2014-05-14 - TODAY'S FAKE FLASH UPDATER HOSTED ON MICROSOFT ONEDRIVE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
MICROSOFT ONEDIRVE IP ADDRESSES SEEN HOSTING TODAY'S MALWARE:
- 134.170.108[.]48 - rvok3w.bay.livefilestore[.]com
- 134.170.108[.]72 - rvok3w.bay.livefilestore[.]com
- 134.170.108[.]96 - rvok3w.by3301.livefilestore[.]com
- 134.170.108[.]96 - rvok3w.bay.livefilestore[.]com
- 134.170.108[.]152 - rvok3w.bay.livefilestore[.]com
- 134.170.108[.]176 - rvok3w.bay.livefilestore[.]com
- 134.170.108[.]200 - rvok3w.bay.livefilestore[.]com
BLOG ENTRIES SINCE I STARTED KEEPING TRACK:
- 2014-04-24 - fake Flash update from 217.26.210[.]127 (www.wizardcomputers[.]rs) points to malware on Microsoft OneDrive
- 2014-04-28 - fake Flash updater hosted on Microsoft OneDrive IP addresses
- 2014-04-29 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-03 - Another fake Flash updater hosted on Microsoft OneDrive
- 2014-05-11 - Today's fake Flash updater hosted on Microsoft OneDrive
- 2014-05-14 - Today's fake Flash updater hosted on Microsoft OneDrive
TODAY'S TRAFFIC EXAMPLES
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
www.allmemories[.]com[.]ar --> estudiobonzo[.]com[.]ar --> rvok3w.by3301.livefilestore[.]com
- 2014-05-14 00:15:43 UTC - 200.85.152[.]210:80 - www.allmemories[.]com[.]ar - GET /
- 2014-05-14 00:15:43 UTC - 190.228.29[.]85:80 - estudiobonzo[.]com[.]ar - GET /7wqb8bjy.php?id=82839947
- 2014-05-14 00:15:45 UTC - 190.228.29[.]85:80 - estudiobonzo[.]com[.]ar - GET /7wqb8bjy.php?html=27
- 2014-05-14 00:15:47 UTC - 190.228.29[.]85:80 - estudiobonzo[.]com[.]ar - GET /checker.php [repeats]
- 2014-05-14 00:15:49 UTC - 134.170.108[.]96:443 - rvok3w.by3301.livefilestore[.]com
- 2014-05-14 00:15:49 UTC - 134.170.108[.]96:443 - rvok3w.by3301.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- rvok3w.by3301.livefilestore[.]com/y2mMqVqQ29fGJrrbxutpf-LvYqUWjdlAIMlT3LaZT5GYXsDR5eUEqMVeU-gHrrPM_zXDdwJIG9vndvUhzhLm8sSrzgyIfedSUU6KYBsO-GmxPI/
FlashUpdater56336.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
excelhost[.]com[.]au --> glasgowminibuses[.]co[.]uk --> rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:16:29 UTC - 122.201.80[.]95:80 - excelhost[.]com[.]au - GET /OnlineOffice/
- 2014-05-14 00:16:29 UTC - 213.171.218[.]116:80 - glasgowminibuses[.]co[.]uk - GET /JWxZ3bdR.php?id=10371842
- 2014-05-14 00:16:30 UTC - 213.171.218[.]116:80 - glasgowminibuses[.]co[.]uk - GET /JWxZ3bdR.php?html=27
