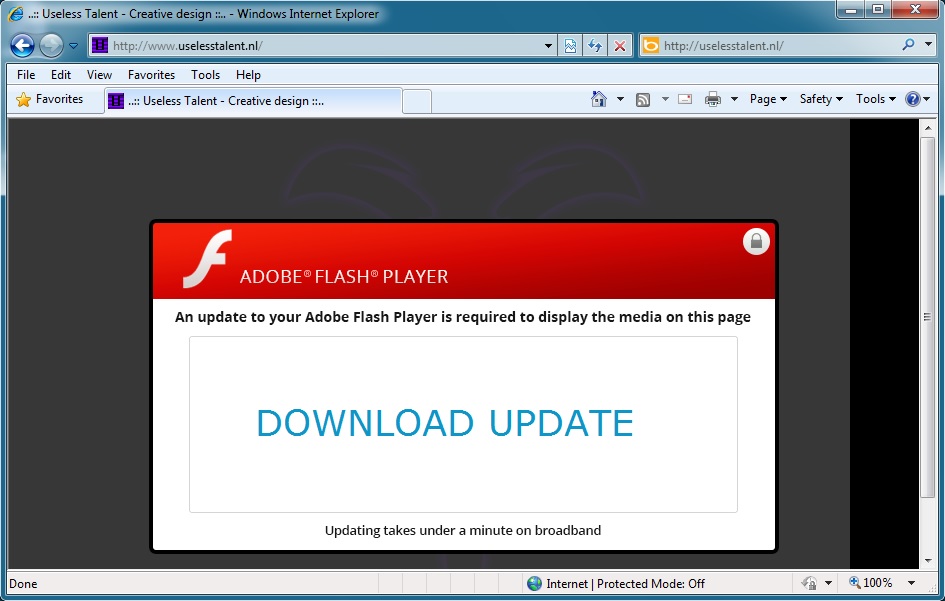
2014-05-11 - TODAY'S FAKE FLASH UPDATER HOSTED ON MICROSOFT ONEDRIVE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
MICROSOFT ONEDIRVE IP ADDRESSES HOSTING THE MALWARE:
- 134.170.107[.]24 - 1lpwjw.bl3301.livefilestore[.]com
- 134.170.107[.]152 - 1lpwjw.blu.livefilestore[.]com
- 134.170.107[.]176 - 1lpwjw.bl3302.livefilestore[.]com
- 134.170.107[.]200 - lpwjw.bl3302.livefilestore[.]com
BLOG ENTRIES SINCE I STARTED KEEPING TRACK:
- 2014-04-24 - fake Flash update from 217.26.210[.]127 (www.wizardcomputers[.]rs) points to malware on Microsoft OneDrive
- 2014-04-28 - fake Flash updater hosted on Microsoft OneDrive IP addresses
- 2014-04-29 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-03 - Another fake Flash updater hosted on Microsoft OneDrive
- 2014-05-11 - Today's fake Flash updater hosted on Microsoft OneDrive
NOTES:
- These compromised websites are listed on scumware.org as Troj/JSRedir-NZ and similarly-named JSRedir threats.
- Read: compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
- go3studio[.]us --> www.gsflaw[.]de --> 1lpwjw.blu.livefilestore[.]com
- www.uselesstalent[.]nl --> 27.50.96[.]160 --> lpwjw.bl3302.livefilestore[.]com
- www.paleochora-rooms[.]gr --> www.genera-group[.]com --> 1lpwjw.bl3301.livefilestore[.]com
- szig-gep[.]gr --> www.genera-group[.]com --> 1lpwjw.bl3302.livefilestore[.]com
TODAY'S EXAMPLES
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
go3studio[.]us --> www.gsflaw[.]de --> 1lpwjw.blu.livefilestore[.]com
- 07:49:43 UTC - 184.106.55[.]68:80 - go3studio[.]us - GET /emrged/js/responsiveTabs.js
- 07:49:54 UTC - 195.170.99[.]24:80 - www.gsflaw[.]de - GET /mdrpzg7d.php?id=88033100
- 07:49:54 UTC - 195.170.99[.]24:80 - www.gsflaw[.]de - GET /mdrpzg7d.php?html=27
- 07:49:55 UTC - 195.170.99[.]24:80 - www.gsflaw[.]de - GET /checker.php [repeats several times]
- 07:50:05 UTC - 134.170.107[.]152:443 - 1lpwjw.blu.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- https://1lpwjw.blu.livefilestore[.]com/y2msHSTiyCQTXV4BANWGbkTLZvINhNsOWkQTDPb8uy-qx1BM_SBMqaoRhSa7MO0pXKQxpQV5CAVoXw9C_whj93HizauPyaIDheVkK
b7Za_EgI8/FlashUpdater86829.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
www.uselesstalent[.]nl --> 27.50.96[.]160 --> lpwjw.bl3302.livefilestore[.]com
- 08:04:59 UTC - 46.30.212[.]189:80 - www.uselesstalent[.]nl - GET /
- 08:04:59 UTC - 27.50.96[.]160:80 - 27.50.96[.]160 - GET /ndqzdn2c.php?id=23486292
- 08:05:00 UTC - 27.50.96[.]160:80 - 27.50.96[.]160 - GET /ndqzdn2c.php?html=27
- 08:05:03 UTC - 27.50.96[.]160:80 - 27.50.96[.]160 - GET /checker.php [repeats several times]
- 08:06:39 UTC - 134.170.107[.]200:443 - lpwjw.bl3302.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- https://1lpwjw.bl3302.livefilestore[.]com/y2mQyNjBa42Ve5OLKvvp93S0csnEwn7bSq-I6MQWeBDwBecKNXco7O7Ni92wLDLyTxWE-ClIFAAs_XLgfjuGcESIg8aAdcdukmTaf6F6
dzwxiU/FlashUpdater83177.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
www.paleochora-rooms[.]gr --> www.genera-group[.]com --> 1lpwjw.bl3301.livefilestore[.]com
- 08:25:57 UTC - 192.154.143[.]222:80 - www.paleochora-rooms[.]gr - GET /stie.js
- 08:26:08 UTC - 195.191.24[.]153:80 - www.genera-group[.]com - GET /SharedImages/cdp2mBwR.php?id=11751342
