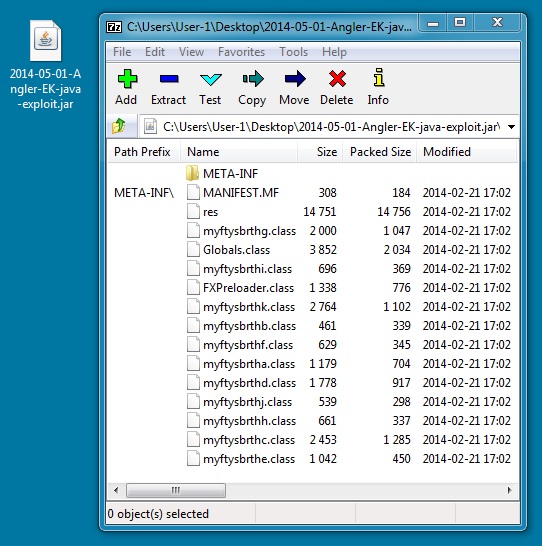
2014-05-01 - ANGLER EK FROM 184.82.69[.]94 - 51M9O.LICITAJYJANYSWED[.]INFO
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PREVIOUS ANGLER EK:
- 2014-02-26 - Angler EK from 23.239.12[.]68 - northerningredients[.]com
- 2014-03-23 - Angler EK from 78.63.247[.]153 - e1xguj.makeuhndall[.]info
- 2014-04-22 - Angler EK from 69.39.239[.]233 - p1315noprat-wezenlijk.tri-citydrywall[.]com
- 2014-04-22 - Angler EK from 23.110.194[.]99 - lampadaryoptimistiselta.particlehero[.]com
- 2014-04-28 - Angler EK from 85.10.220[.]153 - k615o5ij7f.skwosh[.]eu
- 2014-04-29 - Angler EK from 66.96.246[.]151 - ugwpc.bimowamokykpps[.]net
- 2014-05-01 - Angler EK from 184.82.69[.]94 - 51m9o.licitajyjanyswed[.]info
NOTE: Nothing new here that we haven't seen before. Just keeping track...
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 184.82.69[.]94 - 51m9o.licitajyjanyswed[.]info - Angler EK
INFECTION CHAIN OF EVENTS (SILVERLIGHT AND FLASH EXPLOITS)
- 05:11:37 UTC - 51m9o.licitajyjanyswed[.]info - GET /cthhquqwpj
- 05:11:38 UTC - 51m9o.licitajyjanyswed[.]info - GET /Lqg20IjWzP2Enl7FJ8wuoQFRVG15hzZeqYY7K92j4f27LWmWsnGFAwaGXz8sCMLa2bQ78-wykL8= [Flash exploit]
- 05:11:38 UTC - 51m9o.licitajyjanyswed[.]info - GET /AukxodW7jAMQRC1hoTNtpsRMu8UgnHXz1rSjRGhK0O3PwrlbS_oU-ij-anWobP3GBDxb0lY6SJQ= [Silverlight exploit]
- 05:11:41 UTC - 51m9o.licitajyjanyswed[.]info - GET /JuJFE3MY7FrDsOoDzDXQXQFZZwkypij_MtnXYQhTOF64BLxyM6NN1mvl82JII6HIA5fjacs3Oj4= [malware payload]
INFECTION CHAIN OF EVENTS (JAVA EXPLOIT)
- 05:23:11 UTC - 51m9o.licitajyjanyswed[.]info - GET /kedce7b0jl HTTP/1.1
- 05:23:14 UTC - 51m9o.licitajyjanyswed[.]info - HEAD /ieeHfqBIIalCugQb4AIOYv1qBcwPZusNtNomKjt0C4De7zAtZOfeio4qyv6BqTjNNVyB5YySO3w=
- 05:23:14 UTC - 51m9o.licitajyjanyswed[.]info - GET /ieeHfqBIIalCugQb4AIOYv1qBcwPZusNtNomKjt0C4De7zAtZOfeio4qyv6BqTjNNVyB5YySO3w=
- 05:23:30 UTC - 51m9o.licitajyjanyswed[.]info - GET /uOqil8gul9ciSgti0jLsChR7dDRRw_LBMDKOddac9277Bqjpfvzc77dTjW3k2eexe9uQ9RqfVls=
