2018-01-02 - INFECTION FROM WHATSAPP-THEMED MALSPAM TAGETING BRAZIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2018-01-02-infection-traffic.pcap.zip 14.4 MB (14,366,849 bytes)
- 2018-01-02-infection-traffic.pcap (15,560,361 bytes)
- Zip archive of the email: 2018-01-02-WhatsApp-themed-malspam-1443-UTC.eml.zip 1.5 kB (1,516 bytes)
- 2018-01-02-WhatsApp-themed-malspam-1443-UTC.eml (3,581 bytes)
- 2018-01-02-malware-and-artifacts.zip 24.7 MB (24,741,226 bytes)
- 124412.dat (6,499,839 bytes)
- 125412.dat (5,440,967 bytes)
- DISNEY0201.exe (201,679,672 bytes)
- DISNEY020118.exe (202,065,232 bytes)
- usernameHOSTNAME-PC0.txt (3,364 bytes)
- usernameHOSTNAME-PC1.txt (3,360 bytes)
- vIDEO.Nat.25.12.2017.exe (3,490,816 bytes)
NOTES:
- I documented similar malspam last year on 2017-10-03 and 2017-10-11.
- The end results appears to be the same type of Banload-style information stealer/banking malware we've seen before from this type of malspam.
- The only alerts of note on the network traffic were alerts for a Lets Encrypt SSL certificate used by whatsapp.visualizar[.]cf, a server established to help distribute the malware.
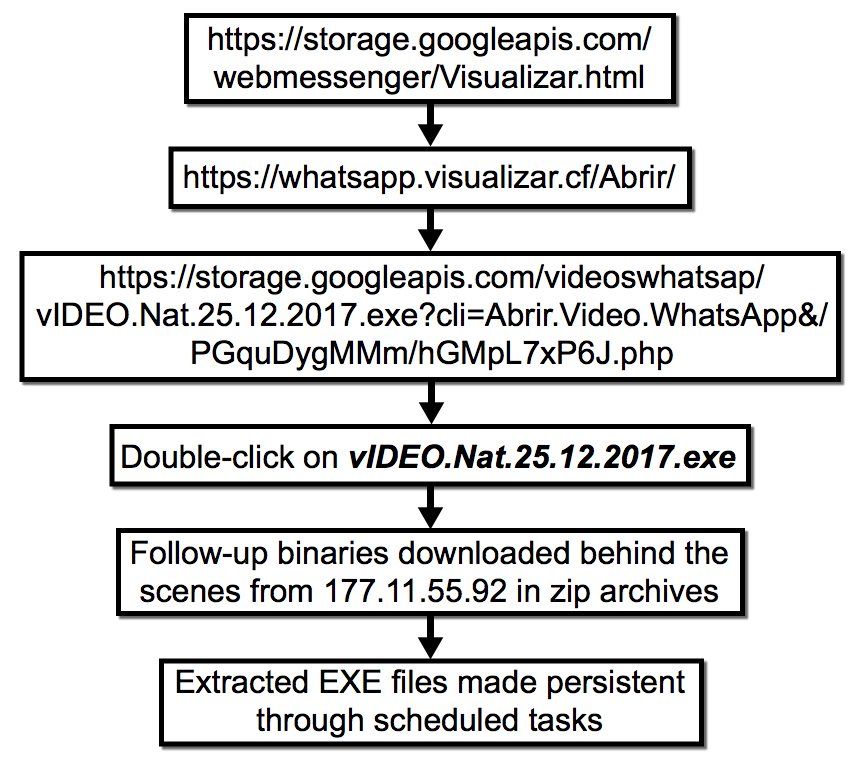
Shown above: Flowchart for today's infection.
WEB TRAFFIC BLOCK LIST
Indicators are not a block list. If you feel the need to block web traffic, I suggest the following domains and URLs:
- hxxps[:]//storage.googleapis[.]com/webmessenger/Visualizar.html
- whatsapp.visualizar[.]cf
- hxxps[:]//storage.googleapis[.]com/videoswhatsap/vIDEO.Nat.25.12.2017.exe
- hxxp[:]//177.11.55[.]92/upload.php?id=PRO
- hxxp[:]//177.11.55[.]92/upload.php?id=LXO
- hxxp[:]//177.11.55[.]92/index1.php
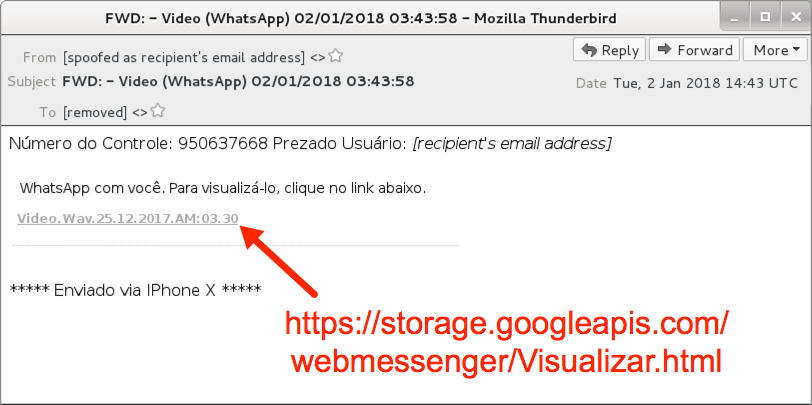
Shown above: Screenshot of the email.
