2017-10-06 - POWERSHELL-BASED MALWARE INFECTION FROM BRAZIL MALSPAM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-10-06-infection-traffic.pcap.zip 3.2 MB (3,210,713 bytes)
- 2017-10-06-infection-traffic.pcap (4,339,019 bytes)
- 2017-10-06-Brazil-malspam-2-examples.zip 93.5 kB (93,471 bytes)
- 2017-10-04-Brazil-malspam-2315-UTC.eml (66,994 bytes)
- 2017-10-06-Brazil-malspam-0609-UTC.eml (68,505 bytes)
- 2017-10-06-files-from-an-infection.zip 5.1 MB (5,134,500 bytes)
- 1508201700016067882247230289631.pdf (49,198 bytes)
- 250920170000006734569912369086500998.pdf (48,063 bytes)
- 2609201700084745873458920923497456823489234792.vbs.txt (25,728 bytes)
- HKCU-Software-SYSPROUSTPC-SYS-base64string.txt (5,120 bytes)
- HKCU-Software-SYSPROUSTPC-SYS-decoded-text.txt (3,736 bytes)
- HKCU-Software-SYSPROUSTPC56-SYPROUSTPC56-decoded-text.txt (2,973 bytes)
- HKCU-Software-SYSPROUSTPC56-SYPROUSTPC56-value.txt (4,218 bytes)
- Ionic.Zip.Reduced.dll (253,440 bytes)
- PROUST-PC.aes (16 bytes)
- PROUST-PC.zip (3,291,290 bytes)
- PROUST-PCx.ocx (376 bytes)
- SYSPROUSTPC56-scheduled-task.txt (3,374 bytes)
- SYSPROUSTPC56.exe (452,608 bytes)
- c.cer (905 bytes)
- crov.exe (1,690,096 bytes)
- dll.dll.exe (396,480 bytes)
- endqw03j.fpq.vbs.txt (114 bytes)
- mmaqzsfa.pej.vbs.txt (130 bytes)
- ps.exe (452,608 bytes)
NOTES:
- I have similar posts for this activity on 2017-08-28, 2017-09-22 and several previous to that.
- As usual, the PDF attachment has a different link than the email, but they both redirect to the same URL to downloaded a VBS file.
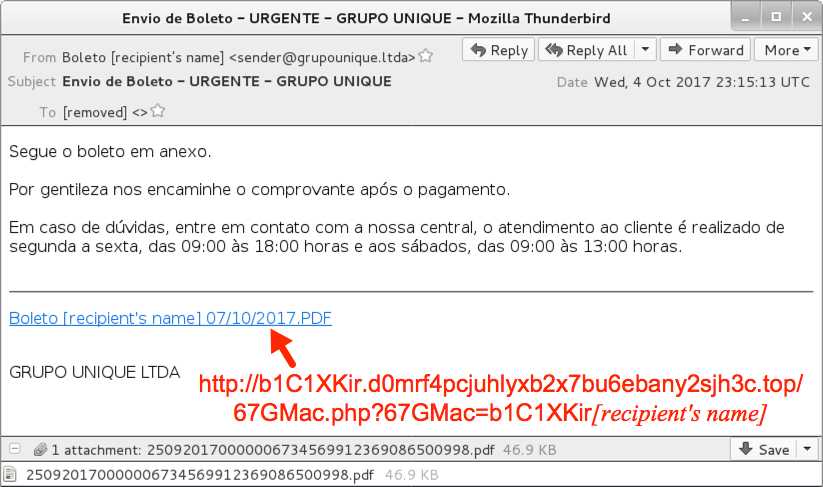
Shown above: Screenshot of an email (1 of 2).
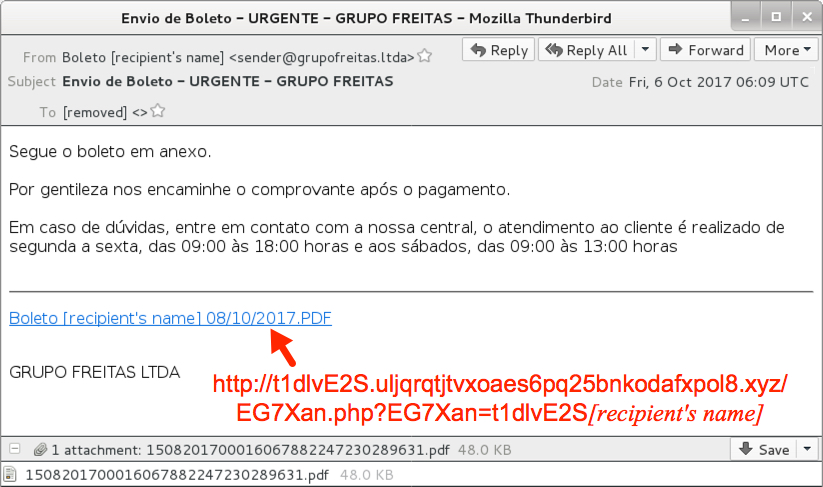
Shown above: Screenshot of an email (2 of 2).