- 2014-05-14 00:16:31 UTC - 213.171.218[.]116:80 - glasgowminibuses[.]co[.]uk - GET /checker.php [repeats]
- 2014-05-14 00:16:33 UTC - 134.170.108[.]152:443 - rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:16:33 UTC - 134.170.108[.]152:443 - rvok3w.bay.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- rvok3w.bay.livefilestore[.]com/y2mU6xXdJYVisIKlwgibbSKFWV_qiitQV19q8iDFY2fUCIUD_G3uB4lzZbYxuT5x5PmyNyhrIhk2O7Zwa7U7jedoB-lkaGHEjGnxoHe35sN0OI/
FlashUpdater61869.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
www.abbruch-schille.de --> johnsoncontracting.org --> rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:17:58 UTC - 81.169.145[.]157:80 - www.abbruch-schille[.]de - GET /
- 2014-05-14 00:18:00 UTC - 50.62.230[.]1:80 - johnsoncontracting[.]org - GET /2x7fwWz6.php?id=14929460
- 2014-05-14 00:18:03 UTC - 50.62.230[.]1:80 - johnsoncontracting[.]org - GET /2x7fwWz6.php?html=27
- 2014-05-14 00:18:03 UTC - 50.62.230[.]1:80 - johnsoncontracting[.]org - GET /checker.php [repeats]
- 2014-05-14 00:18:05 UTC - 134.170.108[.]176:443 - rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:18:05 UTC - 134.170.108[.]176:443 - rvok3w.bay.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- rvok3w.bay.livefilestore[.]com/y2mU6xXdJYVisIKlwgibbSKFWV_qiitQV19q8iDFY2fUCIUD_G3uB4lzZbYxuT5x5PmyNyhrIhk2O7Zwa7U7jedoB-lkaGHEjGnxoHe35sN0OI/
FlashUpdater15246.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
freezeengineers[.]co[.]in --> 85.214.64[.]33 --> rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:19:25 UTC - 192.185.157[.]48:80 - freezeengineers[.]co[.]in - GET /voltas-water-dispensers.html
- 2014-05-14 00:19:25 UTC - 85.214.64[.]33:80 - 85.214.64[.]33 - GET /ragdoll-von-amandine/LK7fF9P3.php?id=6123180
- 2014-05-14 00:19:25 UTC - 85.214.64[.]33:80 - 85.214.64[.]33 - GET /ragdoll-von-amandine/LK7fF9P3.php?id=6123052
- 2014-05-14 00:19:30 UTC - 85.214.64[.]33:80 - 85.214.64[.]33 - GET /ragdoll-von-amandine/LK7fF9P3.php?html=27
- 2014-05-14 00:19:31 UTC - 85.214.64[.]33:80 - 85.214.64[.]33 - GET /ragdoll-von-amandine/checker.php [repeats]
- 2014-05-14 00:19:32 UTC - 134.170.108[.]200:443 - rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:19:32 UTC - 134.170.108[.]200:443 - rvok3w.bay.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- rvok3w.bay.livefilestore[.]com/y2mU6xXdJYVisIKlwgibbSKFWV_qiitQV19q8iDFY2fUCIUD_G3uB4lzZbYxuT5x5PmyNyhrIhk2O7Zwa7U7jedoB-lkaGHEjGnxoHe35sN0OI/
FlashUpdater74216.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