HEADER INFORMATION:
- Date: Tuesday, 2018-01-01 at 14:44 UTC
- Received: from fh5 ([89.40.119[.]45])
- Message-ID: <20180102144358.30DB91F88F@fh5>
- From: [spoofed as recipient's email address]
- Subject: FWD: - Video (WhatsApp) 02/01/2018 03:43:58
- Link in the email: hxxps[:]//storage.googleapis[.]com/webmessenger/Visualizar.html
MESSAGE TEXT:
Número do Controle: 950637668 Prezado Usuário: [recipient's email address]
WhatsApp com você. Para visualizá-lo, clique no link abaixo.
Video.Wav.25.12.2017.AM:03.30
***** Enviado via IPhone X *****
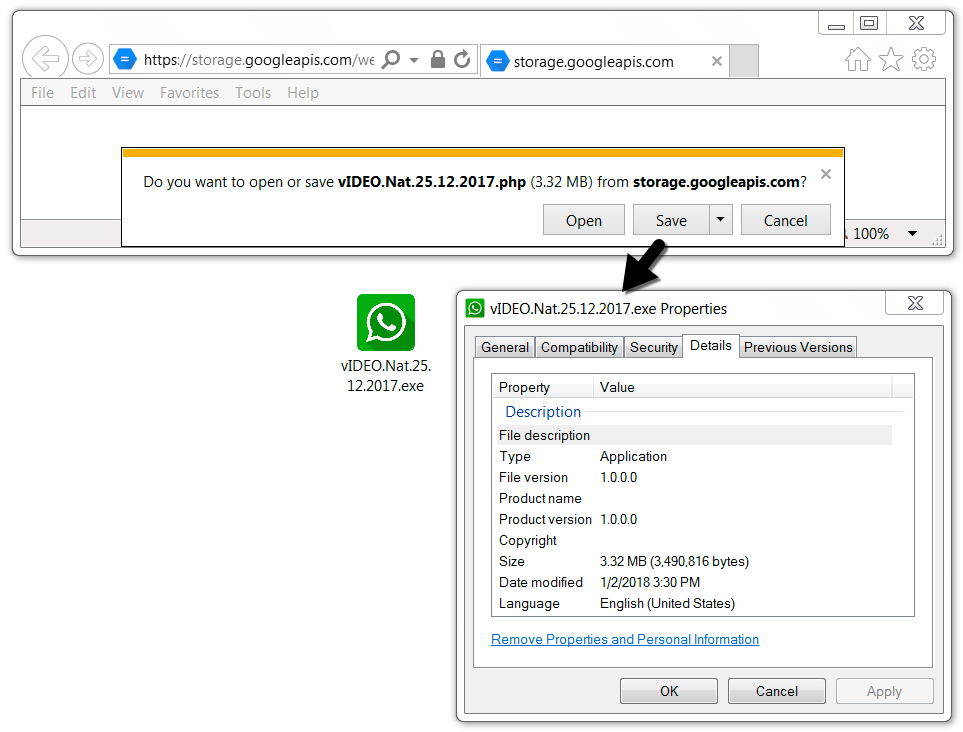
Shown above: Downloading malware from link in the email.
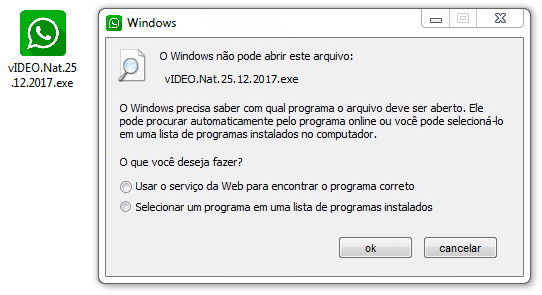
Shown above: Saw this pop-up message, but the malware still infected my lab host..