- 05:23:30 UTC - 51m9o.licitajyjanyswed[.]info - GET /uOqil8gul9ciSgti0jLsChR7dDRRw_LBMDKOddac9277Bqjpfvzc77dTjW3k2eexe9uQ9RqfVls= [Java exploit]
- 05:23:30 UTC - 51m9o.licitajyjanyswed[.]info - GET /vDMsODbV7aBqrhDchAYoKlEXnClPQIcgew8R-_RuXS6Zux-RqWDGVo29iKS2IDARPTqG1Da8YLI= [malware payload]
PRELIMINARY MALWARE ANALYSIS
- 2014-05-01-Angler-EK-flash-exploit.swf - 40,424 bytes - MD5: 23c62fff2b9f8499cc560e0a83269394 - Virus Total link
- 2014-05-01-Angler-EK-silverlight-exploit.xap - 52,653 bytes - MD5: cd51e7a9a0487561605e3efec3436f52 - Virus Total link
- 2014-05-01-Angler-EK-java-exploit.jar - 26,840 bytes - MD5: 3de78737b728811af38ea780de5f5ed7 - Virus Total link
- 2014-05-01-Angler-EK-malware-payload.dll - 74,240 bytes - MD5: 2387377699cd0bbe891a1377e4302a28 - Virus Total link
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
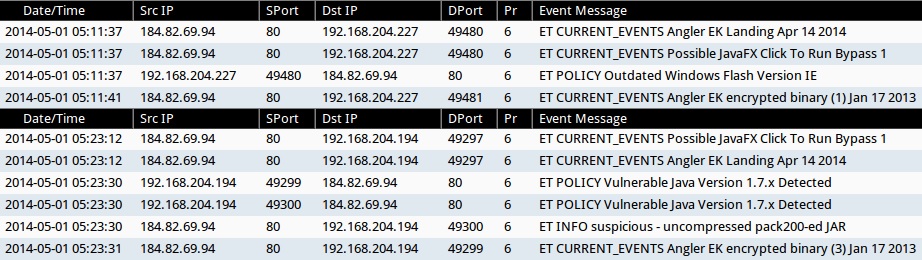
- 2014-05-01 05:11:37 UTC - 184.82.69[.]94:80 - ET CURRENT_EVENTS Angler EK Landing Apr 14 2014
- 2014-05-01 05:11:37 UTC - 184.82.69[.]94:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 1
- 2014-05-01 05:11:37 UTC - 184.82.69[.]94:80 - ET POLICY Outdated Windows Flash Version IE
- 2014-05-01 05:11:41 UTC - 184.82.69[.]94:80 - ET CURRENT_EVENTS Angler EK encrypted binary (1) Jan 17 2013
- 2014-05-01 05:23:12 UTC - 184.82.69[.]94:80 - ET CURRENT_EVENTS Possible JavaFX Click To Run Bypass 1
- 2014-05-01 05:23:12 UTC - 184.82.69[.]94:80 - ET CURRENT_EVENTS Angler EK Landing Apr 14 2014
- 2014-05-01 05:23:30 UTC - 184.82.69[.]94:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-05-01 05:23:30 UTC - 184.82.69[.]94:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-05-01 05:23:30 UTC - 184.82.69[.]94:80 - ET INFO suspicious - uncompressed pack200-ed JAR
- 2014-05-01 05:23:31 UTC - 184.82.69[.]94:80 - ET CURRENT_EVENTS Angler EK encrypted binary (3) Jan 17 2013
OTHER NOTES
The Silverlight exploit used in Angler EK is updated frequently--the modified date for this one is less than 48 hours ago.
The Java exploit used by Angler EK was last updated in February 2014--over 2 months ago.
Click here to return to the main page.