www.studio-creatief.nl --> bair[.]com[.]ua --> rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:22:20 UTC - 83.96.159[.]11:80 - www.studio-creatief[.]nl - GET /tekeningen.html
- 2014-05-14 00:22:20 UTC - 192.185.145[.]93:80 - bair[.]com[.]ua - GET /_vti_bin/CZvQX6KW.php?id=12928438
- 2014-05-14 00:22:21 UTC - 192.185.145[.]93:80 - bair[.]com[.]ua - GET /_vti_bin/CZvQX6KW.php?id=12928442
- 2014-05-14 00:22:21 UTC - 192.185.145[.]93:80 - bair[.]com[.]ua - GET /_vti_bin/CZvQX6KW.php?id=12928448
- 2014-05-14 00:22:22 UTC - 192.185.145[.]93:80 - bair[.]com[.]ua - GET /_vti_bin/CZvQX6KW.php?id=12928447
- 2014-05-14 00:22:22 UTC - 192.185.145[.]93:80 - bair[.]com[.]ua - GET /_vti_bin/CZvQX6KW.php?html=27
- 2014-05-14 00:22:22 UTC - 192.185.145[.]93:80 - bair[.]com[.]ua - GET /_vti_bin/checker.php [repeats]
- 2014-05-14 00:22:24 UTC - 134.170.108[.]48:443 - rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:22:24 UTC - 134.170.108[.]48:443 - rvok3w.bay.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- rvok3w.bay.livefilestore[.]com/y2mP4PhRanMO0PefZLlzYIwwoR0lTKLHDoEr9oLA5piza-nM9-y1aGrZEWBuL4tMStdYAiBONCi1yWnktpjUKWAN8TYGQeyFwapdjgCgmiXDzs/
FlashUpdater69723.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
www.tamerhosny[.]ws --> www.viscure[.]eu --> rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:23:12 UTC - 108.178.61[.]42:80 - www.tamerhosny[.]ws - GET /site2011/
- 2014-05-14 00:23:13 UTC - 69.61.75[.]55:80 - www.viscure[.]eu - GET /php/zVXPCmYJ.php?id=2786160
- 2014-05-14 00:23:13 UTC - 69.61.75[.]55:80 - www.viscure[.]eu - GET /php/zVXPCmYJ.php?id=2786146
- 2014-05-14 00:23:14 UTC - 69.61.75[.]55:80 - www.viscure[.]eu - GET /php/zVXPCmYJ.php?html=27
- 2014-05-14 00:23:15 UTC - 69.61.75[.]55:80 - www.viscure[.]eu - GET /php/checker.php [repeats]
- 2014-05-14 00:23:16 UTC - 134.170.108[.]72:443 - rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:23:16 UTC - 134.170.108[.]72:443 - rvok3w.bay.livefilestore[.]com
- rvok3w.bay.livefilestore[.]com/y2mP4PhRanMO0PefZLlzYIwwoR0lTKLHDoEr9oLA5piza-nM9-y1aGrZEWBuL4tMStdYAiBONCi1yWnktpjUKWAN8TYGQeyFwapdjgCgmiXDzs/
FlashUpdater43290.exe
compromised website --> fake Flash updater notice --> Microsoft OneDrive hosting the malware
hbo[.]gr --> collectiveintelligence[.]net --> rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:25:52 UTC - 62.1.159[.]34:80 - hbo[.]gr - GET /klostiridiaki_mionekrosi.html
- 2014-05-14 00:25:53 UTC - 70.32.68[.]82:80 - collectiveintelligence[.]net - GET /nR9Xh72V.php?id=6439242