TRAFFIC
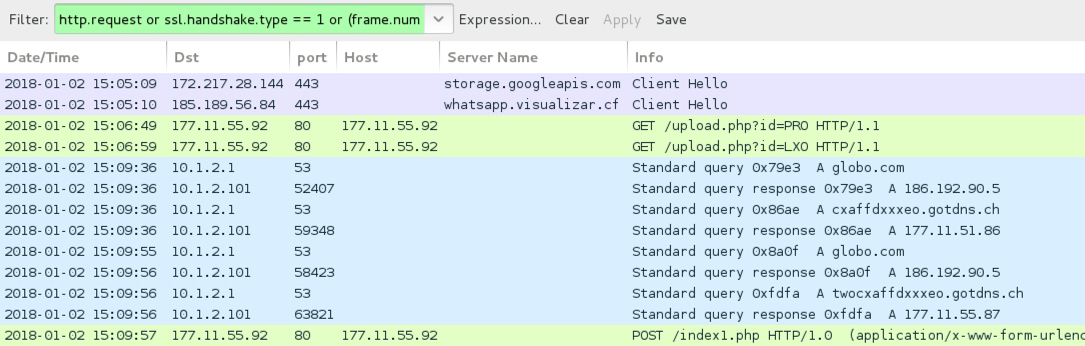
Shown above: HTTP traffic from the infection filtered in Wireshark.
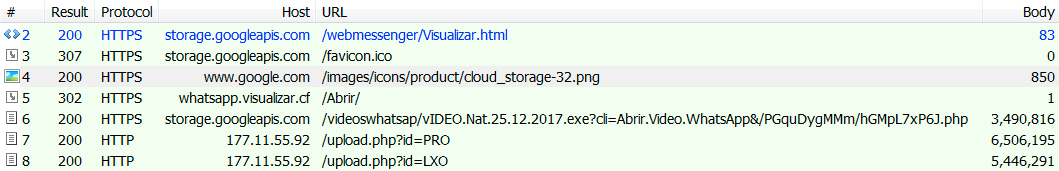
Shown above: HTTPS URLs noted in Fiddler web debugger.
ASSOCIATED DOMAINS:
- port 443 (HTTPS) - storage.googleapis[.]com - GET /webmessenger/Visualizar.html
- 185.189.56[.]84 port 443 (HTTPS) - whatsapp.visualizar[.]cf - GET /Abrir/
- port 443 (HTTPS) - storage.googleapis[.]com - GET /videoswhatsap/vIDEO.Nat.25.12.2017.exe&[string of characters]
- 177.11.55[.]92 port 80 - 177.11.55[.]92 - GET /upload.php?id=PRO
- 177.11.55[.]92 port 80 - 177.11.55[.]92 - GET /upload.php?id=LXO
- 177.11.55[.]92 port 80 - 177.11.55[.]92 - POST /index1.php
- DNS queries for globo[.]com (a legitimate site), cxaffdxxxeo.gotdns[.]ch, and twocxaffdxxxeo.gotdns[.]ch - but no associated TCP traffic.
MALWARE
MALWARE DOWNLOADED FROM LINK IN EMAIL:
- SHA256 hash: 3e7fe55b467948c0e4f788581e2bd2008619f53cf1cb2a3c6dcd156042d553ec
File size: 3,490,816 bytes
File name: vIDEO.Nat.25.12.2017.exe
FOLLOW-UP ZIP ARCHIVE (1 OF 2):
- SHA256 hash: 116872ae52c6f59aee0d5114445c3c3db2153db0ccb3c6869d8983ecc766a4cd