EMAIL HEADERS:
- Date: Wednesday, 2017-10-04 23:15 UTC
- Sending mail server: grupounique[.]ltda
- From: Boleto [recipient's name] <sender@grupounique[.]ltda>
- Subject: Envio de Boleto - URGENTE - GRUPO UNIQUE
- Attachment name: 250920170000006734569912369086500998.pdf
- Link from the message: b1C1XKir.d0mrf4pcjuhlyxb2x7bu6ebany2sjh3c[.]top/67GMac.php?67GMac=b1C1XKir[recipient's name]
- Date: Friday, 2017-10-06 06:09 UTC
- Sending mail server: grupofreitas[.]ltda
- From: Boleto [recipient's name] <sender@grupofreitas[.]ltda>
- Subject: Envio de Boleto - URGENTE - GRUPO FREITAS
- Attachment name: 1508201700016067882247230289631.pdf
- Link from the message: t1dlvE2S.uljqrqtjtvxoaes6pq25bnkodafxpol8[.]xyz/EG7Xan.php?EG7Xan=t1dlvE2S[recipient's name]
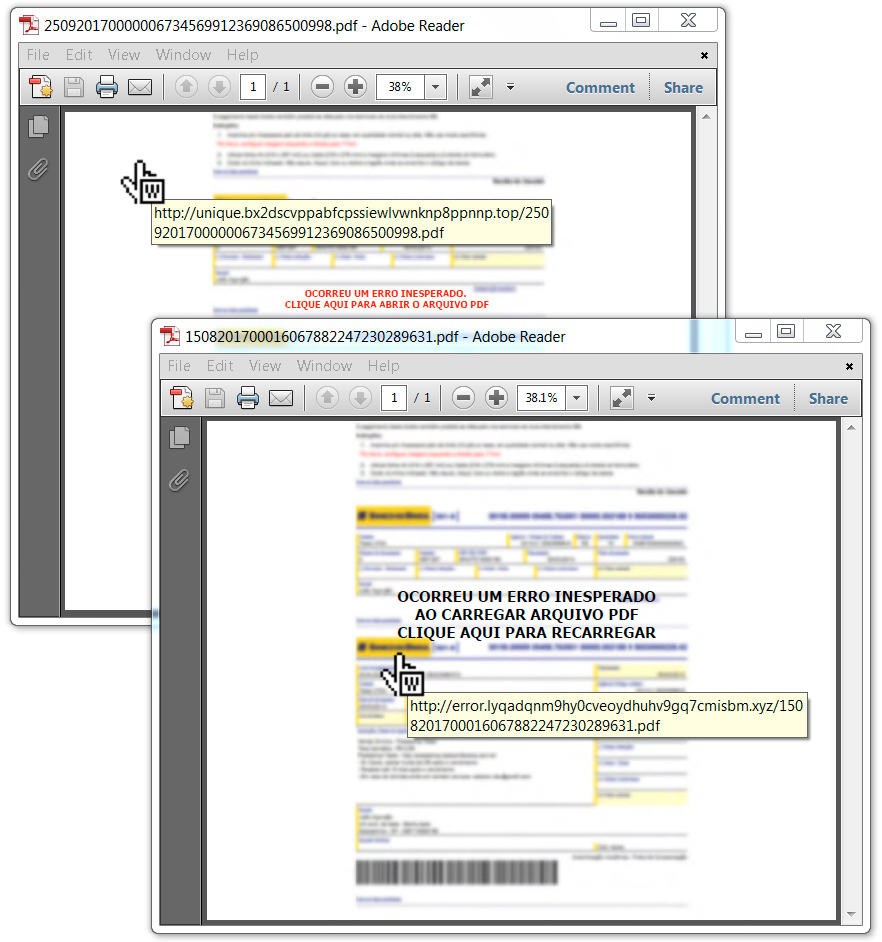
Shown above: Link seen from one of the PDF attachments.