- 08:26:09 UTC - 195.191.24[.]153:80 - www.genera-group[.]com - GET /SharedImages/cdp2mBwR.php?html=27
- 08:26:11 UTC - 195.191.24[.]153:80 - www.genera-group[.]com - GET /SharedImages/checker.php [repeats several times]
- 08:26:19 UTC - 134.170.107[.]24:443 - 1lpwjw.bl3301.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- https://1lpwjw.bl3301.livefilestore[.]com/y2mIDqPKHs63QU5o-j7KbxBGmK4VyPeiial8pB397GkBVcPc8cpiAmE8buAQe98mZHs2fV3S6hq_secJ96r1IUoIBxu8HWfgTZRWnE_P
p8wy4g/FlashUpdater11121.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
szig-gep[.]hu --> www.genera-group[.]com --> 1lpwjw.bl3302.livefilestore[.]com
- 08:37:27 UTC - 195.228.242[.]66:80 - szig-gep[.]hu GET /iwebalbumfiles2/gb_scripts.js
- 08:37:35 UTC - 194.126.172[.]212:80 - zsazsasu[.]nl GET /zgtbjqpv.php?id=50919352
- 08:37:37 UTC - 194.126.172[.]212:80 - zsazsasu[.]nl GET /zgtbjqpv.php?html=27
- 08:37:38 UTC - 194.126.172[.]212:80 - zsazsasu[.]nl GET /checker.php [repeats several times]
- 08:37:45 UTC - 134.170.107[.]176:443 - 1lpwjw.bl3302.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- https://1lpwjw.bl3302.livefilestore[.]com/y2mKCQSI_9uo4eyas4sv8DVatiCRuaCrj2ERNpG0V7JFNYRKxx5Lg4MG2OqXFALzoguYp4FGBDNe8Ga_DRUyMHuARME2iPC9Y2lv
VW9ubLv_aQ/FlashUpdater96312.exe
PRELIMINARY MALWARE ANALYSIS
File name: FlashUpdater86829.exe
File size: 260952 bytes
MD5 hash: 88e6335017cbc0a14a7304276971437d
Detection ratio: 7 / 52
First submission: 2014-05-11 01:50:28 UTC
VirusTotal link: https://www.virustotal.com/en/file/d73ff7e72b556daf17549bb1672229ea2c5ad0a3b3d5fb53d89b8f01cb07f6de/analysis/
TRAFFIC FROM MALWR SANDBOX ANALYSIS PCAP
- 193.105.210[.]32 - domaintomakeit[.]com - POST /unecheitd/8732593/index.php
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/inexsabit.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/aveksynkens.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/tobnenuko.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/nukotobne.exe
- 79.165.229[.]42 - zemmes-gimbl[.]com - GET /b/shoe/54607 [repeats several times]
- 176.97.106[.]27 - chanse-leaf[.]com - GET /components-jumla-bq/jquery/ [repeats several times]
- 79.142.66[.]240 - report.9317skuo9oc79uocei1[.]com - GET /?31793g731=%96%CB%A8[long string of characters, repeats with different strings]
- 5.149.248[.]153 - report.9317skuo9oc79uocei1[.]com - POST /
- 5.149.248[.]153 - update1.n4pskrij[.]com - GET /?rp=kduoxsWryWSSn2bS1M[long string of characters]
ALERTS
EXAMPLE OF ALERTS FOR THE INITIAL TRAFFIC (from Sguil on Security Onion)

- ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive(1) (sid:2014919)
- ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive(2) (sid:2014920)
ALERTS
ALERTS FROM THE SANDBOX ANALYSIS PCAP
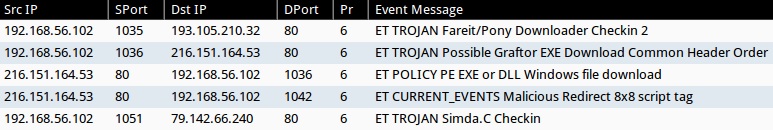
- ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- ET TROJAN Possible Graftor EXE Download Common Header Order (sid:2018254)
- ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- ET TROJAN Simda.C Checkin (sid:2016300)
NOTE: Had some issues playing back the pcap using tcpreplay in Security Onion. 69 out of 1144 packets failed, so I'm not sure if the list of events above is complete.
Click here to return to the main page.