File size: 6,499,839 bytes
File name: 124412.dat
File location: hxxp[:]//177.11.55[.]92/upload.php?id=PRO
EXTRACTED EXECUTABLE (1 OF 2):
- SHA256 hash: a44c6a4233201818c8b86303e06d70141e526dfa47ef5cb0dcb42c98d7078948
File size: 201,679,672 bytes
File name: kqabnrgr.dat
File location: C:\Users\[username]\AppData\Local\A9313E2A1BB5D422EA99\DISNEY0201.exe
FOLLOW-UP ZIP ARCHIVE (2 OF 2):
- SHA256 hash: b69421193dc529eb50a76549c81ab34ecc12cbbdb0aa2376681cdd8cbc95bc4b
File size: 5,440,967 bytes
File name: 125412.dat
File location: hxxp[:]//177.11.55[.]92/upload.php?id=LXO
EXTRACTED EXECUTABLE (2 OF 2):
- SHA256 hash: 7c7d58eb470fa4a6dd697bfeb802b0a48c0e0f670ea2c015e589263af3f52353
File size: 202,065,232 bytes
File name: ptdwplcp.dat
File location: C:\Users\[username]\AppData\Local\B9313E2A1BB5D422EA98\DISNEY020118.exe
IMAGES
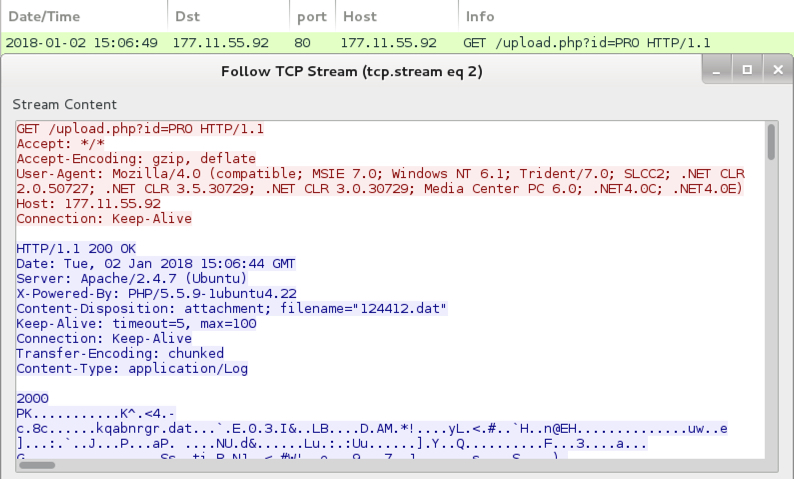
Shown above: Follow-up download for a zip archive with malware for the infection.
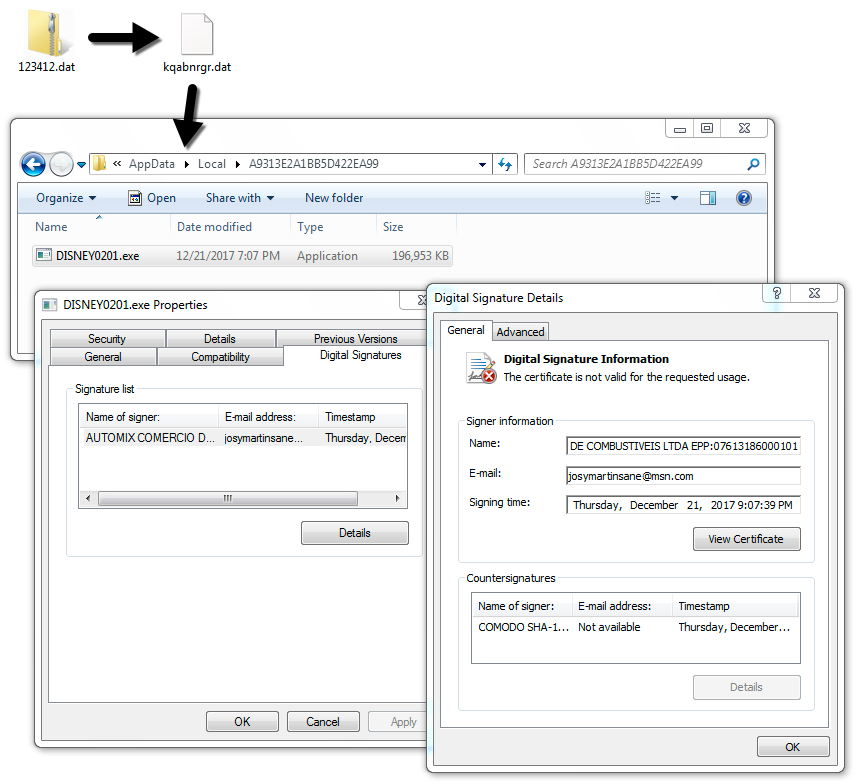
Shown above: Contents of the zip archive and where it was dropped for persistence.