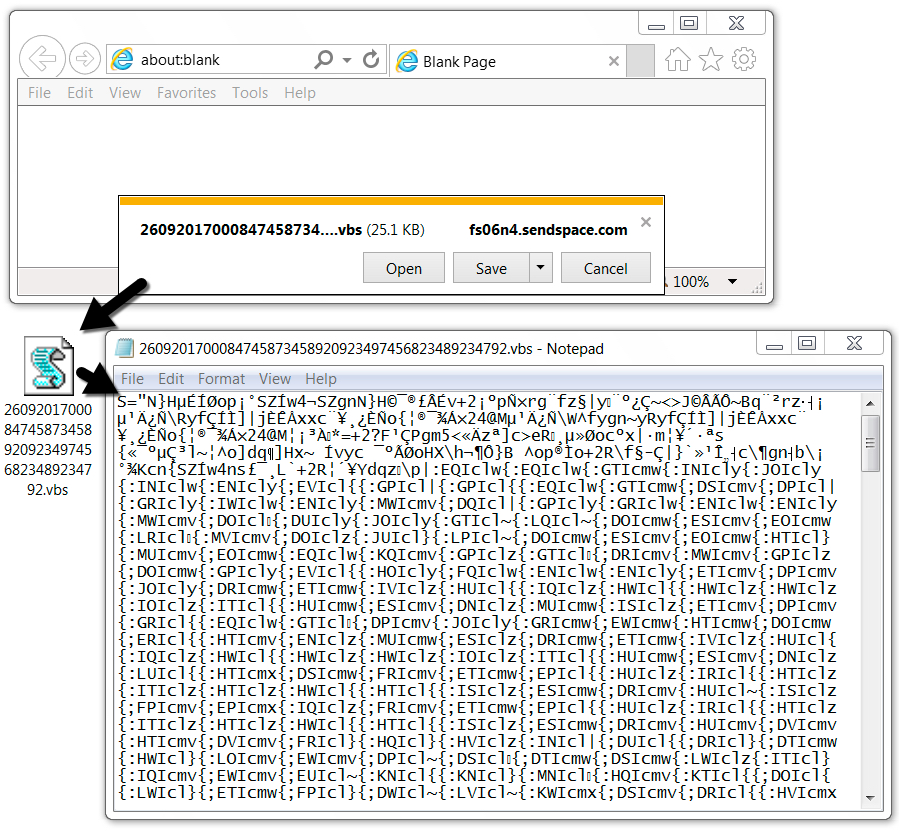
Shown above: Whether email link or PDF link, you end up with the same file from sendspace.com.
TRAFFIC
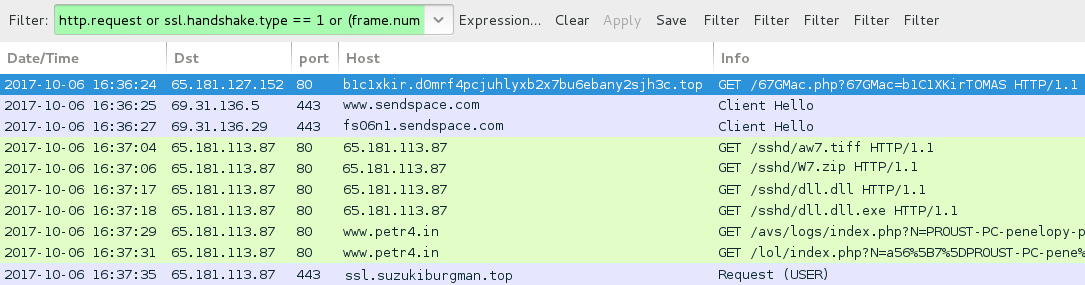
Shown above: Traffic from an infection filtered in Wireshark.
TRAFFIC AN INFECTION:
- 65.181.127[.]152 port 80 - b1c1xkir.d0mrf4pcjuhlyxb2x7bu6ebany2sjh3c[.]top - GET /67GMac.php?67GMac=b1C1XKir[recipient's name]
- port 443 (HTTPS) www.sendspace[.]com - GET /pro/dl/fp5yb0
- port 443 (HTTPS) fs06n1.sendspace[.]com - GET /dlpro/[long string]/2609201700084745873458920923497456823489234792.vbs
- 65.181.113[.]87 port 80 - 65.181.113[.]87 - GET /sshd/aw7.tiff
- 65.181.113[.]87 port 80 - 65.181.113[.]87 - GET /sshd/W7.zip
- 65.181.113[.]87 port 80 - 65.181.113[.]87 - GET /sshd/dll.dll
- 65.181.113[.]87 port 80 - 65.181.113[.]87 - GET /sshd/dll.dll.exe
- 65.181.113[.]87 port 80 - www.petr4[.]in - GET /avs/logs/index.php?N=[hostname]-[username]%20=%20%20%20%20FORCE%20OK
- 65.181.113[.]87 port 80 - www.petr4.in - GET /lol/index.php?N=a56%5B7%5D[hostname]-[first part of username]%5B[5-digit number]%5D&gb=
- DNS query for imestre.suzukiburgman[.]top - resolved to 127.0.0.1
- 65.181.113[.]87 port 443 - ssl.suzukiburgman[.]top - unencrypted IRC traffic
FILE HASHES
PDF ATTACHMENT (1 OF 2):
- SHA256 hash: bd194a81bfed3d57744183dd700e9e4a68f7b05b0f4c94a4eacac5ef6f9c3e49
File size: 49,198 bytes
File name: 1508201700016067882247230289631.pdf
PDF ATTACHMENT (2 OF 2):
- SHA256 hash: 3b9944bbb3d1e088c03882d2d5cde19bcd2ac4059aa5d002d9165674a1617fea
File size: 48,063 bytes
File name: 250920170000006734569912369086500998.pdf
DOWNLOADED VBS FILE:
- SHA256 hash: d5f6ff744fa49c6fcc180fdb47e04abd8d757e0505dd3b38920513683b090f5d
File size: 25,728 bytes
File name: 2609201700084745873458920923497456823489234792.vbs
FILES FROM AN INFECTION
FILES FROM THE INFECTED WINDOWS HOST:
- NOTE: Many of these files are not inherently malicious. For example, ps.exe is a legitimate executable for Powershell. However, they are being used in a malicious manner.