- 2014-05-14 00:25:54 UTC - 70.32.68[.]82:80 - collectiveintelligence[.]net - GET /nR9Xh72V.php?html=27
- 2014-05-14 00:25:55 UTC - 70.32.68[.]82:80 - collectiveintelligence[.]net - GET /checker.php [repeats]
- 2014-05-14 00:25:56 UTC - 134.170.108[.]96:443 - rvok3w.bay.livefilestore[.]com
- 2014-05-14 00:25:56 UTC - 134.170.108[.]96:443 - rvok3w.bay.livefilestore[.]com
HTTPS link from fake Flash updater notice:
- rvok3w.bay.livefilestore[.]com/y2mP4PhRanMO0PefZLlzYIwwoR0lTKLHDoEr9oLA5piza-nM9-y1aGrZEWBuL4tMStdYAiBONCi1yWnktpjUKWAN8TYGQeyFwapdjgCgmiXDzs/
FlashUpdater60598.exe
PRELIMINARY MALWARE ANALYSIS
File name: FlashUpdater60598.exe
File size: 182,616 bytes
MD5 hash: f5af9d1881cf5470121bb994ea95ed9c
Detection ratio: 9 / 43
First submission: 2014-05-13 14:03:46 UTC
VirusTotal link: https://www.virustotal.com/en/file/132e6e1ef6d011d05da6f033498121bbe926cfa6ede1e69f4131684944fbe455/analysis/
TRAFFIC FROM SANDBOX ANALYSIS
- 193.105.210[.]32 - domaintomakeit[.]com - POST /unecheitd/8732593/index.php [repeats]
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/inexsabit.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/aveksynkens.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/tobnenuko.exe
- 216.151.164[.]53 - arkinsoftware[.]in - GET /images/nukotobne.exe
- 46.119.23[.]41 - zemmes-gimbl[.]com - GET /b/shoe/54607 [repeats]
- 5.149.222[.]125 - chanse-leaf[.]com - GET /components-jumla-bq/jquery/ [repeats]
- 134.90.108[.]105 - chanse-leaf[.]com - GET /components-jumla-bq/ajax/ [repeats]
- 79.142.66[.]240 - report.m7gmyw931gmy1c93[.]com - GET /?G7iQ31=%96%9E%A3%D2[long string of characters, repeats with different strings]
- 5.149.248[.]153 - report.m7gmyw931gmy1c93[.]com - POST /
- 5.149.248[.]153 - update1.7uxyxkihmso[.]com - GET /?kx=ka6jx5ikyGpga9arr6[long string of characters]
ALERTS
EXAMPLE OF ALERTS FOR THE TRAFFIC (from Sguil on Security Onion)
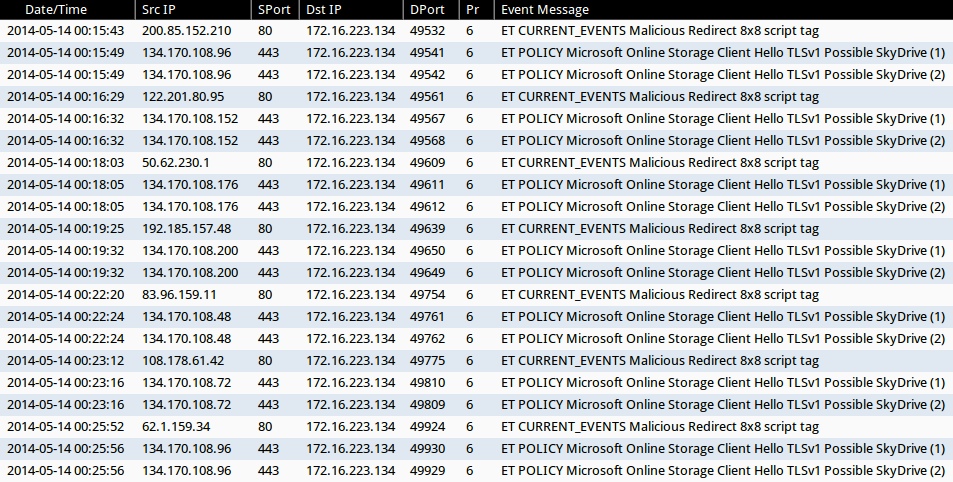
- ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive(1) (sid:2014919)
- ET POLICY Microsoft Online Storage Client Hello TLSv1 Possible SkyDrive(2) (sid:2014920)
ALERTS FROM THE SANDBOX ANALYSIS
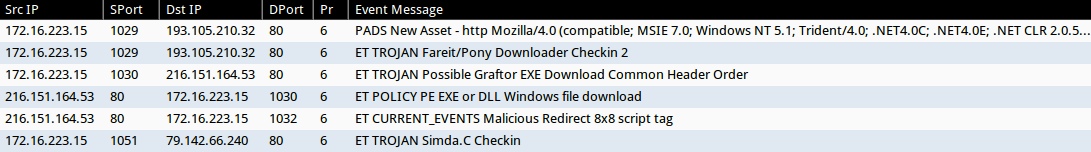
- ET TROJAN Fareit/Pony Downloader Checkin 2 (sid:2014411)
- ET TROJAN Possible Graftor EXE Download Common Header Order (sid:2018254)
- ET POLICY PE EXE or DLL Windows file download (sid:2000419)
- ET CURRENT_EVENTS Malicious Redirect 8x8 script tag (sid:2018053)
- ET TROJAN Simda.C Checkin (sid:2016300)
Click here to return to the main page.