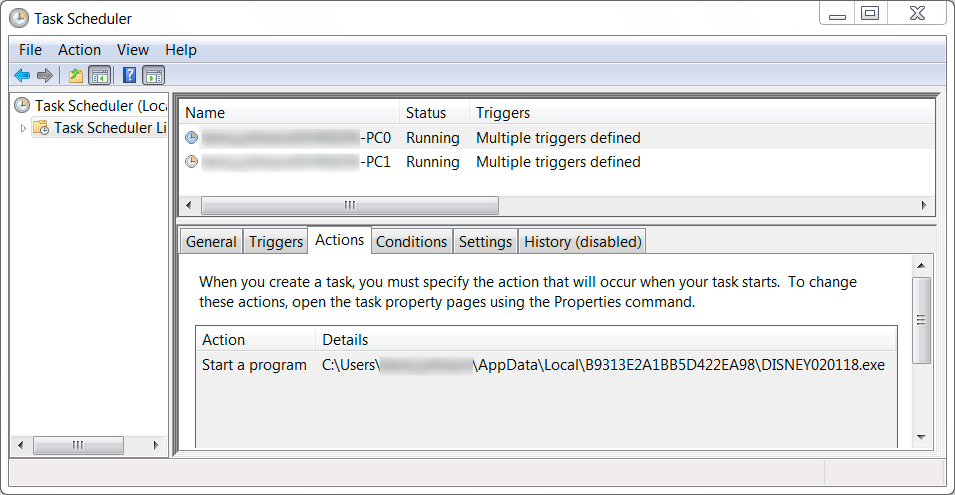
Shown above: Two zip archives were retrieved by the initial installer, and the extracted EXE files were made persistent through scheduled tasks.
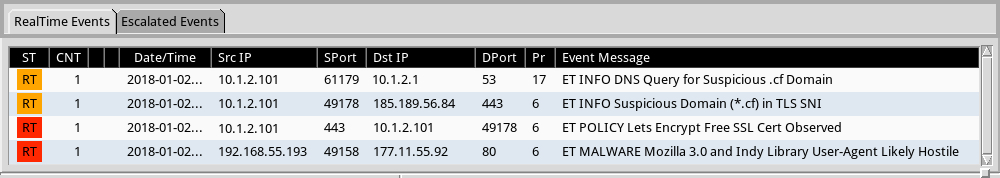
Shown above: Alerts from Sguil in Security Onion using Suricata and the EmergingThreats Pro (ETPRO) ruleset.
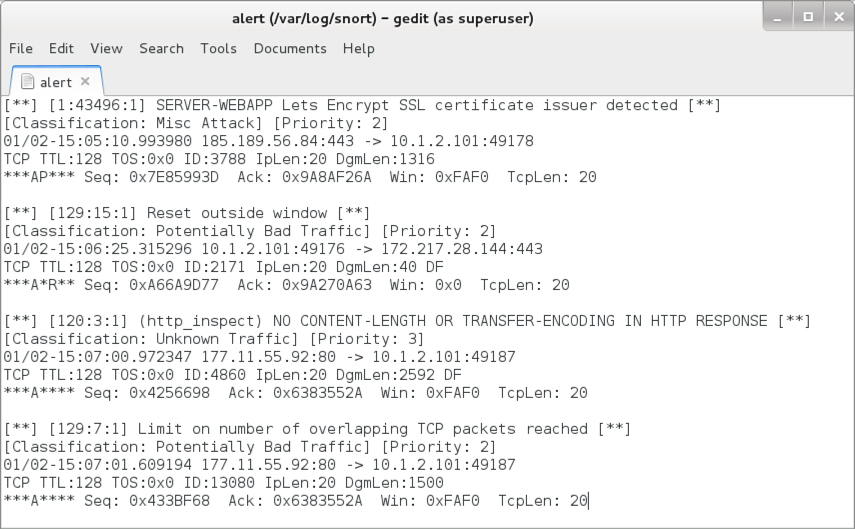
Shown above: Some alerts on the infection traffic from the Snort subscriber ruleset when reading the pcap with Snort 2.9.11.
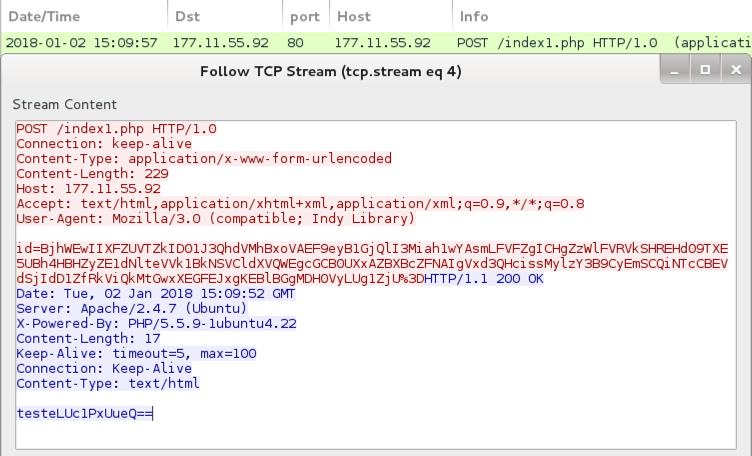
Shown above: Post-infection callback from the infected Windows host.
Click here to return to the main page.