- C:\Users\[username]\AppData\Local\Temp\Java\dll.dll.exe
- C:\Users\[username]\AppData\Local\Temp\Java\endqw03j.fpq.vbs
- C:\Users\[username]\AppData\Local\Temp\Java\Ionic.Zip.Reduced.dll
- C:\Users\[username]\AppData\Local\Temp\Java\[hostname].aes
- C:\Users\[username]\AppData\Local\Temp\Java\[hostname].zip
- C:\Users\[username]\AppData\Local\Temp\ps.exe
- C:\Windows\System32\c.cer
- C:\Windows\System32\crov.exe
- C:\Windows\System32\mmaqzsfa.pej.vbs
- C:\Windows\System32\[hostname]x.ocx
- C:\Windows\System32\Java\Ionic.Zip.Reduced.dll
- C:\Windows\System32\Java\[hostname].aes
- C:\Windows\System32\Java\[hostname].zip
- C:\Windows\system32\SYS[hostname]56.exe
- C:\Windows\System32\Tasks\SYS[hostname]56
REGISTRY UPDATES ON THE INFECTED WINDOWS HOST:
- HKCU\Software\SYS[hostname]\SYS[hostname]
- HKCU\Software\SYS[hostname]56\SYS[hostname]56
- HKCU\System\SYS[hostname]56\SYS[hostname]56\cache
- HKCU\System\SYS[hostname]56\SYS[hostname]56\control
- HKCU\System\SYS[hostname]56\SYS[hostname]56\SYS[hostname]56
IMAGES
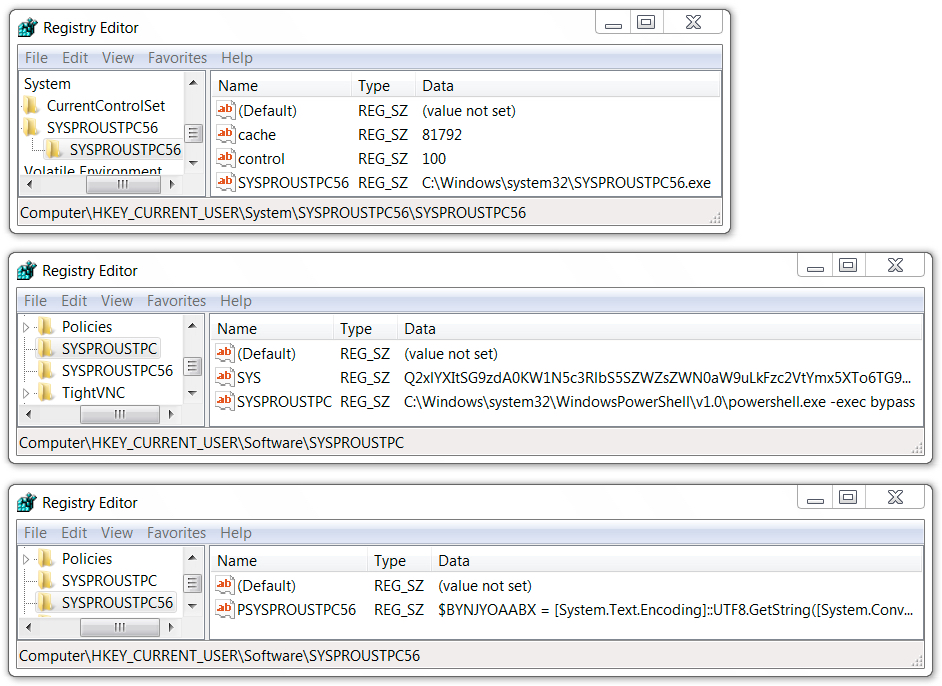
Shown above: Windows Registry updates on an infected host.
Click here to return to the main page.
